cannot be utilized for any conformance or compliance purposes.
INTERNATIONAL
SURFACE VEHICLE
STANDARD
ISO/SAE DIS 21434
Issued
2020-02-12
Road Vehicles - Cybersecurity Engineering
FOREWORD
ISO (the International Organization for Standardization) is a worldwide federation of national standards bodies (ISO
member bodies). The work of preparing International Standards is normally carried out through ISO technical
committees. Each member body interested in a subject for which a technical committee has been established has the
right to be represented on that committee. International organizations, governmental and non-governmental, in liaison
with ISO, also take part in the work. ISO collaborates closely with the International Electrotechnical Commission (IEC)
on all matters of electrotechnical standardization.
SAE International is a global association of more than 128,000 engineers and related technical experts in the aerospace,
automotive and commercial-vehicle industries. Standards from SAE International are used to advance mobility
engineering throughout the world. The SAE Technical Standards Development Program is among the organization's
primary provisions to those mobility industries it serves aerospace, automotive, and commercial vehicle. These works
are authorized, revised, and maintained by the volunteer efforts of more than 9,000 engineers, and other qualified
professionals from around the world. SAE subject matter experts act as individuals in the standards process, not as
representatives of their organizations. Thus, SAE standards represent optimal technical content developed in a
transparent, open, and collaborative process.
The procedures used to develop this document and those intended for its further maintenance are described in the
ISO/IEC Directives, Part 1 and the SAE Technical Standards Board Policy. In particular, the different approval criteria
needed for the different types of ISO documents should be noted. This document was drafted in accordance with the
editorial rules of the ISO/IEC Directives, Part 2 (see www.iso.org/directives).
Attention is drawn to the possibility that some of the elements of this document may be the subject of patent rights. ISO
and SAE International shall not be held responsible for identifying any or all such patent rights. Details of any patent
rights identified during the development of the document will be in the Introduction and/or on the ISO list of patent
declarations received (see www.iso.org/patents).
SAE Technical Standards Board Rules provide that: "This document is published to advance the state of technical and
engineering sciences. The use of this document is entirely voluntary, and its applicability and suitability for any particular
use, including any patent infringement arising therefrom, is the sole responsibility of the user."
Any trade name used in this document is information given for the convenience of users and does not constitute an
endorsement.
For an explanation of the voluntary nature of standards, the meaning of ISO specific terms and expressions related to
conformity assessment, as well as information about ISO's adherence to the World Trade Organization (WTO) principles
in the Technical Barriers to Trade (TBT), see www.iso.org/iso/foreword.html.
© ISO/SAE International 2020
All rights reseived. Unless otherwise specified, or required in the context of its Implementation, no part of this publication may be reproduced; or
utilized otherwise in any form or by any means, electronic or mechanical, including photocopying, or posting on the internet or an intranel, without
prior written permission. Permission can be requested from either ISO or SAE International al the respective address below or ISO's member body
in the country of the requester.
ISO copyright office
CP 401 • Ch. de Blandonnet 8
CH-1214 Vernier, Geneva
Phone: +41 22 749 01 11
Fax: +41 22 749 09 47
Email: oopyright@iso.org
Website: www.iso.org
Published in Switzerland and USA.
SAE International
Tel': 877-606-7323 (inside USA and Canada)
Tel: +1 724-776-4970 (outside USA)
Fax: 724-776-0790
Email: CustomerSeivice@sae.org
SAE WEB ADDRESS: http://www.sae.org
�
ISO/SAE INTERNATIONAL
ISO/SAE DIS 21434
Page 2 of 108
This document was jointly prepared in the ISO/SAE Cybersecurity Engineering Joint Working Group, with experts from
ISO Technical Committee 22 Road Vehicles, Subcommittee 32 Electrical and electronic components and general
system aspects and SAE Vehicle Cybersecurity Systems Engineering Committee.
This first edition cancels and supersedes the SAE J3061_201601 .
A list of all parts in the ISO/SAE 21434 series can be found on the ISO and SAE websites.
Any feedback or questions on this document should be directed to the user's national standards body. A complete listing
of these bodies can be found at www.iso.org/members.html. Alternatively, to provide feedback on this document, please
visit https://www .sae.orq/standards/contenVISO/SAE21434. D1.
�
ISO/SAE INTERNAT IONAL
ISO/SAE DIS 21434
Page 3 of 108
Purpose of this Document
INTRODUCTION
This document addresses the cybersecurity perspective in engineering of electrical and electronic (E/E) systems within
road vehicles. By ensuring appropriate consideration of cybersecurity, this document aims to enable the engineering of
E/E systems to keep up with changing technology and attack methods.
This document provides vocabulary, objectives, requirements and guidelines as a foundation for common understanding
throughout the supply chain. This enables organizations to:
- define cybersecurity policies and processes;
- manage cybersecurity risk; and
- foster a cybersecurity culture.
This document can be used to implement a cybersecurity management system including cybersecurity risk management
in accordance with ISO 31000. This document is intended to supersede SAE J3061 recommended practice.
Organization of this Document
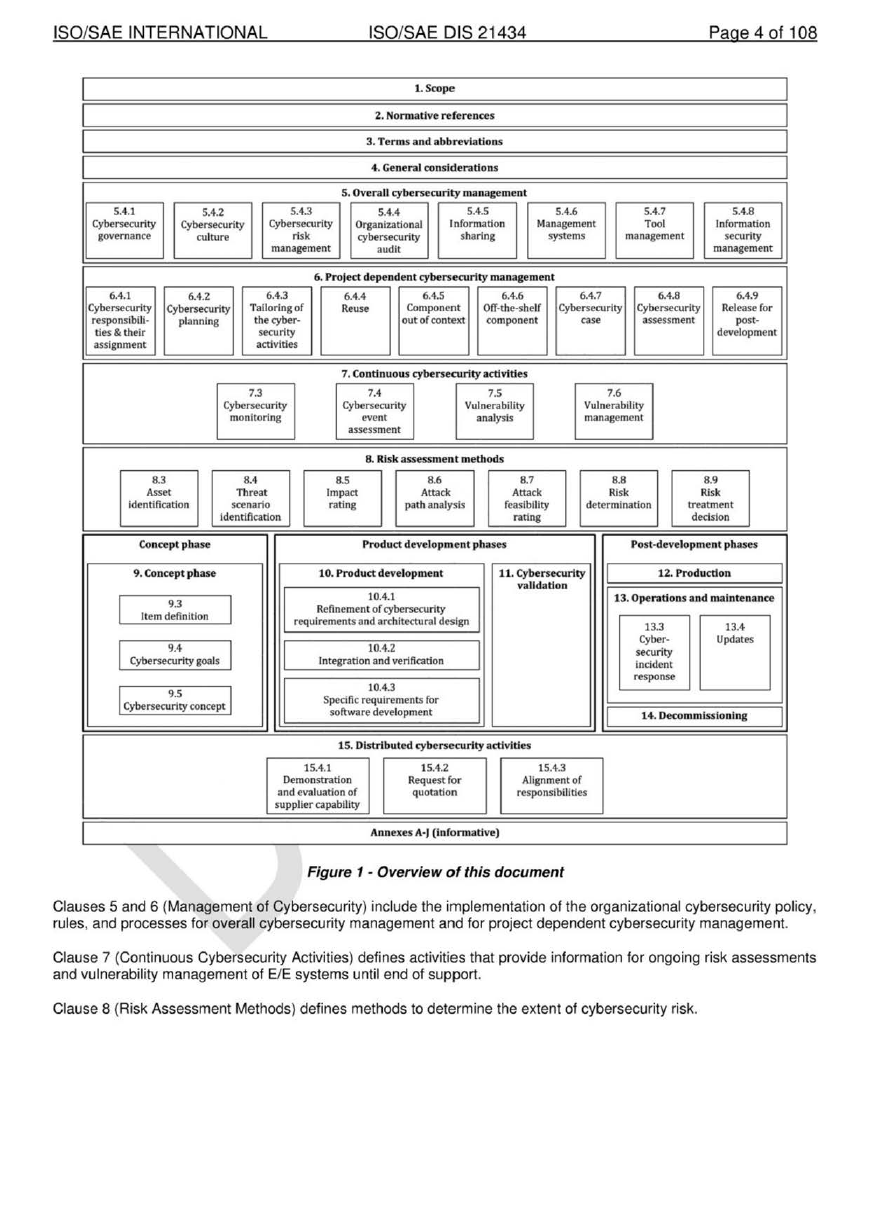
An overview of the document structure is given in Figure 1. The elements of Figure 1 do not prescribe an execution
sequence of the individual topics.
�
ISO/SAE INTERNATIONAL
ISO/SAE DIS 21434
Page 4 of 108
1.Scope
2. Nonnative references
3. Terms and abbreviations
4. General considerations
5.4.1
Cybersecurity
governance
5.4.2
Cybersecurity
culture
5.4.3
Cybersecurity
risk
management
5.4.4
Organizational
cybersecurity
audit
5.4.5
Information
s haring
5. Overall cybersecurity ma nagement
5.4.6
Management
systems
5.4.7
Tool
management
5.4.8
Information
security
management
6. Project dependent cybersecurlty manageme nt
6.4.1
6.4.2
Cybersecurlty Cybersecurity
responsibili·
ties & their
assignment
planning
6.4.6
6.4.7
6.4.8
Off-the-shelf Cybersecurity Cybersecurlty
component
assessment
case
6.4.9
Release for
post-
development
e
Component
out of context
Tailoring of
the cyber•
security
activities
6.4.3 □ 6.4.5
7.4
7.3
7. Continuous cybersec:urlty activities
Cybersecurity
monitoring
Cybersecurity
event
assessment
7.5
Vulnerability
analysis
7.6
Vulnerability
management
8. RJsk assessment me thods
8.3
Asset
ldentlncation
8.4
Threat
scenario
ldentlflcadon
8.5
Impact
rating
8.6
Attack
path analysis
8.1
Attack
feasibility
rating
8.8
Risk
determination
8.9
Risk
treatment
decision
Concept phase
Product development phases
Post-development phases
9. Concept phase
10. Product deve lopment
9.3
Item definition
9.4
Cybersecurity goals
I
I
I
I
10.4.1
Refinement of cybersecurlty
requirements and architectural design
I
10.4.2
Integration and verification
I
9.5
Cybersecurity concept
10.4.3
spec1nc requirements for
software development
11. Cybersecurity
validation
I
12.Productlon
13. Operations an d maintenance
13.4
Updates
13.3
Cyber-
security
incident
response
I
14. Decommissioning
I
I
1S. Distribute d cybersecurlty activities
15.4.1
Demonstration
and evaluation of
supplier capability
15.4.2
Request for
quotation
15.4.3
Alignment of
responsibilities
Annexes A·J (Informative)
Figure 1 - Overview of this document
Clauses 5 and 6 (Management of Cybersecurity) include the implementation of the organizational cybersecurity policy,
rules, and processes for overall cybersecurity management and for project dependent cybersecurity management.
Clause 7 (Continuous Cybersecurity Activities) defines activities that provide information for ongoing risk assessments
and vulnerability management of E/E systems until end of support.
Clause 8 (Risk Assessment Methods) defines methods to determine the extent of cybersecurity risk.
�
ISO/SAE INTERNATIONAL
ISO/SAE DIS 21434
Page 5 of 108
Clause 9 (Concept Phase) defines an item and the relevant assets, provides cybersecurity risk determination, and
defines the cybersecurity goals.
Clause 1 O (Product Development) defines the cybersecurity specification, implements and verifies cybersecurity
requirements specific to an item or component.
Clause 11 (Cybersecurity Validation) describes the cybersecurity validation of an item at the vehicle level.
Clause 12 (Production) specifies the cybersecurity related aspects of fabrication, assembly and/or calibration of an item
or component.
Clause 13 (Operations and Maintenance) specifies activities related to cybersecurity incident response and updates to
an item or component.
Clause 14 (Decommissioning) includes cybersecurity considerations that relate to the decommissioning of an item or
component.
Clause 15 (Distributed Activities) includes requirements for supplier management.
�
ISO/SAE INTERNAT IONAL
ISO/SAE DIS 21434
Page 6 of 108
1.
2.
3.
3.1
3.2
4.
5.
5.1
5.2
5.3
5.3.1
5.3.2
5.4
5.4.1
5.4.2
5.4.3
5.4.4
5.4.5
5.4.6
5.4.7
5.4.8
5.5
6.
6.1
6.2
6.3
6.3.1
6.3.2
6.4
6.4.1
6.4.2
6.4.3
6.4.4
6.4.5
6.4.6
6.4. 7
6.4.8
6.4.9
6.5
7.
7.1
7.2
7.3
7.3.1
7.3.2
7.3.3
7.4
7.4.1
7.4.2
7.4.3
TABLE OF CONTENTS
SCOPE .................................................................................................................................................. 10
NORMATIVE REFERENCES ............................................................................................................... 10
TERMS AND ABBREVIATIONS ........................................................................................................... 10
Terms and Definitions ........................................................................................................................... 10
Abbreviated Terms ................................................................................................................................ 14
GENERAL CONSIDERATIONS ........................................................................................................... 14
OVERALL CYBERSECURITY MANAGEMENT ................................................................................... 16
General .................................................................................................................................................. 16
Objectives ............................................................................................................................................. 16
Inputs ..................................................................................................................................................... 17
Prerequisites ......................................................................................................................................... 17
Further Supporting Information ............................................................................................................. 17
Requirements and Recommendations .................................................................................................. 17
Cybersecurity Governance ................................................................................................................... 17
Cybersecurity Culture ............................................................................................................................ 18
Cybersecurity Risk Management .......................................................................................................... 19
Organizational Cybersecurity Audit.. ..................................................................................................... 19
Information Sharing ............................................................................................................................... 20
Management Systems .......................................................................................................................... 20
Tool Management ................................................................................................................................. 21
Information Security Management ........................................................................................................ 21
Work Products ....................................................................................................................................... 21
PROJECT DEPENDENT CYBERSECURITY MANAGEMENT ........................................................... 22
General. ................................................................................................................................................. 22
Objectives ............................................................................................................................................. 22
Inputs ..................................................................................................................................................... 23
Prerequisites ......................................................................................................................................... 23
Further Supporting Information ............................................................................................................. 23
Requirements and Recommendations .................................................................................................. 23
Cybersecurity Responsibilities and Their Assignment .......................................................................... 23
Cybersecurity Planning ......................................................................................................................... 23
Tailoring of the Cybersecurity Activities ................................................................................................ 24
Reuse .................................................................................................................................................... 25
Component Out of Context ................................................................................................................... 26
Off-the-Shelf Component ...................................................................................................................... 26
Cybersecurity Case ............................................................................................................................... 26
Cybersecurity Assessment. ................................................................................................................... 26
Release for Post-Development ............................................................................................................. 28
Work Products ....................................................................................................................................... 29
CONTINUOUS CYBERSECURITY ACTIVITIES ................................................................................. 29
General .................................................................................................................................................. 29
Objectives ............................................................................................................................................. 29
Cybersecurity Monitoring ...................................................................................................................... 29
Inputs ..................................................................................................................................................... 29
Requirements and Recommendations .................................................................................................. 30
Work Products ....................................................................................................................................... 30
Cybersecurity Event Assessment ......................................................................................................... 30
Inputs ..................................................................................................................................................... 30
Requirements and Recommendations .................................................................................................. 31
Work Products ....................................................................................................................................... 31
�
ISO/SAE INTERNATIONAL
ISO/SAE DIS 21434
Page 7 of 108
7.5
7.5.1
7.5.2
7.5.3
7.6
7.6.1
7.6.2
7.6.3
8.
8.1
8.2
8.3
8.3.1
8.3.2
8.3.3
8.4
8.4.1
8.4.2
8.4.3
8.5
8.5.1
8.5.2
8.5.3
8.6
8.6.1
8.6.2
8.6.3
8.7
8.7.1
8.7.2
8.7.3
8.8
8.8.1
8.8.2
8.8.3
8.9
8.9.1
8.9.2
8.9.3
9.
9.1
9.2
9.3
9.3.1
9.3.2
9.3.3
9.4
9.4.1
9.4.2
9.4.3
9.5
9.5.1
9.5.2
9.5.3
Vulnerability Analysis ............................................................................................................................ 31
Inputs ..................................................................................................................................................... 31
Requirements and Recommendations .................................................................................................. 31
Work Products ....................................................................................................................................... 32
Vulnerability Management .................................................................................................................... 32
Inputs ..................................................................................................................................................... 32
Requirements and Recommendations .................................................................................................. 32
Work Products ....................................................................................................................................... 33
RISK ASSESSMENT METHODS ......................................................................................................... 33
General .................................................................................................................................................. 33
Objectives ............................................................................................................................................. 34
Asset Identification ................................................................................................................................ 34
Inputs ..................................................................................................................................................... 34
Requirements and Recommendations .................................................................................................. 34
Work Products ....................................................................................................................................... 35
Threat Scenario Identification ............................................................................................................... 35
Inputs ..................................................................................................................................................... 35
Requirements and Recommendations .................................................................................................. 35
Work Products ....................................................................................................................................... 36
Impact Rating ........................................................................................................................................ 36
Inputs ..................................................................................................................................................... 36
Requirements and Recommendations .................................................................................................. 36
Work Products ....................................................................................................................................... 37
Attack Path Analysis ............................................................................................................................. 37
Inputs ..................................................................................................................................................... 37
Requirements and Recommendations .................................................................................................. 37
Work Products ....................................................................................................................................... 38
Attack Feasibility Rating ........................................................................................................................ 39
Inputs ..................................................................................................................................................... 39
Requirements and Recommendations .................................................................................................. 39
Work Products ....................................................................................................................................... 40
Risk Determination ................................................................................................................................ 40
Inputs ..................................................................................................................................................... 40
Requirements and Recommendations .................................................................................................. 40
Work Products ....................................................................................................................................... 40
Risk Treatment Decision ....................................................................................................................... 40
Inputs ..................................................................................................................................................... 40
Requirements and Recommendations .................................................................................................. 41
Work Products ....................................................................................................................................... 41
CONCEPT PHASE ............................................................................................................................... 41
General .................................................................................................................................................. 41
Objectives ............................................................................................................................................. 42
Item Definition ....................................................................................................................................... 42
Inputs ..................................................................................................................................................... 42
Requirements and Recommendations .................................................................................................. 42
Work Products ....................................................................................................................................... 43
Cybersecurity Goals .............................................................................................................................. 43
Inputs ..................................................................................................................................................... 43
Requirements and Recommendations .................................................................................................. 44
Work Products ....................................................................................................................................... 45
Cybersecurity Concept .......................................................................................................................... 45
Inputs ..................................................................................................................................................... 45
Requirements and Recommendations .................................................................................................. 46
Work Products ....................................................................................................................................... 46
10.
10.1
10.2
10.3
10.3.1
10.3.2
PRODUCT DEVELOPMENT ................................................................................................................ 46
General. ................................................................................................................................................. 46
Objectives ............................................................................................................................................. 49
Inputs ..................................................................................................................................................... 49
Prerequisites ......................................................................................................................................... 49
Further Supporting Information ............................................................................................................. 50
�
ISO/SAE INTERNATIONAL
ISO/SAE DIS 21434
Page 8 of 108
10.4
10.4.1
10.4.2
10.4.3
10.5
11 .
11 .1
11 .2
11 .3
11.3.1
11 .3.2
11.4
11.5
12.
12.1
12.2
12.3
12.3.1
12.3.2
12.4
12.5
13.
13.1
13.2
13.3
13.3.1
13.3.2
13.3.3
13.4
13.4.1
13.4.2
13.4.3
14.
14.1
14.2
14.3
14.3.1
14.3.2
14.4
14.5
15.
15.1
15.2
15.3
15.3.1
15.3.2
15.4
15.4.1
15.4.2
15.4.3
15.5
Requirements and Recommendations .................................................................................................. 50
Refinement of Cybersecurity Requirements and Architectural Design ................................................. 50
Integration and Verification ................................................................................................................... 53
Specific Requirements for Software Development ............................................................................... 56
Work Products ....................................................................................................................................... 57
CYBERSECURITY VALIDATION ......................................................................................................... 57
General. ................................................................................................................................................. 57
Objectives ............................................................................................................................................. 57
Inputs ..................................................................................................................................................... 57
Prerequisites ......................................................................................................................................... 57
Further Supporting Information ............................................................................................................. 58
Requirements and Recommendations .................................................................................................. 58
Work Products ....................................................................................................................................... 58
PRODUCTION ...................................................................................................................................... 58
General. ................................................................................................................................................. 58
Objectives ............................................................................................................................................. 58
Inputs ..................................................................................................................................................... 59
Prerequisites ......................................................................................................................................... 59
Further Supporting Information ............................................................................................................. 59
Requirements and Recommendations .................................................................................................. 59
Work Products ....................................................................................................................................... 60
OPERATIONS AND MAINTENANCE ................................................................................................... 60
General. ................................................................................................................................................. 60
Objectives ............................................................................................................................................. 60
Cybersecurity Incident Response ......................................................................................................... 60
Inputs ..................................................................................................................................................... 60
Requirements and Recommendations .................................................................................................. 60
Work Products ....................................................................................................................................... 61
Updates ................................................................................................................................................. 61
Inputs ..................................................................................................................................................... 61
Requirements and Recommendations .................................................................................................. 62
Work Products ....................................................................................................................................... 62
DECOMMISSIONING ........................................................................................................................... 62
General. ................................................................................................................................................. 62
Objectives ............................................................................................................................................. 62
Inputs ..................................................................................................................................................... 62
Prerequisites ......................................................................................................................................... 62
Further Supporting Information ............................................................................................................. 62
Requirements and Recommendations .................................................................................................. 63
Work Products ....................................................................................................................................... 63
DISTRIBUTED CYBERSECURITY ACTIVITIES .................................................................................. 63
General. ................................................................................................................................................. 63
Objectives ............................................................................................................................................. 63
Inputs ..................................................................................................................................................... 63
Prerequisites ......................................................................................................................................... 63
Further Supporting Information ............................................................................................................. 63
Requirements and Recommendations .................................................................................................. 63
Demonstration and Evaluation of Supplier Capability ........................................................................... 63
Request for Quotation ........................................................................................................................... 64
Alignment of Responsibilities ................................................................................................................ 64
Work Products ....................................................................................................................................... 65
�















 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc