The Cyber Center for Security and Analytics
The Cyber Center for Security and Analytics
ZEEK INTRUSION DETECTION SERIES
Lab 1: Introduction to the Capabilities of Zeek
Document Version: 03-13-2020
“CyberTraining CIP: Cyberinfrastructure Expertise on High-throughput
Networks for Big Science Data Transfers”
Award 1829698
�
Lab 1: Introduction to the Capabilities of Zeek
1
1.1
3
1.1.1
1.1.2
1.1.3
1.1.4
Contents
Overview ............................................................................................................................. 3
Objectives............................................................................................................................ 3
Lab topology........................................................................................................................ 3
Lab settings ......................................................................................................................... 3
Lab roadmap ................................................................................................................... 4
Introduction to Zeek ................................................................................................... 4
The Zeek event engine ......................................................................................... 5
State management ........................................................................................ 5
Transport layer analyzers .............................................................................. 5
Application layer analyzers ........................................................................... 5
Infrastructure ................................................................................................ 5
The Zeek policy script interpreter ........................................................................ 6
Zeek analyzers ...................................................................................................... 6
Signatures ............................................................................................................. 6
ZeekControl .......................................................................................................... 7
2 Using ZeekControl to update the status of Zeek ........................................................ 7
Starting a new instance of Zeek ........................................................................... 9
Stopping the active instance of Zeek ................................................................. 10
Introduction to Zeek’s traffic analysis capabilities ................................................... 10
Processing offline packet capture files .............................................................. 11
Command format for processing packet capture files ............................... 11
Leveraging a script to detect brute force attacks present in a pcap file .... 11
3.2
Launching Mininet .............................................................................................. 12
3.3 Generating and analyzing live network traffic capture ..................................... 15
Leveraging the Tcpdump command utility ................................................. 16
Capturing live network traffic ..................................................................... 16
Analyzing the newly captured network traffic ........................................... 18
References ........................................................................................................................ 20
3.3.1
3.3.2
3.3.3
3.1.1
3.1.2
1.2
1.3
1.4
1.5
2.1
2.2
3.1
Page 2
�
Lab 1: Introduction to the Capabilities of Zeek
Overview
This lab introduces Zeek, an open-source network analysis framework primarily used in
security monitoring and traffic analysis. The primary focus of this lab is to explain Zeek’s
layered architecture while demonstrating Zeek’s capabilities towards performing network
traffic analysis.
Objectives
By the end of this lab, students should be able to:
1. Understand Zeek’s layered architecture.
2. Start and manage a Zeek instance using the ZeekControl utility.
3. Use Zeek to process packet captures files.
4. Generate and analyze live network traffic in Zeek.
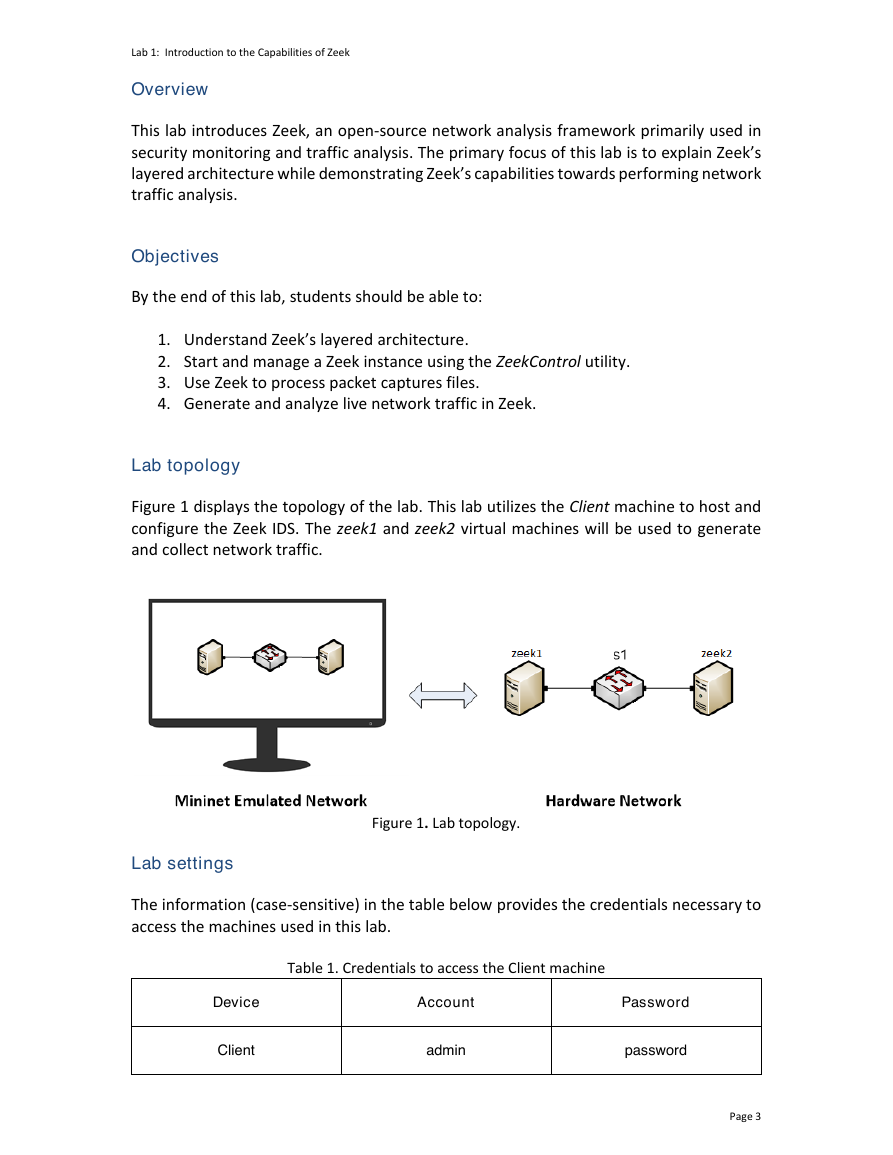
Lab topology
Figure 1 displays the topology of the lab. This lab utilizes the Client machine to host and
configure the Zeek IDS. The zeek1 and zeek2 virtual machines will be used to generate
and collect network traffic.
Figure 1. Lab topology.
Lab settings
The information (case-sensitive) in the table below provides the credentials necessary to
access the machines used in this lab.
Table 1. Credentials to access the Client machine
Device
Client
Account
Password
admin
password
Page 3
�
Lab 1: Introduction to the Capabilities of Zeek
Table 2. Shell variables and their corresponding absolute paths.
Variable Name
Absolute Path
$ZEEK_INSTALL
/usr/local/zeek
$ZEEK_TESTING_TRACES
/home/zeek/zeek/testing/btest/Traces
$ZEEK_PROTOCOLS_SCRIPT
/home/zeek/zeek/scripts/policy/protocols
Lab roadmap
This lab is organized as follows:
1. Section 1: Introduction to Zeek.
2. Section 2: Using ZeekControl to update the status of Zeek.
3. Section 3: Introduction to Zeek’s traffic analysis capabilities.
Introduction to Zeek
1
Zeek is a passive, open-source network traffic analyzer. It is primarily used as a security
monitor that inspects all traffic on a network link for signs of suspicious activity1. It can
run on commodity hardware with standard UNIX-based systems and can be used as a
passive network monitoring tool.
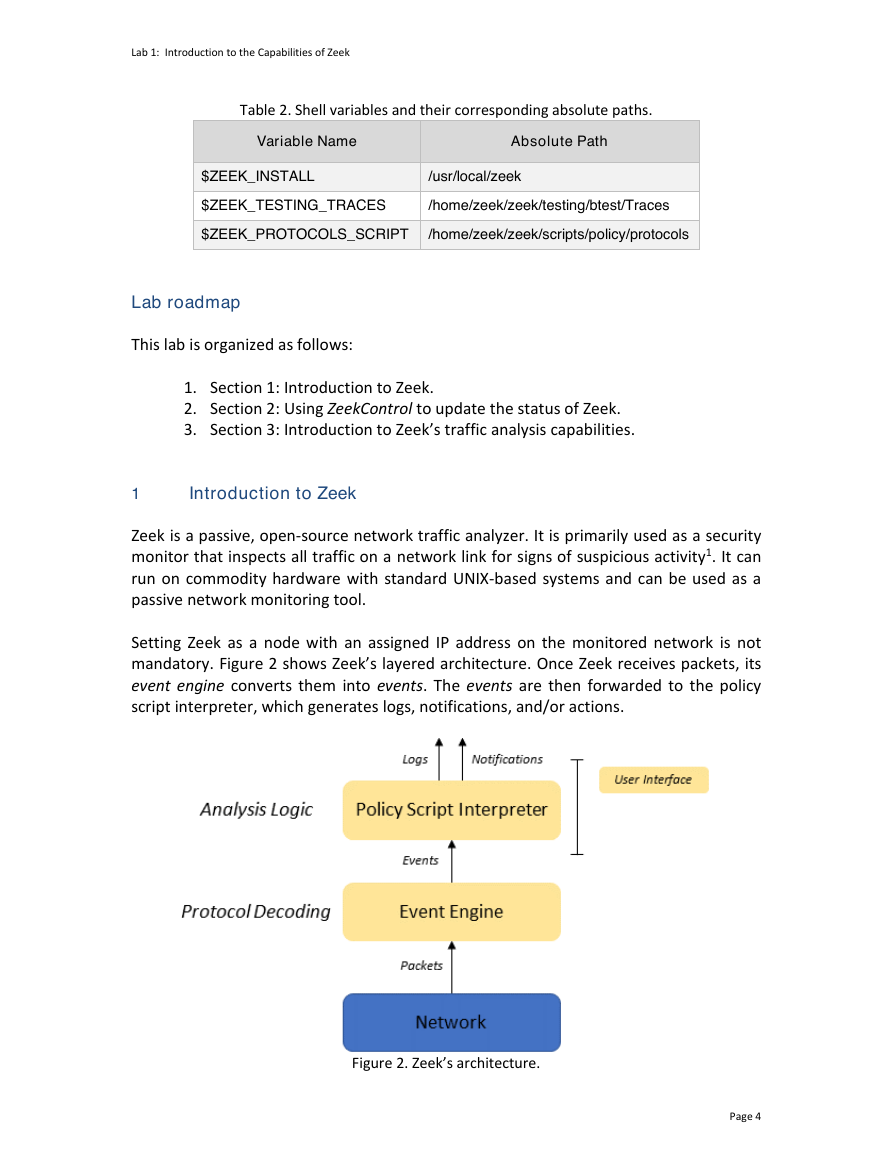
Setting Zeek as a node with an assigned IP address on the monitored network is not
mandatory. Figure 2 shows Zeek’s layered architecture. Once Zeek receives packets, its
event engine converts them into events. The events are then forwarded to the policy
script interpreter, which generates logs, notifications, and/or actions.
Figure 2. Zeek’s architecture.
Page 4
�
Lab 1: Introduction to the Capabilities of Zeek
The Zeek event engine
Zeek uses the standard libpcap library for capturing packets to be used in network
monitoring and analysis.
1.1
The event engine layer performs low-level network packets analysis. It receives raw
packets from the network layer (packet capture), sorts them by connection, reassembles
data streams, and decodes application layer protocols. Whenever it encounters
something potentially relevant to the policy layer, it generates an event.
The event engine consists of several analyzers responsible for well-defined tasks. Typical
tasks include decoding a specific protocol, performing signature-matching, identifying
backdoors, etc. Usually, an analyzer is accompanied by a default script which implements
some general policy adjustable to the local environment. The event engine can be divided
into four major parts.
1.1.1 State management
Zeek’s main data structure is a connection which follows typical flow identification
mechanisms, such as 5-tuple approaches. The 5-tuple structure consists of the source IP
address/port number, destination IP address/port number, and the protocol in use. For a
connection-oriented protocol like TCP, the definition of a connection is more clear-cut,
however for others such as UDP and ICMP, Zeek implements a flow-like abstraction to
aggregate packets. Each packet belongs to exactly one connection.
1.1.2 Transport layer analyzers
On the transport layer, Zeek analyzes TCP, UDP packets. In TCP, Zeek’s associated analyzer
closely follows the various state changes, keeps track of acknowledgments, handles
retransmissions and much more.
1.1.3 Application layer analyzers
The analysis of the application layer data of a connection depends on the service. There
are analyzers for a wide variety of different protocols, e.g. HTTP, SMTP or DNS, that
generally conduct detailed analysis of the data stream.
1.1.4
The general
components, the script interpreter, and data structures.
includes the event and timer management
Infrastructure
infrastructure of Zeek
Page 5
�
Lab 1: Introduction to the Capabilities of Zeek
The Zeek policy script interpreter
1.2
While the event engine itself is policy-neutral, the top layer of Zeek defines the
environment-specific network security policy. By writing handlers for events that may be
raised by the event engine, the user can precisely define the constraints within the given
network. If a security breach is detected, the policy layer generates an alert.
New event handlers can be created in Zeek’s own scripting language. While providing all
expected convenience of a powerful scripting language, it has been designed with
network intrusion detection in mind. While it is expected that additional policy scripts are
written by the user, there are nevertheless several default scripts included with the initial
installation of Zeek. These default scripts already perform a wide range of analyses and
are easily customizable.
1.3
The majority of Zeek’s analyzers are in its event engine with accompanying policy scripts
that can be customized by the user. Sometimes, however, the analyzer is just a policy
script implementing multiple event handlers. The analyzers perform application layer
decoding, anomaly detection, signature matching and connection analysis. Zeek has been
designed so that it is easy to add additional analyzers.
1.4
Most network intrusion detection systems (NIDS) match a large set of signatures against
the network traffic. Here, a signature is a pattern of bytes that the NIDS tries to locate in
the payload of network packets. As soon as a match is found, the system generates an
alert.
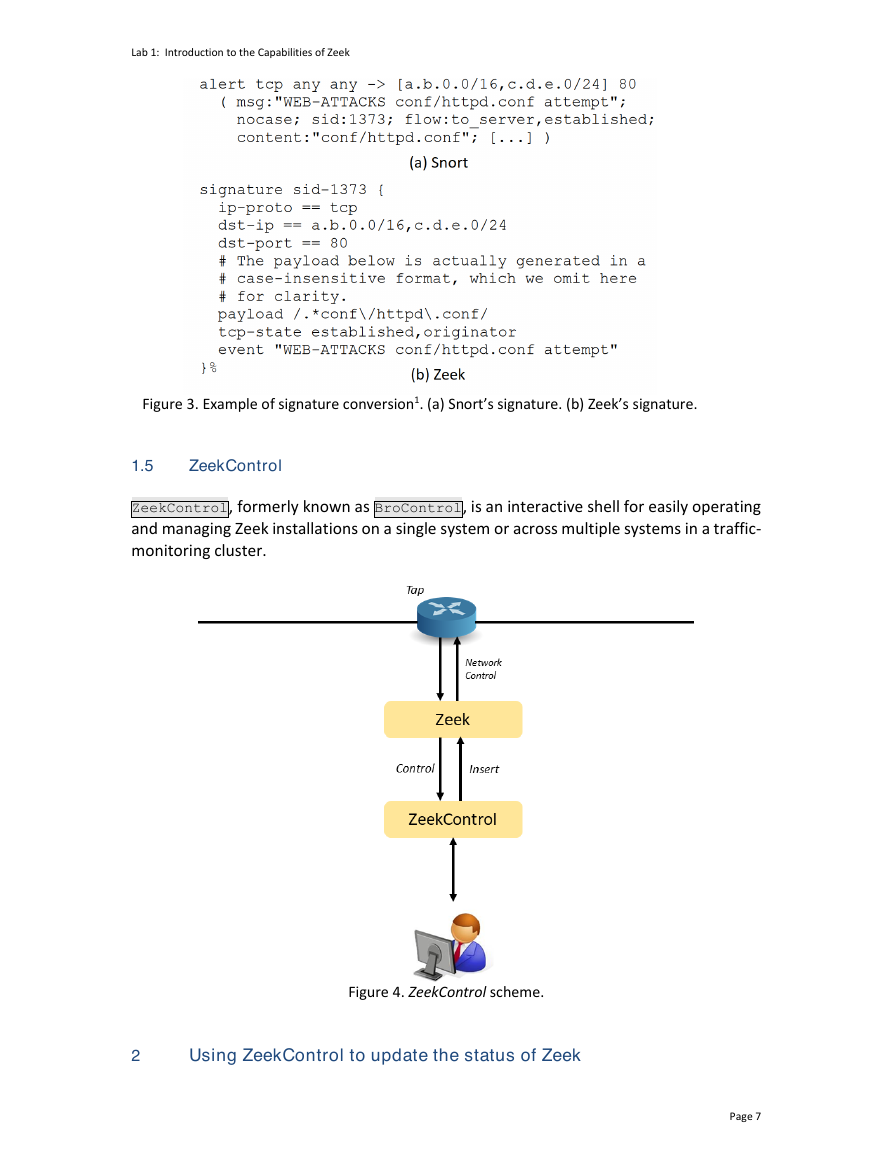
A well-known IDS system is Snort; conversely, Zeek’s general approach to intrusion
detection has a much broader scope than traditional signature-matching, yet still contains
a signature engine providing a functionality that is similar to that of other systems.
Furthermore, while Zeek implements its own flexible signature language, there exists a
converter which directly translates Snort’s signatures into Zeek’s syntax, as shown below:
Zeek analyzers
Signatures
Page 6
�
Lab 1: Introduction to the Capabilities of Zeek
Figure 3. Example of signature conversion1. (a) Snort’s signature. (b) Zeek’s signature.
ZeekControl
1.5
ZeekControl, formerly known as BroControl, is an interactive shell for easily operating
and managing Zeek installations on a single system or across multiple systems in a traffic-
monitoring cluster.
Figure 4. ZeekControl scheme.
Using ZeekControl to update the status of Zeek
Page 7
2
�
Lab 1: Introduction to the Capabilities of Zeek
Step 1. From the top of the screen, click on the Client button as shown below to enter the
Client machine.
Step 2. The Client machine will now open, and the desktop will be displayed. On the left
side of the screen, click on the LXTerminal icon as shown below.
Step 3. Using the Terminal, input the following command to enter the ZeekControl
directory. To type capital letters, it is recommended to hold the Shift key while typing
rather than using the Caps key.
cd $ZEEK_INSTALL/bin/
The active directory will change, as seen on the second line of the Terminal. Note that
$ZEEK_INSTALL variable was substituted by its value (/usr/local/zeek) listed in Table 2.
Step 4. Use the following command to view the contents of the active directory.
ls
The directory contents will be displayed. The green file name portrays an executable file.
Step 5. Use the following command to launch the ZeekControl tool. When prompted
for a password, type password and hit Enter.
Page 8
�












 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc