An Introduction to programming the TPM
TSS / Trousers basics
Johns Hopkins University Applied Physics Laboratory
David Challener
1
�
Table of Contents
Getting the machine set up………………………………………………………….
3
Includes……………………………………………………………………………… 5
Error reporting……………………………………………………………………...
6
Preamble…………………………………………………………………………….. 7
Postlude – Cleanup…………………………………………………………………. 8
Memory handling…………………………………………………………………… 9
Authorization……………………………………………………………………….. 11
Keys…………………………………………………………………………………. 15
Binding data ………………………………………………………………………. 25
Sealing data………………………………………………………………………… 29
Signing……………………………………………………………………………… 33
NVRAM…………………………………………………………………………….. 37
PCRs………………………………………………………………………………… 43
RNG…………………………………………………………………………………. 52
HASH……………………………………………………………………………….. 54
Owner evict keys …………………………………………………………………….56
Scenario………………………………………………………………………………59
2
�
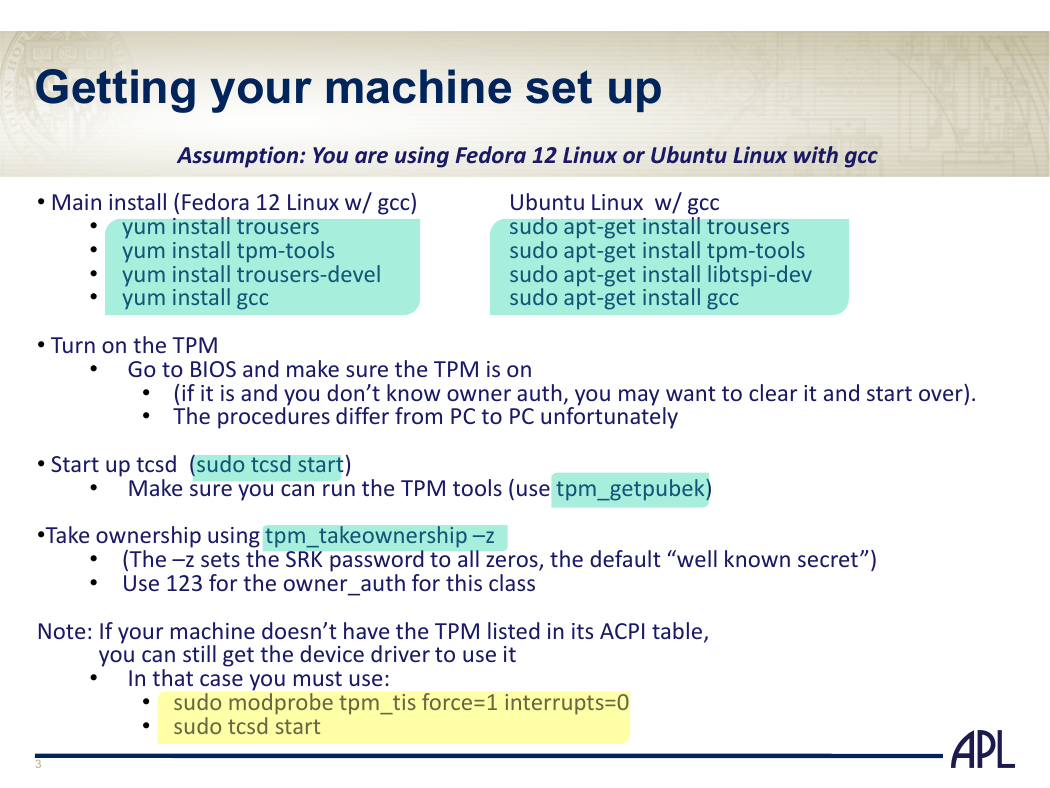
Getting your machine set up
Assumption: You are using Fedora 12 Linux or Ubuntu Linux with gcc
• Main install (Fedora 12 Linux w/ gcc)
•
•
•
•
yum install trousers
yum install tpm-tools
yum install trousers-devel
yum install gcc
Ubuntu Linux w/ gcc
sudo apt-get install trousers
sudo apt-get install tpm-tools
sudo apt-get install libtspi-dev
sudo apt-get install gcc
• Turn on the TPM
• Go to BIOS and make sure the TPM is on
(if it is and you don’t know owner auth, you may want to clear it and start over).
•
• The procedures differ from PC to PC unfortunately
• Start up tcsd (sudo tcsd start)
• Make sure you can run the TPM tools (use tpm_getpubek)
•Take ownership using tpm_takeownership –z
(The –z sets the SRK password to all zeros, the default “well known secret”)
•
• Use 123 for the owner_auth for this class
Note: If your machine doesn’t have the TPM listed in its ACPI table,
you can still get the device driver to use it
In that case you must use:
•
•
sudo modprobe tpm_tis force=1 interrupts=0
sudo tcsd start
•
3
�
Comment: Sample code
• The Trousers test suite exercises each command at
• As a result, sample code using each command is
least once.
available
• http://sourceforge.net/projects/trousers/files/
– Download TSS API Test Suite
4
�
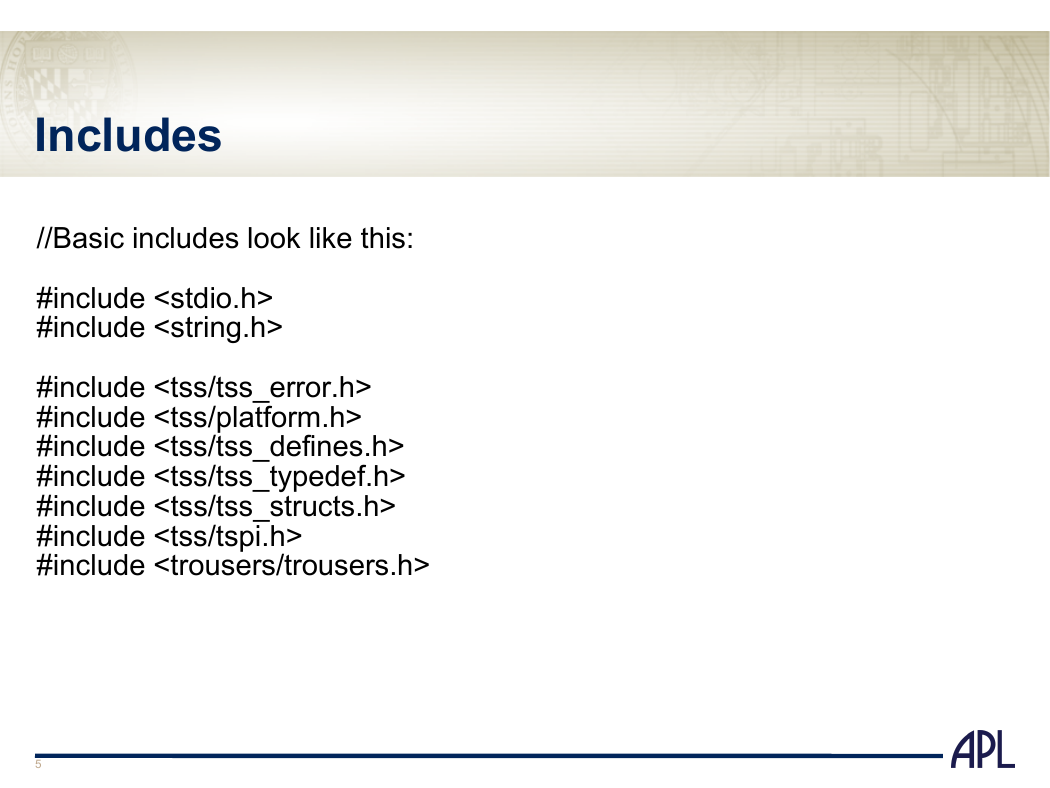
Includes
//Basic includes look like this:
#include
#include
#include
#include
#include
#include
#include
#include
#include
5
�
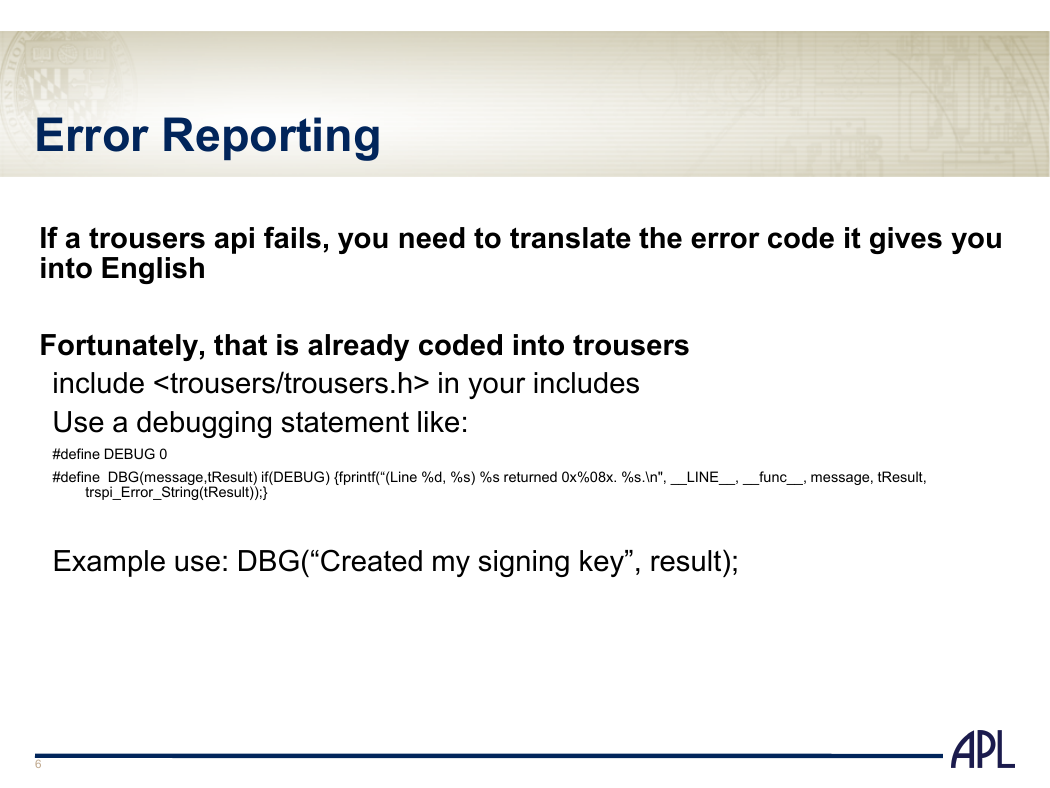
Error Reporting
If a trousers api fails, you need to translate the error code it gives you
into English
Fortunately, that is already coded into trousers
include in your includes
Use a debugging statement like:
#define DEBUG 0
#define DBG(message,tResult) if(DEBUG) {fprintf(“(Line %d, %s) %s returned 0x%08x. %s.\n", __LINE__, __func__, message, tResult,
trspi_Error_String(tResult));}
Example use: DBG(“Created my signing key”, result);
6
�
Preamble (in virtually every program)
int main(int argc, char **argv)
{
TSS_HCONTEXT
TSS_HTPM
TSS_RESULT
TSS_HKEY
TSS_HPOLICY
TSS_UUID
BYTE
memset(wks,0,20);
hContext=0;
hTPM = 0;
result;
hSRK = 0;
hSRKPolicy=0;
SRK_UUID = TSS_UUID_SRK;
wks[20]; // Place to put the well known secret
// Set wks to the well known secret of 20 bytes of all zeros
// Pick the TPM you are talking to in this case the system TPM (which you connect to with “NULL”)
result =Tspi_Context_Create(&hContext);
result=Tspi_Context_Connect(hContext, NULL);
// Get the TPM handle
DBG(" Create a Context\n",result);
DBG(" Connect to TPM\n“, result);
result=Tspi_Context_GetTpmObject(hContext, &hTPM);
DBG(" GetTPM Handle\n“,result); //
Get the SRK handle
result=Tspi_Context_LoadKeyByUUID(hContext, TSS_PS_TYPE_SYSTEM, SRK_UUID, &hSRK);
DBG(" Tspi_Context_Connect\n“,result);
//Get the SRK policy
result=Tspi_GetPolicyObject(hSRK, TSS_POLICY_USAGE, &hSRKPolicy);
DBG(" Get TPM Policy\n“ ,result; );
// Then we set the SRK policy to be the well known secret
result=Tspi_Policy_SetSecret(hSRKPolicy,TSS_SECRET_MODE_SHA1,20, wks); // Note: TSS_SECRET_MODE_SHA1 says “Don’t hash this. Just use the 20 bytes
as is.
DBG(" Tspi_Policy_Set_Secret\n“ ,result);
7
�
Cleanup (at end of every program)
/* Clean up */
Tspi_Context_Close (h objects you have created);
Tspi_Context_FreeMemory(hContext, NULL);
// this frees memory that was automatically allocated for you
Tspi_Context_Close(hContext);
return 0;
}
gcc file –o file.exe -ltspi -Wall
8
�












 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc