3GPP TS 35.206 V9.0.0 (2009-12)
Technical Specification
3rd Generation Partnership Project;
Technical Specification Group Services and System Aspects;
3G Security;
Specification of the MILENAGE Algorithm Set:
An example algorithm set for the 3GPP authentication and
key generation functions f1, f1*, f2, f3, f4, f5 and f5*;
Document 2: Algorithm Specification
(Release 9)
The present document has been developed within the 3rd Generation Partnership Project (3GPP TM) and may be further elaborated for the purposes of 3GPP.
The present document has not been subject to any approval process by the 3GPP Organisational Partners and shall not be implemented.
This Specification is provided for future development work within 3GPP only. The Organisational Partners accept no liability for any use of this Specification.
Specifications and reports for implementation of the 3GPP TM system should be obtained via the 3GPP Organisational Partners' Publications Offices.
�
3GPP TS 35.206 V9.0.0 (2009-12)
Release 9
2
Keywords
UMTS , Security, Algorithm
3GPP
Postal address
3GPP support office address
650 Route des Lucioles - Sophia Antipolis
Valbonne - FRANCE
Tel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16
Internet
http://www.3gpp.org
Copyright Notification
No part may be reproduced except as authorized by written permission.
The copyright and the foregoing restriction extend to reproduction in all media.
©2009, 3GPP Organizational Partners (ARIB, ATIS, CCSA, ETSI, TTA, TTC).
UMTS™ is a Trade Mark of ETSI registered for the benefit of its members
3GPP™ is a Trade Mark of ETSI registered for the benefit of its Members and of the 3GPP Organizational Partners
LTE™ is a Trade Mark of ETSI currently being registered for the benefit of its Members and of the 3GPP Organizational Partners
GSM® and the GSM logo are registered and owned by the GSM Association
All rights reserved.
3GPP
�
Release 9
3
3GPP TS 35.206 V9.0.0 (2009-12)
Contents
Foreword ...................................................................................................................................................... 4
Introduction .................................................................................................................................................. 4
The name "MILENAGE" .................................................................................................................... 5
0
1
Outline of the document ...................................................................................................................... 5
References ................................................................................................................................................... 5
1.1
INTRODUCTORY INFORMATION ................................................................................................. 6
2
2.1
Introduction ................................................................................................................................................. 6
Notation ....................................................................................................................................................... 6
2.2
Radix...................................................................................................................................................... 6
2.2.1
2.2.2
Conventions ........................................................................................................................................... 6
2.2.3
Bit/Byte ordering .................................................................................................................................... 6
2.2.4
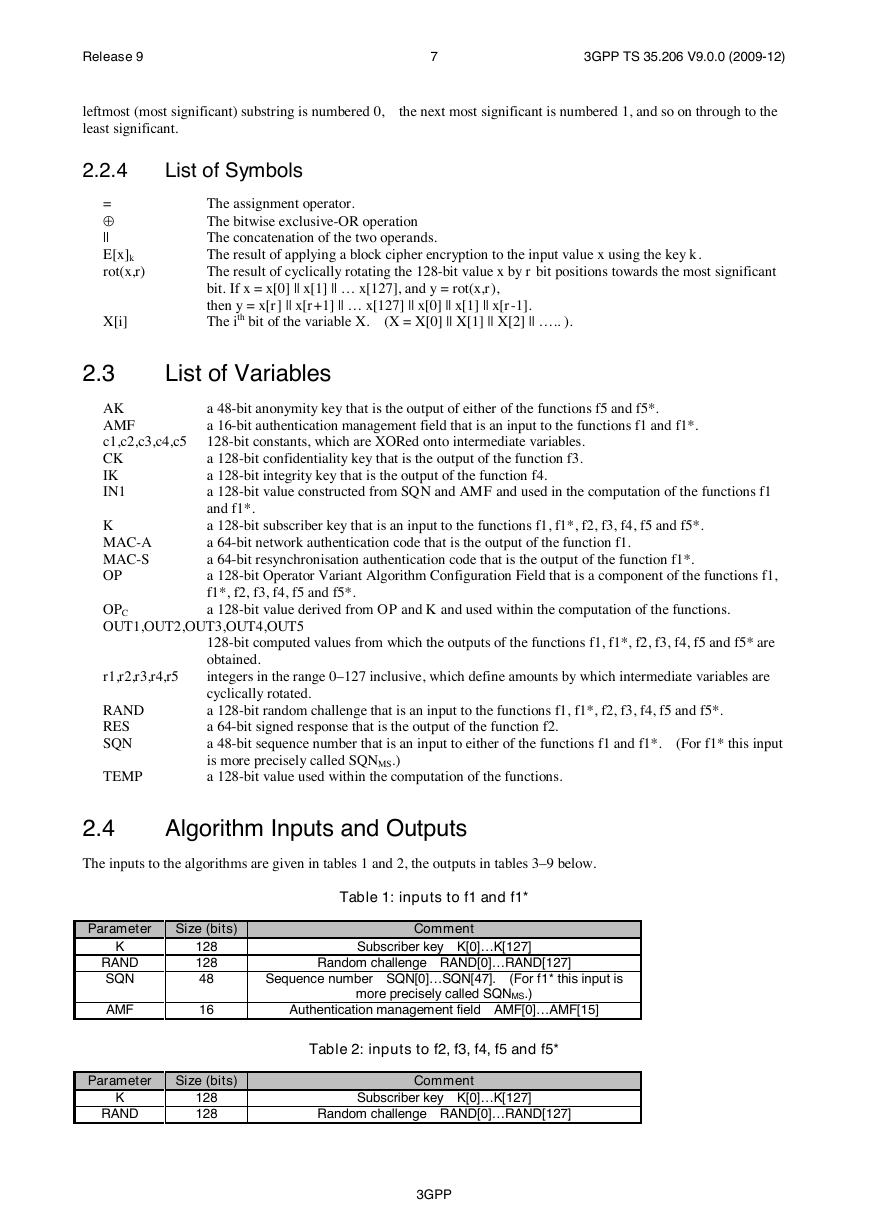
List of Symbols ...................................................................................................................................... 7
List of Variables........................................................................................................................................... 7
2.3
Algorithm Inputs and Outputs ...................................................................................................................... 7
2.4
3
The algorithm framework and the specific example algorithms ........................................................... 8
Definition of the example algorithms .................................................................................................. 9
4
4.1
Algorithm Framework .................................................................................................................................. 9
4.2
Specific Example Algorithms ....................................................................................................................... 9
Implementation considerations .......................................................................................................... 10
5
OPC computed on or off the USIM? ............................................................................................................ 10
5.1
Customising the choice of block cipher....................................................................................................... 10
5.2
5.3
Further customisation ................................................................................................................................. 11
5.4
Resistance to side channel attacks ............................................................................................................... 11
Figure of the Algorithms .................................................................................................. 12
Annex 1:
Specification of the Block Cipher Algorithm Rijndael.................................................... 13
Annex 2:
A2.1 Introduction ...................................................................................................................................... 13
A2.2 The State and External Interfaces of Rijndael .................................................................................... 13
A2.3 Internal Structure .............................................................................................................................. 14
A2.4 The Byte Substitution Transformation ............................................................................................... 14
A2.5 The Shift Row Transformation .......................................................................................................... 15
A2.6 The Mix Column Transformation ...................................................................................................... 15
A2.7 The Round Key addition ................................................................................................................... 16
A2.8 Key schedule .................................................................................................................................... 16
A2.9 The Rijndael S-box ........................................................................................................................... 17
Simulation Program Listing - Byte Oriented .................................................................. 18
Annex 3:
Rijndael Listing - 32-Bit Word Oriented ......................................................................... 25
Annex 4:
Change history ........................................................................................... 31
Annex A (informative):
3GPP
�
Release 9
4
3GPP TS 35.206 V9.0.0 (2009-12)
Foreword
This Technical Specification (TS) has been produced by the 3rd Generation Partnership Project (3GPP).
The contents of the present document are subject to continuing work within the TSG and may change following formal
TSG approval. Should the TSG modify the contents of the present document, it will be re-released by the TSG with an
identifying change of release date and an increase in version number as follows:
Version x.y.z
where:
x
the first digit:
1 presented to TSG for information;
2 presented to TSG for approval;
3 or greater indicates TSG approved document under change control.
y the second digit is incremented for all changes of substance, i.e. technical enhancements, corrections, updates,
etc.
z
the third digit is incremented when editorial only changes have been incorporated in the document.
Introduction
This document has been prepared by the 3GPP Task Force, and contains an example set of algorithms which may be
used as the authentication and key generation functions f1, f1*, f2, f3, f4, f5 and f5*. (It is not mandatory that the
particular algorithms specified in this document are used — all seven functions are operator-specifiable rather than
being fully standardised). This document is one five, which between them form the entire specification of the example
algorithms, entitled:
- 3GPP TS 35.205: "3rd Generation Partnership Project; Technical Specification Group Services and System
Aspects; 3G Security; Specification of the MILENAGE Algorithm Set: An example algorithm set for the 3GPP
authentication and key generation functions f1, f1*, f2, f3, f4, f5 and f5*;
Document 1: General".
- 3GPP TS 35.206: "3rd Generation Partnership Project; Technical Specification Group Services and System
Aspects; 3G Security; Specification of the MILENAGE Algorithm Set: An example algorithm set for the 3GPP
authentication and key generation functions f1, f1*, f2, f3, f4, f5 and f5*;
Document 2: Algorithm Specification".
- 3GPP TS 35.207: "3rd Generation Partnership Project; Technical Specification Group Services and System
Aspects; 3G Security; Specification of the MILENAGE Algorithm Set: An example algorithm set for the 3GPP
authentication and key generation functions f1, f1*, f2, f3, f4, f5 and f5*;
Document 3: Implementors' Test Data".
- 3GPP TS 35.208: "3rd Generation Partnership Project; Technical Specification Group Services and System
Aspects; 3G Security; Specification of the MILENAGE Algorithm Set: An example algorithm set for the 3GPP
authentication and key generation functions f1, f1*, f2, f3, f4, f5 and f5*;
Document 4: Design Conformance Test Data".
- 3GPP TR 35.909: "3rd Generation Partnership Project; Technical Specification Group Services and System
Aspects; 3G Security; Specification of the MILENAGE Algorithm Set: An example algorithm set for the 3GPP
authentication and key generation functions f1, f1*, f2, f3, f4, f5 and f5*;
Document 5: Summary and results of design and evaluation".
3GPP
�
Release 9
5
3GPP TS 35.206 V9.0.0 (2009-12)
The name "MILENAGE"
0
The name of this algorithm set is "MILENAGE". It should be pronounced like a French word — something like "mi-
le-nahj".
Outline of the document
1
Section 2 introduces the algorithms and describes the notation used in the subsequent sections.
Section 3 explains how the algorithms are designed as a framework in such a way that various "customising
components" can be selected in order to customise the algorithm for a particular operator.
Section 4 defines the example algorithms. The algorithm framework is defined in section 4.1; in section 4.2, specific
instances of the components are selected to define the specific example algorithm set.
Section 5 explains various options and considerations for implementation of the algorithms, including considerations to
be borne in mind when modifying the customising components.
Illustrative pictures are given in Annex 1. Annex 2 gives a specification of the block cipher algorithm which is used as a
cryptographic kernel in the definition of the example algorithms. Annexes 3 and 4 contain source code in the C
programming language: Annex 3 gives a complete and straightforward implementation of the algorithm set, while
Annex 4 gives an example of an alternative high-performance implementation just of the kernel function.
References
1.1
The following documents contain provisions which, through reference in this text, constitute provisions of the present
document.
References are either specific (identified by date of publication, edition number, version number, etc.) or
non-specific.
For a specific reference, subsequent revisions do not apply.
For a non-specific reference, the latest version applies. In the case of a reference to a 3GPP document
(including a GSM document), a non-specific reference implicitly refers to the latest version of that document in
the same Release as the present document.
[1]
[2]
[3]
[4]
[5]
3GPP TS 33.102 v3.5.0: "3rd Generation Partnership Project; Technical Specification Group
Services and System Aspects; 3G Security; Security Architecture".
3GPP TS 33.105 v3.4.0: "3rd Generation Partnership Project; Technical Specification Group
Services and System Aspects; 3G Security; Cryptographic Algorithm Requirements".
3GPP TS 35.206: "3rd Generation Partnership Project; Technical Specification Group Services
and System Aspects; 3G Security; Specification of the MILENAGE Algorithm Set: An example
algorithm set for the 3GPP authentication and key generation functions f1, f1*, f2, f3, f4, f5 and
f5*; Document 2: Algorithm Specification" (this document).
3GPP TS 35.207: "3rd Generation Partnership Project; Technical Specification Group Services
and System Aspects; 3G Security; Specification of the MILENAGE Algorithm Set: An example
algorithm set for the 3GPP authentication and key generation functions f1, f1*, f2, f3, f4, f5 and
f5*; Document 3: Implementors' Test Data".
3GPP TS 35.208: "3rd Generation Partnership Project; Technical Specification Group Services
and System Aspects; 3G Security; Specification of the MILENAGE Algorithm Set: An example
algorithm set for the 3GPP authentication and key generation functions f1, f1*, f2, f3, f4, f5 and
f5*; Document 4: Design Conformance Test Data".
3GPP
�
Release 9
6
3GPP TS 35.206 V9.0.0 (2009-12)
[6]
[7]
[8]
[9]
[10]
[11]
[12]
[13]
Joan Daemen and Vincent Rijmen: "AES Proposal: Rijndael", available at
http://csrc.nist.gov/encryption/aes/round2/AESAlgs/Rijndael/Rijndael.pdf or
http://www.esat.kuleuven.ac.be/~rijmen/rijndael/rijndaeldocV2.zip
http://csrc.nist.gov/encryption/aes/
Thomas S. Messerges, "Securing the AES finalists against Power Analysis Attacks", in FSE 2000,
Seventh Fast Software Encryption Workshop, ed. Schneier, Springer Verlag, 2000.
P. C. Kocher, "Timing Attacks on Implementations of Diffie-Hellman, RSA, DSS, and Other
Systems", in CRYPTO'96, Lecture Notes in Computer Science #1109, Springer Verlag, 1996.
J. Kelsey, B. Schneier, D. Wagner, C. Hall, "Side Channel Cryptanalysis of Product Ciphers", in
ESORICS'98, Lecture Notes in Computer Science #1485, Springer Verlag, 1998.
L. Goubin, J. Patarin, "DES and differential power analysis", in CHES'99, Lecture Notes in
Computer Science #1717, Springer Verlag, 1999.
P. Kocher, J. Jaffe, B. Jun, "Differential Power Analysis", in CRYPTO'99, Lecture Notes in
Computer Science #1666, Springer Verlag, 1999.
L. Goubin, J.-S. Coron, "On boolean and arithmetic masking against differential power analysis",
in CHES'00, Lecture Notes in Computer Science series, Springer Verlag (to appear).
2
INTRODUCTORY INFORMATION
Introduction
2.1
Within the security architecture of the 3GPP system there are seven security functions f1, f1*, f2, f3, f4, f5 and f5*.
The operation of these functions falls within the domain of one operator, and the functions are therefore to be specified
by each operator rather than being fully standardised. The algorithms specified in this document are examples that
may be used by an operator who does not wish to design his own.
The inputs and outputs of all seven algorithms are defined in section 2.4.
2.2
Notation
Radix
2.2.1
We use the prefix 0x to indicate hexadecimal numbers.
Conventions
2.2.2
We use the assignment operator '=', as used in several programming languages. When we write
=
we mean that assumes the value that had before the assignment took place. For instance,
means
x = x + y + 3
(new value of x) becomes (old value of x) + (old value of y) + 3.
Bit/Byte ordering
2.2.3
All data variables in this specification are presented with the most significant bit (or byte) on the left hand side and the
least significant bit (or byte) on the right hand side. Where a variable is broken down into a number of substrings, the
3GPP
�
Release 9
7
3GPP TS 35.206 V9.0.0 (2009-12)
leftmost (most significant) substring is numbered 0, the next most significant is numbered 1, and so on through to the
least significant.
2.2.4
List of Symbols
The assignment operator.
The bitwise exclusive-OR operation
The concatenation of the two operands.
The result of applying a block cipher encryption to the input value x using the key k.
The result of cyclically rotating the 128-bit value x by r bit positions towards the most significant
bit. If x = x[0] || x[1] || … x[127], and y = rot(x,r),
then y = x[r] || x[r+1] || … x[127] || x[0] || x[1] || x[r-1].
The ith bit of the variable X. (X = X[0] || X[1] || X[2] || ….. ).
List of Variables
a 48-bit anonymity key that is the output of either of the functions f5 and f5*.
a 16-bit authentication management field that is an input to the functions f1 and f1*.
128-bit constants, which are XORed onto intermediate variables.
a 128-bit confidentiality key that is the output of the function f3.
a 128-bit integrity key that is the output of the function f4.
a 128-bit value constructed from SQN and AMF and used in the computation of the functions f1
and f1*.
a 128-bit subscriber key that is an input to the functions f1, f1*, f2, f3, f4, f5 and f5*.
a 64-bit network authentication code that is the output of the function f1.
a 64-bit resynchronisation authentication code that is the output of the function f1*.
a 128-bit Operator Variant Algorithm Configuration Field that is a component of the functions f1,
f1*, f2, f3, f4, f5 and f5*.
a 128-bit value derived from OP and K and used within the computation of the functions.
=
||
E[x]k
rot(x,r)
X[i]
2.3
AK
AMF
c1,c2,c3,c4,c5
CK
IK
IN1
K
MAC-A
MAC-S
OP
OPC
OUT1,OUT2,OUT3,OUT4,OUT5
r1,r2,r3,r4,r5
RAND
RES
SQN
128-bit computed values from which the outputs of the functions f1, f1*, f2, f3, f4, f5 and f5* are
obtained.
integers in the range 0–127 inclusive, which define amounts by which intermediate variables are
cyclically rotated.
a 128-bit random challenge that is an input to the functions f1, f1*, f2, f3, f4, f5 and f5*.
a 64-bit signed response that is the output of the function f2.
a 48-bit sequence number that is an input to either of the functions f1 and f1*. (For f1* this input
is more precisely called SQNMS.)
a 128-bit value used within the computation of the functions.
TEMP
2.4
The inputs to the algorithms are given in tables 1 and 2, the outputs in tables 3–9 below.
Algorithm Inputs and Outputs
Parameter
K
RAND
SQN
Size (bits)
128
128
48
AMF
16
Parameter
K
RAND
Size (bits)
128
128
Table 1: inputs to f1 and f1*
Comment
Subscriber key K[0]…K[127]
Random challenge RAND[0]…RAND[127]
Sequence number SQN[0]…SQN[47]. (For f1* this input is
more precisely called SQNMS.)
Authentication management field AMF[0]…AMF[15]
Table 2: inputs to f2, f3, f4, f5 and f5*
Comment
Subscriber key K[0]…K[127]
Random challenge RAND[0]…RAND[127]
3GPP
�
Release 9
8
3GPP TS 35.206 V9.0.0 (2009-12)
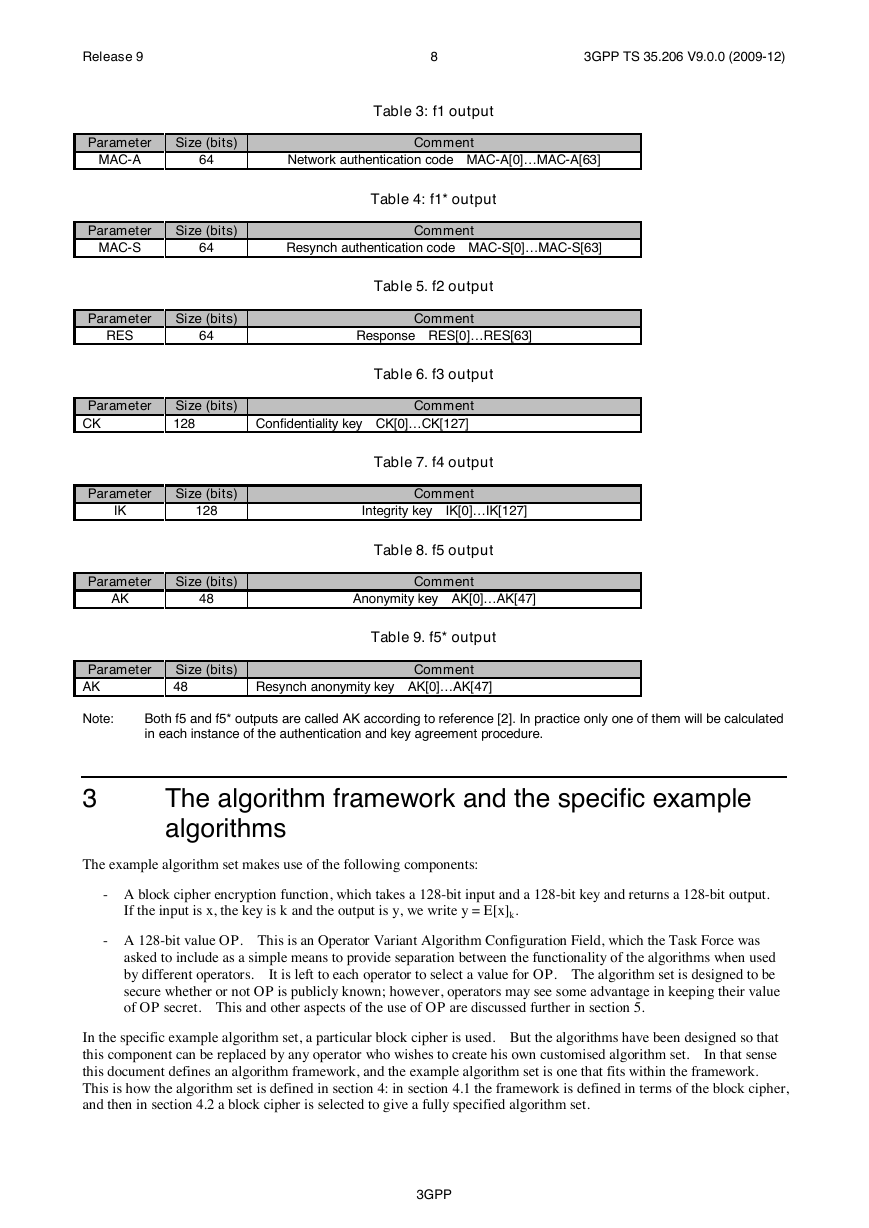
Table 3: f1 output
Parameter
MAC-A
Size (bits)
64
Network authentication code MAC-A[0]…MAC-A[63]
Comment
Parameter
MAC-S
Size (bits)
64
Resynch authentication code MAC-S[0]…MAC-S[63]
Comment
Table 4: f1* output
Parameter
RES
Size (bits)
64
Table 5. f2 output
Comment
Response RES[0]…RES[63]
Table 6. f3 output
Parameter
CK
Size (bits)
128
Comment
Confidentiality key CK[0]…CK[127]
Parameter
IK
Size (bits)
128
Parameter
AK
Size (bits)
48
Table 7. f4 output
Comment
Integrity key IK[0]…IK[127]
Table 8. f5 output
Comment
Anonymity key AK[0]…AK[47]
Table 9. f5* output
Size (bits)
48
Resynch anonymity key AK[0]…AK[47]
Comment
Both f5 and f5* outputs are called AK according to reference [2]. In practice only one of them will be calculated
in each instance of the authentication and key agreement procedure.
Parameter
AK
Note:
3
The algorithm framework and the specific example
algorithms
The example algorithm set makes use of the following components:
- A block cipher encryption function, which takes a 128-bit input and a 128-bit key and returns a 128-bit output.
If the input is x, the key is k and the output is y, we write y = E[x]k.
- A 128-bit value OP. This is an Operator Variant Algorithm Configuration Field, which the Task Force was
asked to include as a simple means to provide separation between the functionality of the algorithms when used
by different operators. It is left to each operator to select a value for OP. The algorithm set is designed to be
secure whether or not OP is publicly known; however, operators may see some advantage in keeping their value
of OP secret. This and other aspects of the use of OP are discussed further in section 5.
In the specific example algorithm set, a particular block cipher is used. But the algorithms have been designed so that
this component can be replaced by any operator who wishes to create his own customised algorithm set. In that sense
this document defines an algorithm framework, and the example algorithm set is one that fits within the framework.
This is how the algorithm set is defined in section 4: in section 4.1 the framework is defined in terms of the block cipher,
and then in section 4.2 a block cipher is selected to give a fully specified algorithm set.
3GPP
�














 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc