Start Secure. Stay Secure.®
CIS Controls™
�
April 1, 2019
This work is licensed under a Creative Commons Attribution-Non Commercial-No Derivatives 4.0
International Public License (the link can be found at https://creativecommons.org/licenses/by-
nc-nd/4.0/legalcode). To further clarify the Creative Commons license related to the CIS ControlsTM
content, you are authorized to copy and redistribute the content as a framework for use by
you, within your organization and outside of your organization, for non-commercial purposes
only, provided that (i) appropriate credit is given to CIS, and (ii) a link to the license is provided.
Additionally, if you remix, transform, or build upon the CIS Controls, you may not distribute the
modified materials. Users of the CIS Controls framework are also required to refer to (http://
www.cisecurity.org/controls/) when referring to the CIS Controls in order to ensure that users are
employing the most up-to-date guidance. Commercial use of the CIS Controls is subject to the
prior approval of CIS® (Center for Internet Security, Inc.®).
Acknowledgments
CIS® (Center for Internet Security, Inc.®) would like to thank the many
security experts who volunteer their time and talent to support the
CIS ControlsTM and other CIS work. CIS products represent the effort
of a veritable army of volunteers from across the industry, generously
giving their time and talent in the name of a more secure online
experience for everyone.
�
Contents
1
2
3
3
4
6
6
Introduction
Why the CIS Controls Work:
Methodology and Contributors
How to Get Started
This Version of the CIS Controls
Implementation Groups
Other Resources
Structure of the
CIS Controls Document
7
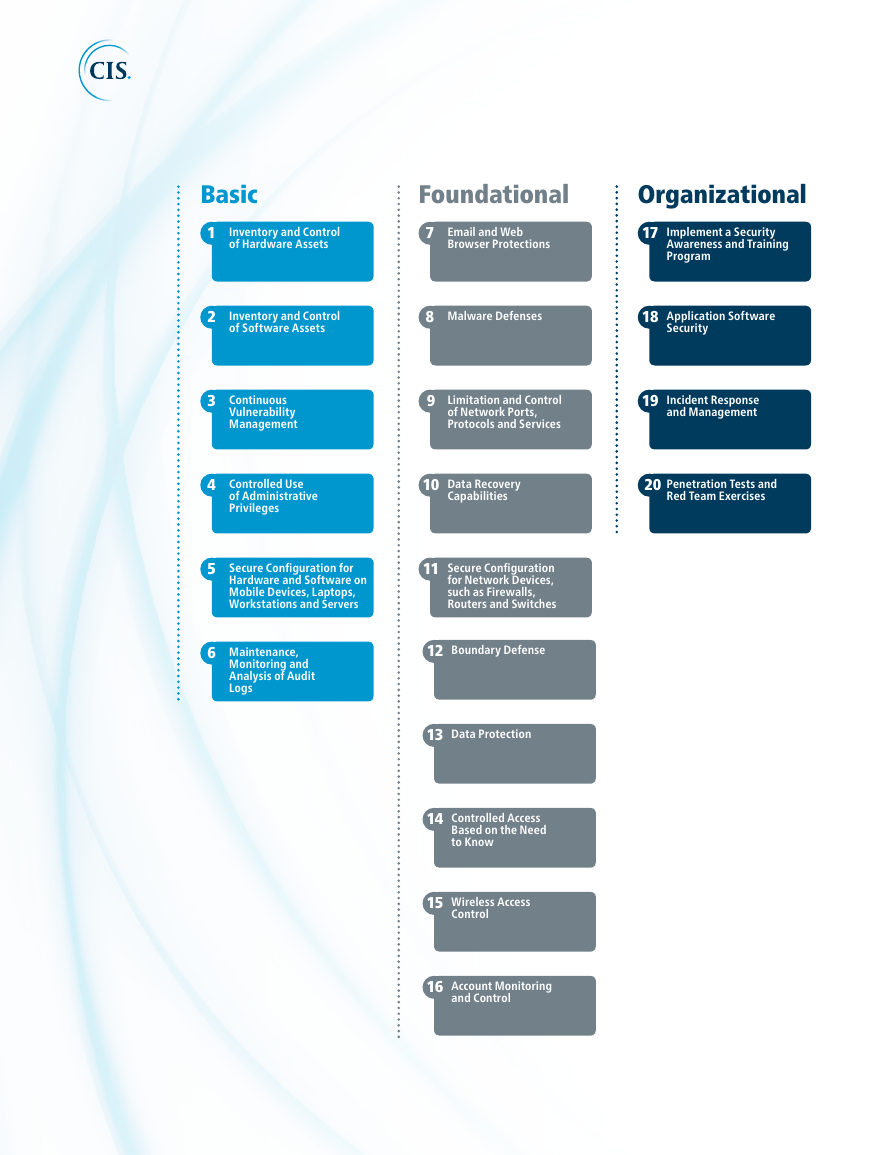
CIS Controls 1 – 20
71
Closing Notes
�
Basic
1
Inventory and Control
of Hardware Assets
Foundational
7
Email and Web
Browser Protections
Organizational
17
Implement a Security
Awareness and Training
Program
2
3
4
5
6
Inventory and Control
of Software Assets
8
Malware Defenses
18
Application Software
Security
Continuous
Vulnerability
Management
Controlled Use
of Administrative
Privileges
9
Limitation and Control
of Network Ports,
Protocols and Services
19
Incident Response
and Management
10
Data Recovery
Capabilities
20
Penetration Tests and
Red Team Exercises
Secure Configuration for
Hardware and Software on
Mobile Devices, Laptops,
Workstations and Servers
11
Secure Configuration
for Network Devices,
such as Firewalls,
Routers and Switches
Maintenance,
Monitoring and
Analysis of Audit
Logs
12
Boundary Defense
13
Data Protection
14
Controlled Access
Based on the Need
to Know
15
Wireless Access
Control
16
Account Monitoring
and Control
�
1
Introduction
The CIS Controls™ are a prioritized set of actions that collectively form a defense-in-depth set
of best practices that mitigate the most common attacks against systems and networks. The
CIS Controls are developed by a community of IT experts who apply their first-hand experience
as cyber defenders to create these globally accepted security best practices. The experts who
develop the CIS Controls come from a wide range of sectors including retail, manufacturing,
healthcare, education, government, defense, and others.
We are at a fascinating point in the evolution of what we now call cyber defense. Massive data
losses, theft of intellectual property, credit card breaches, identity theft, threats to our privacy,
denial of service – these have become a way of life for all of us in cyberspace.
As defenders we have access to an extraordinary array of security tools and technology,
security standards, training and classes, certifications, vulnerability databases, guidance, best
practices, catalogs of security controls, and countless security checklists, benchmarks, and
recommendations. To help us understand the threat, we have seen the emergence of threat
information feeds, reports, tools, alert services, standards, and threat sharing frameworks. To top
it all off, we are surrounded by security requirements, risk management frameworks, compliance
regimes, regulatory mandates, and so forth. There is no shortage of information available to
security practitioners on what they should do to secure their infrastructure.
But all of this technology, information, and oversight has become a veritable “Fog of More” –
competing options, priorities, opinions, and claims that can paralyze or distract an enterprise
from vital action. Business complexity is growing, dependencies are expanding, users are
becoming more mobile, and the threats are evolving. New technology brings us great benefits,
but it also means that our data and applications are now distributed across multiple locations,
many of which are not within our organization’s infrastructure. In this complex, interconnected
world, no enterprise can think of its security as a standalone problem.
So how can we as a community – the community-at-large, as well as within industries, sectors,
partnerships, and coalitions – band together to establish priority of action, support each other,
and keep our knowledge and technology current in the face of a rapidly evolving problem and
an apparently infinite number of possible solutions? What are the most critical areas we need
to address and how should an enterprise take the first step to mature their risk management
program? Rather than chase every new exceptional threat and neglect the fundamentals, how
can we get on track with a roadmap of fundamentals, and guidance to measure and improve?
Which defensive steps have the greatest value?
These are the kinds of issues that led to and now drive the CIS Controls. They started as a grass-
roots activity to cut through the “Fog of More” and focus on the most fundamental and valuable
actions that every enterprise should take. And value here is determined by knowledge and data –
the ability to prevent, alert, and respond to the attacks that are plaguing enterprises today.
Led by CIS®, the CIS Controls have been matured by an international community of individuals and
institutions that:
• Share insight into attacks and attackers, identify root causes, and
translate that into classes of defensive action;
• Document stories of adoption and share tools to solve problems;
• Track the evolution of threats, the capabilities of adversaries, and
current vectors of intrusions;
• Map the CIS Controls to regulatory and compliance frameworks and
bring collective priority and focus to them;
• Share tools, working aids, and translations; and
• Identify common problems (like initial assessment and
implementation roadmaps) and solve them as a community.
V7.1�
2
These activities ensure that the CIS Controls are not just another list of good things to do, but
a prioritized, highly focused set of actions that have a community support network to make
them implementable, usable, scalable, and compliant with all industry or government security
requirements.
Why the CIS Controls Work: Methodology and Contributors
The CIS Controls are informed by actual attacks and effective defenses and reflect the combined
knowledge of experts from every part of the ecosystem (companies, governments, individuals);
with every role (threat responders and analysts, technologists, vulnerability-finders, tool makers,
solution providers, defenders, users, policy-makers, auditors, etc.); and within many sectors
(government, power, defense, finance, transportation, academia, consulting, security, IT) who
The Center for Internet Security, Inc.
(CIS) is a 501(c)(3) nonprofit
organization whose mission is to
identify, develop, validate, promote,
and sustain best practices in cyber
security; deliver world-class cyber
security solutions to prevent and
rapidly respond to cyber incidents;
and build and lead communities
to enable an environment of trust
in cyberspace.
For additional information, go to
https://www.cisecurity.org/
have banded together to create, adopt, and support the Controls.
Top experts from organizations pooled their extensive first-hand
knowledge from defending against actual cyber-attacks to evolve the
consensus list of Controls, representing the best defensive techniques
to prevent or track them. This ensures that the CIS Controls are the
most effective and specific set of technical measures available to detect,
prevent, respond, and mitigate damage from the most common to the
most advanced of those attacks.
The CIS Controls are not limited to blocking the initial compromise of
systems, but also address detecting already-compromised machines
and preventing or disrupting attackers’ follow-on actions. The defenses
identified through these Controls deal with reducing the initial attack
surface by hardening device configurations, identifying compromised
machines to address long-term threats inside an organization’s
network, disrupting attackers’ command-and-control of implanted
malicious code, and establishing an adaptive, continuous defense, and
response capability that can be maintained and improved.
The five critical tenets of an effective cyber defense system as reflected
in the CIS Controls are:
Offense informs defense: Use knowledge of actual attacks that have
compromised systems to provide the foundation to continually learn
from these events to build effective, practical defenses. Include only
those controls that can be shown to stop known real-world attacks.
Prioritization: Invest first in Controls that will provide the greatest risk
reduction and protection against the most dangerous threat actors
and that can be feasibly implemented in your computing environment.
The CIS Implementation Groups discussed below are a great place for
organizations to start identifying relevant Sub-Controls.
Measurements and Metrics: Establish common metrics to provide a
shared language for executives, IT specialists, auditors, and security
officials to measure the effectiveness of security measures within
an organization so that required adjustments can be identified and
implemented quickly.
Continuous diagnostics and mitigation: Carry out continuous
measurement to test and validate the effectiveness of current security
measures and to help drive the priority of next steps.
Automation: Automate defenses so that organizations can achieve
reliable, scalable, and continuous measurements of their adherence to
the Controls and related metrics.
V7.1�
3
How to Get Started
The CIS Controls are a relatively small number of prioritized, well-vetted, and supported security
actions that organizations can take to assess and improve their current security state. They also
change the discussion from “What should my enterprise do?” to “What should we ALL be doing?”
to improve security across a broad scale.
But this is not a one-size-fits-all solution, in either content or priority. You must still understand
what is critical to your business, data, systems, networks, and infrastructures, and you must
consider the adversarial actions that could impact your ability to be successful in the business or
operation. Even a relatively small number of Controls cannot be executed all at once, so you will
need to develop a plan for assessment, implementation, and process management.
This Version of the CIS Controls
With the release of Version 6 of the CIS Controls (in October 2015), we put in place the means to
better understand the needs of adopters, gather ongoing feedback, and understand how the
security industry supports the CIS Controls. We used this to drive the evolution of Version 7 and
also Version 7.1.
In addition to the critical tenets of cyber defense previously mentioned, we also tried to ensure
that every CIS Control is clear, concise, and current. While there’s no magic bullet when defining
security controls, we believe this version sets the foundation for much more straightforward and
manageable implementation, measurement, and automation.
At CIS, we listen carefully to all of your feedback and ideas for the CIS Controls. In particular,
many of you have asked for more help with prioritizing and phasing in the CIS Controls for
your cybersecurity program. This topic deserved a substantial treatment and resulted in the
Implementation Groups discussed below. As such, the following principles were used to drive the
V7.1 update.
• Reassess the prioritization scheme for the CIS Controls down to the
Sub-Controls level, given the evolving threat landscape and resource
constraints;
• Fix minor typos and errors;
• Enhance the clarity and readability of the CIS Controls and Sub-Controls; and
• Refrain from adding or subtracting from the technical content, or “spirit”,
of a CIS Control or Sub-Control.
We also provide detailed change information to minimize the work for enterprises that choose
to migrate from Version 7 to Version 7.1. You can also assist by sending your feedback and ideas
on prioritization efforts or other matters to controlsinfo@cisecurity.org, or by joining the CIS
WorkBench Community (https://workbench.cisecurity.org/communities/71).
V7.1�
4
Implementation Groups
Historically the CIS Controls utilized the order of the Controls as a means of focusing an
organization’s cybersecurity activities, resulting in a subset of the first six CIS Controls referred
to as cyber hygiene. However, many of the practices found within the CIS cyber hygiene control
set can be difficult for organizations with limited resources to implement. This highlighted a
need for a collection of best practices focused on balancing resource constraints and effective
risk mitigation. As a result, CIS recommends the following new guidance to prioritize CIS Control
utilization, known as CIS Controls Implementation Groups.
The CIS Controls Implementation Groups (IGs) are self-assessed categories for organizations
based on relevant cybersecurity attributes. Each IG identifies a subset of the CIS Controls that the
community has broadly assessed to be reasonable for an organization with a similar risk profile
and resources to strive to implement. These IGs represent a horizontal cut across the CIS Controls
tailored to different types of enterprises. Each IG builds upon the previous one. As such, IG2
includes IG1, and IG3 includes all of the CIS Sub-Controls in IG1 and IG2. A resource constrained
organization may have to protect critical data and, therefore, implement Sub-Controls in a higher
IG. Ultimately, an organization implementing the CIS Sub-Controls defined for their IG is moving
toward a standard duty of care as described in the CIS Risk Assessment Method (CIS RAM). CIS
RAM is a free resource available at https://learn.cisecurity.org/cis-ram.
CIS recommends that organizations prioritize their implementation of the Controls by following
the IGs. Organizations should implement Sub-Controls in IG1, followed by IG2 and then IG3.
The Sub-Controls contained within IG1 are essential to success. Implementation of IG1 should
be considered among the very first things to be done as part of a cybersecurity program. CIS
refers to IG1 as “Cyber Hygiene” – the essential protections that must be put into place to defend
against common attacks. Organizations are encouraged to classify themselves as belonging to
one of three Implementation Groups. For instance:
• A family-owned business with ~10 employees may self-classify as IG1;
• A regional organization providing a service may classify itself as IG2; or
• A large corporation with thousands of employees may be labeled IG3.
Once a classification is determined, organizations can then focus on implementing the CIS
Sub-Controls found within that IG. The criteria organizations use to identify their organizational
category are based on the characteristics described below:
1. Data sensitivity and criticality of services offered by the organization.
Organizations providing services that must be available for any reason (e.g.,
public safety, critical infrastructure) or working with data that must be protected
under a further restricted set of requirements (e.g., federal legislation) need to
implement more advanced cybersecurity controls than those that do not.
2. Expected level of technical expertise exhibited by staff or on contract.
Cybersecurity knowledge and experience are difficult to obtain, yet are
necessary to implement many of the detailed cybersecurity mitigations outlined
within the CIS Controls. Many of the CIS Controls require minimum core IT
competencies, whereas others necessitate in-depth cybersecurity skills and
knowledge to successfully implement.
3. Resources available and dedicated toward cybersecurity activities.
Time, money, and personnel are all necessary in order to implement many of the
best practices contained within the CIS Controls. Enterprises that can dedicate
these resources toward cybersecurity can mount a more sophisticated defense
against today’s adversaries. While there are open-source tools available that
assist an organization’s implementation, they may come at a cost of additional
management and deployment overhead that needs to be recognized and taken
into consideration.
Note that organizations are encouraged to perform a risk assessment using a methodology
such as CIS RAM. This will definitively inform which CIS Sub-Controls should be implemented for
an organization. The IGs are not absolute; they are intended to provide a rough measure that
organizations can use to better prioritize cybersecurity efforts. The following further defines and
describes each Group.
V7.1�















 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc