Journal of Computer and Communications, 2018, 6, 311-325
http://www.scirp.org/journal/jcc
ISSN Online: 2327-5227
ISSN Print: 2327-5219
Access Control Attacks on PLC Vulnerabilities
Yong Wang1, Jinyong Liu1, Can Yang1, Lin Zhou1, Shuangfei Li1, Zhaoyan Xu2
1Department of Information Security, Shanghai University of Electric Power, Shanghai, China
2Palo Alto Networks, California, CA, USA
How to cite this paper: Wang, Y., Liu, J.Y.,
Yang, C., Zhou, L., Li, S.F. and Xu, Z.Y.
(2018) Access Control Attacks on PLC
Vulnerabilities. Journal of Computer and
Communications, 6, 311-325.
https://doi.org/10.4236/jcc.2018.611028
Received: October 19, 2018
Accepted: November 26, 2018
Published: November 29, 2018
Copyright © 2018 by authors and
Scientific Research Publishing Inc.
This work is licensed under the Creative
Commons Attribution International
License (CC BY 4.0).
http://creativecommons.org/licenses/by/4.0/
Open Access
Abstract
In Industrial Control Systems (ICS), security issues are getting more and
more attention. The number of hacking attacks per year is endless, and the
attacks on industrial control systems are numerous. Programmable Logic
Controller (PLC) is one of the main controllers of industrial processes. Since
the industrial control system network is isolated from the external network,
many people think that PLC is a safety device. However, virus attacks in re-
cent years, such as Stuxnet, have confirmed the erroneousness of this idea. In
this paper, we use the vulnerability of Siemens PLC to carry out a series of at-
tacks, such as S7-200, S7-300, S7-400, S7-1200 and so on. We read the data
from the PLC output and then rewrite the data and write it to the PLC. We
tamper with the writing of data to achieve communication chaos. When we
attack the primary station, all slave devices connected to the primary station
will be in a state of communication confusion. The attack methods of us can
cause delay or even loss of data in the communications from the Phasor Data
Concentrator (PMU) to the data concentrator. The most important thing is
that our attack method generates small traffic and short attack time, which is
difficult to be identified by traditional detection methods.
Keywords
ICS, PLC, PMU, Data Tampering, Delay, Attack Methods
1. Introduction
Most of the ICS consist of several sub-components, such as PLC, Human Ma-
chine Interface (HMI), Master Terminal Unit (MTU) and Remote Terminal
Unit (RTU) [1]. Due to the high reliability, simple programming, variable con-
trol program, good flexibility and convenient expansion of PLC, it has been fa-
vored by many designers of the ICS. In the power industry, PLC is used for
communication operations, equipment operations, and so on. For example, the
DOI: 10.4236/jcc.2018.611028 Nov. 29, 2018
311
Journal of Computer and Communications
�
Y. Wang et al.
DOI: 10.4236/jcc.2018.611028
power system must ensure that the power equipment of the power plant and the
substation operate synchronously. Firstly, it is necessary to ensure the consis-
tency of the internal clock of the equipment. The safe operation of the power
system requires high-precision time synchronization within a wide range. Syn-
chronous phase measurement, power angle measurement, fault location, and
fault recording of the entire power system require time synchronization tech-
nology. Safe and reliable high-precision time synchronization technology is a
basic requirement for the normal operation of the smart grid in the contempo-
rary power grid and in the future.
In this article, we use the PLC experimental equipment of Siemens. The
communication protocol adopted by Siemens PLC is S7Comm protocol. It pro-
vides the service definition and protocols for real-time communication based on
Ethernet [2]. At the beginning of the S7Comm protocol designer, the designer
mainly focused on improving production efficiency and did not consider its se-
curity. Because PLC is the core equipment of the ICS, it has become the target of
more and more hackers. A quick search in the ICS-CERT repository reveals
more than 80 target PLCs out of a total of 589 advisories [3]. Many believed that
PLCs are secured devices due to its isolation from the external networks of the
system. The attacks such as Stuxnet have proven the incorrectness of such
thoughts [1] [2] [3] [4] [5]. In addition, on December 23, 2015, the Ukrainian
power grid was attacked by hackers, causing large-scale power outages, which
has caused people to pay sufficient attention to communication security. In the
field of information security, the most vulnerable is not the system itself, but just
people. If a disgruntled engineer wants to destroy the system, a small loophole
can cause devastating damage to the ICS. Therefore, the research on any tiny
vulnerability also has high research value.
In this paper, we mainly carry out corresponding experimental research on
PLC of Siemens. We use the Siemens PLC access control vulnerability, first es-
tablish a legal connection with the PLC, and then read and write the PLC’s in-
termediate register data to achieve the effect of abnormal communications. In
this way, we can attack the Siemens S7 series controllers, such as S7-200, S7-300,
S7-400, S7-1200 and so on. In the PLC architecture, the CPUs execute the results
of the program into the intermediate registers and then execute the results. We
read and rewrite the value of the intermediate register to implement the attack.
The rest of this paper is organized as follows. The related work is explained in
Section 2. The test bed setup is given in Section 3 and then the attack approach
on PLC based systems is introduced in Section 4. Furthermore, we discussed the
lack of attack methods and corresponding emergency measures in Section 5 be-
fore where the paper is concluded in Section 6.
2. Related Work
At present, many researchers have done a lot of research work on PLC security
vulnerabilities. According to [1] analysis of PLC vulnerabilities, we recognize the
312
Journal of Computer and Communications
�
Y. Wang et al.
effectiveness of the researchers’ three attacks on PLC. And based on the Siemens
PLC access vulnerability, three effective attacks were proposed: replay attack,
man-in-the-middle attack and S7 Authentication Bypass Attack. Haroon War-
dak et al. [3] have also explicitly proposed PLC access control vulnerabilities in-
cluding poor authentication mechanisms, lack of integrity methods, defect
password protection, and flawed communication protocols. Based on the access
control vulnerability, the attacker can use the legal way to carry out illegal opera-
tions according to the principle of the PLC communication protocol. Moreover,
this illegal operation is difficult to be identified by the general methods and cor-
responding measures are taken to deal with the attack. In [4], the researchers al-
so confirmed that Internet-oriented PLCs are more vulnerable to malicious code
injection and attacks. According to the research of [6], worms capable of
spreading between PLCs have been realized. In [7] [8], researchers conducted
vulnerability analysis and attacks on PLCs on the network side. Studies pre-
sented false sequence attack that could disable the fault detection against Pro-
grammable Logic Controllers (PLCs) with partial information about the victim
system are in [9]. And [10] presented a methodology of crafting an attack which
exploited the Tricon configuration download phase to modify the downloaded
control logic with the objective to cause common-mode failures in Tricon. In
[11], researchers proposed a firmware-level detection mechanism which can
detect abnormal runtime behaviors of malicious PLC payload. The result showed
that a wide variety of payload attacks could be effectively detected by the pro-
posed approach.
The above researchers conducted related vulnerability analysis and corres-
ponding attack experiments on PLC. Some scholars have proposed preventive
measures for the corresponding vulnerabilities and attack experiments. Particu-
larly, the worms studied in [6] are extremely destructive to PLC. However, the
detection method based on PLC engineering logic static analysis proposed by
[12] and the virus detection method based on dynamic analysis of debugging
protocol can effectively detect it. In this paper, the I/O port can be easily oper-
ated by legal communication to achieve the intended attack purpose and will not
be detected.
3. Testbed Setup
In this paper, we use Siemens PLC as the experimental equipment. The PLC uses
a simple architecture. They are based on central processing modules (CPUs) and
other modules that support digital inputs and outputs. The CPU executes the
operating system of the PLC and runs the user program. In addition, the CPU is
responsible for communicating with other devices and managing the process
image. The process image stores the status of all inputs and outputs. The user
program operates on the process image instead of on physical inputs and out-
puts. The user program runs in a loop. The CPU refreshes the process image at
the beginning and end of each cycle. The biggest limit of the loop is the cycle
313
Journal of Computer and Communications
DOI: 10.4236/jcc.2018.611028
�
Y. Wang et al.
time. If this limit is violated, the PLC will stop the user program and raise an ex-
ception.
In the PLC architecture, the CPUs execute the results of the program into the
intermediate registers and then execute the results. We can program according
to the format of the PLC communication protocol, establish a connection with
the PLC, and read and write the value of the register. After the value of the reg-
ister is overwritten, it will be executed immediately. The PLC architecture is
showing in Figure 1.
Siemens PLC uses the proprietary S7Comm protocol transport block. It is a
remote procedure call (RPC) protocol based on TCP/IP and ISO over TCP. The
encapsulation of the protocol is showing in Figure 2.
The connection needs to be initialized when performing some functions. After
the regular TCP handshake, the ISO over TCP settings continue to negotiate the
PDU size. In the S7Comm protocol, the client must provide the CPU’s racks and
slots for its preferred PDU size. The CPU responds with its preferred PDU size
and agrees to continue using the minimum of the two values. After initialization,
the client can call the functions on the CPU.
Our experimental equipment includes two Siemens S7-1200s and one Siemens
LOGO. We set one of the Siemens S7-1200s as the master station in the electric
power industry, and the other two devices are slaves. The IP address of the mas-
ter station device is 192.168.0.200 and the master station device is recorded as A.
Then the IP address of the S7-1200 slave device is 192.168.0.100 and the S7-1200
slave device is recorded as B. Last the IP address of the Siemens LOGO slave de-
vice is 192.168.0.3 and the Siemens LOGO slave device is recorded as C. Three
devices communicate over Ethernet through a switch connection. The network
topology is showing in Figure 3.
Figure 1. PLC Architecture, adopted from [6].
DOI: 10.4236/jcc.2018.611028
Figure 2. Packet encapsulation, adopted from [13].
314
Journal of Computer and Communications
�
Y. Wang et al.
Figure 3. The network topology.
The four devices in the picture are connected through a switch, and the com-
puter can monitor them. The master device can communicate with the slave de-
vice and can control the input and output of the slave device.
The power system must ensure that the power equipment of the power plant
and the substation operate synchronously. So, the real-time and efficient trans-
mission of data from power industry equipment plays an important role in the
safe operation of power systems. Two Siemens S7-1200 devices simulate data
communications from the PMU to the data concentrator in the electric power
industry. The slave takes the data from the PMU, and the slave gets the data ob-
tained to the master. After the master gets the data from all the slaves, it trans-
fers all the data to the data concentrator. The tested configuration is showing in
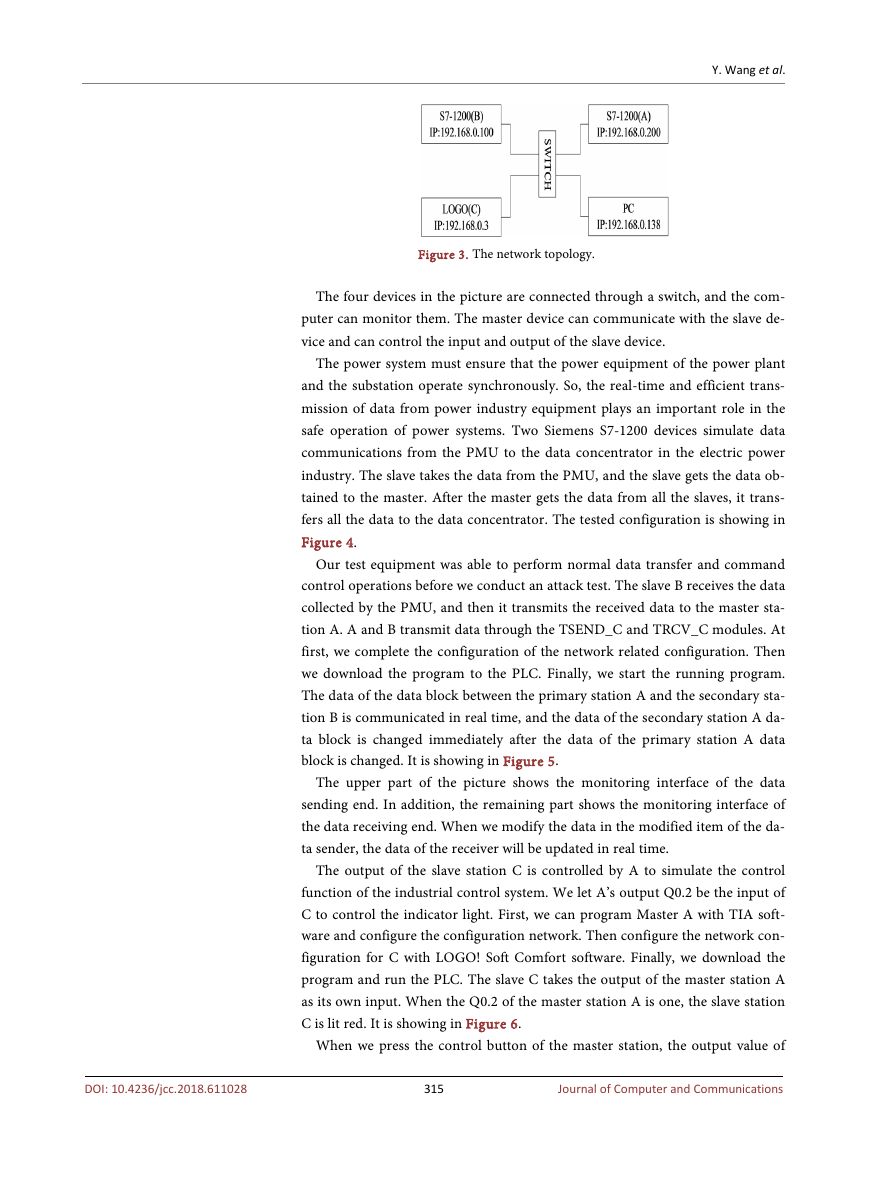
Figure 4.
Our test equipment was able to perform normal data transfer and command
control operations before we conduct an attack test. The slave B receives the data
collected by the PMU, and then it transmits the received data to the master sta-
tion A. A and B transmit data through the TSEND_C and TRCV_C modules. At
first, we complete the configuration of the network related configuration. Then
we download the program to the PLC. Finally, we start the running program.
The data of the data block between the primary station A and the secondary sta-
tion B is communicated in real time, and the data of the secondary station A da-
ta block is changed immediately after the data of the primary station A data
block is changed. It is showing in Figure 5.
The upper part of the picture shows the monitoring interface of the data
sending end. In addition, the remaining part shows the monitoring interface of
the data receiving end. When we modify the data in the modified item of the da-
ta sender, the data of the receiver will be updated in real time.
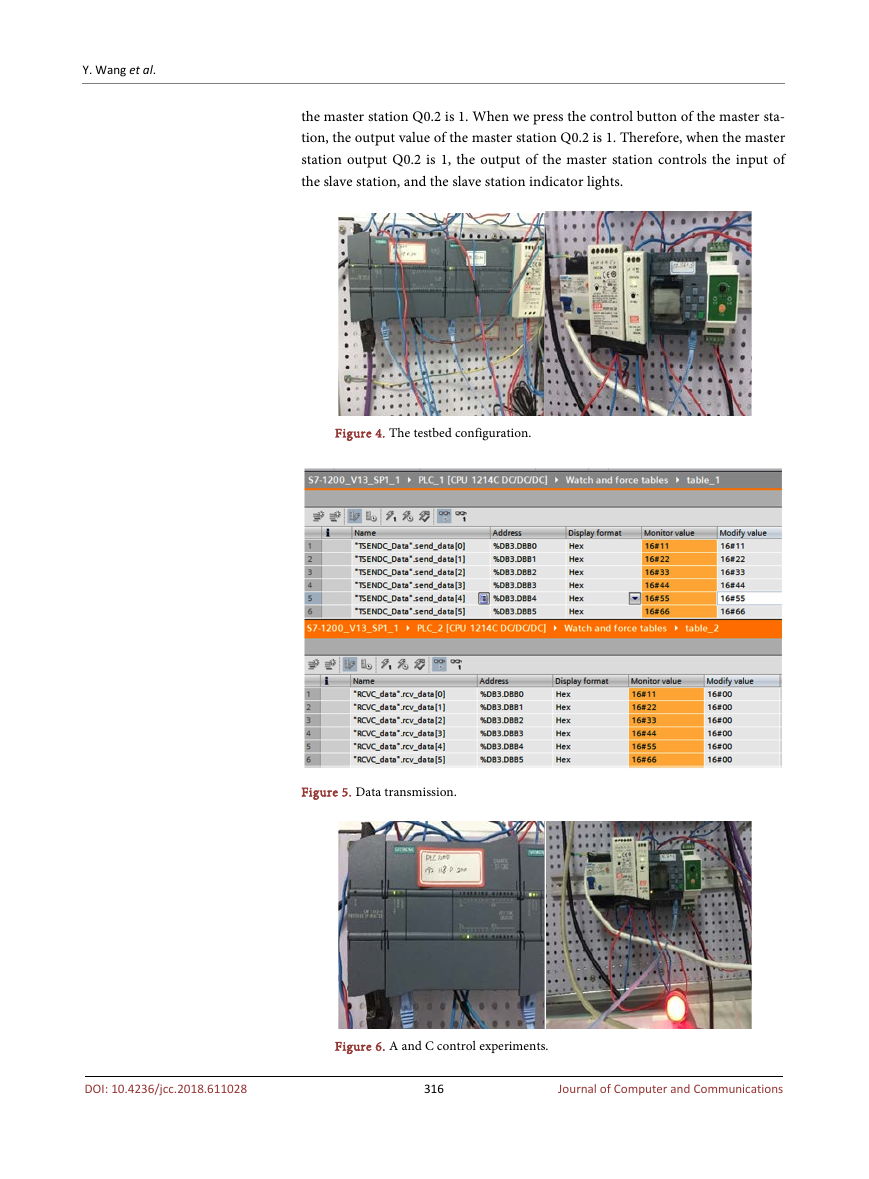
The output of the slave station C is controlled by A to simulate the control
function of the industrial control system. We let A’s output Q0.2 be the input of
C to control the indicator light. First, we can program Master A with TIA soft-
ware and configure the configuration network. Then configure the network con-
figuration for C with LOGO! Soft Comfort software. Finally, we download the
program and run the PLC. The slave C takes the output of the master station A
as its own input. When the Q0.2 of the master station A is one, the slave station
C is lit red. It is showing in Figure 6.
When we press the control button of the master station, the output value of
315
Journal of Computer and Communications
DOI: 10.4236/jcc.2018.611028
�
Y. Wang et al.
the master station Q0.2 is 1. When we press the control button of the master sta-
tion, the output value of the master station Q0.2 is 1. Therefore, when the master
station output Q0.2 is 1, the output of the master station controls the input of
the slave station, and the slave station indicator lights.
Figure 4. The testbed configuration.
Figure 5. Data transmission.
DOI: 10.4236/jcc.2018.611028
Figure 6. A and C control experiments.
316
Journal of Computer and Communications
�
Y. Wang et al.
4. The Attack Approach
We understand PLC access control vulnerabilities and use them for attacks. As
an attacker, we must have the ability to automatically recognize the PLC and
successfully establish a connection with the PLC. When we detect the IP address,
we can automatically identify whether it is the PLC that we are looking for. In
this paper, we establish a connection with the detected PLC IP address to detect
whether it is the type of PLC we want. Since the tool we use to establish a con-
nection with the PLC can only be connected to the PLC of a manufacturer, when
we can successfully establish a connection with the searched IP address, it is the
target we want to attack, otherwise we will abandon the attack operation on this
IP. When we establish a connection with the target, we first read the value of the
PLC input and output. According to the environment in the real industrial con-
trol system, we have different effects on the 0 or 1 of the input and output ports
of the PLC. Therefore, we invert the read data and write the inverted value to the
PLC register to make the PLC output abnormal. We repeat the above operation
in a loop until the PLC stops running. The attack process is showing in Figure 7.
In our attack method, the most critical step is to establish a connection with
the PLC according to the principle of S7Comm protocol. According to the prin-
ciple of the S7Comm protocol, we write a program to establish a connection.
The format of the message sent by the program to the PLC is the same as that of
the S7Comm protocol.
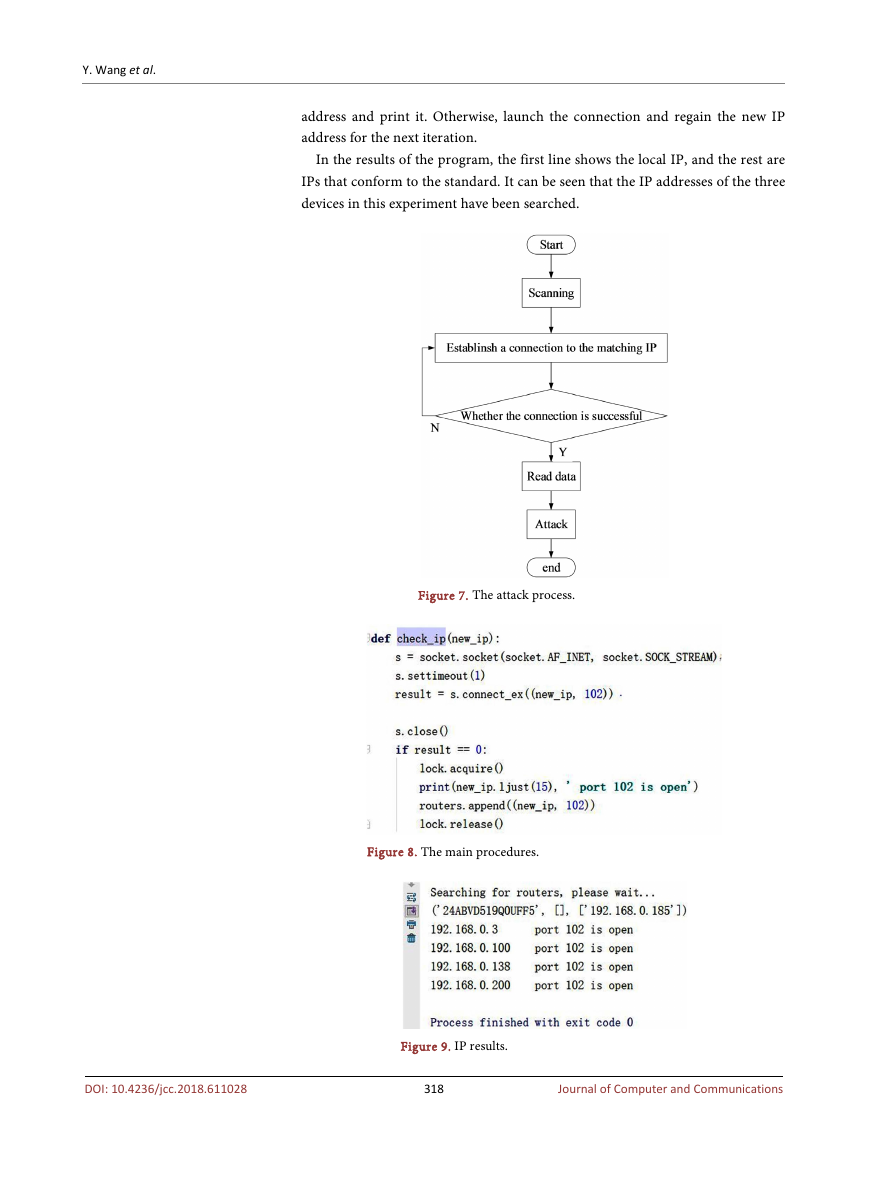
4.1. Scanning
For an attacker, once it is activated in a specific environment, the first thing is to
lock the target. After starting the program, the program starts scanning the port
and IP. The connection result is tested one by one. We attack the PLCs that can
connect successfully, assuming that the industrial control system equipment
PLC is in the same network segment. After starting to attack the system, the lo-
cal IP is first identified. We search all open port (102) IPs in the local IP network
segment. In this paper, the experimental device port is 102, so this experiment
takes port (102) as an example. The scanner can be broken down into the fol-
lowing steps:
Get local IP and port;
Calculate IPs of the subnet;
Set up TCP connection;
Save valid IP and port;
Stop scanning and disconnect TCP connection.
Some of the main procedures and results are showing in Figure 8 and Figure
9.
In the program, we define a function to find the IP. The initial IP we use is a
local IP to get the IP of the device quickly. In the defined function, we first use
the socket function to connect with the new IP. If it detects that the device port
is 102, we store this IP. In the eighth line of the program, we record a valid IP
317
Journal of Computer and Communications
DOI: 10.4236/jcc.2018.611028
�
Y. Wang et al.
address and print it. Otherwise, launch the connection and regain the new IP
address for the next iteration.
In the results of the program, the first line shows the local IP, and the rest are
IPs that conform to the standard. It can be seen that the IP addresses of the three
devices in this experiment have been searched.
Figure 7. The attack process.
Figure 8. The main procedures.
DOI: 10.4236/jcc.2018.611028
Figure 9. IP results.
318
Journal of Computer and Communications
�













 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc