Contents at a Glance
Contents
About the Author
About the Project Manager
About the Technical Reviewer
Acknowledgments
Foreword
Chapter 1: It’s Different Out Here
Why the Internet of Things Requires a New Solution
It’s Networking on the Frontier
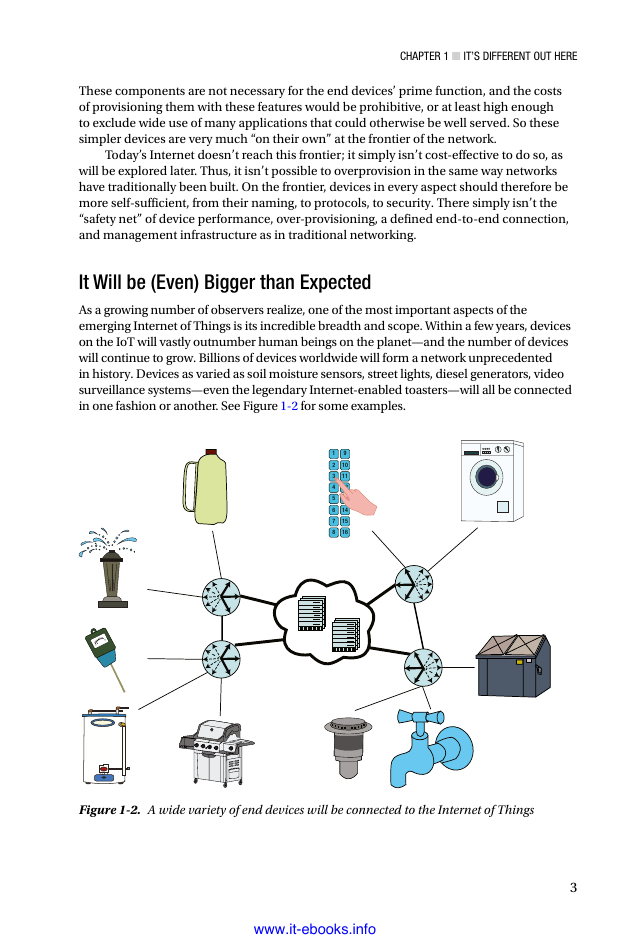
It Will be (Even) Bigger than Expected
Terse, Purposeful, and Uncritical
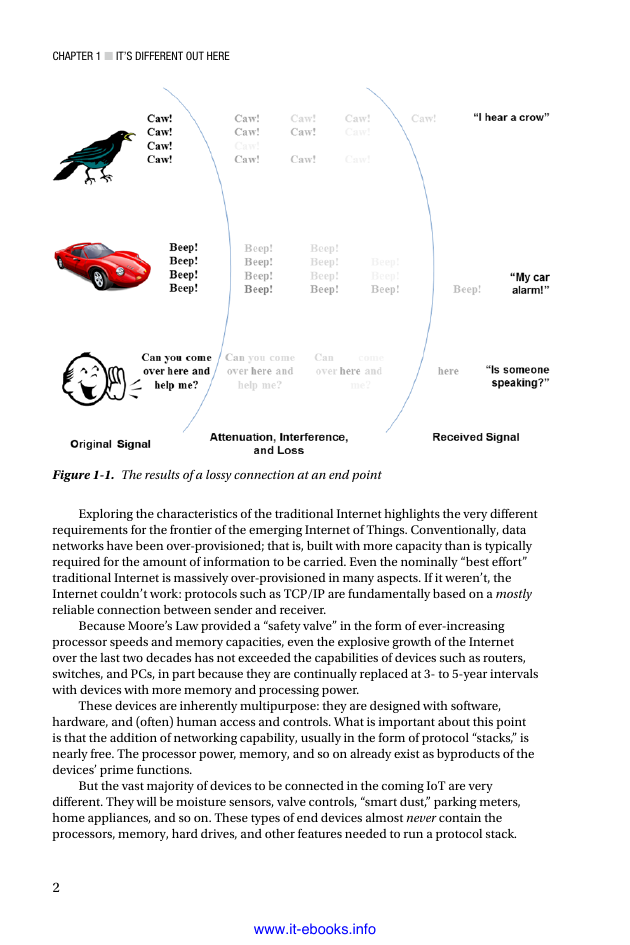
Dealing with Loss
The Protocol Trap
Mind the Overhead
More Smarts, More Risk
The Overhead of Overhead
Humans Need Not Apply
Economics and Technology of the Internet of Things
Functionality Costs Money
Inexpensive Devices Can’t Bear Traditional Protocols
Overseeing 700 Billion Devices
Only Where and When Needed
Security Through Simplicity (and Stupidity)
Cost and Connectivity
Solving the IoT Dilemma
Inspiration for a New Architecture
Nature: The Original Big Data
Autonomy of Individuals
Zones and Neighborhoods of Interest
In the Eyes of the Beholder
Signal Simplicity
Leveraging Nature
Peer-to-Peer Is Not Equal
Transporting IoT Traffic
Billions of Devices; Three Functional Levels
Propagator Nodes Add Networking Functionality
Collecting, Integrating, Acting
When the Scope Is Too Massive
Functional vs. Physical Packaging
Connecting to the “Big I”
Smaller Numbers, Bigger Functionality
Chapter 2: Anatomy of the Internet of Things
Traditional Internet Protocols Aren’t the Solution for Much of the IoT
Introducing the “Chirp ”
Lightweight and Disposable
Functionality the IoT Needs—and Doesn’t
Efficiency Out of Redundancy
It’s All Relative
Format Flexibility
Private Markers for Customization and Extensibility
Addressing and “Rhythms ”
Family Types
Applying Network Intelligence at Propagator Nodes
Transport and Functional Architectures
Functional Network Topology
Defined by Integrator Functions
Harvesting Information from the IoT
Programming and “Bias”
Receiver-Oriented Selectivity
Chapter 3: On the Edge
A World of Different Devices
Intended to be Untended: Some Examples of IoT Systems
Temporary and Ad Hoc Devices
Addressing an Uncertain Frontier
Reliability Through Numbers
Meaning from Many
End Devices in Dedicated Networks
Expanding to the World
Converting States to Chirps
“Setting” End Devices
Cornucopia of Connections
Chirp on a Chip
Aftermarket Options
RFID Integration in the Internet of Things
End Devices with Higher Demands
The Big Idea: “Small” Data
Chapter 4: Building a Web of Things
Versatility in Function and Form
Architecting Trees and Leaves
On Behalf of Chirps at the Edge
Isolating and Securing the Edge
Autonomy and Coordination
Structuring a Networking Path
Structuring a Tree—with Redundancy
Housekeeping
By Any Means
Take Out the Thrash
The Power of Bias and the Role of the Integrator Function
Bias and Influence
Degrees of Functionality
Aggregating End Points
Dumping the Dupes
Loading the Bus: The Propagator Node Transit System
Weathering the Storms
Dodging the Collisions
What’s in a Name?
Packaging Options
Building Blocks of the IoT
Chapter 5: Small Data, Big Data, and Human Interaction
The “Brains” of the IoT
For Once, IP Makes Sense
Extracting the Streams
Analysis and Control
Chirps to “Small Data” to Big Data: An Example
Neighborhoods and Affinities
Public, Private, and Some of Each
Bias Bonus
Searching for and Managing Agents
High- and Low-Level “Loops ”
Human Interface and Control Points
Machines and Metcalfe
Collaborative Scheduling Tools
Packaging and Provisioning
Distribut ed Integrator Functions
Location, Location, Location
Filtering the Streams
Accessing the Power of the Internet of Things
Chapter 6: Architecture for the Frontier
A Necessary Alternative to IP
A Big Problem, and Getting Bigger
An Alternative Inspired by Nature
A Protocol Based on Category Classifications
Skeletal Architecture of Chirp Packets
Individual Information within Chirp Signatures
“Light” Error Detection and Security
Generic Chirp Handling
Incognito Chirp Transport
Transmission Agility Information within the Chirp
Extensible, Nonunique, Pattern-driven
Category Byte Size
Marker Pattern Templates
Finer Control via Agents
Scheduling the Bus
Routing on Category Classifications
Managing the Load
Propagator Node Networks and Operation
A Tree Grows in the IoT
Choosing Parents Wisely
Scanning and Switching
Specialized and Basic Routing
Housekeeping Frames for Network Intelligence
Latency and Throughput Tradeoffs
Routing Table Updates
The Power of Local Agents and Integrator Functions
Task Scheduling within the Internet of Things
Higher-level Interchange
Managing Multiple Isochronous Relationships
An Organic Solution for the IoT
Chapter 7: Examples and Applications
Controlling the Cacophony
Intelligence Near the Edge
Incorporating Legacy Devices
Staying in the Loop(s)
Okay on their Own
All the World Is a Subscription
Exploring Affinities
Social Machines
Agriculture
Home Health Care
Safe and Efficient Process Control
Better Perimeter Security and Surveillance
Faster Factory Floors
True Home Automation
Wholesale and Retail: Beyond RFID
A Broader “Net” in Natural Sciences
Living Applications
Chapter 8: Pathways to the Internet of Things
Data Drives a Change
Classification is the Challenge, Chirp is the Answer
The Ends are the Means
Begin at the Edge
Making a Mark
Acting on Markers
Propagator Nodes Provide the “and”
Open-Source Networking Solutions
Gaining Access
The Standards Conundrum
Machine-to-Machine Communications and Autonomy
Shared Vocabularies and de facto Standards
Build it and End Devices will Come
OEM Leverage
Shared Software and Business Process Vocabularies
Working in Groups
Call to Constituencies for the IoT
Semiconductor Providers
Appliance and Other End Device Manufacturers
Networking Equipment Vendors
Home Automation/Entertainment Suppliers
Carriers and Big Data Providers
Major End-to-End OEMs
Global Scope, Vast Numbers, Constant Adaptation, New Insights
Index














 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc