Computer Networks 54 (2010) 2787–2805
Contents lists available at ScienceDirect
Computer Networks
j o u r n a l h o m e p a g e : w w w . e l s e v i e r . c o m / l o c a t e / c o m n e t
The Internet of Things: A survey
Luigi Atzori a, Antonio Iera b, Giacomo Morabito c,*
a DIEE, University of Cagliari, Italy
b University ‘‘Mediterranea” of Reggio Calabria, Italy
c University of Catania, Italy
a r t i c l e
i n f o
a b s t r a c t
Article history:
Received 10 December 2009
Received in revised form 27 April 2010
Accepted 14 May 2010
Available online 1 June 2010
Responsible Editor: E. Ekici
Keywords:
Internet of Things
Pervasive computing
RFID systems
1. Introduction
This paper addresses the Internet of Things. Main enabling factor of this promising para-
digm is the integration of several technologies and communications solutions. Identifica-
tion and tracking technologies, wired and wireless sensor and actuator networks,
enhanced communication protocols (shared with the Next Generation Internet), and dis-
tributed intelligence for smart objects are just the most relevant. As one can easily imagine,
any serious contribution to the advance of the Internet of Things must necessarily be the
result of synergetic activities conducted in different fields of knowledge, such as telecom-
munications, informatics, electronics and social science. In such a complex scenario, this
survey is directed to those who want to approach this complex discipline and contribute
to its development. Different visions of this Internet of Things paradigm are reported
and enabling technologies reviewed. What emerges is that still major issues shall be faced
by the research community. The most relevant among them are addressed in details.
Ó 2010 Elsevier B.V. All rights reserved.
The Internet of Things (IoT) is a novel paradigm that is
rapidly gaining ground in the scenario of modern wireless
telecommunications. The basic idea of this concept is the
pervasive presence around us of a variety of things or
objects – such as Radio-Frequency IDentification (RFID)
tags, sensors, actuators, mobile phones, etc. – which,
through unique addressing schemes, are able to interact
with each other and cooperate with their neighbors to
reach common goals [1].
Unquestionably, the main strength of the IoT idea is the
high impact it will have on several aspects of everyday-life
and behavior of potential users. From the point of view of a
private user, the most obvious effects of the IoT introduc-
tion will be visible in both working and domestic fields.
In this context, domotics, assisted living, e-health, en-
hanced learning are only a few examples of possible appli-
* Corresponding author. Tel.: +39 095 7382355; fax: +39 095 7382397.
E-mail addresses: l.atzori@diee.unica.it (L. Atzori), antonio.iera@unirc.
it (A. Iera), giacomo.morabito@diit.unict.it (G. Morabito).
1389-1286/$ - see front matter Ó 2010 Elsevier B.V. All rights reserved.
doi:10.1016/j.comnet.2010.05.010
cation scenarios in which the new paradigm will play a
leading role in the near future. Similarly, from the perspec-
tive of business users, the most apparent consequences
will be equally visible in fields such as, automation and
industrial manufacturing, logistics, business/process man-
agement, intelligent transportation of people and goods.
By starting from the considerations above, it should not
be surprising that IoT is included by the US National Intel-
ligence Council in the list of six ‘‘Disruptive Civil Technol-
ogies” with potential impacts on US national power [2].
NIC foresees that ‘‘by 2025 Internet nodes may reside in
everyday things – food packages, furniture, paper docu-
ments, and more”. It highlights future opportunities that
will arise, starting from the idea that ‘‘popular demand
combined with technology advances could drive wide-
spread diffusion of an Internet of Things (IoT) that could,
like the present Internet, contribute invaluably to eco-
nomic development”. The possible threats deriving from
a widespread adoption of such a technology are also
stressed. Indeed, it is emphasized that ‘‘to the extent that
everyday objects become information security risks, the
IoT could distribute those risks far more widely than the
Internet has to date”.
�
2788
L. Atzori et al. / Computer Networks 54 (2010) 2787–2805
Actually, many challenging issues still need to be ad-
dressed and both technological as well as social knots have
to be untied before the IoT idea being widely accepted.
Central issues are making a full interoperability of inter-
connected devices possible, providing them with an always
higher degree of smartness by enabling their adaptation and
autonomous behavior, while guaranteeing trust, privacy,
and security. Also, the IoT idea poses several new problems
concerning the networking aspects. In fact, the things com-
posing the IoT will be characterized by low resources in
terms of both computation and energy capacity. Accord-
ingly, the proposed solutions need to pay special attention
to resource efficiency besides the obvious scalability
problems.
Several industrial, standardization and research bodies
are currently involved in the activity of development of
solutions to fulfill the highlighted technological require-
ments. This survey gives a picture of the current state of
the art on the IoT. More specifically, it:
� provides the readers with a description of the different
visions of the Internet of Things paradigm coming from
different scientific communities;
� reviews the enabling technologies and illustrates which
are the major benefits of spread of this paradigm in
everyday-life;
� offers an analysis of the major research issues the scien-
tific community still has to face.
The main objective is to give the reader the opportunity of
understanding what has been done (protocols, algorithms,
proposed solutions) and what
to be
addressed, as well as which are the enabling factors of this
evolutionary process and what are its weaknesses and risk
factors.
remains
still
The remainder of the paper is organized as follows. In
Section 2, we introduce and compare the different visions
of the IoT paradigm, which are available from the litera-
ture. The IoT main enabling technologies are the subject
of Section 3, while the description of the principal applica-
tions, which in the future will benefit from the full deploy-
ment of the IoT idea, are addressed in Section 4. Section 5
gives a glance at the open issues on which research should
focus more, by stressing topics such as addressing, net-
working, security, privacy, and standardization efforts.
Conclusions and future research hints are given in Section
6.
2. One paradigm, many visions
Manifold definitions of Internet of Things traceable with-
in the research community testify to the strong interest in
the IoT issue and to the vivacity of the debates on it. By
browsing the literature, an interested reader might experi-
ence a real difficulty in understanding what IoT really
means, which basic ideas stand behind this concept, and
which social, economical and technical implications the
full deployment of IoT will have.
The reason of today apparent fuzziness around this
term is a consequence of the name ‘‘Internet of Things”
itself, which syntactically is composed of two terms. The
first one pushes towards a network oriented vision of IoT,
while the second one moves the focus on generic ‘‘objects”
to be integrated into a common framework.
Differences, sometimes substantial, in the IoT visions
raise from the fact that stakeholders, business alliances, re-
search and standardization bodies start approaching the is-
sue from either an ‘‘Internet oriented” or a ‘‘Things
oriented” perspective, depending on their specific inter-
ests, finalities and backgrounds.
It shall not be forgotten, anyway, that the words ‘‘Inter-
net” and ‘‘Things”, when put together, assume a meaning
which introduces a disruptive level of innovation into to-
day ICT world. In fact, ‘‘Internet of Things” semantically
means ‘‘a world-wide network of interconnected objects
uniquely addressable, based on standard communication
protocols” [3]. This implies a huge number of (heteroge-
neous) objects involved in the process.
The object unique addressing and the representation
and storing of the exchanged information become the most
challenging issues, bringing directly to a third, ‘‘Semantic
oriented”, perspective of IoT.
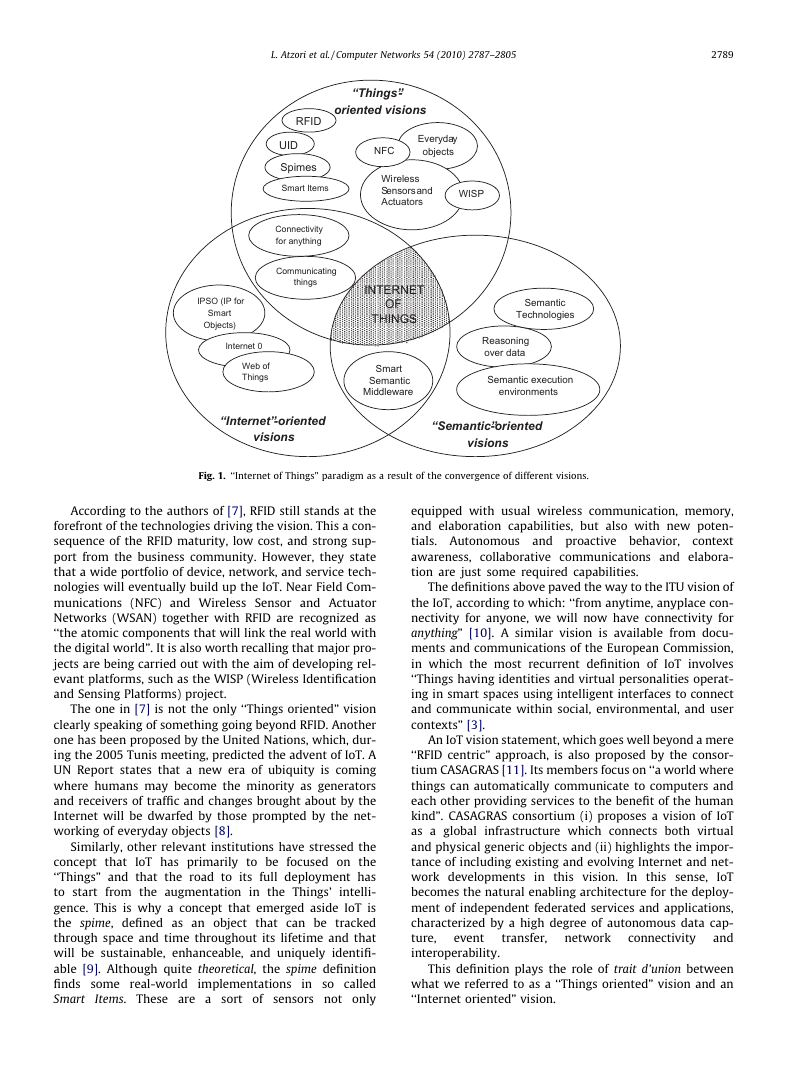
In Fig. 1, the main concepts, technologies and standards
are highlighted and classified with reference to the IoT vi-
sion/s they contribute to characterize best. From such an
illustration, it clearly appears that the IoT paradigm shall
be the result of the convergence of the three main visions
addressed above.
The very first definition of IoT derives from a ‘‘Things
oriented” perspective; the considered things were very
simple items: Radio-Frequency IDentification (RFID) tags.
The terms ‘‘Internet of Things” is, in fact, attributed to
The Auto-ID Labs [4], a world-wide network of academic
research laboratories in the field of networked RFID and
emerging sensing technologies. These institutions, since
their establishment, have been targeted to architect the
IoT, together with EPCglobal [5]. Their focus has primar-
ily been on the development of the Electronic Product
Code™ (EPC) to support the spread use of RFID in
world-wide modern trading networks, and to create
the industry-driven global standards for the EPCglobal
Network™. These standards are mainly designed to im-
prove object visibility (i.e. the traceability of an object
and the awareness of its status, current location, etc.).
This is undoubtedly a key component of the path to
the full deployment of the IoT vision; but it is not the
only one.
In a broader sense, IoT cannot be just a global EPC sys-
tem in which the only objects are RFIDs; they are just a
part of the full story! And the same holds for the alterna-
tive Unique/Universal/Ubiquitous IDentifier (uID) architec-
ture [6], whose main idea is still the development of
(middleware based) solutions for a global visibility of ob-
jects in an IoT vision. It is the authors’ opinion that, starting
from RFID centric solutions may be positive as the main as-
pects stressed by RFID technology, namely item traceabil-
ity and addressability, shall definitely be addressed also
by the IoT. Notwithstanding, alternative, and somehow
more complete, IoT visions recognize that the term IoT im-
plies a much wider vision than the idea of a mere objects
identification.
�
L. Atzori et al. / Computer Networks 54 (2010) 2787–2805
2789
RFID
UID
Spimes
Smart Items
“Things”-
oriented visions
NFC
Everyday
objects
Wireless
Sensorsand
Actuators
WISP
Connectivity
for anything
Communicating
things
IPSO (IP for
Smart
Objects)
Internet 0
Web of
Things
INTERNET
OF
THINGS
Smart
Semantic
Middleware
Semantic
Technologies
Reasoning
over data
Semantic execution
environments
“Internet”-oriented
visions
“Semantic”-oriented
visions
Fig. 1. ‘‘Internet of Things” paradigm as a result of the convergence of different visions.
According to the authors of [7], RFID still stands at the
forefront of the technologies driving the vision. This a con-
sequence of the RFID maturity, low cost, and strong sup-
port from the business community. However, they state
that a wide portfolio of device, network, and service tech-
nologies will eventually build up the IoT. Near Field Com-
munications (NFC) and Wireless Sensor and Actuator
Networks (WSAN) together with RFID are recognized as
‘‘the atomic components that will link the real world with
the digital world”. It is also worth recalling that major pro-
jects are being carried out with the aim of developing rel-
evant platforms, such as the WISP (Wireless Identification
and Sensing Platforms) project.
The one in [7] is not the only ‘‘Things oriented” vision
clearly speaking of something going beyond RFID. Another
one has been proposed by the United Nations, which, dur-
ing the 2005 Tunis meeting, predicted the advent of IoT. A
UN Report states that a new era of ubiquity is coming
where humans may become the minority as generators
and receivers of traffic and changes brought about by the
Internet will be dwarfed by those prompted by the net-
working of everyday objects [8].
Similarly, other relevant institutions have stressed the
concept that IoT has primarily to be focused on the
‘‘Things” and that the road to its full deployment has
to start from the augmentation in the Things’
intelli-
gence. This is why a concept that emerged aside IoT is
the spime, defined as an object that can be tracked
through space and time throughout its lifetime and that
will be sustainable, enhanceable, and uniquely identifi-
able [9]. Although quite theoretical, the spime definition
finds some real-world implementations in so called
Items. These are a sort of sensors not only
Smart
equipped with usual wireless communication, memory,
and elaboration capabilities, but also with new poten-
tials. Autonomous
context
awareness, collaborative communications and elabora-
tion are just some required capabilities.
and proactive behavior,
The definitions above paved the way to the ITU vision of
the IoT, according to which: ‘‘from anytime, anyplace con-
nectivity for anyone, we will now have connectivity for
anything” [10]. A similar vision is available from docu-
ments and communications of the European Commission,
in which the most recurrent definition of IoT involves
‘‘Things having identities and virtual personalities operat-
ing in smart spaces using intelligent interfaces to connect
and communicate within social, environmental, and user
contexts” [3].
An IoT vision statement, which goes well beyond a mere
‘‘RFID centric” approach, is also proposed by the consor-
tium CASAGRAS [11]. Its members focus on ‘‘a world where
things can automatically communicate to computers and
each other providing services to the benefit of the human
kind”. CASAGRAS consortium (i) proposes a vision of IoT
as a global
infrastructure which connects both virtual
and physical generic objects and (ii) highlights the impor-
tance of including existing and evolving Internet and net-
work developments in this vision.
IoT
becomes the natural enabling architecture for the deploy-
ment of independent federated services and applications,
characterized by a high degree of autonomous data cap-
ture,
and
interoperability.
In this sense,
transfer,
network
connectivity
event
This definition plays the role of trait d’union between
what we referred to as a ‘‘Things oriented” vision and an
‘‘Internet oriented” vision.
�
2790
L. Atzori et al. / Computer Networks 54 (2010) 2787–2805
Within the latter category falls the IoT vision of the IPSO
(IP for Smart Objects) Alliance [11], a forum formed in Sep-
tember 2008 by 25 founding companies to promote the
Internet Protocol as the network technology for connecting
Smart Objects around the world. According to the IPSO vi-
sion, the IP stack is a light protocol that already connects a
huge amount of communicating devices and runs on tiny
and battery operated embedded devices. This guarantees
that IP has all the qualities to make IoT a reality. By reading
IPSO whitepapers, it seems that through a wise IP adapta-
tion and by incorporating IEEE 802.15.4 into the IP archi-
tecture,
the full
deployment of the IoT paradigm will be automatically
enabled.
in the view of 6LoWPAN [12],
Internet Ø [13] follows a similar approach of reducing
the complexity of the IP stack to achieve a protocol de-
signed to route ‘‘IP over anything”. In some forums this is
looked at as the wisest way to move from the Internet of
Devices to the Internet of Things. According to both the
IPSO and Internet Ø approaches, the IoT will be deployed
by means of a sort of simplification of the current IP to
adapt it to any object and make those objects addressable
and reachable from any location.
As said before, it is worth noticing that ‘‘Semantic ori-
ented” IoT visions are available in the literature [14–17].
The idea behind them is that the number of items involved
in the Future Internet is destined to become extremely
high. Therefore, issues related to how to represent, store,
interconnect, search, and organize information generated
by the IoT will become very challenging. In this context,
semantic technologies could play a key role. In fact, these
can exploit appropriate modeling solutions for things
description, reasoning over data generated by IoT, seman-
tic execution environments and architectures that accom-
modate IoT requirements and scalable storing and
communication infrastructure [14].
A further vision correlated with the IoT is the so called
‘‘Web of Things” [18], according to which Web standards
are re-used to connect and integrate into the Web every-
day-life objects that contain an embedded device or
computer.
3. Enabling technologies
Actualization of the IoT concept into the real world is
possible through the integration of several enabling tech-
nologies. In this section we discuss the most relevant ones.
Note that it is not our purpose to provide a comprehensive
survey of each technology. Our major aim is to provide a
picture of the role they will likely play in the IoT. Interested
readers will find references to technical publications for
each specific technology.
3.1. Identification, sensing and communication technologies
‘‘Anytime, anywhere, anymedia” has been for a long
time the vision pushing forward the advances in communi-
cation technologies. In this context, wireless technologies
have played a key role and today the ratio between radios
and humans is nearing the 1 to 1 value [19].
However, the reduction in terms of size, weight, energy
consumption, and cost of the radio can take us to a new era
where the above ratio increases of orders of magnitude.
This will allow us to integrate radios in almost all objects
and thus, to add the world ‘‘anything” to the above vision,
which leads to the IoT concept.
In this context, key components of the IoT will be RFID
systems [20], which are composed of one or more reader(s)
and several RFID tags. Tags are characterized by a unique
identifier and are applied to objects (even persons or ani-
mals). Readers trigger the tag transmission by generating
an appropriate signal, which represents a query for the
possible presence of tags in the surrounding area and for
the reception of their IDs. Accordingly, RFID systems can
be used to monitor objects in real-time, without the need
of being in line-of-sight; this allows for mapping the real
world into the virtual world. Therefore, they can be used
in an incredibly wide range of application scenarios, span-
ning from logistics to e-health and security.
From a physical point of view a RFID tag is a small
microchip1 attached to an antenna (that is used for both
receiving the reader signal and transmitting the tag ID) in
a package which usually is similar to an adhesive sticker
[21]. Dimensions can be very low: Hitachi has developed a
tag with dimensions 0.4 mm � 0.4 mm � 0.15 mm.
Usually, RFID tags are passive, i.e., they do not have on-
board power supplies and harvest the energy required for
transmitting their ID from the query signal transmitted
by a RFID reader in the proximity. In fact, this signal gener-
ates a current into the tag antenna by induction and such a
current is utilized to supply the microchip which will
transmit the tag ID. Usually, the gain (power of the signal
received by the reader divided by the power of the signal
transmitted by the same reader) characterizing such sys-
tems is very low. However, thanks to the highly directive
antennas utilized by the readers, tags ID can be correctly
received within a radio range that can be as long as a
few meters. Transmission may occur in several frequency
bands spanning from low frequencies (LF) at 124–
135 kHz up to ultra high frequencies (UHF) at 860–
960 MHz that have the longest range.
Nevertheless, there are also RFID tags getting power
supply by batteries. In this case we can distinguish semi-
passive from active RFID tags. In semi-passive RFIDs batter-
ies power the microchip while receiving the signal from
the reader (the radio is powered with the energy harvested
by the reader signal). Differently, in active RFIDs the bat-
tery powers the transmission of the signal as well. Obvi-
ously the radio coverage is the highest for active tags
even if this is achieved at the expenses of higher produc-
tion costs.
Sensor networks will also play a crucial role in the IoT.
In fact, they can cooperate with RFID systems to better
track the status of things, i.e., their location, temperature,
movements, etc. As such, they can augment the awareness
of a certain environment and, thus, act as a further bridge
between physical and digital world. Usage of sensor net-
1 New RFID tags, named chipless tags, are under study which do not use
microchips so as to decrease production cost [96].
�
L. Atzori et al. / Computer Networks 54 (2010) 2787–2805
2791
works has been proposed in several application scenarios,
such as environmental monitoring, e-health, intelligent
transportation systems, military, and industrial plant
monitoring.
Sensor networks consist of a certain number (which can
be very high) of sensing nodes communicating in a wire-
less multi-hop fashion. Usually nodes report the results
of their sensing to a small number (in most cases, only
one) of special nodes called sinks. A large scientific litera-
ture has been produced on sensor networks in the recent
past, addressing several problems at all layers of the proto-
col stack [22]. Design objectives of the proposed solutions
are energy efficiency (which is the scarcest resource in
most of the scenarios involving sensor networks), scalabil-
ity (the number of nodes can be very high), reliability (the
network may be used to report urgent alarm events), and
robustness (sensor nodes are likely to be subject to failures
for several reasons).
Today, most of commercial wireless sensor network
solutions are based on the IEEE 802.15.4 standard, which
defines the physical and MAC layers for low-power, low
bit rate communications in wireless personal area net-
works (WPAN) [23]. IEEE 802.15.4 does not include speci-
fications on the higher layers of the protocol stack, which is
necessary for the seamless integration of sensor nodes into
the Internet. This is a difficult task for several reasons, the
most important are given below:
� Sensor networks may consist of a very large number of
nodes. This would result in obvious problems as today
there is a scarce availability of IP addresses.
� The largest physical layer packet in IEEE 802.15.4 has
127 bytes; the resulting maximum frame size at the
media access control layer is 102 octets, which may fur-
ther decrease based on the link layer security algorithm
utilized. Such sizes are too small when compared to
typical IP packet sizes.
� In many scenarios sensor nodes spend a large part of
their time in a sleep mode to save energy and cannot
communicate during these periods. This is absolutely
anomalous for IP networks.
Integration of sensing technologies into passive RFID tags
would enable a lot of completely new applications into
the IoT context, especially into the e-health area [24].
Recently, several solutions have been proposed in this
direction. As an example, the WISP project is being carried
out at Intel Labs to develop wireless identification and sens-
ing platforms (WISP) [25]. WISPs are powered and read by
standard RFID readers, harvesting the power from the
reader’s querying signal. WISPs have been used to measure
quantities in a certain environment, such as light, temper-
ature, acceleration, strain, and liquid level.
Sensing RFID systems will allow to build RFID sensor
networks [26], which consist of small, RFID-based sensing
and computing devices, and RFID readers, which are the
sinks of the data generated by the sensing RFID tags and
provide the power for the network operation.
Table 1 compares the characteristics of RFID systems
(RFID), wireless sensor networks (WSN), and RFID sensor
networks (RSN) [26]. Observe that the major advantages
of:
� RFID systems are the very small size and the very low
cost. Furthermore, their lifetime is not limited by the
battery duration;
� wireless sensor networks are the high radio coverage
and the communication paradigm, which does not
require the presence of a reader (communication is
peer-to-peer whereas, it is asymmetric for the other
types of systems);
� RFID sensor network are the possibility of supporting
sensing, computing, and communication capabilities
in a passive system.
3.2. Middleware
The middleware is a software layer or a set of sub-lay-
ers interposed between the technological and the applica-
tion levels. Its feature of hiding the details of different
technologies is fundamental to exempt the programmer
from issues that are not directly pertinent to her/his fo-
cus, which is the development of the specific application
enabled by the IoT infrastructures. The middleware is
gaining more and more importance in the last years due
to its major role in simplifying the development of new
services and the integration of legacy technologies into
new ones. This excepts the programmer from the exact
knowledge of the variegate set of technologies adopted
by the lower layers.
As it is happening in other contexts, the middleware
architectures proposed in the last years for the IoT often
follow the Service Oriented Architecture (SOA) approach.
The adoption of the SOA principles allows for decompos-
ing complex and monolithic systems into applications
consisting of an ecosystem of simpler and well-defined
components. The use of common interfaces and standard
protocols gives a horizontal view of an enterprise system.
Thus, the development of business processes enabled by
the SOA is the result of the process of designing work-
flows of coordinated services, which eventually are asso-
ciated with
the
interaction among the parts of an enterprise and allows
for reducing the time necessary to adapt itself to the
changes imposed by the market evolution [27]. A SOA ap-
proach also allows for software and hardware reusing, be-
facilitates
This
objects
actions.
Table 1
Comparison between RFID systems, wireless sensor networks, and RFID sensor networks.
Processing
Sensing
Communication
Range (m)
Power
RFID
WSN
RSN
No
Yes
Yes
No
Yes
Yes
Asymmetric
Peer-to-peer
Asymmetric
10
100
3
Harvested
Battery
Harvested
Lifetime
Indefinite
<3 years
Indefinite
Size
Very small
Small
Small
Standard
ISO18000
IEEE 802.15.4
None
�
2792
L. Atzori et al. / Computer Networks 54 (2010) 2787–2805
cause it does not impose a specific technology for the ser-
vice implementation [28].
Advantages of the SOA approach are recognized in most
studies on middleware solutions for IoT. While a com-
monly accepted layered architecture is missing, the pro-
posed solutions face essentially the same problems of
abstracting the devices functionalities and communica-
tions capabilities, providing a common set of services and
an environment for service composition. These common
objectives lead to the definition of the middleware sketch
shown in Fig. 2. It tries to encompass all the functionalities
addressed in past works dealing with IoT middleware is-
sues. It is quite similar to the scheme proposed in [29],
which addresses the middleware issues with a complete
and integrated architectural approach. It relies on the
layers explained in Sections 3.2.1–3.2.5.
3.2.1. Applications
Applications are on the top of the architecture, export-
ing all the system’s functionalities to the final user. Indeed,
this layer is not considered to be part of the middleware
but exploits all the functionalities of the middleware layer.
Through the use of standard web service protocols and ser-
vice composition technologies, applications can realize a
perfect
integration between distributed systems and
applications.
3.2.2. Service composition
This is a common layer on top of a SOA-based middle-
ware architecture. It provides the functionalities for the
composition of single services offered by networked ob-
jects to build specific applications. On this layer there is
no notion of devices and the only visible assets are ser-
vices. An important insight into the service landscape is
to have a repository of all currently connected service in-
stances, which are executed in run-time to build composed
services. The logic behind the creation and the manage-
ment of complex services, can be expressed in terms of
Fig. 2. SOA-based architecture for the IoT middleware.
workflows of business processes, using workflow lan-
guages. In this context, a frequent choice is to adopt stan-
dard languages such as the Business Process Execution
Language (BPEL) and Jolie [29,30]. Workflow languages de-
fine business processes that interact with external entities
through Web Service operations, defined by using the Web
Service Definition Language (WSDL) [31]. Workflows can
be nested, so it is possible to call a workflow from inside
another one. The creation of complex processes can be rep-
resented as a sequence of coordinated actions performed
by single components.
3.2.3. Service management
This layer provides the main functions that are expected
to be available for each object and that allow for their man-
agement in the IoT scenario. A basic set of services encom-
passes: object dynamic discovery, status monitoring, and
service configuration. At this layer, some middleware pro-
posals include an expanded set of functionalities related to
the QoS management and lock management, as well as
some semantic functions (e.g., police and context manage-
ment) [32]. This layer might enable the remote deploy-
ment of new services during run-time, in order to satisfy
application needs. A service repository is built at this layer
so as to know which is the catalogue of services that are
associated to each object in the network. The upper layer
can then compose complex services by joining services
provided at this layer.
3.2.4. Object abstraction
The IoT relies on a vast and heterogeneous set of ob-
jects, each one providing specific functions accessible
through its own dialect. There is thus the need for an
abstraction layer capable of harmonizing the access to
the different devices with a common language and proce-
dure. Accordingly, unless a device offers discoverable
web services on an IP network, there is the need to intro-
duce a wrapping layer, consisting of two main sub-layers:
the interface and the communication sub-layers. The first
one provides a web interface exposing the methods avail-
able through a standard web service interface and is
responsible for the management of all the incoming/out-
coming messaging operations involved in the communica-
tion with the external world. The second sub-layer
implements the logic behind the web service methods
and translates these methods into a set of device-specific
commands to communicate with the real-world objects.
Some works proposed the embedding of TCP/IP stacks
in the devices, such as the TinyTCP, the mIP and the IwIP
(see [33] and references herein), which provide a socket
like interface for embedded applications. Embedded web
servers can then be integrated in the objects, performing
the function of this object abstraction layer. However,
more often this wrapping function is provided through a
proxy, which is then responsible to open a communication
socket with the device’s console and send all the com-
mands to it by using different communication languages.
It is then responsible to make the conversion into a stan-
dard web service language and, sometimes, elaborate the
request to reduce the complexity of the operations re-
quired by the end-device [30].
�
L. Atzori et al. / Computer Networks 54 (2010) 2787–2805
2793
3.2.5. Trust, privacy and security management
The deployment of automatic communication of objects
in our lives represents a danger for our future. Indeed, un-
seen by users, embedded RFID tags in our personal devices,
clothes, and groceries can unknowingly be triggered to re-
ply with their ID and other information. This potentially
enables a surveillance mechanism that would pervade
large parts of our lives. The middleware must then include
functions related to the management of the trust, privacy
and security of all the exchanged data. The related func-
tions may be either built on one specific layer of the previ-
ous ones or (it happens more often) distributed through
the entire stack, from the object abstraction to the service
composition, in a manner that does not affect system per-
formance or introduce excessive overheads.
While most of the proposed middleware solutions make
use of the SOA approach, some others have followed a dif-
ferent way, especially if developed for a specific scenario
(target application, specific set of objects or limited geo-
graphical scenario). One remarkable project is the Fosstrak
one, which is specifically focused on the management of
RFID related applications [34]. It is an open source RFID
infrastructure that implements the interfaces defined in
the EPC Network specifications. It provides the following
services related to RFID management: data dissemination,
data aggregation, data filtering, writing to a tag, trigger
RFID reader from external sensors, fault and configuration
management, data interpretation, sharing of RFID triggered
business events, lookup and directory service, tag identifier
management, and privacy [35]. All these functions are
made available to the application layer to ease the deploy-
ment of RFID-related services. In [36], the authors present
another RFID-related middleware which relies on three
functionalities: the tag, the place, and the scenic managers.
The first allows the user to associate each tag to an object;
the second supports creating and editing location informa-
tion associated to RFID antennas; the third one is used to
combine the events collected by the antennas and the
developed related applications.
Another architecture that does not follow the SOA ap-
proach is proposed in the e-SENSE project, which focuses
on issues related to capturing ambient intelligence through
wireless sensor networks. The proposed architecture is di-
vided into four logical subsystems, namely the application,
management, middleware, and connectivity subsystems.
Each subsystem comprises various protocol and control
entities, which offer a wide range of services and functions
at service access points to other subsystems [37]. This entire
stack is implemented in a full function sensor node and in a
gateway node; while a reduced-function sensor node has
fewer functions. In the e-SENSE vision the middleware
subsystem has the only purpose to develop and handle an
infrastructure where information sensed by nodes is pro-
cessed in a distributed fashion and, if necessary, the result
is transmitted to an actuating node and/or to the fixed infra-
structure by means of a gateway. The other functions that
we have assigned to the middleware shown in Fig. 2 are
attributed to other components and layers. The project
UbiSec&Sens was also aimed at defining a comprehensive
architecture for medium and large scale wireless sensor net-
works, with a particular attention to the security issues so as
to provide a trusted and secure environment for all applica-
tions [38]. The middleware layer in this architecture mostly
focuses on: (i) the secure long-term logging of the collected
environmental data over time and over some regions (Tiny-
PEDS), (ii) functions that provides the nodes in the network
with the abstraction of shared memory (TinyDSM), (iii) the
implementation of distributed information storage and col-
lection (DISC) protocol for wireless sensor networks.
4. Applications
Potentialities offered by the IoT make possible the
development of a huge number of applications, of which
only a very small part is currently available to our society.
Many are the domains and the environments in which new
applications would likely improve the quality of our lives:
at home, while travelling, when sick, at work, when jog-
ging and at the gym, just to cite a few. These environments
are now equipped with objects with only primitive intelli-
gence, most of times without any communication capabil-
ities. Giving these objects the possibility to communicate
with each other and to elaborate the information perceived
from the surroundings imply having different environ-
ments where a very wide range of applications can be de-
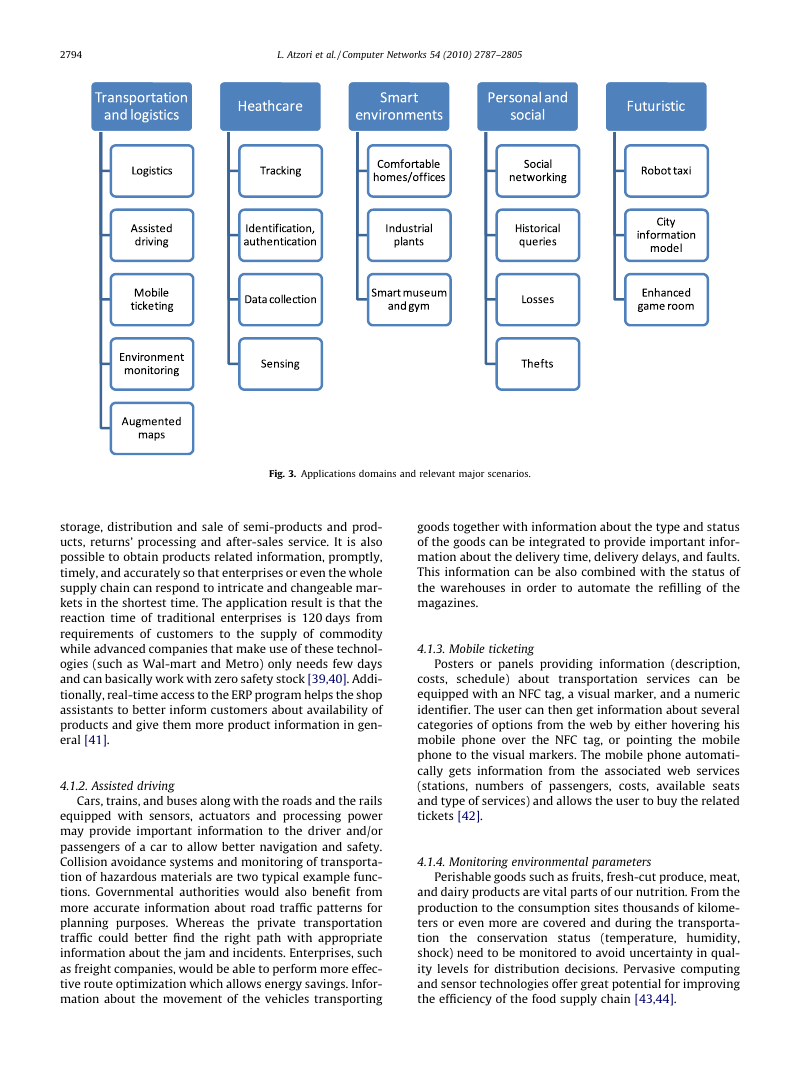
ployed. These can be grouped into the following domains:
� Transportation and logistics domain.
� Healthcare domain.
� Smart environment (home, office, plant) domain.
� Personal and social domain.
Among the possible applications, we may distinguish
between those either directly applicable or closer to our
current living habitudes and those futuristic, which we
can only fancy of at the moment, since the technologies
and/or our societies are not ready for their deployment
(see Fig. 3). In the following subsections we provide a
review of the short-medium term applications for each of
these categories and a range of futuristic applications.
4.1. Transportation and logistics domain
Advanced cars, trains, buses as well as bicycles along
with roads and/or rails are becoming more instrumented
with sensors, actuators, and processing power. Roads
themselves and transported goods are also equipped with
tags and sensors that send important information to traffic
control sites and transportation vehicles to better route the
traffic, help in the management of the depots, provide the
tourist with appropriate transportation information, and
monitor the status of the transported goods. Below, the
main applications in the transportation and logistics do-
main are described.
4.1.1. Logistics
Real-time information processing technology based on
RFID and NFC can realize real-time monitoring of almost
every link of the supply chain, ranging from commodity de-
sign, raw material purchasing, production, transportation,
�
2794
L. Atzori et al. / Computer Networks 54 (2010) 2787–2805
Fig. 3. Applications domains and relevant major scenarios.
storage, distribution and sale of semi-products and prod-
ucts, returns’ processing and after-sales service. It is also
possible to obtain products related information, promptly,
timely, and accurately so that enterprises or even the whole
supply chain can respond to intricate and changeable mar-
kets in the shortest time. The application result is that the
reaction time of traditional enterprises is 120 days from
requirements of customers to the supply of commodity
while advanced companies that make use of these technol-
ogies (such as Wal-mart and Metro) only needs few days
and can basically work with zero safety stock [39,40]. Addi-
tionally, real-time access to the ERP program helps the shop
assistants to better inform customers about availability of
products and give them more product information in gen-
eral [41].
4.1.2. Assisted driving
Cars, trains, and buses along with the roads and the rails
equipped with sensors, actuators and processing power
may provide important information to the driver and/or
passengers of a car to allow better navigation and safety.
Collision avoidance systems and monitoring of transporta-
tion of hazardous materials are two typical example func-
tions. Governmental authorities would also benefit from
more accurate information about road traffic patterns for
planning purposes. Whereas the private transportation
traffic could better find the right path with appropriate
information about the jam and incidents. Enterprises, such
as freight companies, would be able to perform more effec-
tive route optimization which allows energy savings. Infor-
mation about the movement of the vehicles transporting
goods together with information about the type and status
of the goods can be integrated to provide important infor-
mation about the delivery time, delivery delays, and faults.
This information can be also combined with the status of
the warehouses in order to automate the refilling of the
magazines.
4.1.3. Mobile ticketing
Posters or panels providing information (description,
costs, schedule) about transportation services can be
equipped with an NFC tag, a visual marker, and a numeric
identifier. The user can then get information about several
categories of options from the web by either hovering his
mobile phone over the NFC tag, or pointing the mobile
phone to the visual markers. The mobile phone automati-
cally gets information from the associated web services
(stations, numbers of passengers, costs, available seats
and type of services) and allows the user to buy the related
tickets [42].
4.1.4. Monitoring environmental parameters
Perishable goods such as fruits, fresh-cut produce, meat,
and dairy products are vital parts of our nutrition. From the
production to the consumption sites thousands of kilome-
ters or even more are covered and during the transporta-
tion the conservation status (temperature, humidity,
shock) need to be monitored to avoid uncertainty in qual-
ity levels for distribution decisions. Pervasive computing
and sensor technologies offer great potential for improving
the efficiency of the food supply chain [43,44].
�














 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc