Introduction
Purpose
Background
Scope & Application
Related Documents
Assumptions
Architecture and Concepts
Glossary
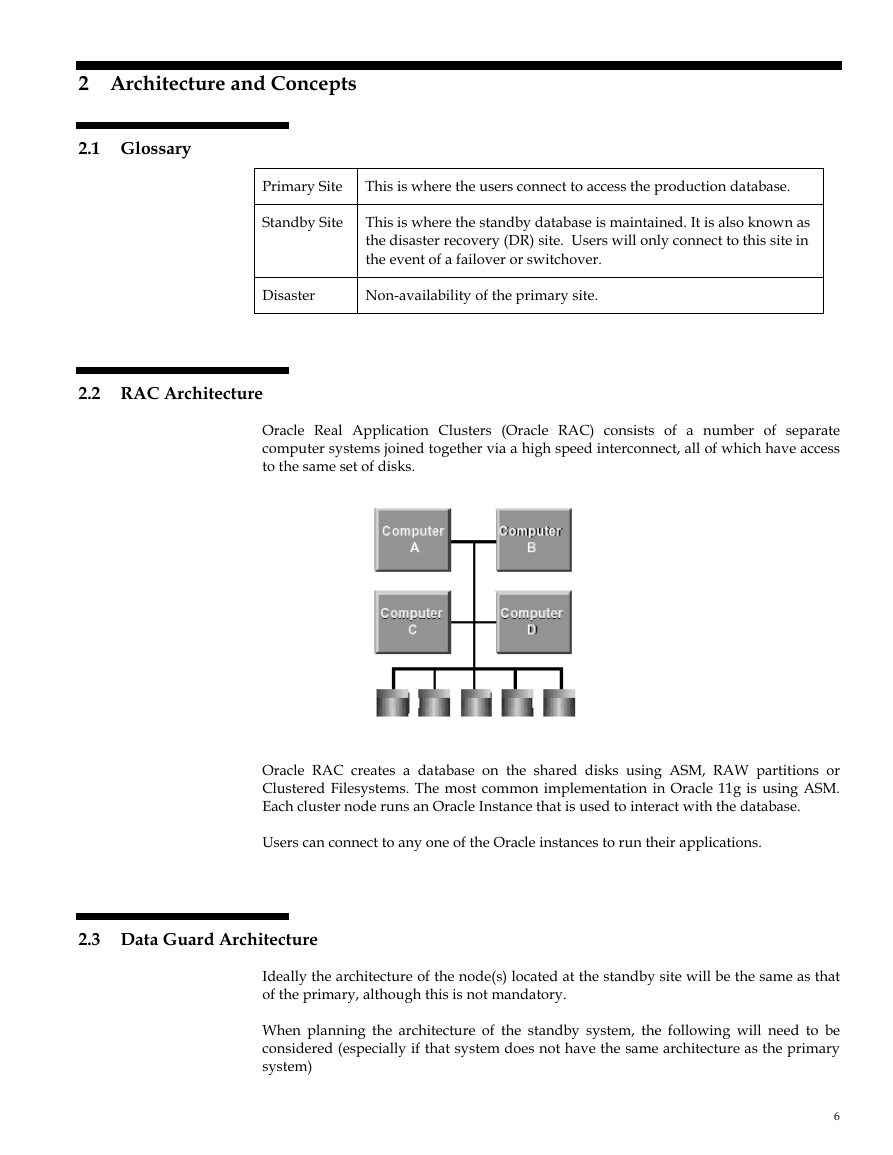
RAC Architecture
Data Guard Architecture
Network
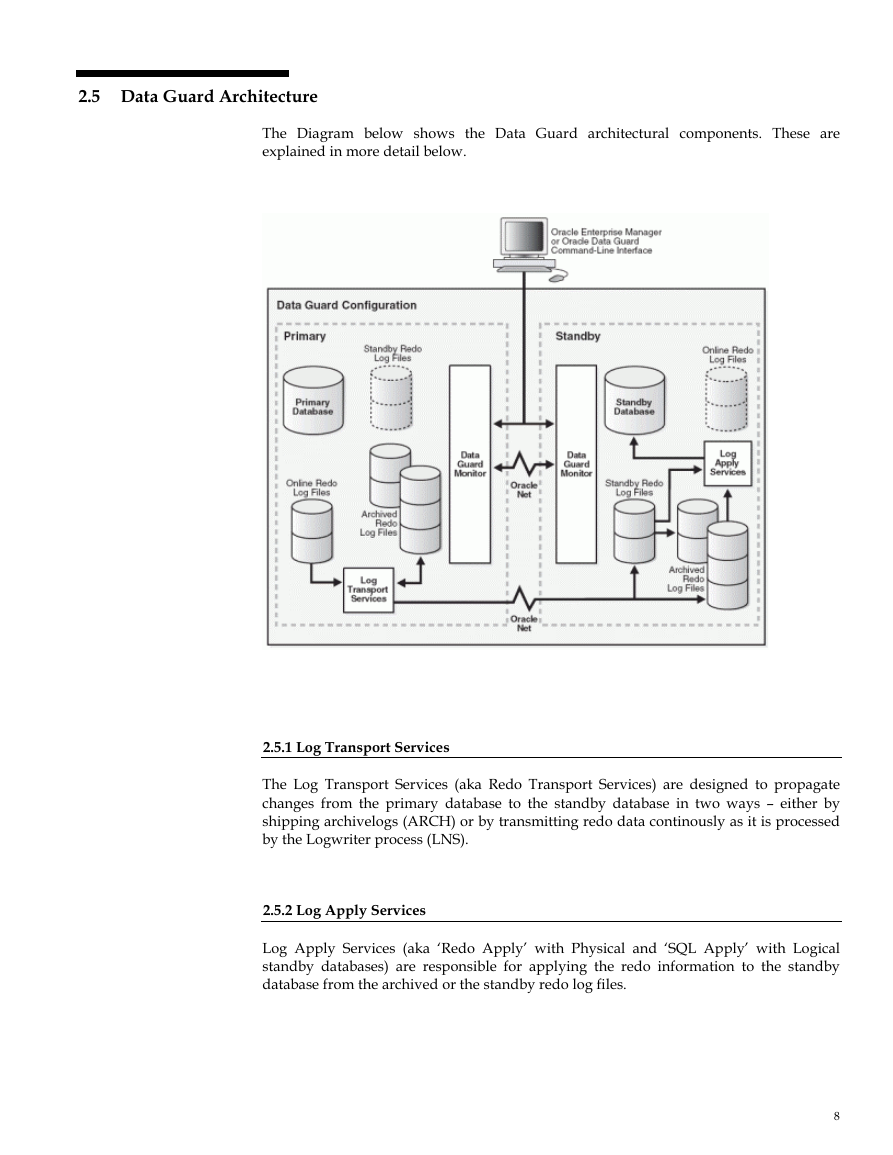
Data Guard Architecture
Log Transport Services
Log Apply Services
Data Guard Broker
How it Works
Archived Log Shipping
Standby Redo logs
Levels of Protection
Maximum Protection
Maximum Availability
Maximum Performance
Pros and Cons
Prerequisites
Hardware
Network
Software
Real Application Clusters
ASM
Raw Devices
Non Raw Devices
Creating a Data Guard Environment
Assumptions
Procedure - Summary
Creating the RAC Standby Database
Configure Primary and Standby sites
Install Oracle Software on each site.
Server Names / VIPs
Configure Oracle Networking
Configure Listener on Each Site
Static Registration
Sample Listener.ora
Configure TNS entries on each site.
Sample tnsnames.ora (europa)
Configure ASM on each Site
Prepare Primary Database for Duplication.
Primary Site Preparation
Standby Site Preparation
Duplicate the Primary database.
Create an SPFILE for the Standby Database
Get location of the Control File
Create a textual initialisation file
Edit the init.ora
Create SPFILE
Create Pointer File
Create secondary control files
Cluster-enable the Standby Database
Ensure Server Side Load Balancing is configured
Register the Database with CRS
Test
Temporary Files
Create Standby Redo Logs
Configuring Data Guard using SQL Plus
Introduction
Configure the Standby Database
Configure the Primary Database
Set the Protection Mode
Enable Redo Transport & Redo Apply
Standby Site
Primary Site:
Configuring Data Guard using the Data Guard Broker
Introduction
Broker Configuration Files
Enabling the Broker
Creating a Broker Configuration
Enable the Broker Configuration
Broker Customisation
Maximum Availability/Protection
Monitoring
Introduction
Log Files
Fixed Views
Management
Switchover
Switchover using SQL Plus
Switchover using Data Guard Broker
Failover
Failover using SQL Plus
Failover using Data Guard Broker
Forced failover
Forced Failover using Data Guard Broker
Opening a Standby Database Read Only
Real Time Apply / Real Time Query
Appendix A – Using RMAN to create the Sta�
Assumptions
RMAN Backup
New Backup
Existing Backup
Creating the Standby Database
Prerequisites
Procedure
Appendix B – Further reading
Oracle Manuals
Metalink














 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc