Chapter01
Chapter 1
Introduction
Exercises
1. As of January 2009, the RFC with the highest number is RFC 5459, titled RTP Payload Format Update.
3. RFC 2014: This RFC discusses the IRTF working group guidelines and procedures.
5. RFC 3692 and RFC 1410 are two examples of experimental RFCs.
7. The main RFC for FTP is RFC 959 that has become the standard STD0009.
9. The main RFC related to TCP is RFC 793 (J. Postel) that has become the standard STD0007.
Chapter02
Chapter 2
The OSI Model and the TCP/IP Protocol Suite
Exercises
1. The International Standards Organization (ISO) is a multinational body dedicated to worldwide agreement on international standards. An ISO standard that covers all aspects of network communications is the Open Systems Interconnection (OSI) model.
3.
a. Transport layer
b. Network layer
c. Data link layer
d. Application layer
e. Physical layer
5.
a. Presentation layer
b. Session layer
c. Data link and transport layers
d. Session layer
e. Presentation layer
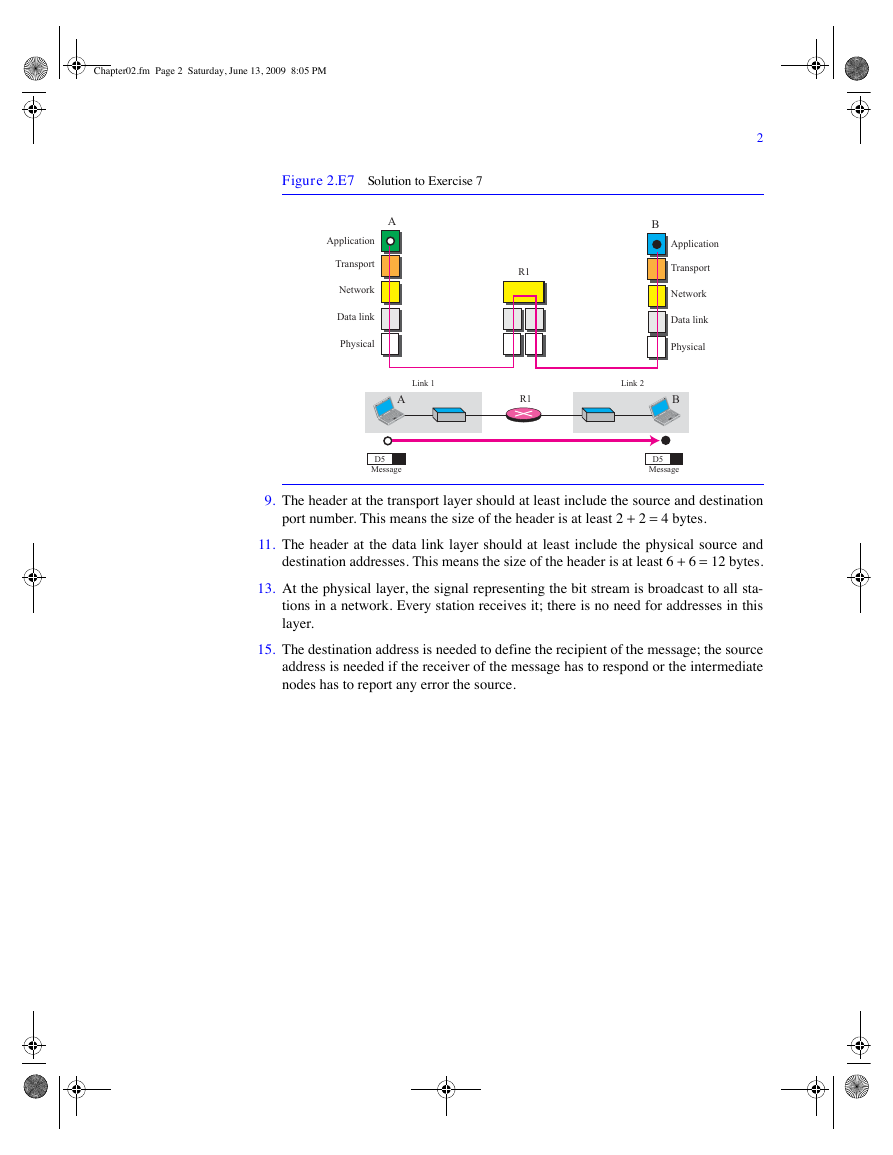
7. If we think about the switch as a passive one (not a bridge), Figure 2.E7 shows the solution.
Figure 2.E7 Solution to Exercise 7
9. The header at the transport layer should at least include the source and destination port number. This means the size of the header is at least 2 + 2 = 4 bytes.
11. The header at the data link layer should at least include the physical source and destination addresses. This means the size of the header is at least 6 + 6 = 12 bytes.
13. At the physical layer, the signal representing the bit stream is broadcast to all stations in a network. Every station receives it; there is no need for addresses in this layer.
15. The destination address is needed to define the recipient of the message; the source address is needed if the receiver of the message has to respond or the intermediate nodes has to report any error the source.
Chapter03
Chapter 3
Underlying Technologies
Exercises
1. We know that D = T ´ V, where D is the distance, T is the time, and V is the velocity or speed. In other words, T = D / V. We insert the corresponding values to find the time needed for a bit to travel the cable.
T = D / V = (2500 meters) / (200,000,000 meters/second) = 0.0000125 s = 12.5 ms
3. Assume that the minimum frame size is 65 bytes or 520 bits. We have L = T ´ R, where L is the length of the frame, T is the time, and the R is the data rate. We can say T = L / R. The time can be calculated as
T = L / R = (520 bits) / (10,000,000) bits/second = 0.000052 s = 52 ms
5. The padding needs to make the size of the data section 46 bytes. If the data received from the upper layer is 42 bytes, we need 46 - 42 = 4 bytes of padding.
7.
a. Similarities: Each station has an equal right to the medium. Each station senses the medium.
b. Differences: CSMA/CD: A station can send if it senses no signal on the line. CSMA/CA: A station needs to inform other stations that it needs the medium for a specific amount of time.
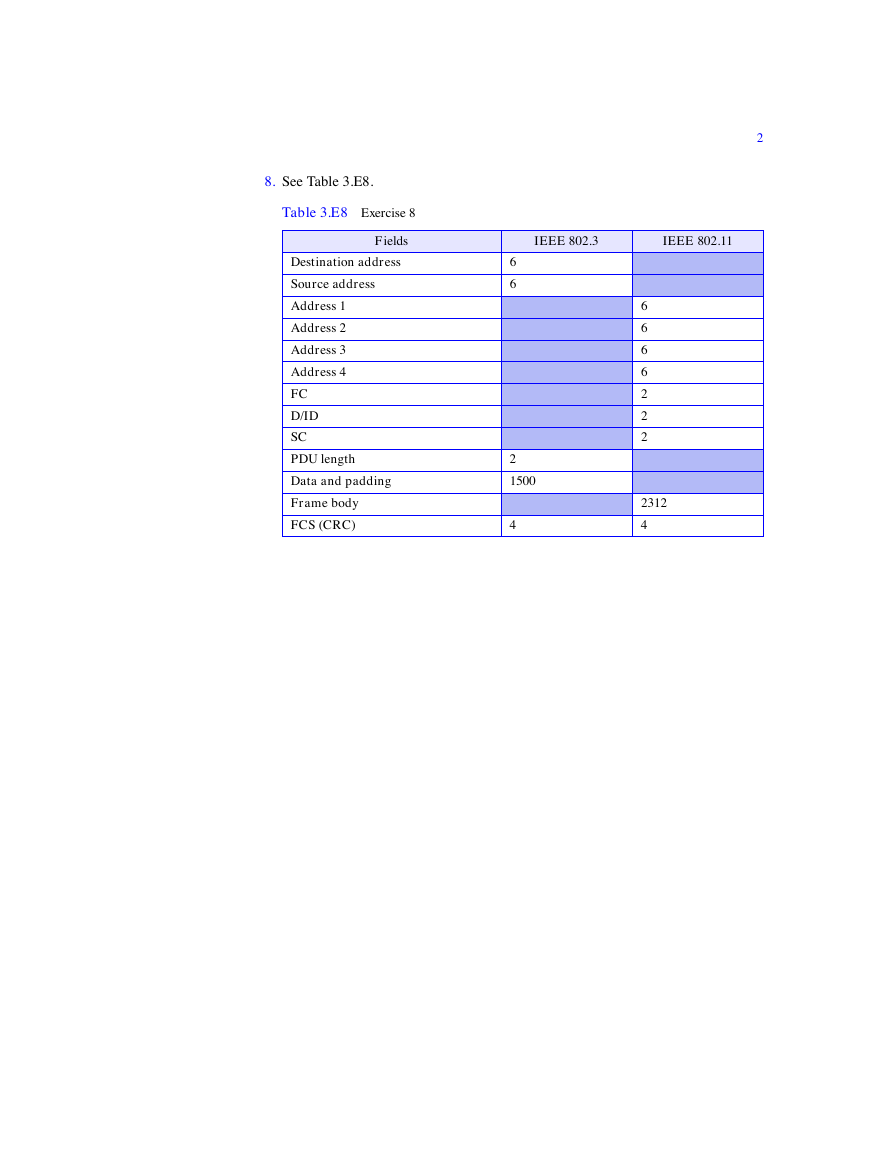
8. See Table 3.E8.
Table 3.E8 Exercise 8
Fields
IEEE 802.3
IEEE 802.11
Chapter04
Chapter 4
Introduction to Network Layer
Exercises
1. We mention one advantage and one disadvantage for a connectionless service:
a. The connectionless service has at least one advantage. A connectionless service is simple. The source, destination, and the routers need to deal with each packet individually without considering the relationship between them. This means there are ...
b. The connectionless service has at least one disadvantage. The packets may arrive out of order; the upper layer that receive them needs to reorder them.
3. An n-bit label can create 2n different virtual-circuit identifier.
5. Each packet started from the source needs to have a fragmentation identification, which is repeated in each fragment. The destination computer use this identification to reassemble all fragments belonging to the same packet.
7. The delay in the connection-oriented service is always more than the delay in the connectionless service no matter the message is long or short. However, the ratio of the overhead delay (setup and teardown phases) to the data transfer delay (trans...
9. A router is normally connected to different link (networks), each with different MTU. The link from which the packet is received may have a larger MTU than the link to which the packet is sent, which means that router needs to fragment the packet....
11. A fragment may have been lost and never arrives. The destination host cannot wait forever. The destination host starts a time and after the time-out, it can sends an error message (see Chapter 9) to inform the source host that the packet is lost ...
Chapter05
Chapter 5
IPv4 Addresses
Exercises
1.
a. 28 = 256 addresses
b. 216 = 65536 addresses
c. 264 = 1.846744737 × 1019 addresses
3. 310 = 59,049 addresses
5.
a. 0x72220208
b. 0x810E0608
c. 0xD022360C
d. 0xEE220201
7.
a. (8 bits) / (4 bits per hex digits) = 2 hex digits
b. (16 bits) / (4 bits per hex digits) = 4 hex digits
c. (24 bits) / (4 bits per hex digits) = 6 hex digits
9. We use Figure 5.6 (the right table) to find the class:
a. The first byte is 208 (between 192 and 223) ® Class C
b. The first byte is 238 (between 224 and 299) ® Class D
c. The first byte is 242 (between 240 and 255) ® Class E
d. The first byte is 129 (between 000 and 127) ® Class A
11.
a. Class is A ® netid: 114 and hostid: 34.2.8
b. Class is B ® netid: 132.56 and hostid: 8.6
c. Class is C ® netid: 208.34.54 and hostid: 12
d. Class is E ® The address is not divided into netid and hostid.
13. We first change the number of addresses in the range (minus 1) to base 256
2,048 - 1 = (0.0.7.255)256
First Address:
122
.
12
.
7
.
0
0
.
0
.
7
.
255
Last Address:
122
.
12
.
14
.
255
15.
a. We can apply the first short cut to all bytes here. The result is (22.14.0.0).
b. We can apply the first short cut to all bytes here. The result is (12.0.0.0).
c. We can apply the first short cut to bytes 1and 4; we need to apply the second short cut to bytes 2 and 3. The result is (14.72.0.0).
d. We can apply the first short cut to bytes 1 and 4; we need to apply the second short cut to bytes 2 and 3. The result is (28.0.32.0).
17. The first address can be found by ANDing the mask with the IP address as shown below: The last address can be found by either adding the number of addresses in the subnet 232 - n = 216 or by ORing the complement of the mask with the IP address (s...
IP Address:
25
.
34
.
12
.
56
255
.
255
.
0
.
0
25
.
34
.
0
.
0
IP Address:
25
.
34
.
12
.
56
0
.
0
.
255
.
255
25
.
34
.
255
.
255
19. The first address can be found by ANDing the mask with the IP address as shown below:
IP Address:
202
.
44
.
82
.
16
255
.
255
.
255
.
192
202
.
44
.
82
.
0
16
®
0
+
0
+
0
+
16
+
0
+
0
+
0
+
0
192
®
128
+
64
+
32
+
0
+
0
+
0
+
0
+
0
0
®
0
+
0
+
0
+
0
+
0
+
0
+
0
+
0
IP Address:
202
.
44
.
82
.
16
0
.
0
.
0
.
63
202
.
44
.
82
.
127
16
®
0
+
64
+
32
+
16
+
0
+
0
+
0
+
0
63
®
0
+
0
+
32
+
16
+
8
+
4
+
2
+
1
127
®
0
+
64
+
32
+
16
+
8
+
4
+
2
+
1
21. With the information given, the first address is found by ANDing the host address with the mask 255.255.0.0 (/16). The last address can be found by ORing the host address with the mask complement 0.0.255.255. However, we need to mention that this...
23. See below. The number of created subnets are equal to or greater than required.
a. log22 = 1
b. log262 = 5.95
c. log2122 = 6.93
d. log2250 = 7.96
25.
a. log21024 = 10 Extra 1s = 10 Possible subnets: 1024 Mask: /26
b. 232- 26 = 64 addresses in each subnet
c. First subnet: The first address is the beginning address of the block. To find the last address, we need to write 63 (one less than the number of addresses in each subnet) in base 256 (0.0.0.63) and add it to the first address (in base 256).
d. Last subnet (Subnet 1024): To find the first address in subnet 1024, we need to add 65,472 (1023 ´ 64) in base 256 (0.0.255.92) to the first address in subnet 1. Now we can calculate the last address in subnet 1024 as we did for the first address.
27. We first change the mask to binary to find the number of 1’s:
a. 11111111 11111111 11111111 00000000 ® /24
b. 11111111 00000000 00000000 00000000 ® /8
c. 11111111 11111111 11100000 00000000 ® /19
d. 11111111 11111111 11110000 00000000 ® /20
29. If the first and the last addresses are known, the block is fully defined. We can first find the number of addresses in the block. We can then use the relation
N = 232 - n ® n = 32 - log2N
n = 32 - log2N = 32 - log264 = 26
31. Many blocks can have the same prefix length. The prefix length only determines the number of addresses in the block, not the block itself. Two blocks can have the same prefix length but start in two different point in the address space. For examp...
127.15.12.32/27
174.18.19.64/27
33.
35. There are actually two choices. If the ISP wants to use subnetting (a router with 32 output ports) then the prefix length for each customer is nsub = 32. However, there is no need for a router and subnetting. Each customer can be directly connect...
Chapter06
Chapter 6
Delivery, Forwarding, and Routing of IP Packets
Exercises
1. Direct; Both hosts are on the same network (same netid: 137.23).
3. See Table 6.E3.
Table 6.E3 Solution to Exercise 3
Class
Destination
Next Hop
Interface
Class A
111.0.0.0
¾
m1
Class B
145.80.0.0
111.25.19.20
m1
170.14.0.0
111.25.19.20
m1
Class C
192.16.7.0
111.15.17.32
m1
Default
0
default router
m0
5. Destination address: 192.16.7.42
7. Destination address: 147.26.50.30
9. Destination address: 135.11.80.21
11. Destination address: 202.70.20.30
Mask: /26
Result: 202.70.20.0
No match
Mask: /25
Result: 202.70.20.0
No match
Mask: /24
Result: 202.70.20.0
No match
Mask: /22
Result: 202.70.20.0
No match
13. A routing table for a LAN not connected to the Internet and with no subnets can have a routing table with host-specific addresses. There is no next-hop address since all packets remain within the network.
15. If the packet with destination address 140.24.7.194 arrives at R3, it gets sent to interface m0. If it arrives at R2, it gets sent to interface m1 and then to router R3. The only way R1 can receive the packet is if the packet comes from organizat...
17. See Table 6.E17.
Table 6.E17 Solution to Exercise 17
Mask
Network address
Next-hop address
Interface
/20
120.14.64.0
¾
m0
/20
120.14.96.0
¾
m2
/20
120.14.112.0
¾
m3
/0
0.0.0.0
default router
m4
19. See Table 6.E19.
Table 6.E19 Solution to Exercise 19
Mask
Network address
Next-hop address
Interface
/22
120.14.96.0
¾
m0
/22
120.14.100.0
¾
m1
/22
120.14.104.0
¾
m2
/22
120.14.108.0
¾
m3
/0
0.0.0.0
default router
m4
21. See Table 6.E21.
Table 6.E21 Solution to Exercise 21
Mask
Network address
Next-hop address
Interface
/30
120.14.64.0
¾
m0
/30
120.14.64.4
¾
m1
/30
120.14.64.8
¾
m2
/30
120.14.64.12
¾
m3
¼
¼
¼
¼
/30
120.14.65.252
¾
m127
/0
0.0.0.0
default router
m128
Chapter07
Chapter 7
Internet Protocol Version 4 (IPv4)
Exercises
1. If no fragmentation occurs at the router, then the only field to change in the base header is the time to live field. If any of the multiple-byte options are present, then there will be changes in the option headers as well (to record the route an...
3.
5. In this case, we use a Loose Source Route option with only one entry as shown in Figure 7.E5.
Figure 7.E5 Solution to Exercise 5
7. The value of the header length field of an IP packet can never be less than 5 because every IP datagram must have at least a base header that has a fixed size of 20 bytes. The value of HLEN field, when multiplied by 4, gives the number of bytes co...
9. If the size of the option field is 20 bytes, then the total length of the header is 40 bytes (20 byte base header plus 20 bytes of options). The HLEN field will be the total number of bytes in the header divided by 4, in this case ten (1010 in bin...
11. HLEN field : 5 = (0101)2
Total length field : 1044 = (00000100 00010100)2
13. If the fragmentation offset is 0 and the more fragment bit is off, this is not a fragment.
15.
a. There are no options.
b. The packet is not fragmented.
c. The packet carries 64 bytes of data.
d. The header is 20 bytes long.
e. The checksum is not used.
f. The packet may visit up to 32 more routers.
g. The identification number of the packet is 3 (decimal). The type of service is normal.
Chapter08
Chapter 8
Address Resolution Protocol (ARP)
Exercises
1. The size of an ARP packet is variable, depending on the length of addresses.
3. An ARP packet is normally less than minimum Ethernet payload. The size of an Ethernet frame carrying an ARP packet is therefore 72 bytes.
5. See Figure 8.E5. Note that although the problem mentions the physical address of the destination, it is assumed that ARP will find this address. The problem gives the destination physical address to be filled in the ARP reply packet.
Figure 8.E5 Solution to Exercise 5
7. See Figure 8.E7
Figure 8.E7 Solution to Exercise 7
9. See Figure 8.E9.
Figure 8.E9 Solution to Exercise 9
Chapter09
Chapter 9
Internet Control Message Protocol Version 4 (ICMPv4)
Exercises
1.
a. The original message is lost in transit. The sender can re-send the message.
b. The reply is lost in transit. The sender can re-send the message.
c. The original message was corrupted and discarded. The sender can re-send the message.
3. It could happen that host B is unreachable, for some reason. The error message generated by an intermediate router could then be lost on its way back to host A. Or perhaps the datagram was dropped due to congestion and the error message generated ...
5. The maximum value is 59 because the pointer points to a byte somewhere in the original IP header (a maximum of 60 bytes). An offset of 0 would point to the first byte, so an offset of 59 would point to the 60th byte.
7. See Table 9.E7.
Table 9.E7 Solution to Exercise 7
Category
Type
Code
Non-Dest. host
Router
Destin. host
Error
Destination
unreachable
0
Ö
1
Ö
2
Ö
3
Ö
4
Ö
5
Ö
6
Ö
7
Ö
8
Ö
9
Ö
10
Ö
11
Ö
12
Ö
13
Ö
14
Ö
15
Ö
Source quench
0
Ö
Ö
Time exceeded
0
Ö
1
Ö
Parameter problem
0
Ö
Ö
Redirection
0
Ö
Query
Echo request
0
Ö
Ö
Ö
Echo reply
0
Ö
Ö
Ö
Timestamp request
0
Ö
Timestamp reply
0
Ö
9. The one way time is not the round trip divided by 2 because the request packet may have traveled by a different route than the response packet. In this case, the transmission time in one direction may be different than the transmission time in the...
11. The minimum size of an IP packet that carries an ICMP packet would be 28 bytes (a 20 byte IP header + an 8 byte router solicitation packet). The maximum size would be 2068 bytes (a 20 byte IP header + a 2048 byte router advertisement packet).
13. The value of the protocol field of an IP packet carrying an ICMP packet is 1.
15. See Figure 9.E15.
Figure 9.E15 Solution to Exercise 15
17. The type in this message is 3, which means it is a destination unreachable message. The code in this message is 3, which means that the target port is unreachable. The purpose of this message is to inform the sender that the destination port is n...
19. See Figure 9.E19.
Figure 9.E19 Solution to Exercise 19
21.
2:34:20 PM = 52,460,000 ms
52,460,000 ms - 52,453,000 ms = 7000 ms
7000 ms + 5 ms = 7005 milliseconds
23. Assume that the message travels at 2 ´ 108 meters/second and that 6.2 miles equals 10 kilometers.
(5000) (10)/6.2 = 8064.5 km = 8.06 ´ 106 meters
(8.06 ´ 106 meters)/ 2 ´ 108 meters/second = 4.03 ´ 10-2 s = 40.3 ms
Chapter10
Chapter 10
Mobile IP
Exercises
1. If a mobile host acts as a foreign agent, registration is still required. The mobile host/foreign agent still needs to identify itself to the home agent.
3. See Figure 10.E3.
Figure 10.E3 Solution to Exercise 3
5. An ICMP router solicitation message can also be used for agent solicitation by a mobile host. No extra fields are needed.
7. See Figure 10.E7. The protocol field is set to 1 to indicate ICMP.
Figure 10.E7 Solution to Exercise 7
9. See Figure 10.E9.
Figure 10.E9 Solution to Exercise 9
11. See Figure 10.E11.
Figure 10.E11 Solution to Exercise 11
13. Triangle routing is a case of inefficiency. The packet travels to an extra network before it reaches the destination.
Chapter11
Chapter 11
Unicast Routing Protocols (RIP, OSPF, and BGP)
Exercises
1. The expiration timer value is 6 times that of the periodic timer to allow for some missed communication between routers.
3. In distance vector routing each router sends all of its knowledge about an autonomous system to all of the routers on its neighboring networks at regular intervals. It uses a fairly simple algorithm to update the routing tables but results in a lo...
5.
a. The size of a RIP message that advertises a single network is 24 bytes.
b. The size of a RIP message that advertises N networks is (4 + 20 ´ N) bytes.
c. The general formula can be given as 4 + (20 ´ N)
7. See Figure 11.E7.
Figure 11.E7 Solution to Exercise 7
9. The general header has two empty bytes (set to 0’s). Each advertisement section has 10 empty bytes. This means we have 2 + (10 ´ N) empty bytes in a message advertising N networks.
11. See Figure 11.E11.
Figure 11.E11 Solution to Exercise 11
13. Figure 11.E13 shows the autonomous system and the graphical representation. N3 and N4 are stub networks; N1, N2, N5, and N6 are transient networks..
Figure 11.E13 Solution to Exercise 13
15. See Figure 11.E15. We have revised each routing table to shows the change.
Figure 11.E15 Solution to Exercise 15
17. See Figure 11.E17. We have written a Java program based on the pseudocode defined in the text to calculate the distances. The cost and the distances are represented as two dimensional tables. Rows are sources; columns are destinations.
Figure 11.E17 Solution to Exercise 17
19. Figure 11.E19 shows how to find the shortest path tree for node B.
Figure 11.E19 Solution to Exercise 19
21. Figure 11.E21 shows how to find the shortest path tree for node G.
Figure 11.E21 Solution to Exercise 21
Chapter12
Chapter 12
Multicasting and Multicast Routing Protocols
Exercises
1. If we want to find CIDR notation for a range of addresses when the first and last address in the block are given, we need to find the value of n (the prefix length). One way to do that is to find the maximum number of the same rightmost bits in bo...
a. The block does not pass the test because there is one 1 in the suffix of the first address. This block can be split into several smaller CIDR blocks in the future.
b. The block does not pass the test because there are two 1’s in the suffix of the first address. This block can be split into several smaller CIDR blocks in the future.
c. The block does not pass the test because there is one 1 in the suffix of the first address and one 0 in the suffix of the last address. This block can be split into several smaller CIDR blocks in the future.
3. We use binary notation to do transformation: The resulting address in hexadecimal is: 01:00:5E:18:3C:09. Using the same method, we get the same result.
5. There is no need for a report message to travel outside of its own network because its only purpose is to inform the next router in the spanning tree of group membership. There is no need for a query message to travel outside of the local network ...
7. The membership report message is [8 + 3 ´ (8 + 5 ´ 4)] = 92 bytes long. We cannot give a general formula for the size because the number of specific addresses in each record may be different.
9. See Figure 12.E9.
Figure 12.E9 Solution to Exercise 9
11. Figure 12.E11 shows the header and group records. We use record type 6 to exclude any message from the only source defines in the previous report.
Figure 12.E11 Solution to Exercise 11
13. Figure 12.E13 shows the state.
Figure 12.E13 Solution to Exercise 13
15.
a. This is a query message.
b. The checksum is 0xEEFF or (1110 1110 1111 1111)2.
c. The group address is (E80E1508)16 or 232.14.21.8.
17. This is a repeat of Exercise 4, but we repeat the solution below. In each case, we find the rightmost three bytes, subtract 8 from the leftmost digit if it is greater than 8, and add result to the starting Ethernet address. Note that a and b repr...
a.
b.
c.
d.
19. See Tables below:
R2 Table
R3 Table
R4 Table
Dest.
Next-hop
Dest.
Next-hop
Dest.
Next-hop
G1
---, R1, R3
G1
---, R2
G1
---, R1
G2
---, R3
G2
---, R2
G2
R1
G3
---, R1
G3
---, R2
G3
---, R1
G4
R1, R3
G4
---, R2
G4
---, R1
G5
---, R1
G5
---, R2
G5
---, R1
21. Router B is the designated parent router.
23. Yes, RPB creates a shortest path tree because a multicast packet reaches every network and that network receives only one copy of the packet. The leaves of the tree are the networks .
Chapter13
Chapter 13
Introduction to Transport Layer
Exercises
1. The sequence number of any packet can be found using the following relation:
seqNo = (starting segNo + packet number -1) mod 2m
seqNo = (0 + 100 - 1) mod 25 = 99 mod 32 = 3
3. See Figure 13.E3.
Figure 13.E3 Solution to Exercise 3
5. Figure 13.E5 shows the outline. Note that since the simple protocol provide no error control, if a packet is lost, the receiving process is responsible to find a solution. The transport layer is not even aware that this has happened.The packets ma...
Figure 13.E5 Solution to Exercise 5
7. See Figure 13.E7.
Figure 13.E7 Solution to Exercise 7
9. See Figure 13.E9.
Figure 13.E9 Solution to Exercise 9
11. We assume each event is independent.
a. seqNo = 15.
b. Five packets with seqNo set to 10, 11, 12, 13, and 14 are to be resent.
c. Sf = 13 and Sn = 15.
d. The size of the window remains the same. Max Wsize = 26 - 1 = 63.
e. Sf = 18 and Sn = 21 Next state = ready
f. Rn = 17 Action: an ACK with ackNo = 17 is sent.
Chapter14
Chapter 14
User Datagram Protocol (UDP)
Exercises
1. Reliability is not of primary importance in applications such as echo, daytime, BOOTP, TFTP and SNMP. In custom software, reliability can be built into the client/server applications to provide a more reliable, low overhead service.
3. See Figure 14.E3
Figure 14.E3 Solution to Exercise 3
5. The server would use the IP address 130.45.12.7, combined with the well-known port number 69 for its source socket address and the IP address 14.90.90.33, combined with an ephemeral port number as the destination socket address.
7. Efficiency = (16 bytes of data) / (24 bytes of total length) = 0.666 = 66.6 percent.
9. Efficiency = (16 bytes of data) / (72 byte minimum frame size) = 0.222 = 22.2 percent.
Chapter15
Chapter 15
Transmission Control Protocol (TCP)
Exercises
1. See Table 15.E1. Note that the only field that exists in UDP, but is missing in TCP, is the total length field. The designer of TCP did not feel that this field is needed because the size of the TCP segment can be determined from the size of the I...
Table 15.E1 Solution to Exercise 1
Fields
UDP
TCP
Purpose
Ö
Ö
To define the source port number
Ö
Ö
To define the destination port number
Ö
Ö
For error control
Ö
It is not actually needed even in UDP
Ö
For flow control
Ö
For flow control
Ö
To define variable header length in TCP
Ö
To define different type of segments
Ö
To define the end of urgent data
Ö
To make TCP to use different options
3. The port is not listed in the transmission control block, which means no process is running associated to this port.
5.
a. The maximum size of the TCP header is 60 bytes (20 bytes of header and a maximum 40 bytes of options).
b. The minimum size of the TCP header is 20 bytes.
7. See Figure 15.E7.
Figure 15.E7 Solution to Exercise 7
9.
a. The source port number is 0532 in hex and 1330 in decimal.
b. The destination port number is 0017 in hex and 23 in decimal.
c. The sequence number is 00000001 in hex and 1 in decimal.
d. The acknowledgment number is 00000000 in hex and 0 in decimal.
e. The HLEN = 5. The header is 5 ´ 4 = 20 bytes long.
f. The control field is 002 in hex. This indicates a SYN segment used for connection establishment.
g. The window size field is 07FF in hex and 2047 in decimal. The window size is 2047 bytes.
11. Every second the counter is increment ed by 64,000 ´ 2 = 128,000. The sequence number field is 32 bits long and can hold only 232-1. So it takes (232-1)/(128,000) or 33,554 seconds to wrap around.
13. The window size is the smaller (3000, 5000) = 3000. Since 2000 bytes is already sent, only 3000 - 2000 = 1000 more bytes can be sent.
15. The data section is only 16 bytes. The TCP header is 20 bytes. IP header is 20 bytes. The header and trailer is 19 bytes (without preamble). We can calculate the efficiency at each layer:
a. At TCP level:
(16) / (16 + 20) = 0.444 ® 44.4%
b. At IP level:
(16) / (16 + 20 + 20) = 28.57 ® 28.57%
c. At data link level:
(16) / (16 + 20 + 20 + 19) = 0.2133 ® 21.33%
17. See Figure 15.E17.
Figure 15.E17 Solution to Exercise 17
19.
a. The server can receive a FIN segment while it is in the ESTABLISHED state. When the FIN segment is received, the server sends an ACK segment to the client and moves to the CLOSE-WAIT state.
b. When the “close” message is received from the application, the client TCP sends a FIN segment; the client goes to the FIN-WAIT-1 state and waits for an ACK.
21.
a. No ACK needed at 0:0:0:0:000, according to Rule 2
b. No ACK needed at 0:0:0:0:027, according to Rule 2
c. ACK: 4 can be sent at 0:0:0:0:500
d. ACK: 5 can be sent at 0:0:0:1:200
e. No ACK needed at 0:0:0:1:208, according to Rule 2
23. See Figure 15.E23.
Figure 15.E23 Solution to Exercise 23
25. See Figure 15.E25.
Figure 15.E25 Solution to Exercise 25
27. See Figure 15.E27.
Figure 15.E27 Solution to Exercise 27
29. See Figure 15.E29.
Figure 15.E29 Solution to Exercise 29
31. See Figure 15.E31.
Figure 15.E31 Solution to Exercise 31
Chapter16
Chapter 16
Stream Control Transmission Protocol (SCTP)
Exercises
1.
3.
5.
a. Fragments: 21, 24, 26, 27
b. First fragment: 21
c. No last fragment given
d. At least 3 middle fragments (22, 23, and 25) are missing
7. The host sends a SHUTDOWN ACK and goes to the SHUTDOWN-ACK-SENT state.
9.
a. ordered, because the U flag is not set
b. B = 0, E = 0 means this is a middle fragment
c. length is 21, so 3 bytes of padding are needed
d. TSN = 5
e. SI = 3
f. SSN = 10
g. message is 48656C6C67
11. See Figure 16.E11. Note that the value of cumTSN must be updated to 8.
Figure 16.E11 Solution to Exercise 11
13. See Figure 16.E13. Chunks 18 and 19 are sent but not acknowledged (200 bytes of data). 18 DATA chunks (1800 bytes) can be sent, but only 4 chunks are in the queue. Chunk 20 is the next chunk to be sent.
Figure 16.E13 Solution to Exercise 13
15. See Figure 16.E15. We have filled the fields with available information. Each packet has the general header and the appropriate control chunk. Note that only the SHUTDOWN chunk has the cumTSN ACK, which acknowledges the receipt of the last packet.
Figure 16.E15 Solution to Exercise 15
Chapter17
Chapter 17
Introduction to the Application Layer
Exercise
1. See Figure 17.E1. The rightmost (little) byte of a 32-bit integer is stored in the first memory location (x).
Figure 17.E1 Solution to Exercise 1
3. A union can be used to define two alternative data types or a combination of a data type and a data structure. We define a union as a combination of a 16-bit integer and an array of two characters. We stored an integer in the union, but use the un...
Table 17.E3 Solution to Exercise 3
5. Table 17.E5 shows a simple program. In lines 17 and18, we create two chunks of memory using the memset function and store the string "AAAAAAAAA" in the first and the string "BBBBBBBBBBBB" in the second. In line 21, we use the function memcpy to co...
Table 17.E5 Solution to Exercise 5
7. We can replace line 14 in Table 17.1 in the text with the following lines:
if (sd = socket (PF_INET, SOCK_DGRAM, 0) = -1)
{
perror("Call to socket function failed”);
exit (1);
}
9. Table 17.E9 shows the new program. The colored section (lines 21 to 28) shows the changes in the original program in the text.
Table 17.E9 Solution to Exercise 9
10. See Figure 17.E10.
Figure 17.E10 Solution to Exercise 10
Chapter18
Chapter 18
Host Configuration: DHCP
Exercises
1. The minimum length of a DHCP packet is 236 (without the option field). The maximum is 300 bytes (with the option field).
3. Figure 18.E3 shows an example of the padding option. The option section starts with the cookie (90.130.83.99) followed by the subnet mask option (included to show the use of the padding option. We also need the end of list option (tag 255).
Figure 18.E3 Solution to Exercise 3
5. The second field is 16 bits long. It can store up to 216 - 1 = 65,535 seconds.
7. A newly added host needs to know its subnet mask because this allows the host to find out which subnet it is on.
9. A newly added host needs to know the address of a name server in order to resolve a domain name to an IP address.
11. See Figure 18.E11. We assume that the server is 4 hops away. We also use transaction ID of 1456. The messages between the client and the relay agent are broadcast. The messages between the relay agent and the server are unicast.
Figure 18.E11 Solution to Exercise 11
Chapter19
Chapter 19
Domain Name System (DNS)
Exercises
1.
a. PQDN (It does not end with dot.)
b. FQDN (It does end with dot.)
c. PQDN (It does not end with dot.)
d. FQDN (It does end with dot.)
3. The following shows the individual fields. The flag is then (00000001 0000000)2 or (0100)16.
QR
OpCode
AA
TC
RD
RA
Three 0’s
rCode
0
0000
0
0
1
0
000
0000
5. The flag 0x8F80 means (1 0001 1 1 1 1 000 0000)2. This means This is a response message from an authoritative server. The request was an inverse request with recursion desired and recursion was available. The message is truncated.
QR
OpCode
AA
TC
RD
RA
Three 0’s
rCode
1
0001
1
1
1
1
000
0000
7. The size of a question record is not fixed because query name field is variable in length.
9. Query name = 3 a t c 4 f h d a 3 e d u 0 = 14 bytes Query type = 2 bytes Query class = 2 bytes Question Record = 14 + 2 + 2 = 18 bytes
11. Assuming that the domain name field is a pointer, the record is 22 bytes in length.
13. Query name = 10 c h a l l e n g e r 3 a t c 4 f h d a 3 e d u 0 = 25 bytes
15. The size of the response message depends on the number of digits in the requested IP address.
17. See Figure 19.E17.
Figure 19.E17 Solution to Exercise 17
19. See Figure 19.E19.
Figure 19.E19 Solution to Exercise 19
21. See Figure 19.E21.
Figure 19.E21 Solution to Exercise 21
23. See Figure 19.E23.
Figure 19.E23 Solution to Exercise 23
25. See Figure 19.E25.
Figure 19.E25 Solution to Exercise 25
27. See Figure 19.E27.
Figure 19.E27 Solution to Exercise 27
Chapter20
Chapter 20
Remote Login: TELNET and SSH
Exercises
1. The pattern is:
11110011 00111100 11111111 11111111
3. To do the task in Exercise 1, we need to send: If each transmission is encapsulated in a single TCP segment with 20 bytes of header, there will be 3 segments of 23, 23, and 24 bytes for the total of 70 bytes or 560 bits.
Client to Server: IAC DO BINARY (3 bytes)
Server to Client: IAC WILL BINARY (3 bytes)
Client to Server: 11110011 00111100 11111111 11111111 (4 bytes)
5. If we assume the useful bits are the 3 bytes of data from Exercise 1:
(3 bytes of data) / (216 transmitted bytes) » 1:70 » 1.42 percent
7. See Figure 20.E7.
Figure 20.E7 Solution to Exercise 7
9. See Figure 20.E9.
Figure 20.E9 Solution to Exercise 9
11. See Figure 20.E11.
Figure 20.E11 Solution to Exercise 11
13. One of the common client/server remote login program is called putty.The client putty program can be freely downloaded and installed on your local computer. If the remote server that you have account on is using the putty server program, you can ...
Chapter21
Chapter 21
File Transfer: FTP and TFTP
Exercises
1. If the control connection is accidentally severed during an FTP transfer, there would be no problem until the data transfer completed and the client attempted to send another command.
3. There should be limitations on anonymous FTP because it is unwise to grant the public complete access to a system. If the commands that an anonymous user could use were not limited, that user could do great damage to the file system (e.g., erase i...
5. See Figure 21.E5. Note that the well-known port number is 21.
Figure 21.E5 Solution to Exercise 5
7. See Figure 21.E6. Note that the well-known port number is 20.
Figure 21.E6 Solution to Exercise 7
9. See Figure 21.E9.
Figure 21.E9 Solution to Exercise 9
11. See Figure 21.E11.
Figure 21.E11 Solution to Exercise 11
13. See Figure 21.E13.
Figure 21.E13 Solution to Exercise 13
15. See Figure 21.E15.
Figure 21.E15 Solution to Exercise 15
17. See Figure 21.E17.
Figure 21.E17 Solution to Exercise 17
19. TFTP needs to use RRQ and WRQ messages for connection establishment and to let the server know what kind of service is required. These functions are served by various commands in FTP using the FTP control connection.
21. See Figure 21.E21. The user datagram is 26 bytes.
Figure 21.E21 Solution to Exercise 21
23. See Figure 21.E23.
Figure 21.E23 Solution to Exercise 23
Chapter22
Chapter 22
World Wide Web and HTTP
1.
a. GET /usr/users/doc/doc.1 HTTP /1.1 Date: Fri, 26-Nov-04 16:46:23 GMT MIME-version: 1.0 Accept: image/gif Accept: image/jpeg Last modified: Mon, 22-Nov-04
b. HTTP/1.1 200 OK Date: Fri, 26-Nov-04 16:46:26 GMT Server: Challenger MIME-version: 1.0 Content-length: 4623 (Body of document)
c. HTTP/1.1 302 Moved permanently Date: Fri, 26-Nov-04 16:46:26 GMT Server: Challenger Location: /usr/deads/doc.1
d. HTTP/1.1 400 Bad Request Date: Fri, 26-Nov-04 16:46:26 GMT Server: Challenger
e. HTTP/1.1 401 Unauthorized Date: Fri, 26-Nov-04 16:46:26 GMT Server: Challenger
3.
a. COPY /bin/usr/bin/file1 HTTP /1.1 Date: Fri, 26-Nov-04 17:07:15 GMT MIME-version: 1.0 Location: /bin/file1
b. HTTP/1.1 200 OK Date: Fri, 26-Nov-04 17:07:22 GMT Server: Challenger
5.
a. GET /bin/etc/file1 HTTP /1.1 Date: Fri, 26-Nov-04 17:29:42 GMT MIME-version: 1.0 Accept: */* If-modified-since: 23-Jan-99 00:00:00 GMT
b. HTTP/1.1 200 OK Date: Fri, 26-Nov-04 17:29:49 GMT Server: Challenger MIME-version: 1.0 Content-length: 2686 (Body of document)
7. Normally eight segments are exchanged for this transaction as shown in Figure 22.E7.
Figure 22.E7 Solution to Exercise 7
9. Figure 22.E9 shows a simple situation. A portal, such as Yahoo, is a special site that holds the often-visited URLs for each client. The cookie stored in the browser under the name of the portal, holds the list of the sites the user normally needs...
Figure 22.E9 Solution to Exercise 9
11. Figure 22.E11 shows a simple example. We assume the computer has installed both the client HTTP and the proxy server HTTP. In part a, the request can be responded by the proxy server. In part b, the proxy needs to send the request to the true ser...
Figure 22.E11 Solution to Exercise 11
13. Figure 22.E13 shows a simple example. We assume that the client is connected via a point-to-point WAN to an ISP network. The proxy server is installed in the proxy server. In part a, the request can be responded by the proxy server. In part b, th...
Figure 22.E13 Solution to Exercise 13
Chapter23
Chapter 23
Electronic Mail: SMTP, POP, IMAP, and MIME
Exercises
1. MIME-version: 1.1
3.
a. 1000 ´ (8 /24) = 333.3 ® 334 blocks of 24 bits. Each block becomes 32 bits.
b. There are 334 ´ (32 / 8) = 1336 bytes in the encoded message.
c. There are 336 redundant bytes.
d. The ratio of redundant bytes to the entire message length is 336 /1336.
5.
a. The efficiency in Exercise 3 is (1,000)/(1,336) = 75%.
b. The efficiency in Exercise 4 is (1,000/1,200) = 83%.
c. The efficiency is improved 8%.
7.
a. Original:
0101011 1
0000111 1
1111000 0
1010111 1
0111000 1
0101010 0
b. Encoded:
0101011 1
0000111 1
=F0
=AF
0111000 1
0101010 0
c. Bit Pattern:
01010111
00001111
00111101
01000110
00110000
00111101
01000001
01000110
01110001
01010100
9.
a. Original:
01010111
00001111
11110000
10101111
01110001
b. Encoded:
01010111
00001111
=F0
=AF
01110001
c. Bit Pattern:
01010111
00001111
00111101
01000110
00110000
00111101
01000001
01000110
01110001
11.
a. The MAIL FROM: in the envelope contains the source e-mail address while the
b. FROM in the header contains the name of the sender.
13. See Figure 23.E13.
Figure 23.E13 Solution to Exercise 13
15. See Figure 23.E15.
Figure 23.E15 Solution to Exercise 15
17. Figure 23.E17 shows both the original and the replay messages.
Figure 23.E17 Solution to Exercise 17
Chapter24
Chapter 24
Network Management: SNMP
Exercises
1. The integer1456 is (00 00 05 B0)16 in hexadecimal. Therefore, we have: The answer is then: 02 04 00 00 05 B0.
3. The following shows the three fields (without the value). Note that the length of the length field is 10000010, which is (82)16.
5.
7.
Chapter25
Chapter 25
Multimedia
Exercises
1.
a. At time 00:00:17
b. At time 00:00:20
c. At time 00:00:25
d. At time 00:00:30
3. RTP plus UDP provides about the same services as TCP without the latter’s retransmission policy.
5. The answer is yes. The protocol defines a server as a process running at the application level. The two servers can be on the same machine or different machines.
7. SIP just sets up and terminates a session between 2 parties. H.323 is a protocol suite that covers everything pertaining to the session. SIP is more flexible in its address formats. H.323 setup is more complicated than that of SIP.
9.
a. The input during the first minute is (100 gallons/minutes) ´ (12 / 60 minutes) or 20 gallons.
b. The output during the first minutes is (5 gallons/minutes) ´ (1 minute) or 5 gallons.
c. This means that after the first minute, 15 gallons of liquid is left in the bucket. The problem does not mention the input rate after the first minute. If there is no input flow, the bucket would be empty after three minutes.
Chapter26
Chapter 26
IPv6 Addressing
Exercises
1.
a. 0000:0000:0000:0000:5555:5555:5555:5555
b. 0000:0000:0000:0000:AAAA:AAAA:AAAA:AAAA
c. 5555:5555:5555:5555:5555:5555:5555:5555
d. 7777:7777:7777:7777:7777:7777:7777:7777
3.
a. 0:FFFF:FFFF::
b. 1234:2346:3456::FFFF
c. 0:1::3456::FFFF :1200:1000
d. ::FFFF::FFFF :24.123.12.6
5.
a. 0000:0000:0000:0000:0000:0000:0000:0002
b. 0000:0023:0000:0000:0000:0000:0000:0000
c. 0000:000A:0002:0000:0000:0000:0000:0003
d. 0123:0000:0000:0000:0000:0000:0012:0023
7. As discussed in the solution to Exercise 6, the best way is to apply different masks (starting from the longest one) to each address to find a match with the beginning address in a block. The prefix lengths are 10, 9, 8, 7, 6, 5, 4, and 3 as shown...
a. In this case, all bits are 0’s, the address is an unspecified address in this block.
b. In this case, since the last 32 bits are all 0’s and the previous 16 bits are all 1’s, the address is a mapped address for an IP address 0.0.0.0
c.
d.
9. We change the seventh bits from 0 to 1 and insert four extra hexadecimal digits (FF-FE) after the sixth digits: The resulting preface address in IPv6 is F7A9:23FF:FE12:7AB2.
11. We assume the subnet identifiers start from (0001)16, but they can also start from (0000)16.
a. The block for the third subnet is 2000:1110:1287:0003/64.
b. We change the IEEE address to EUI address: F7A9:23FF:FE14:7AD2.
c. We add the interface to the block prefix to get the IPv6 address of the station as 2000:1110:1287:0003:F7A9:23FF:FE14:7AD2.
13. The address is ::1111:129.6.12.34/128.
15. The information given cannot belong to a link local address because the address starts with 0’s instead of 1’s.
Chapter27
Chapter 27
IPv6 Protocol
Exercises
1. See Figure 27.E1.
Figure 27.E1 Solution to Exercise 1
Chapter28
Chapter 28
ICMPv6
Exercises
1. Error-reporting messages contain part of the IP datagram for which the error message has be created. This is needed to let the sender of the datagram to identifier which datagram has been discarded due to the error. See Chapter 9 for more information
3. Two informational messages in ICMPv4 is kept in ICMPv6, but the other two have been deleted. Table 28.E3 shows a comparison.
Table 28.E3 Solution to Exercise 3
Message
v4
v6
Explanation
Echo Request/Response
Ö
Ö
Timestamp request/response
Ö
Deleted from ICMPv6; rarely used
5. These message are new in Version 6. Version 4 was using RARP protocol, but it is now deprecated.Table 28.E5 shows a comparison.
Table 28.E5 Solution to Exercise 5
Message
v4
v6
Explanation
Inverse neighbor solicitation
Ö
Version 4 used RARP request message
Inverse neighbor advertisement
Ö
Version 4 used RARP reply message
7.
a. Since Max Response Code (MRC) is less than 32768, we simply find the value of Maximum Response Delay (MRD) as Note that we don’t have to worry about the most significant bit because it is 0 and has no effect in calculation. Calculation can be do...
MRD = (1/10) MRC = (1/10) ´ 22,000 = 2200 seconds
b. Since MRC ³ 32768, we need to find the exponent and the mantissa. This means that we need to shift (10000)16 five bits, (Exp + 3), to the left and OR it with the mantissa.
MRD = (43,000)10 = (AF78)16 = (1010 1111 0111 1000)2
Ex = (010)2 = 2 Mantissa = (1111 0111 1000)2 = (F78)16
Shifting: (10000)16 << 5 = (20000)16
Bit-Wise ORing: (F78)16 | (200000)16 = (200F78)16 = 2,101,112
MRD = (1/10) ´ 2,101,112 » 210,111 seconds
Chapter29
Chapter 29
Cryptography and Network Security
Exercises
1.
a. This is snooping (the attack to confidentiality service). Although the contents of the test is not confidential on the day of the test, it is confidential before the test day.
b. This is modification (the attack to integrity service). The value of the check is changed (from $10 to $100).
c. This is denial of service (the attack to availability service). Sending so many e- mails may crash the server and the service may be interrupted.
3. Double encryption here does not help. Encryption with k1 followed by encryption with k2 is the same as encryption with k = (k1 + k2) mod 26. The following shows the proof. P is the plaintext and C is the ciphertext.
5.
a. A 3-bit circular left shift of (10011011) is (11011100)
b. A 3-bit circular right shift of (11011100) is (10011011)
c. The original word in Part a and the result of Part b are the same, which shows that circular left shift and circular right shift operations are inverses of each other.
7.
a. (01001101) Å (01001101) = (00000000), which means that if the two input words are the same, all the bits in the output word becomes 0’s. This property is used in ciphers.
b. (01001101) Å (10110010) = (11111111), which means that if the two input words are complement of each other, all the bits in the output word becomes 1’s. This property is also used in ciphers.
9.
a. Using 26 for space, the plaintext is: 19070818260818261914200607
b. For encryption, we create 4-digit blocks:
c. We can use the private key, d = 3653 to decrypt the message. The plaintext is:19070818260818261914200607 or “THIS IS TOUGH”.
11. The key which is concatenated with the message in a MAC should be a secret between Alice and Bob; no one else should know this secret. When Alice sends a MAC to Bob, the key cannot be the public key of Bob or the private key of Alice. If the key ...
12. Figure 29.E13 shows one simple, but not very secure solution. It shows the idea, but it is vulnerable to some attacks. There are some better, but more complicated solutions.
a. In the first message, Alice sends her identification and her nonce.
b. In the second message, Bob sends his identification, his nonce, and encrypted Alice’s nonce. Alice’s nonce is encrypted with the shared secret key. When Alice receives this message and decrypts her nonce, Bob is authenticated for her because o...
c. In the third message, Alice sends encrypted Bob’s nonce. When Bob receives this message and decrypts his nonce, Alice is authenticated for Bob because only Alice can encrypt Bob’s nonce with the shared secret key.
Figure 29.E13 Solution to Exercise 13
d.
15. Figure 29.E15 shows one simple, but not very secure solution. It shows the idea, but it is vulnerable to some attacks. There are some better, but more complicated solutions.
Figure 29.E15 Solution to Exercise 15
a. In the first message, Alice sends her identification and her nonce.
b. In the second message, Bob sends his identification, his nonce, and signed Alice’s. Bob uses his private key to sign the message carrying Alice’s nonce. When Alice receives this message and verifies the signature, Bob is authenticated for her ...
c. In the third message, Alice sends Bob a signed message that include the Bob’s nonce. Alice signs this message with her private key. When Bob receives this message, Alice is authenticated for Bob because only Alice can sign a message with her pri...
Chapter30
Chapter 30
Internet Security
Exercises
1. When IPSec is used in the transport mode, two parties need to first create cryptographic secrets between themselves before exchanging secure data. This cannot be done using the connectionless service provided by IP. The two parties need to create ...
3. SSL provides both entity and message authentications. Two entities are authenticated for each other using the handshake protocol. The record protocol provides message authentication when it encapsulates messages from the application layer.
5. Both parties that use PGP or S/MIME need to agree about the list of predefined cryptography algorithms. The sender of the e-mail defines the algorithms used for each purpose (confidentiality, integrity, authentication, and so on); the receiver nee...
7. SA provides two services for IPSec: it creates a virtual connection and establishes security parameters between the two parties. The first service is not needed in the case of SSL because SSL runs over TCP, which is a connection-oriented protocol....
9. Although it is possible to create an SA permanently, but it is strongly discouraged because of the leak of security parameters. With the pass of time, Eve may find the secrets between Alice and Bob and misuse them.














 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc