�
© 2013 by William Stallings
All rights reserved. No part
of this document may be
reproduced, in any form or
by any means, or posted on
the Internet, without
permission in writing from
the author. Selected
solutions may be shared
with students, provided
that they are not available,
unsecured, on the Web.
NOTICE
-2-
This manual contains solutions to the review
questions and homework problems in
Cryptography and Network Security, Sixth Edition.
If you spot an error in a solution or in the
wording of a problem, I would greatly appreciate
it if you would forward the information via email
to wllmst@me.net. An errata sheet for this
manual, if needed, is available at
http://www.box.net/shared/nh8hti5167 . File
name is S-NetSec5e-mmyy
W.S.
TABLE OF CONTENTS
Chapter 1 Introduction ........................................................................4
Chapter 2 Symmetric Encryption and Message Confidentiality ..................7
Chapter 3 Public-Key Cryptography and Message Authentication ............ 19
Chapter 4 Key Distribution and User Authentication ..............................26
Chapter 5 Network Access Control and Cloud Security .......................... 34
Chapter 6 Transport-Level Security .....................................................37
Chapter 7 Wireless Network Security .................................................. 40
Chapter 8 Electronic Mail Security ...................................................... 43
Chapter 9 IP Security ........................................................................48
Chapter 10 Malicious Software ........................................................... 55
Chapter 11 Intruders ........................................................................ 62
Chapter 12 Firewalls ......................................................................... 69
Chapter 13 Network Management Security .......................................... 76
Chapter 14 Legal and Ethical Aspects ..................................................79
Chapter 15 SHA-3 ............................................................................ 87
-3-
�
CHAPTER 1 INTRODUCTION
ANSWERS TO QUESTIONS
1.1 The OSI Security Architecture is a framework that provides a systematic
way of defining the requirements for security and characterizing the
approaches to satisfying those requirements. The document defines
security attacks, mechanisms, and services, and the relationships among
these categories.
1.2 Passive attacks have to do with eavesdropping on, or monitoring,
transmissions. Electronic mail, file transfers, and client/server exchanges
are examples of transmissions that can be monitored. Active attacks
include the modification of transmitted data and attempts to gain
unauthorized access to computer systems.
1.3 Passive attacks: release of message contents and traffic analysis.
Active attacks: masquerade, replay, modification of messages, and
denial of service.
1.4 Authentication: The assurance that the communicating entity is the one
that it claims to be.
Access control: The prevention of unauthorized use of a resource (i.e.,
this service controls who can have access to a resource, under what
conditions access can occur, and what those accessing the resource are
allowed to do).
Data confidentiality: The protection of data from unauthorized
disclosure.
Data integrity: The assurance that data received are exactly as sent by
an authorized entity (i.e., contain no modification, insertion, deletion, or
replay).
Nonrepudiation: Provides protection against denial by one of the
entities involved in a communication of having participated in all or part
of the communication.
Availability service: The property of a system or a system resource
being accessible and usable upon demand by an authorized system
entity, according to performance specifications for the system (i.e., a
-4-
�
system is available if it provides services according to the system design
whenever users request them).
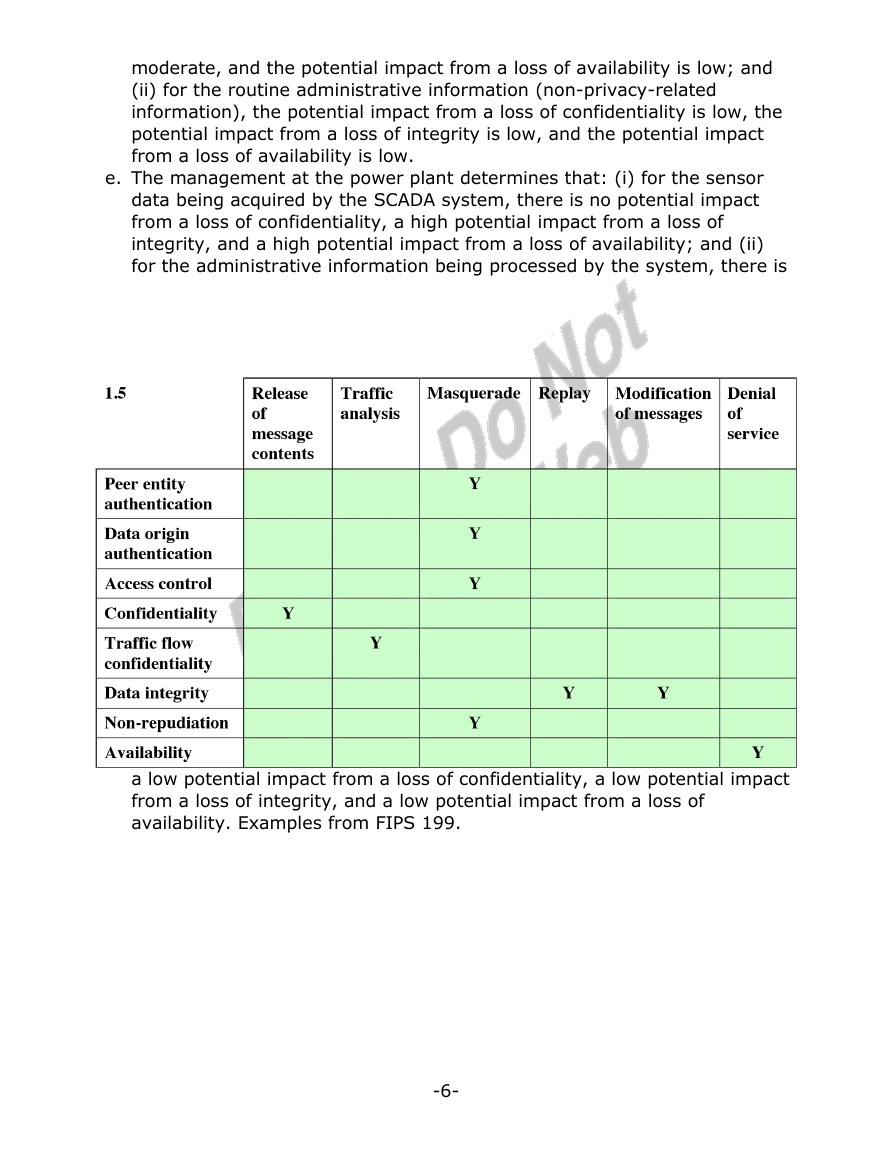
1.5 See Table 1.3.
ANSWERS TO PROBLEMS
1.1 The system must keep personal identification numbers confidential, both
in the host system and during transmission for a transaction. It must
protect the integrity of account records and of individual transactions.
Availability of the host system is important to the economic well being of
the bank, but not to its fiduciary responsibility. The availability of
individual teller machines is of less concern.
1.2 The system does not have high requirements for integrity on individual
transactions, as lasting damage will not be incurred by occasionally
losing a call or billing record. The integrity of control programs and
configuration records, however, is critical. Without these, the switching
function would be defeated and the most important attribute of all -
availability - would be compromised. A telephone switching system must
also preserve the confidentiality of individual calls, preventing one caller
from overhearing another.
1.3 a. The system will have to assure confidentiality if it is being used to
publish corporate proprietary material.
b. The system will have to assure integrity if it is being used to laws or
c. The system will have to assure availability if it is being used to publish a
regulations.
daily paper.
1.4 a. An organization managing public information on its web server
determines that there is no potential impact from a loss of
confidentiality (i.e., confidentiality requirements are not applicable), a
moderate potential impact from a loss of integrity, and a moderate
potential impact from a loss of availability.
b. A law enforcement organization managing extremely sensitive
investigative information determines that the potential impact from a loss
of confidentiality is high, the potential impact from a loss of integrity is
moderate, and the potential impact from a loss of availability is moderate.
c. A financial organization managing routine administrative information (not
privacy-related information) determines that the potential impact from a
loss of confidentiality is low, the potential impact from a loss of integrity is
low, and the potential impact from a loss of availability is low.
d. The management within the contracting organization determines that: (i)
for the sensitive contract information, the potential impact from a loss of
confidentiality is moderate, the potential impact from a loss of integrity is
-5-
�
moderate, and the potential impact from a loss of availability is low; and
(ii) for the routine administrative information (non-privacy-related
information), the potential impact from a loss of confidentiality is low, the
potential impact from a loss of integrity is low, and the potential impact
from a loss of availability is low.
e. The management at the power plant determines that: (i) for the sensor
data being acquired by the SCADA system, there is no potential impact
from a loss of confidentiality, a high potential impact from a loss of
integrity, and a high potential impact from a loss of availability; and (ii)
for the administrative information being processed by the system, there is
a low potential impact from a loss of confidentiality, a low potential impact
from a loss of integrity, and a low potential impact from a loss of
availability. Examples from FIPS 199.
-6-
�
CHAPTER 2 SYMMETRIC ENCRYPTION AND
MESSAGE CONFIDENTIALITY
ANSWERS TO QUESTIONS
-7-
�
2.1 Plaintext, encryption algorithm, secret key, ciphertext, decryption
algorithm.
2.2 Permutation and substitution.
2.3 One secret key.
2.4 A stream cipher is one that encrypts a digital data stream one bit or
one byte at a time. A block cipher is one in which a block of plaintext is
treated as a whole and used to produce a ciphertext block of equal
length.
2.5 Cryptanalysis and brute force.
2.6 In some modes, the plaintext does not pass through the encryption
function, but is XORed with the output of the encryption function. The
math works out that for decryption in these cases, the encryption
function must also be used.
2.7 With triple encryption, a plaintext block is encrypted by passing it
through an encryption algorithm; the result is then passed through the
same encryption algorithm again; the result of the second encryption is
passed through the same encryption algorithm a third time. Typically,
the second stage uses the decryption algorithm rather than the
encryption algorithm.
2.8 There is no cryptographic significance to the use of decryption for the
second stage. Its only advantage is that it allows users of 3DES to
decrypt data encrypted by users of the older single DES by repeating the
key.
-8-
�













 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc