IT
认证电子书
认证电子书
质 量 更 高
服 务 更 好
半年免费升级服务
http://www.itrenzheng.com
�
The safer , easier way to help you pass any IT exams.
Exam : NSE4_FGT-6.2
Title :
Fortinet NSE 4 - FortiOS 6.2
Version : V9.02
1 / 46
�
The safer , easier way to help you pass any IT exams.
1.NGFW mode allows policy-based configuration for most inspection rules.
Which security profile’s configuration does not change when you enable policy-based inspection?
A. Web filtering
B. Antivirus
C. Web proxy
D. Application control
Answer: B
2.Which statements about antivirus scanning mode are true? (Choose two.)
A. In proxy-based inspection mode antivirus buffers the whole file for scarring before sending it to the
client.
B. In flow-based inspection mode, you can use the CLI to configure antivirus profiles to use protocol
option profiles.
C. In proxy-based inspection mode, if a virus is detected, a replacement message may not be displayed
immediately.
D. In quick scan mode, you can configure antivirus profiles to use any of the available signature data
bases.
Answer: A B
Explanation:
A: Buffers the whole file, packets sent to the client after scan finishes-
B: When the antivirus profile is operating in flow-based inspection mode, two scanning mode options are
available: full scan mode and quick scan mode.(Normal extended, or extreme-depending on what is
configured in the CLI).
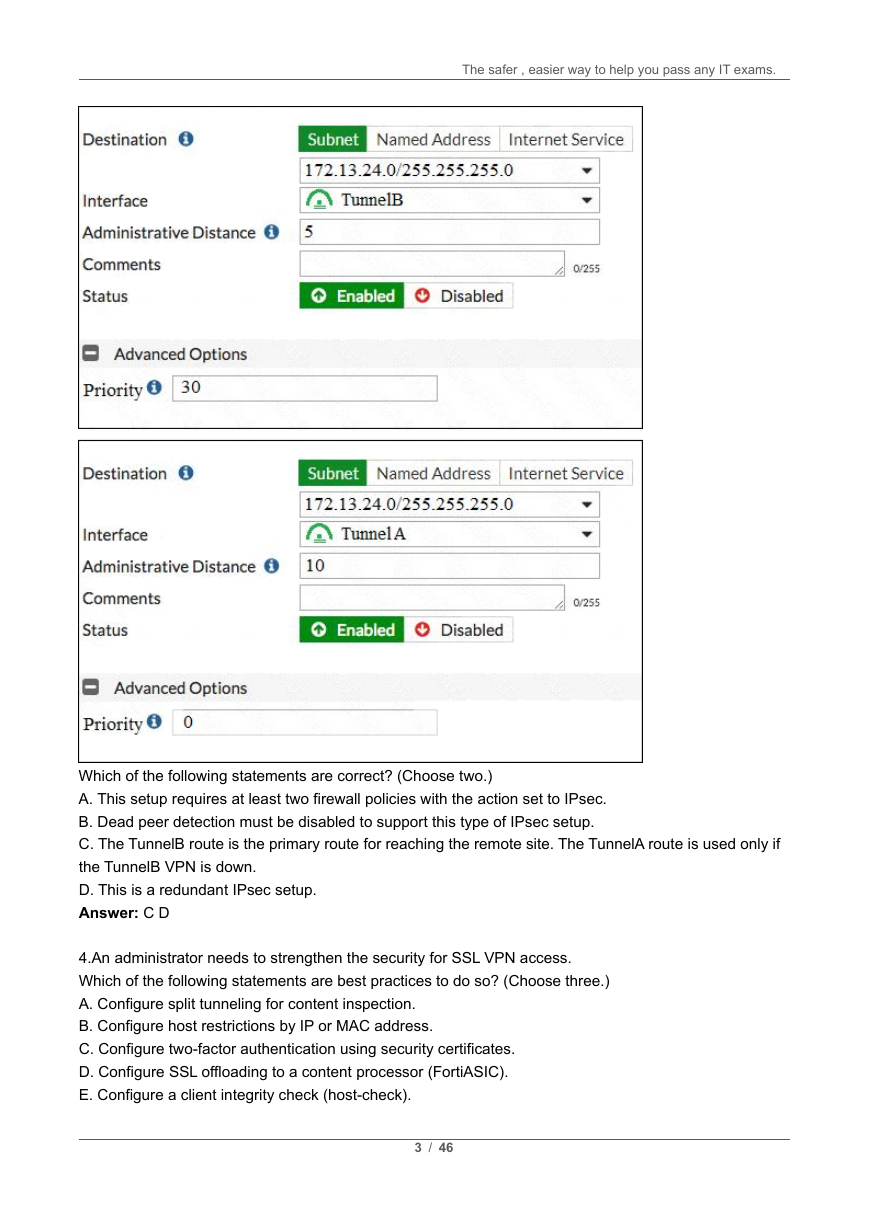
3.View the exhibit.
2 / 46
�
The safer , easier way to help you pass any IT exams.
Which of the following statements are correct? (Choose two.)
A. This setup requires at least two firewall policies with the action set to IPsec.
B. Dead peer detection must be disabled to support this type of IPsec setup.
C. The TunnelB route is the primary route for reaching the remote site. The TunnelA route is used only if
the TunnelB VPN is down.
D. This is a redundant IPsec setup.
Answer: C D
4.An administrator needs to strengthen the security for SSL VPN access.
Which of the following statements are best practices to do so? (Choose three.)
A. Configure split tunneling for content inspection.
B. Configure host restrictions by IP or MAC address.
C. Configure two-factor authentication using security certificates.
D. Configure SSL offloading to a content processor (FortiASIC).
E. Configure a client integrity check (host-check).
3 / 46
�
The safer , easier way to help you pass any IT exams.
Answer: B C E
5.Which statements about DNS filter profiles are true? (Choose two.)
A. They can inspect HTTP traffic.
B. They can redirect blocked requests to a specific portal.
C. They can block DNS requests to known botnet command and control servers.
D. They must be applied in firewall policies with SSL inspection enabled.
Answer: B C
6.Why does FortiGate keep TCP sessions in the session table for some seconds even after both sides
(client and server) have terminated the session?
A. To remove the NAT operation.
B. To generate logs
C. To finish any inspection operations.
D. To allow for out-of-order packets that could arrive after the FIN/ACK packets.
Answer: D
7.Which of the following statements are true when using WPAD with the DHCP discovery method?
(Choose two.)
A. If the DHCP method fails, browsers will try the DNS method.
B. The browser needs to be preconfigured with the DHCP server’s IP address.
C. The browser sends a DHCPONFORM request to the DHCP server.
D. The DHCP server provides the PAC file for download.
Answer: A C
8.Examine this output from a debug flow:
Which statements about the output are correct? (Choose two.)
A. FortiGate received a TCP SYN/ACK packet.
B. The source IP address of the packet was translated to 10.0.1.10.
C. FortiGate routed the packet through port 3.
D. The packet was allowed by the firewall policy with the ID 00007fc0.
Answer: A C
9.Which one of the following processes is involved in updating IPS from FortiGuard?
A. FortiGate IPS update requests are sent using UDP port 443.
B. Protocol decoder update requests are sent to service.fortiguard.net.
C. IPS signature update requests are sent to update.fortiguard.net.
D. IPS engine updates can only be obtained using push updates.
Answer: C
4 / 46
�
The safer , easier way to help you pass any IT exams.
Explanation:
https://help.fortinet.com/fos50hlp/54/Content/FortiOS/fortigate-ports-and-protocols-54/07-FortiGuard.htm
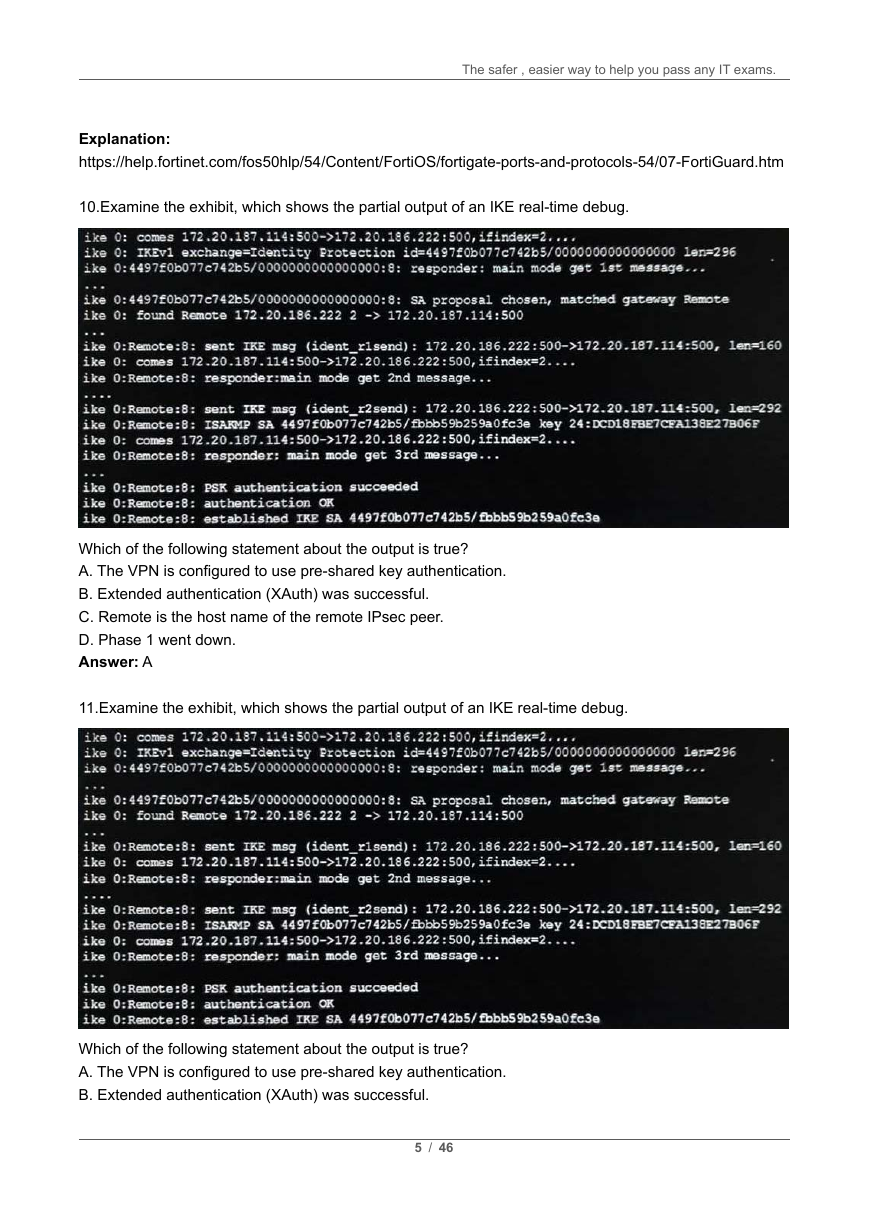
10.Examine the exhibit, which shows the partial output of an IKE real-time debug.
Which of the following statement about the output is true?
A. The VPN is configured to use pre-shared key authentication.
B. Extended authentication (XAuth) was successful.
C. Remote is the host name of the remote IPsec peer.
D. Phase 1 went down.
Answer: A
11.Examine the exhibit, which shows the partial output of an IKE real-time debug.
Which of the following statement about the output is true?
A. The VPN is configured to use pre-shared key authentication.
B. Extended authentication (XAuth) was successful.
5 / 46
�
The safer , easier way to help you pass any IT exams.
C. Remote is the host name of the remote IPsec peer.
D. Phase 1 went down.
Answer: A
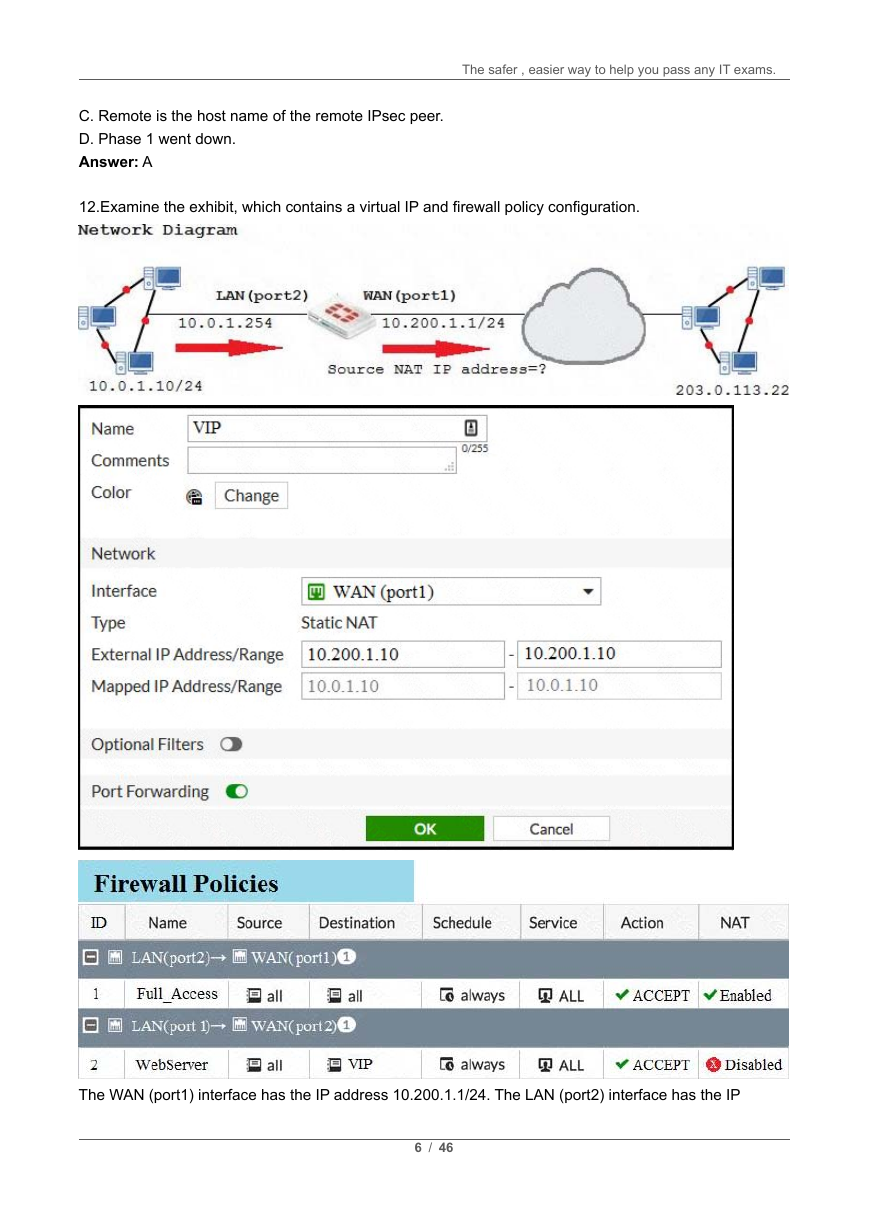
12.Examine the exhibit, which contains a virtual IP and firewall policy configuration.
The WAN (port1) interface has the IP address 10.200.1.1/24. The LAN (port2) interface has the IP
6 / 46
�
The safer , easier way to help you pass any IT exams.
address 10.0.1.254/24.
The first firewall policy has NAT enabled on the outgoing interface address. The second firewall policy is
configured with a VIP as the destination address.
Which IP address will be used to source NAT the Internet traffic coming from a workstation with the IP
address 10.0.1.10/24?
A. 10.200.1.10
B. Any available IP address in the WAN (port1) subnet 10.200.1.0/24
C. 10.200.1.1
D. 10.0.1.254
Answer: D
Explanation:
https://help.fortinet.com/fos50hlp/54/Content/FortiOS/fortigate-firewall-52/Firewall%20Objects/Virtual%20
IPs.htm
13.What information is flushed when the chunk-size value is changed in the config dlp settings?
A. The database for DLP document fingerprinting
B. The supported file types in the DLP filters
C. The archived files and messages
D. The file name patterns in the DLP filters
Answer: A
Explanation:
https://help.fortinet.com/cli/fos50hlp/56/Content/FortiOS/fortiOS-cli-ref-56/config/dlp/settings.htm
14.Which of the following statements about backing up logs from the CLI and downloading logs from the
GUI are true? (Choose two.)
A. Log downloads from the GUI are limited to the current filter view
B. Log backups from the CLI cannot be restored to another FortiGate.
C. Log backups from the CLI can be configured to upload to FTP as a scheduled time
D. Log downloads from the GUI are stored as LZ4 compressed files.
Answer: B C
15.Examine the IPS sensor and DoS policy configuration shown in the exhibit, then answer the question
below.
7 / 46
�













 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc