Eric Mitchell Channel SE, East US and Federal F5 NetworksCERTIFIEDF5 STUDY GUIDE101 – Application Delivery Fundamentals�
F5 STUDY GUIDE
101 – Application Delivery Fundamentals
Contents
Overview
Printed References
Section 1 - OSI
Objective - 1.01 Explain, compare, and contrast the OSI layers
Objective - 1.02 Explain Protocols and Technologies Specific to the Data Link Layer
Objective - 1.03 Explain protocols and apply technologies specific to the network layer
Objective - 1.04 Explain the features and functionality of protocols and technologies specific
to the transport layer
Objective - 1.05 Explain the features and functionality of protocols and technologies specific
to the application layer
Section 2 - F5 Solutions and Technology
Objective - 2.01 Articulate the role of F5 products
Objective - 2.02 Explain the purpose, use, and advantages of iRules
Objective - 2.03 Explain the purpose, use, and advantages of iApps
Objective - 2.04 Explain the purpose of and use cases for full proxy and packet
forwarding/packet based architectures
Objective - 2.05 Explain the advantages and configurations of high availability (HA)
Section 3 – Load Balancing Essentials
Objective - 3.01 Discuss the purpose of, use cases for, and key considerations related to
load balancing
Objective - 3.02 Differentiate between a client and server
Section 4 – Security
Objective - 4.01 Compare and contrast positive and negative security models
Objective - 4.02 Explain the purpose of cryptographic services
Objective - 4.03 Describe the purpose and advantages of authentication
Objective - 4.04 Describe the purpose, advantages, and use cases of IPsec and SSL VPN
4
4
5
5
9
16
31
42
61
61
65
68
71
82
86
86
93
95
95
102
106
110
2
�
F5 STUDY GUIDE
101 – Application Delivery Fundamentals
Section 5 – Application Delivery Platforms
Objective - 5.01 Describe the purpose, advantages, use cases, and challenges associated with
hardware based application delivery platforms and virtual machines
115
115
Objective - 5.02 Describe the purpose of the various types of advanced acceleration techniques
121
Conclusion
129
THIS STUDY GUIDE IS PROVIDED “AS IS” WITH NO EXPRESS OR IMPLIED WARRANTIES OR CONDITIONS OF ANY
KIND, INCLUDING, WITHOUT LIMITATION, WARRANTIES OF ACCURACY, COMPLETENESS OR NON-INFRINGEMENT.
IN NO EVENT SHALL F5 BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL, SPECIAL, OR CONSEQUENTIAL
DAMAGES, INCLUDING, ARISING OUT OF OR IN CONNECTION WITH THE STUDY GUIDES, REGARDLESS OF THE
NATURE OF THE ACTION OR UNDERLYING LEGAL THEORY.
3
�
Overview
Welcome to the F5 Networks 101 - Application Delivery Fundamentals compiled Study Guide. The purpose
of this guide is to help you prepare for the F5 101 - Application Delivery Fundamentals exam. The contents of
this document are based on the 101 - Application Delivery Fundamentals Blueprint Guide.
This study guide provides students with some of the basic foundational knowledge required to pass
the exam.
This study guide is a collection of information and therefore not a completely original work. The majority of
the information is compiled from sources that are located on the Internet. All of the information locations are
referenced at the top of each topic instead of in an Appendix of this document. This was done to help the
reader access the referenced information easier without having to search through a formal appendix. This
guide also references a book that should be basic reading for some of the topics on this exam.
The F5 Certified team provides an official 101 - Application Delivery Fundamentals Study Guide to all
candidates. The F5 Certified Study Guide is a list of reading material that will help any student build a broad
base of general knowledge that can assist in not only their exam success but also in becoming a well-rounded
systems engineer. The Resource Guide will be available to the candidate through the certification.f5.com
website once they are qualified for the Application Delivery Fundamentals exam.
There are not any pre-requisite to this exam.
This guide was prepared by an F5 employee but is not an official F5 document and is not supported by F5
Networks.
Reading = Knowledge = Power
Printed References
These referenced books are important and should be considered basic reading material for this exam.
(Ref:1) Kozierok, Charles M. 2005. The TCP/IP Guide. No Starch Press, Inc. San Francisco, CA. 94103. ISBN
1-59327-047-X pp 947 -1080
4
4
F5 STUDY GUIDE 101 – Application Delivery Fundamentals�
SECTION 1 - OSI
Objective - 1.01 Explain, compare, and contrast the
OSI layers
1.01 – Describe the function of each OSI layer
Ref: 1, pp. 168-181.
Networking Basics: Part 17 - The OSI Model
The OSI Model’s Seven Layers Defined and Functions Explained
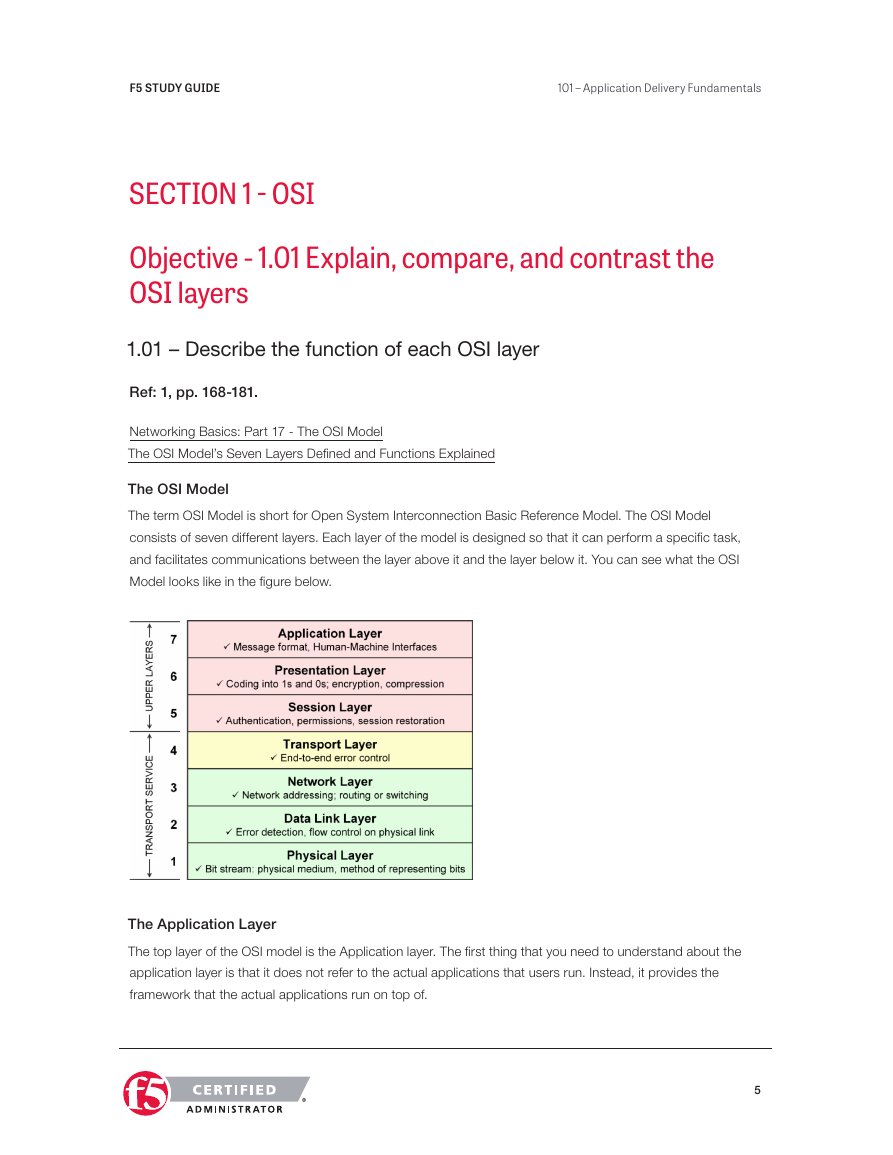
The OSI Model
The term OSI Model is short for Open System Interconnection Basic Reference Model. The OSI Model
consists of seven different layers. Each layer of the model is designed so that it can perform a specific task,
and facilitates communications between the layer above it and the layer below it. You can see what the OSI
Model looks like in the figure below.
The Application Layer
The top layer of the OSI model is the Application layer. The first thing that you need to understand about the
application layer is that it does not refer to the actual applications that users run. Instead, it provides the
framework that the actual applications run on top of.
5
F5 STUDY GUIDE 101 – Application Delivery Fundamentals�
To understand what the application layer does, suppose that a user wanted to use Internet Explorer to open
an FTP session and transfer a file. In this particular case, the application layer would define the file transfer
protocol. This protocol is not directly accessible to the end user. The end user must still use an application
that is designed to interact with the file transfer protocol. In this case, Internet Explorer would be that
application.
The Presentation Layer
The presentation layer does some rather complex things, but everything that the presentation layer does can
be summed up in one sentence. The presentation layer takes the data that is provided by the application layer,
and converts it into a standard format that the other layers can understand. Likewise, this layer converts the
inbound data that is received from the session layer into something that the application layer can understand.
The reason why this layer is necessary is because applications handle data differently from one another. In
order for network communications to function properly, the data needs to be structured in a standard way.
The Session Layer
Once the data has been put into the correct format, the sending host must establish a session with the
receiving host. This is where the session layer comes into play. It is responsible for establishing, maintaining,
and eventually terminating the session with the remote host.
The interesting thing about the session layer is that it is more closely related to the application layer than it is
to the physical layer. It is easy to think of connecting a network session as being a hardware function, but
sessions are established between applications. If a user is running multiple applications, several of those
applications may have established sessions with remote resources at any time.
The Transport Layer
The Transport layer is responsible for maintaining flow control. An operating system allows users to run
multiple applications simultaneously and it is therefore possible that multiple applications may need to
communicate over the network simultaneously. The Transport Layer takes the data from each application,
and integrates it all into a single stream. This layer is also responsible for providing error checking and
performing data recovery when necessary. In essence, the Transport Layer is responsible for ensuring that
all of the data makes it from the sending host to the receiving host.
The Network Layer
The Network Layer is responsible for determining how the data will reach the recipient. This layer handles
things like addressing, routing, and logical protocols. Since this series is geared toward beginners, I do not
want to get too technical, but I will tell you that the Network Layer creates logical paths, known as virtual
circuits, between the source and destination hosts. This circuit provides the individual packets with a way to
6
F5 STUDY GUIDE 101 – Application Delivery Fundamentals�
reach their destination. The Network Layer is also responsible for its own error handling, and for packet
sequencing and congestion control.
Packet sequencing is necessary because each protocol limits the maximum size of a packet. The amount of
data that must be transmitted often exceeds the maximum packet size. Therefore, the data is fragmented into
multiple packets. When this happens, the Network Layer assigns each packet a sequence number. When
the data is received by the remote host, that device’s Network layer examines the sequence numbers of the
inbound packets, and uses the sequence number to reassemble the data and to figure out if any packets
are missing. If you are having trouble understanding this concept, then imagine that you need to mail a large
document to a friend, but do not have a big enough envelope. You could put a few pages into several small
envelopes, and then label the envelopes so that your friend knows what order the pages go in. This is exactly
the same thing that the Network Layer does.
The Data Link Layer
The data link layer can be sub divided into two other layers; the Media Access Control (MAC) layer, and the
Logical Link Control (LLC) layer. The MAC layer basically establishes the computer’s identity on the network,
via its MAC address. A MAC address is the address that is assigned to a network adapter at the hardware
level. This is the address that is ultimately used when sending and receiving packets. The LLC layer controls
frame synchronization and provides a degree of error checking.
The Physical Layer
The physical layer of the OSI model refers to the actual hardware specifications. The Physical Layer defines
characteristics such as timing and voltage. The physical layer defines the hardware specifications used by
network adapters and by the network cables (assuming that the connection is not wireless). To put it simply,
the physical layer defines what it means to transmit and to receive data.
1.01 - Differentiate between the OSI layers
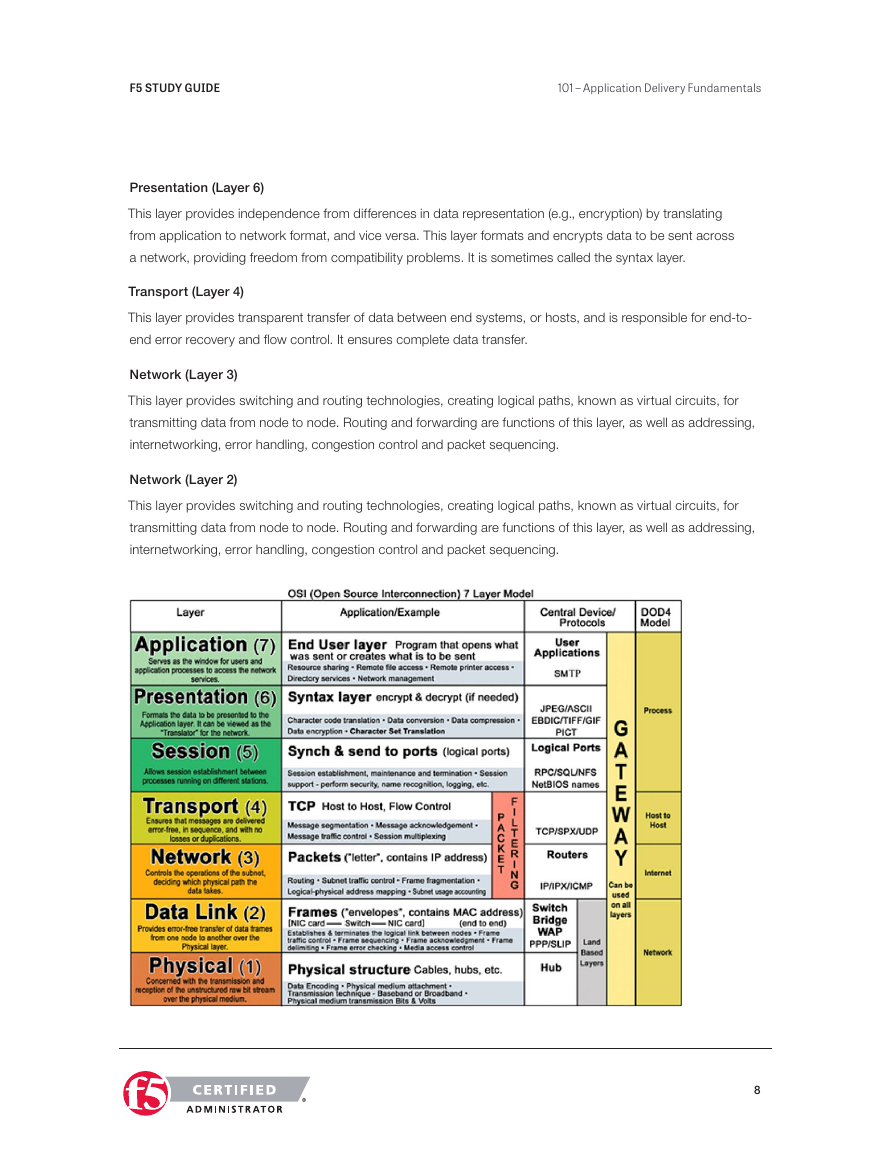
OSI (Open Source Interconnection) 7 Layer Model
OSI Layers
Application (Layer 7)
This layer supports application and end-user processes. Communication partners are identified, quality of
service is identified, user authentication and privacy are considered, and any constraints on data syntax
are identified. Everything at this layer is application-specific. This layer provides application services for file
transfers, e-mail, and other network software services.
7
F5 STUDY GUIDE 101 – Application Delivery Fundamentals�
Presentation (Layer 6)
This layer provides independence from differences in data representation (e.g., encryption) by translating
from application to network format, and vice versa. This layer formats and encrypts data to be sent across
a network, providing freedom from compatibility problems. It is sometimes called the syntax layer.
Transport (Layer 4)
This layer provides transparent transfer of data between end systems, or hosts, and is responsible for end-to-
end error recovery and flow control. It ensures complete data transfer.
Network (Layer 3)
This layer provides switching and routing technologies, creating logical paths, known as virtual circuits, for
transmitting data from node to node. Routing and forwarding are functions of this layer, as well as addressing,
internetworking, error handling, congestion control and packet sequencing.
Network (Layer 2)
This layer provides switching and routing technologies, creating logical paths, known as virtual circuits, for
transmitting data from node to node. Routing and forwarding are functions of this layer, as well as addressing,
internetworking, error handling, congestion control and packet sequencing.
8
F5 STUDY GUIDE 101 – Application Delivery Fundamentals�











 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc