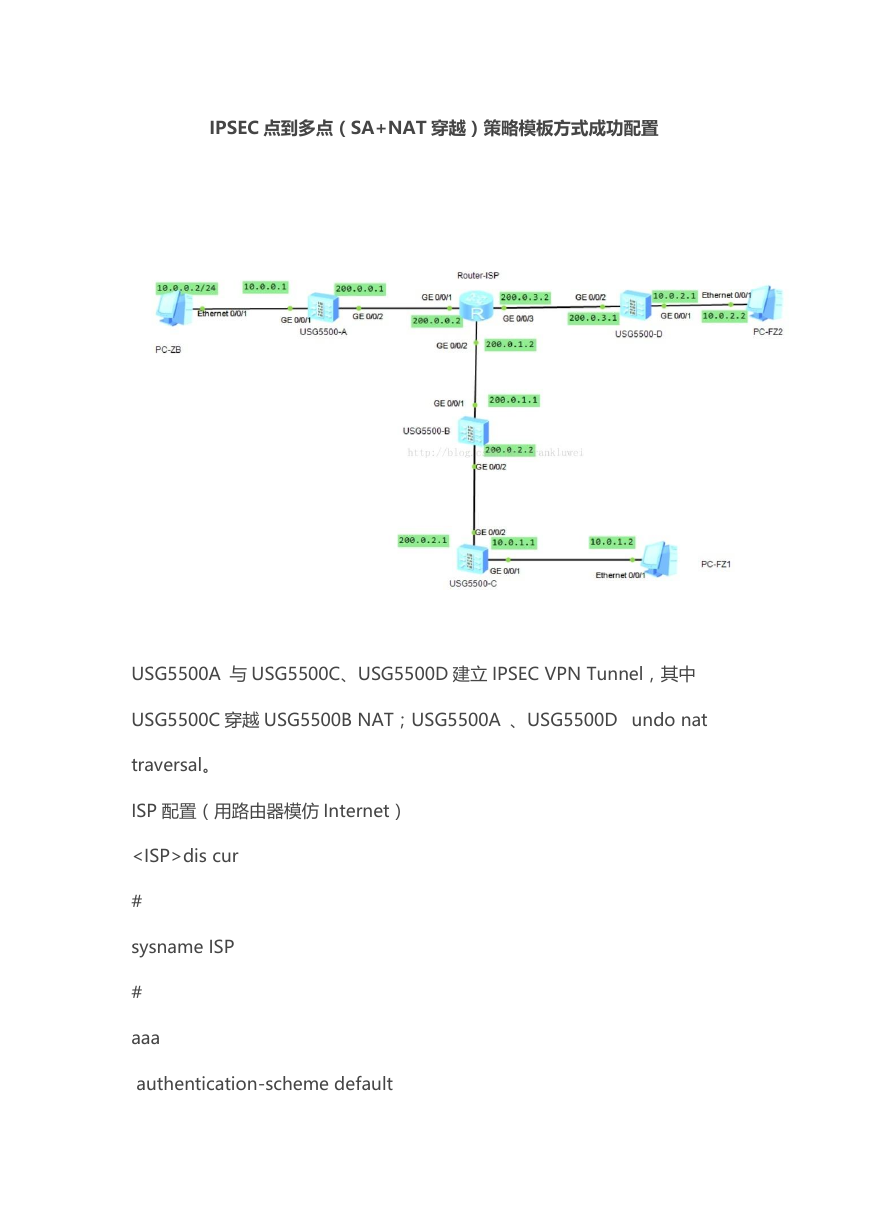
IPSEC 点到多点(SA+NAT 穿越)策略模板方式成功配置
USG5500A 与 USG5500C、USG5500D 建立 IPSEC VPN Tunnel,其中
USG5500C 穿越 USG5500B NAT;USG5500A 、USG5500D undo nat
traversal。
ISP 配置(用路由器模仿 Internet)
dis cur
#
sysname ISP
#
aaa
authentication-scheme default
�
authorization-scheme default
accounting-scheme default
domain default
domain default_admin
local-user admin password cipherxUpvP4d*n"ECB7Ie7'/)`WB#
local-user admin service-type http
#
firewall zone permit
#
firewall zone Local
priority 16
#
interface Ethernet0/0/0
#
interface Ethernet0/0/1
#
interface Serial0/0/0
link-protocol ppp
#
interface Serial0/0/1
link-protocol ppp
#
�
interface Serial0/0/2
link-protocol ppp
#
interface Serial0/0/3
link-protocol ppp
#
interface GigabitEthernet0/0/0
#
interface GigabitEthernet0/0/1
ipaddress 200.0.0.2 255.255.255.0
#
interface GigabitEthernet0/0/2
ipaddress 200.0.1.2 255.255.255.0
#
interface GigabitEthernet0/0/3
ip address 200.0.3.2 255.255.255.0
#
wlan
#
interface NULL0
#
ospf 1
�
import-route direct
import-route static
area0.0.0.0
network 200.0.0.0 0.0.0.255
network 200.0.1.0 0.0.0.255
network 200.0.3.0 0.0.0.255
#
ip route-static 10.0.0.0 255.255.255.0200.0.0.1
ip route-static 10.0.1.0 255.255.255.0200.0.1.1
ip route-static 10.0.2.0 255.255.255.0200.0.3.1
#
user-interface con 0
user-interface vty 0 4
user-interface vty 16 20
#
return
总部防火墙 FWA 配置
dis cur
19:37:14 2014/12/10
#
stp region-configuration
�
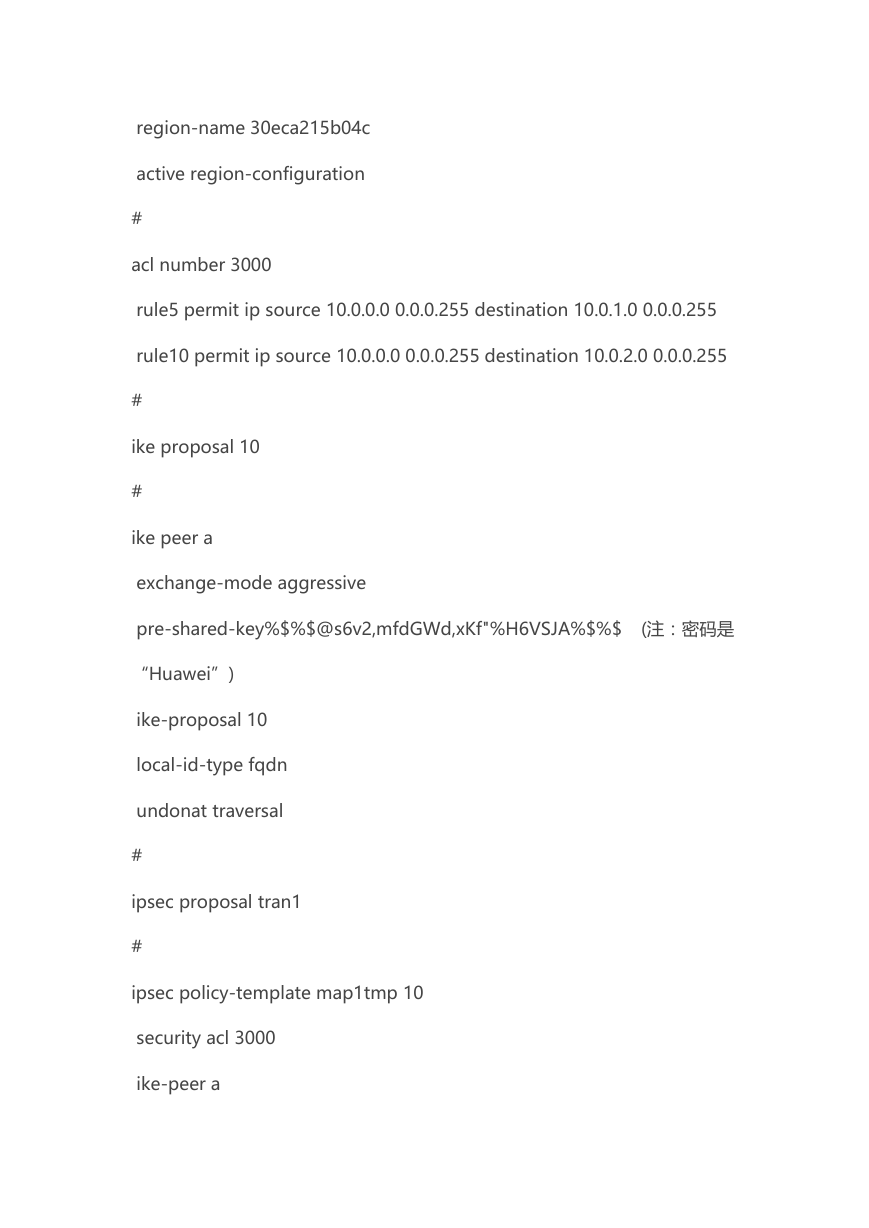
region-name 30eca215b04c
active region-configuration
#
acl number 3000
rule5 permit ip source 10.0.0.0 0.0.0.255 destination 10.0.1.0 0.0.0.255
rule10 permit ip source 10.0.0.0 0.0.0.255 destination 10.0.2.0 0.0.0.255
#
ike proposal 10
#
ike peer a
exchange-mode aggressive
pre-shared-key%$%$@s6v2,mfdGWd,xKf"%H6VSJA%$%$ (注:密码是
“Huawei”)
ike-proposal 10
local-id-type fqdn
undonat traversal
#
ipsec proposal tran1
#
ipsec policy-template map1tmp 10
security acl 3000
ike-peer a
�
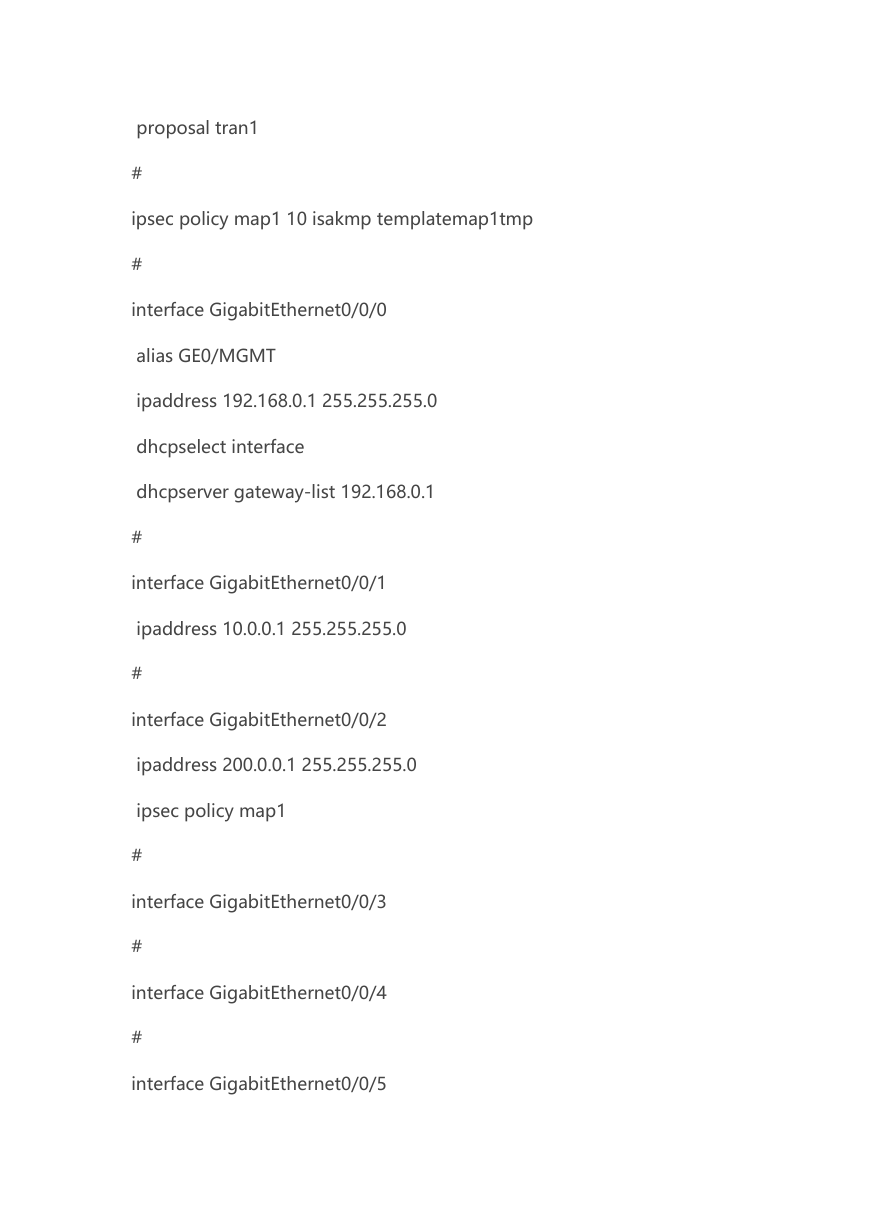
proposal tran1
#
ipsec policy map1 10 isakmp templatemap1tmp
#
interface GigabitEthernet0/0/0
alias GE0/MGMT
ipaddress 192.168.0.1 255.255.255.0
dhcpselect interface
dhcpserver gateway-list 192.168.0.1
#
interface GigabitEthernet0/0/1
ipaddress 10.0.0.1 255.255.255.0
#
interface GigabitEthernet0/0/2
ipaddress 200.0.0.1 255.255.255.0
ipsec policy map1
#
interface GigabitEthernet0/0/3
#
interface GigabitEthernet0/0/4
#
interface GigabitEthernet0/0/5
�
#
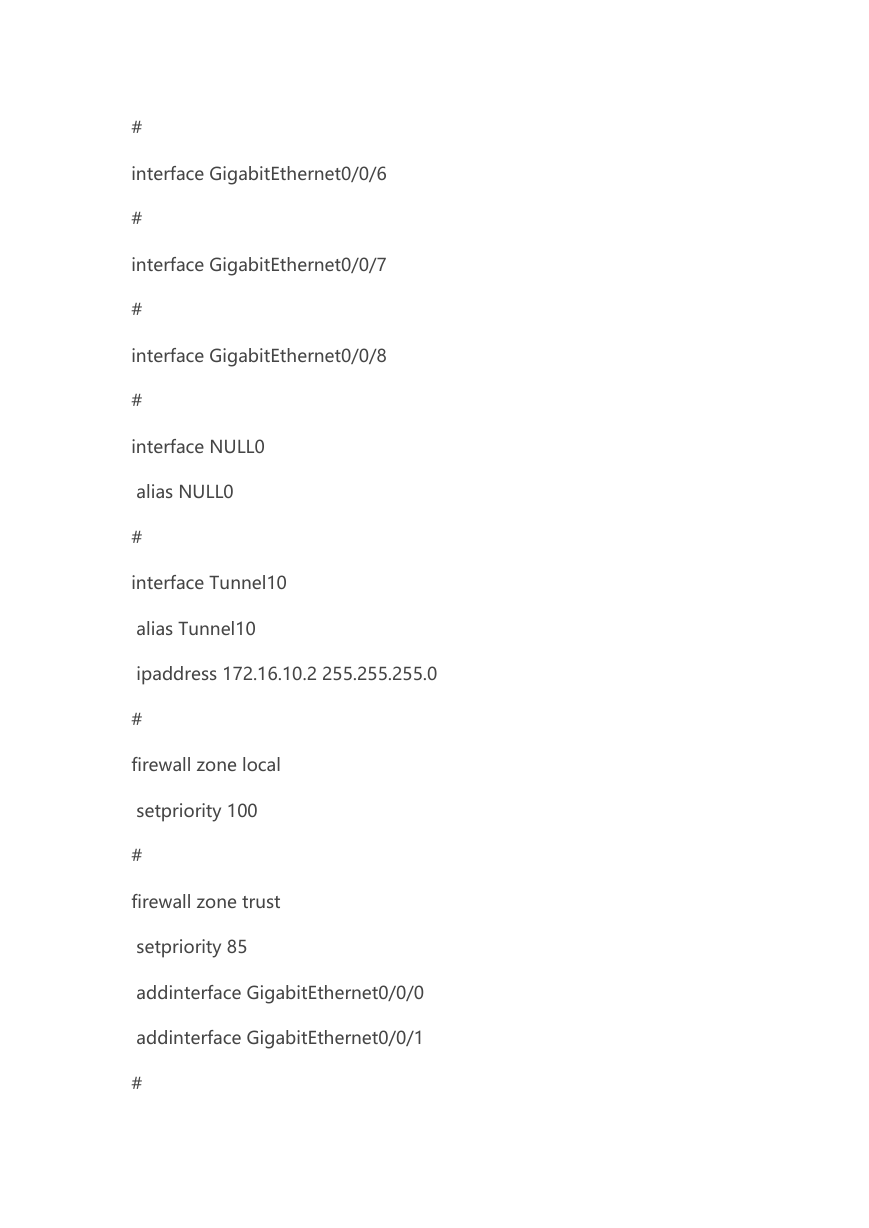
interface GigabitEthernet0/0/6
#
interface GigabitEthernet0/0/7
#
interface GigabitEthernet0/0/8
#
interface NULL0
alias NULL0
#
interface Tunnel10
alias Tunnel10
ipaddress 172.16.10.2 255.255.255.0
#
firewall zone local
setpriority 100
#
firewall zone trust
setpriority 85
addinterface GigabitEthernet0/0/0
addinterface GigabitEthernet0/0/1
#
�
firewall zone untrust
setpriority 5
addinterface GigabitEthernet0/0/2
#
firewall zone dmz
setpriority 50
#
aaa
local-user admin password
cipher%$%$etpe4:p1;Lk,9p9YtPDPOg^U%$%$
local-user admin service-type web terminaltelnet
local-user admin level 15
authentication-scheme default
#
authorization-scheme default
#
accounting-scheme default
#
domain default
#
#
ospf 1
�









 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc