云安全控制矩阵 CCM 中英文版
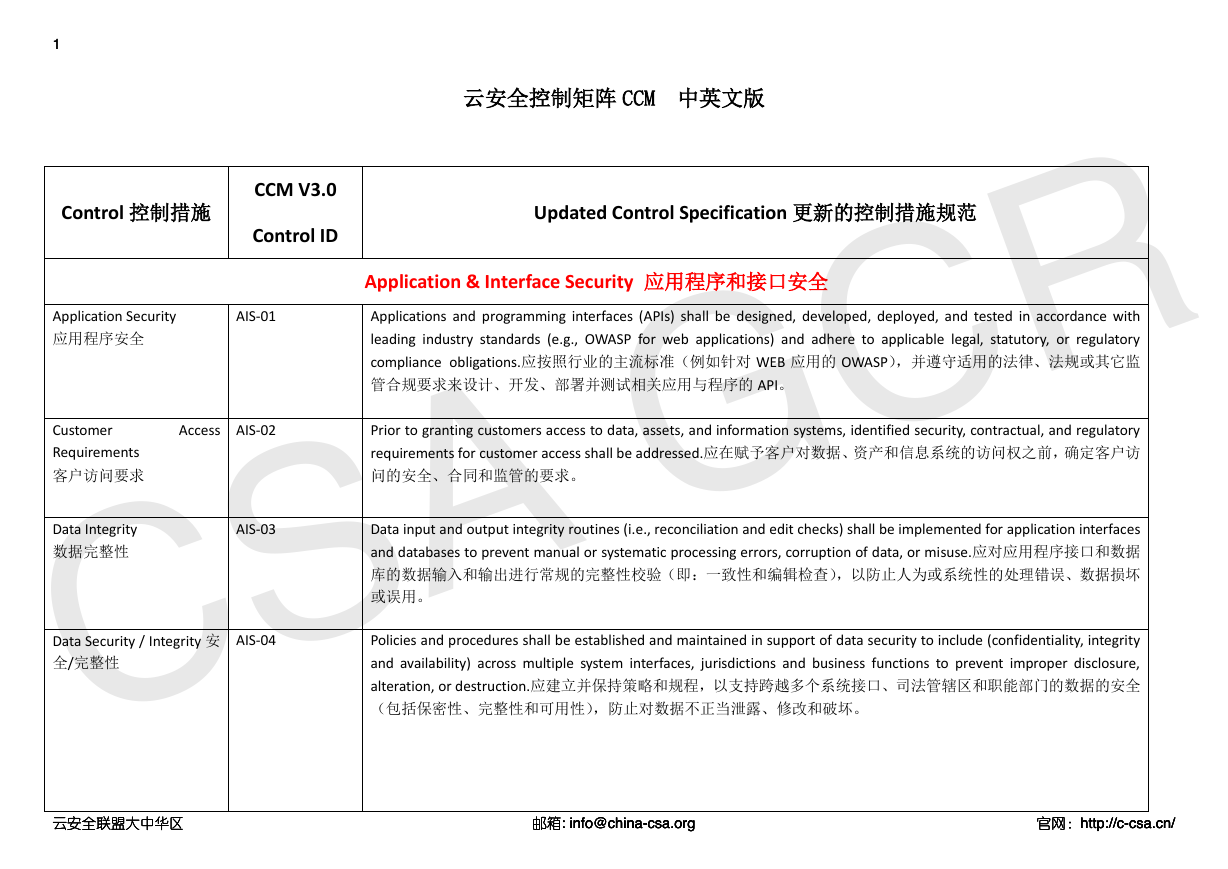
Control 控制措施
CCM V3.0
Control ID
Updated Control Specification 更新的控制措施规范
Application & Interface Security 应用程序和接口安全
Application Security
应用程序安全
AIS-01
Applications and programming interfaces (APIs) shall be designed, developed, deployed, and tested in accordance with
leading industry standards (e.g., OWASP for web applications) and adhere to applicable legal, statutory, or regulatory
compliance obligations.应按照行业的主流标准(例如针对 WEB 应用的 OWASP),并遵守适用的法律、法规或其它监
管合规要求来设计、开发、部署并测试相关应用与程序的 API。
Access
AIS-02
Customer
Requirements
客户访问要求
Prior to granting customers access to data, assets, and information systems, identified security, contractual, and regulatory
requirements for customer access shall be addressed.应在赋予客户对数据、资产和信息系统的访问权之前,确定客户访
问的安全、合同和监管的要求。
Data Integrity
数据完整性
AIS-03
Data Security / Integrity 安
全/完整性
AIS-04
Data input and output integrity routines (i.e., reconciliation and edit checks) shall be implemented for application interfaces
and databases to prevent manual or systematic processing errors, corruption of data, or misuse.应对应用程序接口和数据
库的数据输入和输出进行常规的完整性校验(即:一致性和编辑检查),以防止人为或系统性的处理错误、数据损坏
或误用。
Policies and procedures shall be established and maintained in support of data security to include (confidentiality, integrity
and availability) across multiple system interfaces, jurisdictions and business functions to prevent improper disclosure,
alteration, or destruction.应建立并保持策略和规程,以支持跨越多个系统接口、司法管辖区和职能部门的数据的安全
(包括保密性、完整性和可用性),防止对数据不正当泄露、修改和破坏。
CSA GCR云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/1云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/1云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/�
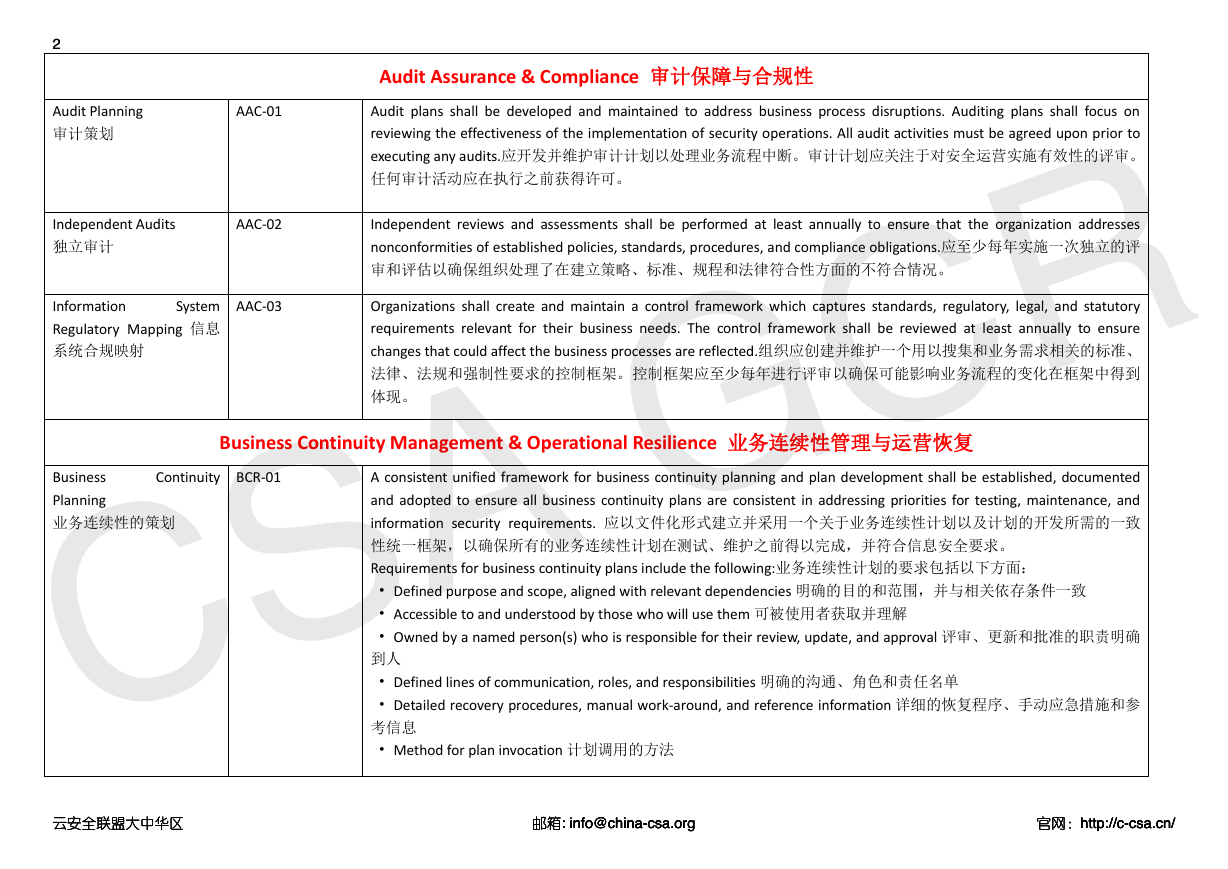
Audit Planning
审计策划
AAC-01
Independent Audits
独立审计
AAC-02
Information
System
Regulatory Mapping 信息
系统合规映射
AAC-03
Audit Assurance & Compliance 审计保障与合规性
Audit plans shall be developed and maintained to address business process disruptions. Auditing plans shall focus on
reviewing the effectiveness of the implementation of security operations. All audit activities must be agreed upon prior to
executing any audits.应开发并维护审计计划以处理业务流程中断。审计计划应关注于对安全运营实施有效性的评审。
任何审计活动应在执行之前获得许可。
Independent reviews and assessments shall be performed at least annually to ensure that the organization addresses
nonconformities of established policies, standards, procedures, and compliance obligations.应至少每年实施一次独立的评
审和评估以确保组织处理了在建立策略、标准、规程和法律符合性方面的不符合情况。
Organizations shall create and maintain a control framework which captures standards, regulatory, legal, and statutory
requirements relevant for their business needs. The control framework shall be reviewed at least annually to ensure
changes that could affect the business processes are reflected.组织应创建并维护一个用以搜集和业务需求相关的标准、
法律、法规和强制性要求的控制框架。控制框架应至少每年进行评审以确保可能影响业务流程的变化在框架中得到
体现。
Business Continuity Management & Operational Resilience 业务连续性管理与运营恢复
Continuity
Business
Planning
业务连续性的策划
BCR-01
A consistent unified framework for business continuity planning and plan development shall be established, documented
and adopted to ensure all business continuity plans are consistent in addressing priorities for testing, maintenance, and
information security requirements. 应以文件化形式建立并采用一个关于业务连续性计划以及计划的开发所需的一致
性统一框架,以确保所有的业务连续性计划在测试、维护之前得以完成,并符合信息安全要求。
Requirements for business continuity plans include the following:业务连续性计划的要求包括以下方面:
• Defined purpose and scope, aligned with relevant dependencies 明确的目的和范围,并与相关依存条件一致
• Accessible to and understood by those who will use them 可被使用者获取并理解
• Owned by a named person(s) who is responsible for their review, update, and approval 评审、更新和批准的职责明确
到人
• Defined lines of communication, roles, and responsibilities 明确的沟通、角色和责任名单
• Detailed recovery procedures, manual work-around, and reference information 详细的恢复程序、手动应急措施和参
考信息
• Method for plan invocation 计划调用的方法
CSA GCR云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/2云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/2云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/�
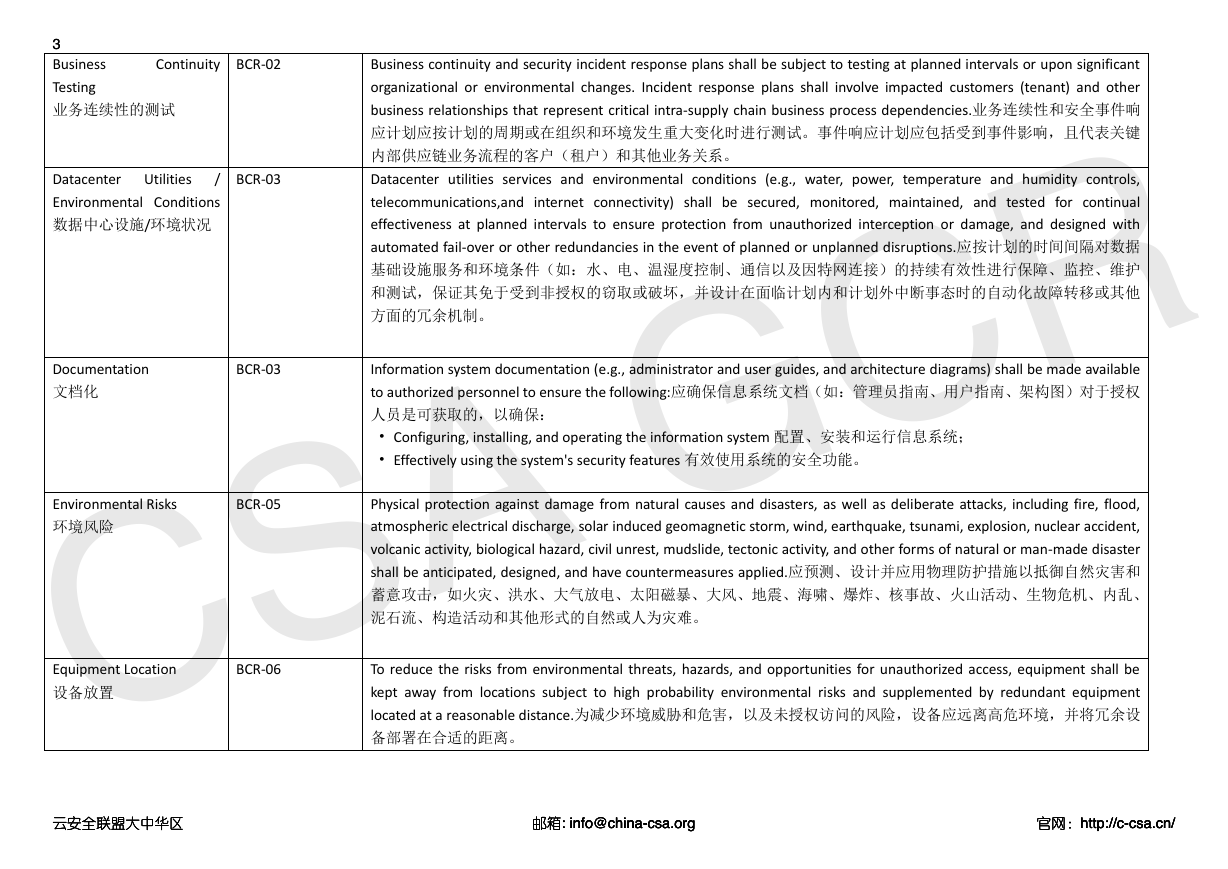
Continuity
Business
Testing
业务连续性的测试
BCR-02
Datacenter Utilities
/
Environmental Conditions
数据中心设施/环境状况
BCR-03
Documentation
文档化
BCR-03
Environmental Risks
环境风险
BCR-05
Business continuity and security incident response plans shall be subject to testing at planned intervals or upon significant
organizational or environmental changes. Incident response plans shall involve impacted customers (tenant) and other
business relationships that represent critical intra-supply chain business process dependencies.业务连续性和安全事件响
应计划应按计划的周期或在组织和环境发生重大变化时进行测试。事件响应计划应包括受到事件影响,且代表关键
内部供应链业务流程的客户(租户)和其他业务关系。
Datacenter utilities services and environmental conditions (e.g., water, power, temperature and humidity controls,
telecommunications,and internet connectivity) shall be secured, monitored, maintained, and tested for continual
effectiveness at planned intervals to ensure protection from unauthorized interception or damage, and designed with
automated fail-over or other redundancies in the event of planned or unplanned disruptions.应按计划的时间间隔对数据
基础设施服务和环境条件(如:水、电、温湿度控制、通信以及因特网连接)的持续有效性进行保障、监控、维护
和测试,保证其免于受到非授权的窃取或破坏,并设计在面临计划内和计划外中断事态时的自动化故障转移或其他
方面的冗余机制。
Information system documentation (e.g., administrator and user guides, and architecture diagrams) shall be made available
to authorized personnel to ensure the following:应确保信息系统文档(如:管理员指南、用户指南、架构图)对于授权
人员是可获取的,以确保:
• Configuring, installing, and operating the information system 配置、安装和运行信息系统;
• Effectively using the system's security features 有效使用系统的安全功能。
Physical protection against damage from natural causes and disasters, as well as deliberate attacks, including fire, flood,
atmospheric electrical discharge, solar induced geomagnetic storm, wind, earthquake, tsunami, explosion, nuclear accident,
volcanic activity, biological hazard, civil unrest, mudslide, tectonic activity, and other forms of natural or man-made disaster
shall be anticipated, designed, and have countermeasures applied.应预测、设计并应用物理防护措施以抵御自然灾害和
蓄意攻击,如火灾、洪水、大气放电、太阳磁暴、大风、地震、海啸、爆炸、核事故、火山活动、生物危机、内乱、
泥石流、构造活动和其他形式的自然或人为灾难。
Equipment Location
设备放置
BCR-06
To reduce the risks from environmental threats, hazards, and opportunities for unauthorized access, equipment shall be
kept away from locations subject to high probability environmental risks and supplemented by redundant equipment
located at a reasonable distance.为减少环境威胁和危害,以及未授权访问的风险,设备应远离高危环境,并将冗余设
备部署在合适的距离。
CSA GCR云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/3云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/3云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/�
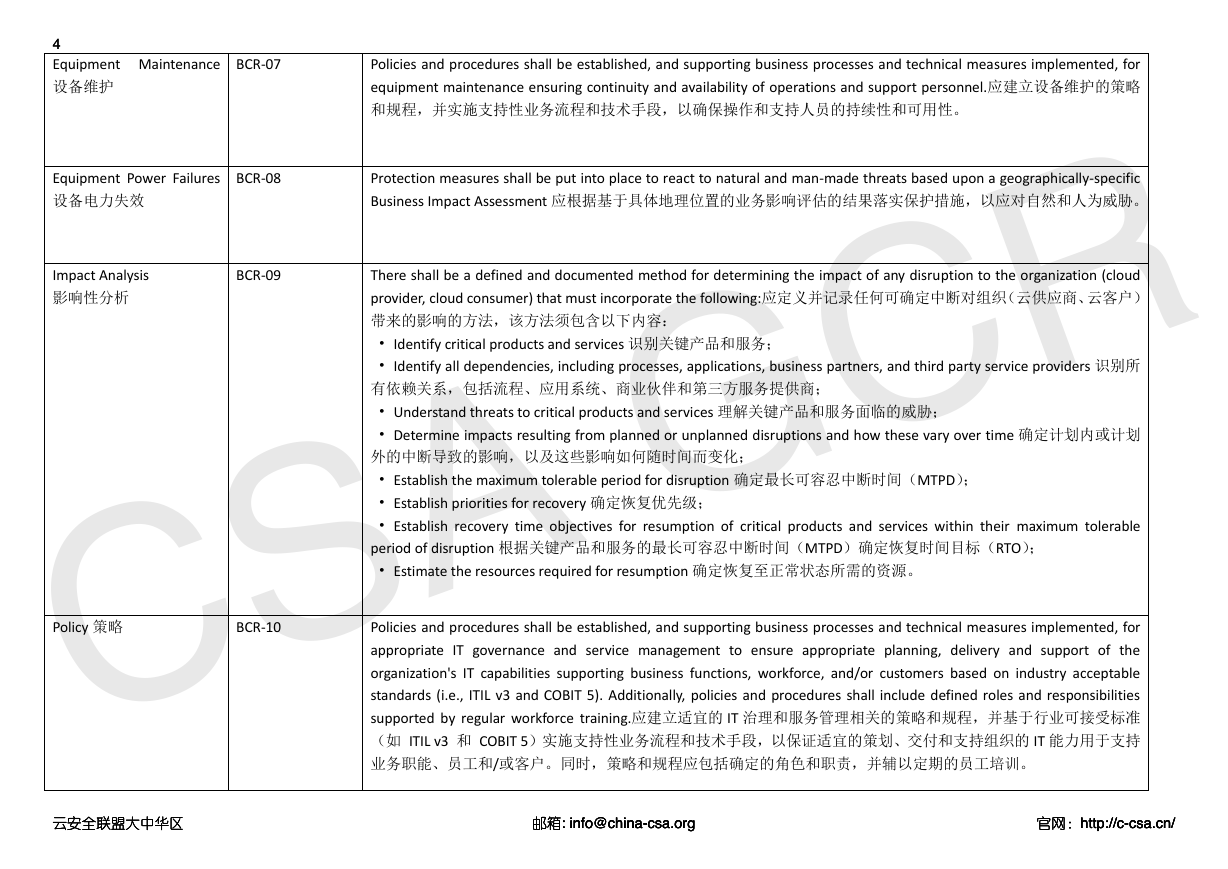
Equipment Maintenance
设备维护
BCR-07
Policies and procedures shall be established, and supporting business processes and technical measures implemented, for
equipment maintenance ensuring continuity and availability of operations and support personnel.应建立设备维护的策略
和规程,并实施支持性业务流程和技术手段,以确保操作和支持人员的持续性和可用性。
Equipment Power Failures
设备电力失效
BCR-08
Protection measures shall be put into place to react to natural and man-made threats based upon a geographically-specific
Business Impact Assessment 应根据基于具体地理位置的业务影响评估的结果落实保护措施,以应对自然和人为威胁。
Impact Analysis
影响性分析
BCR-09
Policy 策略
BCR-10
There shall be a defined and documented method for determining the impact of any disruption to the organization (cloud
provider, cloud consumer) that must incorporate the following:应定义并记录任何可确定中断对组织(云供应商、云客户)
带来的影响的方法,该方法须包含以下内容:
• Identify critical products and services 识别关键产品和服务;
• Identify all dependencies, including processes, applications, business partners, and third party service providers 识别所
有依赖关系,包括流程、应用系统、商业伙伴和第三方服务提供商;
• Understand threats to critical products and services 理解关键产品和服务面临的威胁;
• Determine impacts resulting from planned or unplanned disruptions and how these vary over time 确定计划内或计划
外的中断导致的影响,以及这些影响如何随时间而变化;
• Establish the maximum tolerable period for disruption 确定最长可容忍中断时间(MTPD);
• Establish priorities for recovery 确定恢复优先级;
• Establish recovery time objectives for resumption of critical products and services within their maximum tolerable
period of disruption 根据关键产品和服务的最长可容忍中断时间(MTPD)确定恢复时间目标(RTO);
• Estimate the resources required for resumption 确定恢复至正常状态所需的资源。
Policies and procedures shall be established, and supporting business processes and technical measures implemented, for
appropriate IT governance and service management to ensure appropriate planning, delivery and support of the
organization's IT capabilities supporting business functions, workforce, and/or customers based on industry acceptable
standards (i.e., ITIL v3 and COBIT 5). Additionally, policies and procedures shall include defined roles and responsibilities
supported by regular workforce training.应建立适宜的 IT 治理和服务管理相关的策略和规程,并基于行业可接受标准
(如 ITIL v3 和 COBIT 5)实施支持性业务流程和技术手段,以保证适宜的策划、交付和支持组织的 IT 能力用于支持
业务职能、员工和/或客户。同时,策略和规程应包括确定的角色和职责,并辅以定期的员工培训。
CSA GCR云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/4云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/4云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/�
Retention Policy 保 存 策
略
BCR-11
Policies and procedures shall be established, and supporting business processes and technical measures implemented, for
defining and adhering to the retention period of any critical asset as per established policies and procedures, as well as
applicable legal, statutory, or regulatory compliance obligations. Backup and recovery measures shall be incorporated as
part of business continuity planning and tested accordingly for effectiveness.应建立定义了所有关键资产保存期限的策略
和规程,并实施支持性业务流程和技术手段。每一项策略、规程以及适用的法律、法规和合规性义务应得到遵从。
备份与恢复措施也应该作为 BCP 的一个组成部分,并通过有效性测试。
Change Control & Configuration Management 变更控制和配置管理
Development
New
Acquisition
新开发/获取
/
CCC-01
Policies and procedures shall be established, and supporting business processes and technical measures implemented, to
ensure the development and/or acquisition of new data, physical or virtual applications, infrastructure network and systems
components, or any corporate, operations and/or datacenter facilities have been pre-authorized by the organization's
business leadership or other accountable business role or function.应建立策略和规程,并实施支持性业务流程和技术手
段,以确保开发和/或获取新数据、物理或虚拟应用、基础网络设施和系统组件、或任何公司的、运营的和/或数据
中心的设施时,得到组织的业务领导或其他负责的业务角色或部门的预授权。
Outsourced Development
外包开发
CCC-02
External business partners shall adhere to the same policies and procedures for change management, release, and testing
as internal developers within the organization (e.g. ITIL service management processes).外部业务伙伴应和组织内部开发
者一样遵守相同的变更、发布和测试策略和规程(如:ITIL 服务管理流程)。
Quality Testing
质量测试
CCC-03
Unauthorized
Software
Installations 非 授 权 软 件
安装
CCC-04
Organization shall follow a defined quality change control and testing process (e.g. ITIL Service Management) with
established baselines, testing, and release standards that focus on system availability, confidentiality, and integrity of
systems and services.组织应遵循已定义的质量变更控制和测试流程(如:ITIL 服务管理),基于已建立的关注于系统
可用性、保密性和系统/服务完整性的基线、测试和发布标准。
Policies and procedures shall be established, and supporting business processes and technical measures implemented, to
restrict the installation of unauthorized software on organizationally-owned or managed user end-point devices (e.g., issued
workstations, laptops, and mobile devices) and IT infrastructure network and systems components.应建立策略和规程,并
实施支持性业务流程和技术手段,以限制在组织拥有或管理的用户终端设备(如:配发的工作站、笔记本电脑和移
动设备)、IT 基础网络设施和系统组件上安装非授权软件。
CSA GCR云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/5云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/5云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/�
Production Changes
生产变更
CCC-05
Policies and procedures shall be established for managing the risks associated with applying changes to:应建立策略和规程
以管理与变更实施相关的风险:
• business-critical or customer (tenant)-impacting (physical and virtual) applications and system-system interface (API)
designs and configurations 对关键业务或客户(租户)产生影响(物理或虚拟)的应用程序,及系统间接口(API)的
设计和配置;
• infrastructure network and systems components 基础设施网络和系统组件;
Technical measures shall be implemented to provide assurance that all changes directly correspond to a registered change
request, business-critical or customer (tenant) , and/or authorization by, the customer (tenant) as per agreement (SLA) prior
to deployment.应实施技术手段来为所有直接与已登记的变更请求、关键业务或客户(租户)相关的变更提供保证,
并/或在部署前按协议(SLA)要求获得客户(租户)授权。
Data Security & Information Lifecycle Management 数据安全与信息生命周期管理
Classification
分类
DSI-01
Data and objects containing data shall be assigned a classification by the data owner based on data type, value, sensitivity,
and criticality to the organization.应由数据责任人基于数据类型、数据值和对于组织的敏感程度、关键程度,对数据和
包含数据的对象进行分类。
Data Inventory / Flows 数
据目录/数据流
DSI-02
Policies and procedures shall be established, and supporting business processes and technical measures implemented, to
inventory, document, and maintain data flows for data that is resident (permanently or temporarily) within the service's
geographically distributed (physical and virtual) applications and infrastructure network and systems components and/or
shared with other third parties to ascertain any regulatory, statutory, or supply chain agreement (SLA) compliance impact,
and to address any other business risks associated with the data. Upon request, provider shall inform customer (tenant) of
compliance impact and risk, especially if customer data is used as part of the services.应建立策略和规程,并实施支持性业
务流程和技术手段,对永久性或临时性留存在分布于物理和虚拟区域的服务中的应用程序、基础网络和系统组件的,
和/或其他第三方分享的数据进行归档、记录,以及数据流的维护,以确定任何有关法律法规或 SLA 符合性影响,并
确定其他和数据相关的业务风险。基于以上的要求,提供商应告知客户(租户)关于合规的影响和风险,特别是当
客户数据作为服务的一部分时。
CSA GCR云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/6云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/6云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/�
eCommerce Transactions
电子商务交易
DSI-03
Data related to electronic commerce (e-commerce) that traverses public networks shall be appropriately classified and
protected from fraudulent activity, unauthorized disclosure, or modification in such a manner to prevent contract dispute
and compromise of data.穿越公共网络的电子商务(e-commerce)数据应被适当的分类和保护,以防止遭受欺诈、非
授权披露或修改,避免合同纠纷和数据破坏。
/
Labeling
Handling
Security Policy
处理/标示/安全策略
/
DSI-04
Policies and procedures shall be established for the labeling, handling, and security of data and objects which contain data.
Mechanisms for label inheritance shall be implemented for objects that act as aggregate containers for data.应针对数据及
包含数据的对象,建立有关数据标识、处理和数据安全的策略和规程。对作为聚合数据容器的对象实行标签继承机
制。
Non-Production Data
非生产数据
DSI-05
Production data shall not be replicated or used in non-production environments. Any use of customer data in
non-production environments requires explicit, documented approval from all customers whose data is affected, and must
comply with all legal and regulatory requirements for scrubbing of sensitive data elements.应防止生产数据被复制或使用
于非生产环境。任何在非生产环境中使用客户数据的行为应该经该客户明确许可并记录,同时必须符合敏感数据擦
除相关的法律法规要求。
Ownership / Stewardship
责任人/管理者
DSI-06
All data shall be designated with stewardship, with assigned responsibilities defined, documented, and communicated.所有
数据的管理工作应被定义,并以文件化形式定义和传达被分配的职责。
Secure Disposal 安全处置 DSI-07
Policies and procedures shall be established with supporting business processes and technical measures implemented for
the secure disposal and complete removal of data from all storage media, ensuring data is not recoverable by any computer
forensic means.应建立策略和规程,并实施支持性业务流程和技术手段,以安全处置并完全移除所有存储介质中的数
据,确保数据没有被任何计算机取证方式所恢复。
CSA GCR云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/7云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/7云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/�
Asset Management
资产管理
DCS-01
Datacenter Security 数据中心安全
Assets must be classified in terms of business criticality, service-level expectations, and operational continuity
requirements. A complete inventory of business-critical assets located at all sites and/or geographical locations and their
usage over time shall be maintained and updated regularly, and assigned ownership by defined roles and responsibilities.必
须按照对业务的关键程度、服务级别期望和运营连续性的要求对资产进行分类。应针对所有场所和区域的资产以及
它们的用途,维护一份完整的关键业务资产清单,保持定期的更新,并按照定义的角色和职责来分配责任人。
Controlled Access Points
可控访问点
DCS-02
Physical security perimeters (e.g., fences, walls, barriers, guards, gates, electronic surveillance, physical authentication
mechanisms, reception desks, and security patrols) shall be implemented to safeguard sensitive data and information
systems.应实施物理安全边界(如:栅栏、墙、障碍物、保安、门、电子检测、物理认证机制、前台、安全巡逻)来
保护敏感数据和信息系统。
Equipment Identification
设备识别
DCS-03
Automated equipment identification shall be used as a method of connection authentication. Location-aware technologies
may be used to validate connection authentication integrity based on known equipment location.
应使用自动设备识别作为连接认证授权的方法。位置感知技术可被用于根据已知设备位置来验证连接认证的完整性。
Off-Site Authorization
场外授权
DCS-04
Authorization must be obtained prior to relocation or transfer of hardware, software, or data to an offsite premises.硬件、
软件或数据在搬移或传输到场外前必须经过授权。
Off-Site Equipment 场外设
备
DCS-05
Policies and procedures shall be established for the secure disposal of equipment (by asset type) used outside the
organization's premises. This shall include a wiping solution or destruction process that renders recovery of information
impossible. The erasure shall consist of a full overwrite of the drive to ensure that the erased drive is released to inventory
for reuse and deployment, or securely stored until it can be destroyed.应建立策略和规程,以保证组织场所以外的设备
(按资产类型),通过使信息不可恢复的擦除方案或破坏流程进行了安全处置。应通过对驱动器完整覆写的擦除方式,
来确保擦除的驱动器可以回归资源池以供再次使用和部署,或使数据被安全存储直至被破坏。
CSA GCR云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/8云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/8云安全联盟大中华区邮箱: info@china-csa.org官网:http://c-csa.cn/�









 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc