1 Introduction and functional overview
2 Acronyms and Abbreviations
3 Related documentation
3.1 Input documents & related standards and norms
3.2 Related specification
4 Constraints and assumptions
4.1 Limitations
4.2 Applicability to car domains
4.3 Background information concerning functional safety
4.3.1 Functional safety and communication
4.3.2 Sources of faults in E2E communication
4.3.2.1 Software faults
4.3.2.2 Random hardware faults
4.3.2.3 External influences, environmental stress
4.3.3 Communication faults
4.3.3.1 Repetition of information
4.3.3.2 Loss of information
4.3.3.3 Delay of information
4.3.3.4 Insertion of information
4.3.3.5 Masquerading
4.3.3.6 Incorrect addressing
4.3.3.7 Incorrect sequence of information
4.3.3.8 Corruption of information
4.3.3.9 Asymmetric information sent from a sender to multiple receivers
4.3.3.10 Information from a sender received by only a subset of the receivers
4.3.3.11 Blocking access to a communication channel
5 Functional specification
5.1 Overview of communication protection
5.2 Overview of E2E Profiles
5.2.1 Error detection
5.3 Specification of E2E Profile 1 (Only for CP)
5.3.1 Data Layout
5.3.2 Counter
5.3.3 Data ID
5.3.4 CRC calculation
5.3.5 Timeout detection
5.3.6 E2E Profile 1 variants
5.3.7 E2E_P01Protect
5.3.8 Calculate CRC
5.3.9 E2E_P01Check
5.3.10 E2E Profile 1 Protocol Examples
5.3.10.1 DataIDMode set to E2E_P01DATAID_ALT
5.3.10.2 DataIDMode set to E2E_P01DATAID_LOW
5.3.10.3 DataIDMode set to E2E_P01DATAID_NIBBLE
5.4 Specification of E2E Profile 2 (only for CP)
5.4.1 E2E_P02Protect
5.4.2 E2E_P02Check
5.5 Specification of E2E Profile 4
5.5.1 Data Layout
5.5.1.1 User data layout
5.5.1.2 Header layout
5.5.2 Counter
5.5.3 Length
5.5.4 CRC
5.5.5 Timeout detection
5.5.6 E2E Profile 4 variants
5.5.7 E2E_P04Protect
5.5.8 E2E_P04Check
5.6 Specification of E2E Profile 5
5.6.1 Data Layout
5.6.1.1 User data layout
5.6.1.2 Header layout
5.6.2 Counter
5.6.3 Data ID
5.6.4 Length
5.6.5 CRC
5.6.6 Timeout detection
5.6.7 E2E_P05Protect
5.6.8 E2E_P05Check
5.7 Specification of E2E Profile 6
5.7.1 Data Layout
5.7.1.1 User data layout
5.7.1.2 Header layout
5.7.2 Counter
5.7.3 Data ID
5.7.4 Length
5.7.5 CRC
5.7.6 Timeout detection
5.7.7 E2E_P06Protect
5.7.8 E2E_P06Check
5.8 Specification of E2E Profile 7
5.8.1 Data Layout
5.8.1.1 User data layout
5.8.1.2 Header layout
5.8.2 Counter
5.8.3 Data ID
5.8.4 Length
5.8.5 CRC
5.8.6 Timeout detection
5.8.7 E2E Profile 7 variants
5.8.8 E2E_P07Protect
5.8.9 E2E_P07Check
5.9 Specification of E2E Profile 11
5.9.1 Data Layout
5.9.1.1 User data layout
5.9.1.2 Header layout
5.9.2 Counter
5.9.3 Data ID
5.9.4 Length
5.9.5 CRC
5.9.6 Timeout detection
5.9.7 E2E_P11Protect
5.9.8 E2E_P11Check
5.10 Specification of E2E Profile 22
5.10.1 Data Layout
5.10.1.1 User data layout
5.10.1.2 Header layout
5.10.2 Counter
5.10.3 Data ID
5.10.4 Length
5.10.5 CRC
5.10.6 Timeout detection
5.10.7 E2E_P22Protect
5.10.8 E2E_P22Check
5.11 Specification of E2E state machine
5.11.1 Overview of the state machine
5.11.2 State machine specification
5.12 Basic Concepts of CRC Codes
5.12.1 Mathematical Description
5.12.2 Euclidian Algorithm for Binary Polynomials and Bit-Sequences
5.12.3 CRC calculation, Variations and Parameter
5.13 CRC Standard Parameters
5.13.1 8-bit CRC calculation
5.13.1.1 8-bit SAE J1850 CRC Calculation
5.13.1.2 8-bit 0x2F polynomial CRC Calculation
5.13.2 16-bit CRC calculation
5.13.2.1 16-bit CCITT-FALSE CRC16
5.13.3 32-bit CRC calculation
5.13.3.1 32-bit Ethernet CRC Calculation
5.13.3.2 32-bit 0xF4ACFB13 polynomial CRC calculation
5.13.4 64-bit CRC calculation
5.13.4.1 64-bit ECMA polynomial CRC calculation
6 E2E API specification
6.1 API of middleware to applications
6.2 API of E2E
7 Configuration Parameters
8 Protocol usage and guidelines
8.1 Periodic use of E2E check
8.2 Error handling
8.3 Maximal lengths of Data, communication buses















 V2版本原理图(Capacitive-Fingerprint-Reader-Schematic_V2).pdf
V2版本原理图(Capacitive-Fingerprint-Reader-Schematic_V2).pdf 摄像头工作原理.doc
摄像头工作原理.doc VL53L0X简要说明(En.FLVL53L00216).pdf
VL53L0X简要说明(En.FLVL53L00216).pdf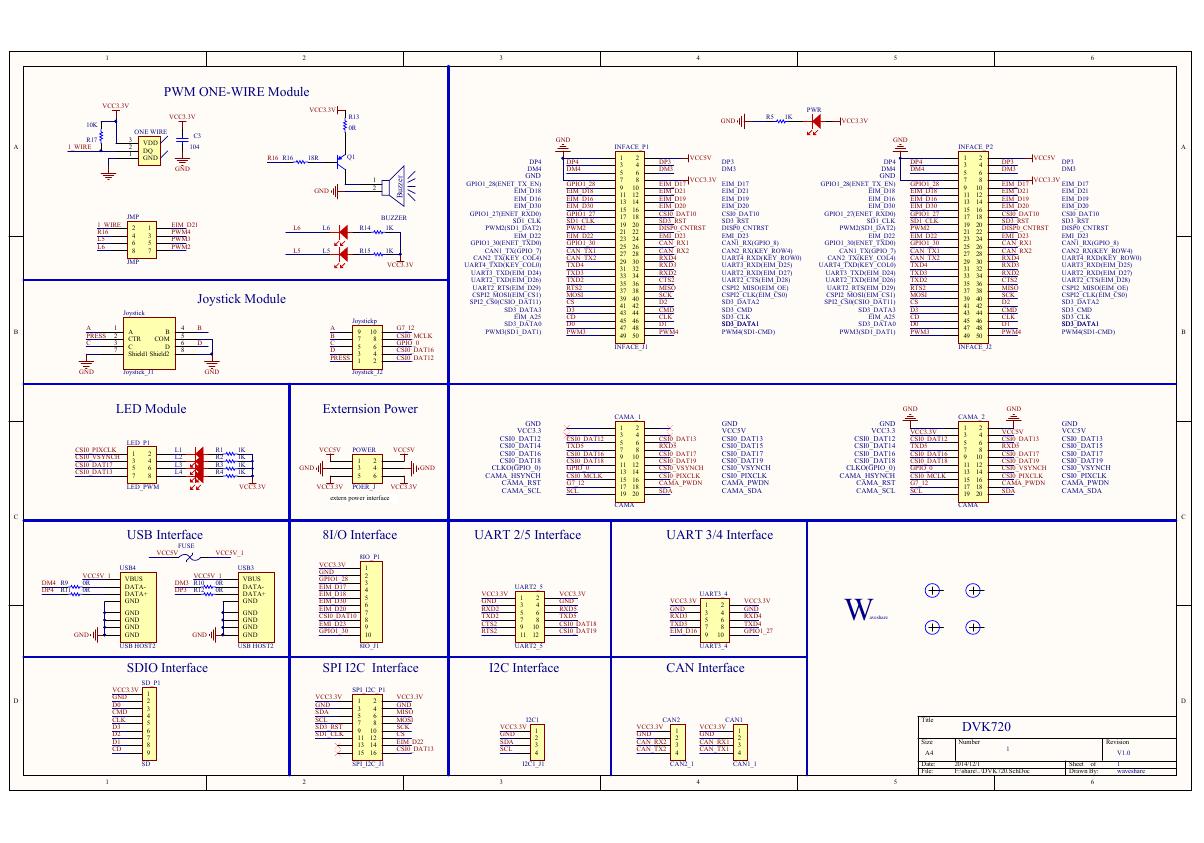 原理图(DVK720-Schematic).pdf
原理图(DVK720-Schematic).pdf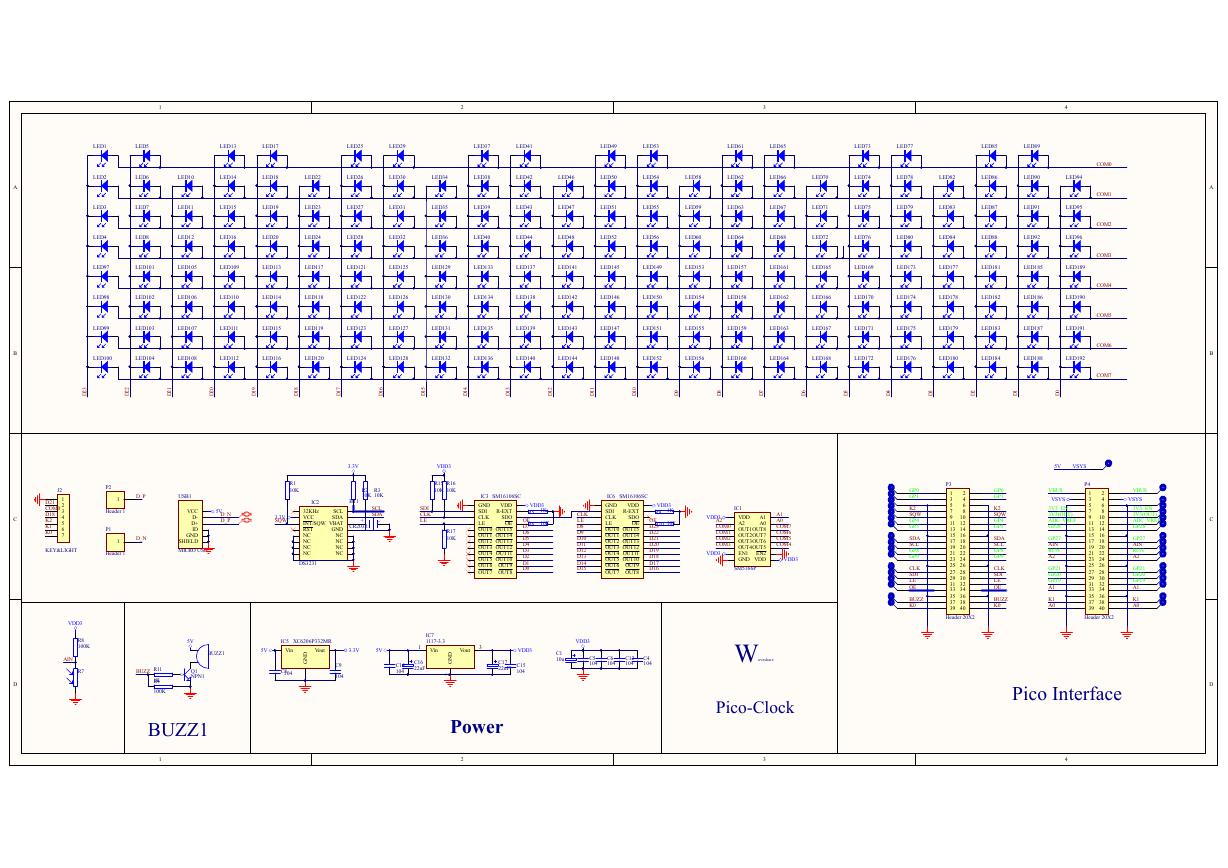 原理图(Pico-Clock-Green-Schdoc).pdf
原理图(Pico-Clock-Green-Schdoc).pdf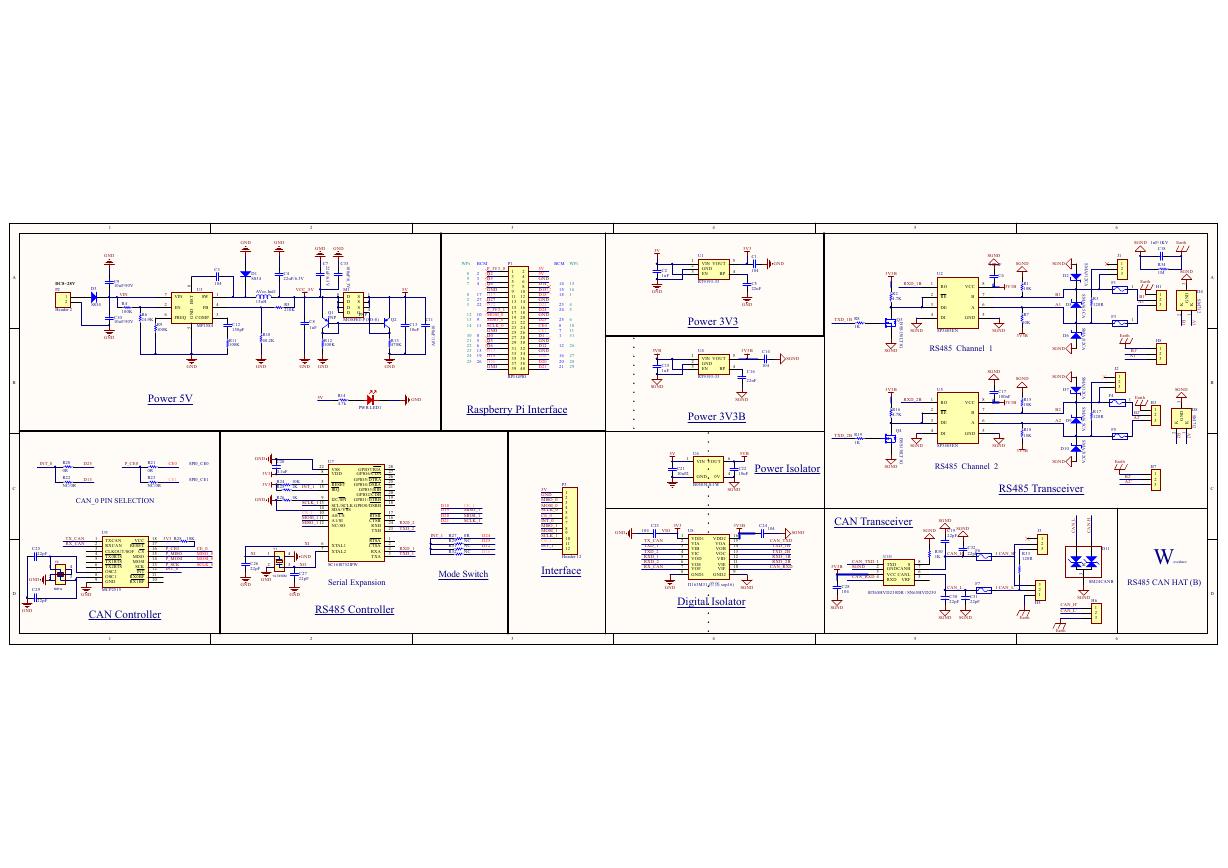 原理图(RS485-CAN-HAT-B-schematic).pdf
原理图(RS485-CAN-HAT-B-schematic).pdf File:SIM7500_SIM7600_SIM7800 Series_SSL_Application Note_V2.00.pdf
File:SIM7500_SIM7600_SIM7800 Series_SSL_Application Note_V2.00.pdf ADS1263(Ads1262).pdf
ADS1263(Ads1262).pdf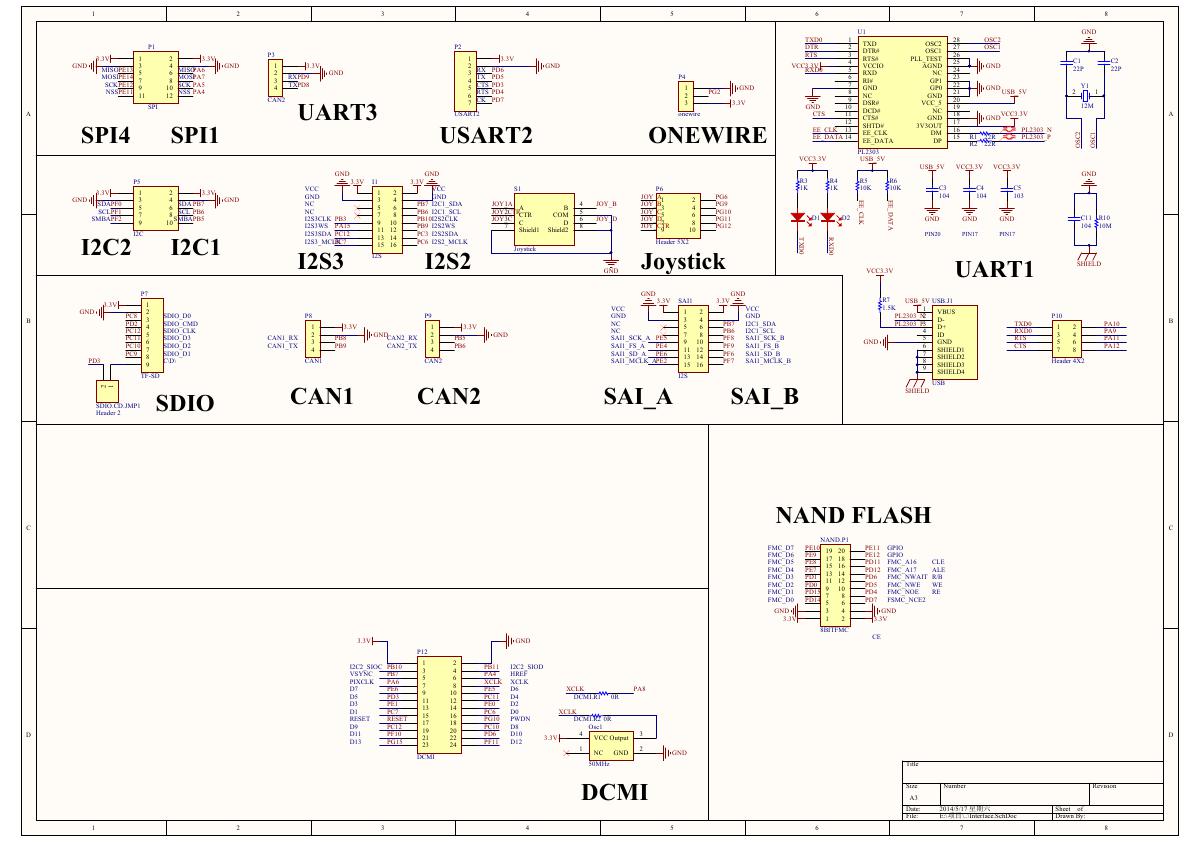 原理图(Open429Z-D-Schematic).pdf
原理图(Open429Z-D-Schematic).pdf 用户手册(Capacitive_Fingerprint_Reader_User_Manual_CN).pdf
用户手册(Capacitive_Fingerprint_Reader_User_Manual_CN).pdf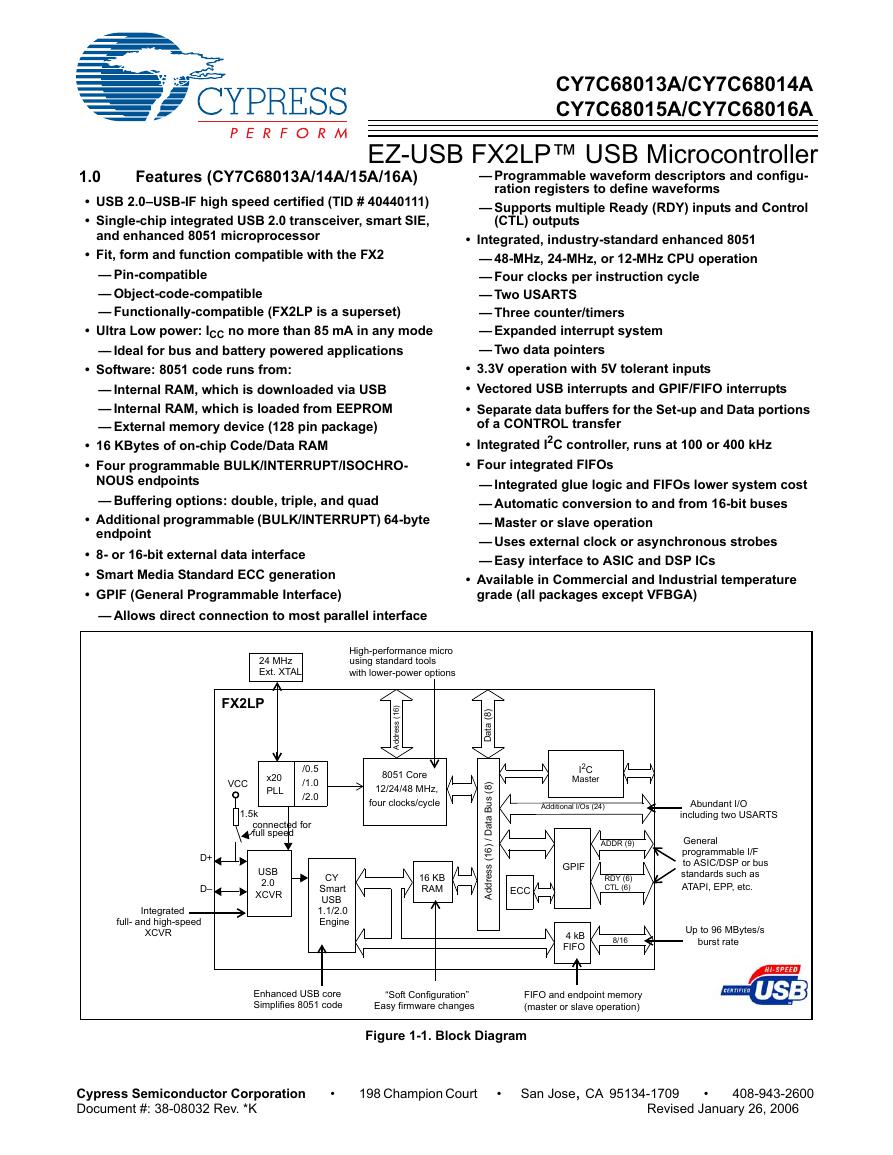 CY7C68013A(英文版)(CY7C68013A).pdf
CY7C68013A(英文版)(CY7C68013A).pdf TechnicalReference_Dem.pdf
TechnicalReference_Dem.pdf