AWS Certified Solutions Architect Associate Practice Test 1
Question 1:
A tech company has a CRM application hosted on an Auto Scaling group of On-
Demand EC2 instances. The application is extensively used during office hours from
9 in the morning till 5 in the afternoon. Their users are complaining that the
performance of the application is slow during the start of the day but then works
normally after a couple of hours.
Which of the following can be done to ensure that the application works properly at
the beginning of the day?
•
Configure a Dynamic scaling policy for the Auto Scaling group to launch new instances
based on the CPU utilization.
•
Configure a Dynamic scaling policy for the Auto Scaling group to launch new instances
based on the Memory utilization.
•
Configure a Scheduled scaling policy for the Auto Scaling group to launch new instances
before the start of the day.
(Correct)
•
Set up an Application Load Balancer (ALB) to your architecture to ensure that the traffic is
properly distributed on the instances.
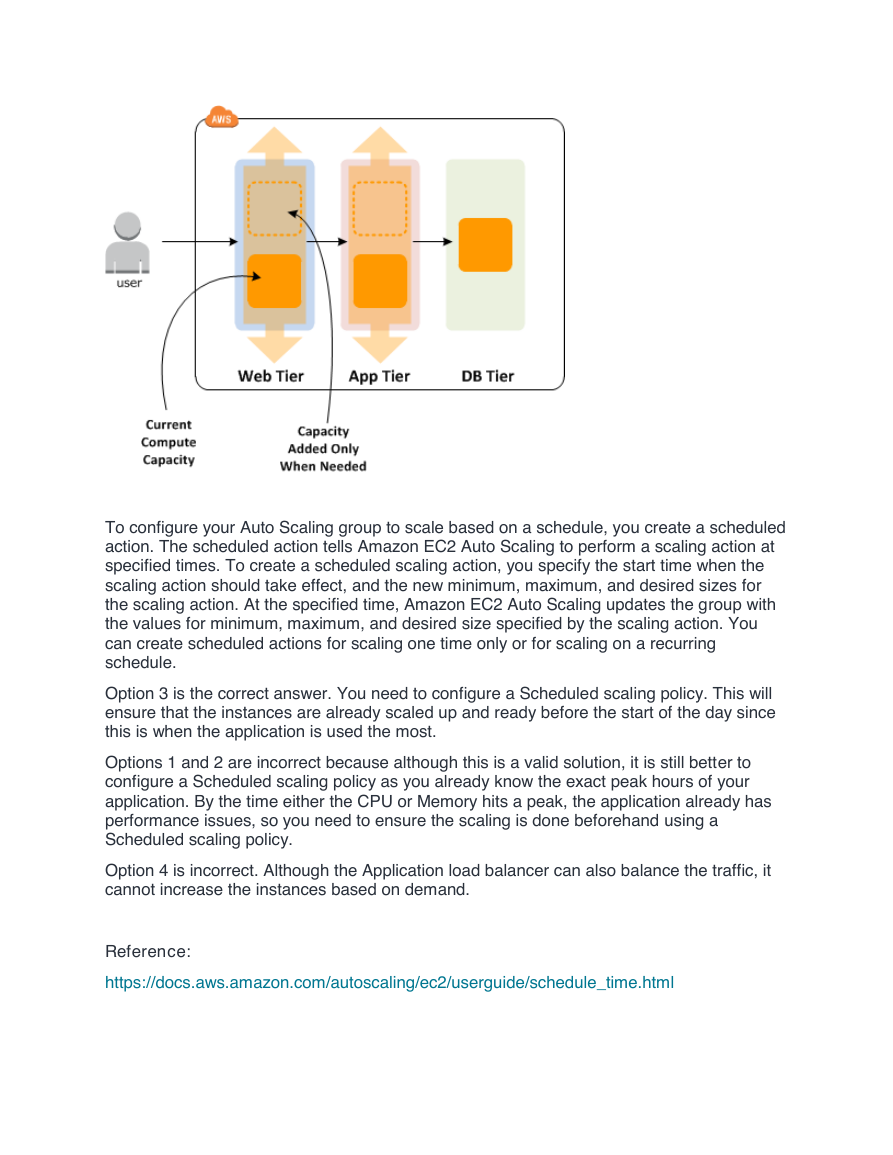
Explanation
Scaling based on a schedule allows you to scale your application in response to predictable
load changes. For example, every week the traffic to your web application starts to increase
on Wednesday, remains high on Thursday, and starts to decrease on Friday. You can plan
your scaling activities based on the predictable traffic patterns of your web application.
�
To configure your Auto Scaling group to scale based on a schedule, you create a scheduled
action. The scheduled action tells Amazon EC2 Auto Scaling to perform a scaling action at
specified times. To create a scheduled scaling action, you specify the start time when the
scaling action should take effect, and the new minimum, maximum, and desired sizes for
the scaling action. At the specified time, Amazon EC2 Auto Scaling updates the group with
the values for minimum, maximum, and desired size specified by the scaling action. You
can create scheduled actions for scaling one time only or for scaling on a recurring
schedule.
Option 3 is the correct answer. You need to configure a Scheduled scaling policy. This will
ensure that the instances are already scaled up and ready before the start of the day since
this is when the application is used the most.
Options 1 and 2 are incorrect because although this is a valid solution, it is still better to
configure a Scheduled scaling policy as you already know the exact peak hours of your
application. By the time either the CPU or Memory hits a peak, the application already has
performance issues, so you need to ensure the scaling is done beforehand using a
Scheduled scaling policy.
Option 4 is incorrect. Although the Application load balancer can also balance the traffic, it
cannot increase the instances based on demand.
Reference:
https://docs.aws.amazon.com/autoscaling/ec2/userguide/schedule_time.html
�
Check out this AWS Auto Scaling Cheat Sheet:
https://tutorialsdojo.com/aws-cheat-sheet-aws-auto-scaling/
Question 2:
You are deploying an Interactive Voice Response (IVR) telephony system in your
cloud architecture that interacts with callers, gathers information, and routes calls to
the appropriate recipients in your company. The system will be composed of an Auto
Scaling group of EC2 instances, an Application Load Balancer, and an RDS instance
in a Multi-AZ Deployments configuration. To protect the confidential data of your
customers, you have to ensure that your RDS database can only be accessed using
the profile credentials specific to your EC2 instances via an authentication token.
As the Solutions Architect of the company, which of the following should you do to
meet the above requirement?
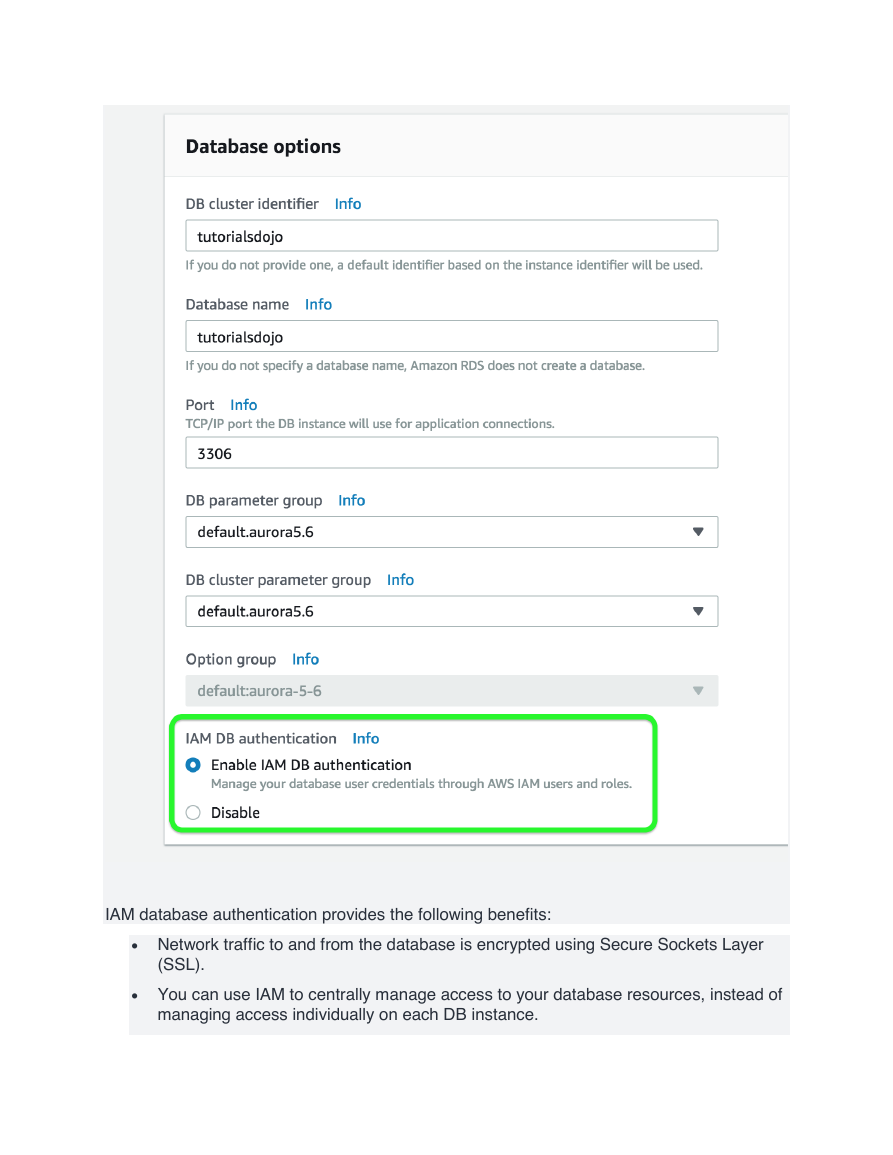
•
Enable the IAM DB Authentication.
•
•
(Correct)
Configure SSL in your application to encrypt the database connection to RDS.
Create an IAM Role and assign it to your EC2 instances which will grant exclusive access to
your RDS instance.
•
Use a combination of IAM and STS to restrict access to your RDS instance via a temporary
token.
Explanation
You can authenticate to your DB instance using AWS Identity and Access Management
(IAM) database authentication. IAM database authentication works with MySQL and
PostgreSQL. With this authentication method, you don't need to use a password when you
connect to a DB instance. Instead, you use an authentication token.
An authentication token is a unique string of characters that Amazon RDS generates on
request. Authentication tokens are generated using AWS Signature Version 4. Each token
has a lifetime of 15 minutes. You don't need to store user credentials in the database,
because authentication is managed externally using IAM. You can also still use standard
database authentication.
�
IAM database authentication provides the following benefits:
• Network traffic to and from the database is encrypted using Secure Sockets Layer
(SSL).
• You can use IAM to centrally manage access to your database resources, instead of
managing access individually on each DB instance.
�
• For applications running on Amazon EC2, you can use profile credentials specific to
your EC2 instance to access your database instead of a password, for greater
security
Hence, Option 1 is the correct answer based on the above reference.
Option 2 is incorrect because an SSL connection is not using an authentication token from
IAM. Although configuring SSL to your application can improve the security of your data in
flight, it is still not a suitable option to use in this scenario.
Option 3 is incorrect because although you can create and assign an IAM Role to your EC2
instances, you still need to configure your RDS to use IAM DB Authentication.
Option 4 is incorrect because you have to use IAM DB Authentication for this scenario, and
not a combination of an IAM and STS. Although STS is used to send temporary tokens for
authentication, this is not a compatible use case for RDS.
Reference:
https://docs.aws.amazon.com/AmazonRDS/latest/UserGuide/UsingWithRDS.IAMDBAuth.ht
ml
Check out this Amazon RDS cheat sheet:
https://tutorialsdojo.com/aws-cheat-sheet-amazon-relational-database-service-amazon-rds/
Question 3:
You founded a tech startup that provides online training and software development
courses to various students across the globe. Your team has developed an online
portal in AWS where the students can log into and access the courses they are
subscribed to.
Since you are in the early phases of the startup and the funding is still hard to come
by, which service can help you manage the budgets for all your AWS resources?
•
•
•
Cost Explorer
Cost Allocation Tags
AWS Budgets
(Correct)
�
•
Payment History
Explanation
AWS Budgets gives you the ability to set custom budgets that alert you when your costs or
usage exceed (or are forecasted to exceed) your budgeted amount.
Budgets can be tracked at the monthly, quarterly, or yearly level, and you can customize the
start and end dates. You can further refine your budget to track costs associated with
multiple dimensions, such as AWS service, linked account, tag, and others. Budget alerts
can be sent via email and/or Amazon Simple Notification Service (SNS) topic.
You can also use AWS Budgets to set a custom reservation utilization target and receive
alerts when your utilization drops below the threshold you define. RI utilization alerts
support Amazon EC2, Amazon RDS, Amazon Redshift, and Amazon ElastiCache
reservations.
Budgets can be created and tracked from the AWS Budgets dashboard or via the Budgets
API.
Option 1 is incorrect because the Cost Explorer only helps you visualize and manage your
AWS costs and usages over time. It offers a set of reports you can view data with for up to
the last 13 months, forecast how much you're likely to spend for the next three months, and
get recommendations for what Reserved Instances to purchase. You use Cost Explorer to
identify areas that need further inquiry and see trends to understand your costs.
Option 2 is incorrect because Cost Allocation Tags only eases the organization of your
resource costs on your cost allocation report, to make it easier for you to categorize and
track your AWS costs.
Option 4 is incorrect because the payment history option only provides a location where you
can view the monthly invoices you receive from AWS. If your account isn't past due, the
Payment History page shows only previous invoices and payment status.
Reference:
https://aws.amazon.com/aws-cost-management/aws-budgets/
Check out this AWS Billing and Cost Management Cheat Sheet:
https://tutorialsdojo.com/aws-cheat-sheet-aws-billing-and-cost-management/
Question 4:
You are trying to establish an SSH connection to a newly created Amazon EC2
instance using the PuTTY tool. However, you are getting the following error
message:
Error: No supported authentication methods available
�
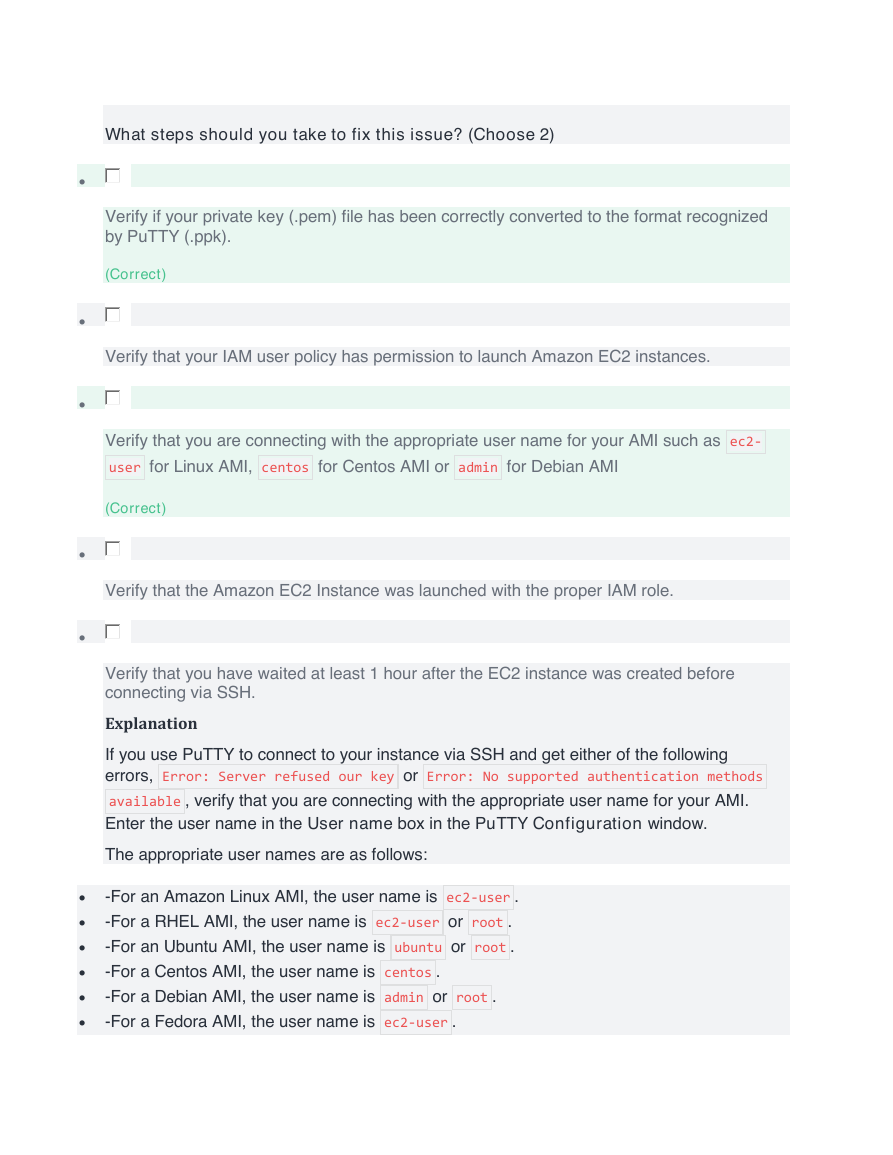
What steps should you take to fix this issue? (Choose 2)
•
Verify if your private key (.pem) file has been correctly converted to the format recognized
by PuTTY (.ppk).
•
•
•
•
(Correct)
Verify that your IAM user policy has permission to launch Amazon EC2 instances.
Verify that you are connecting with the appropriate user name for your AMI such as ec2-
user for Linux AMI, centos for Centos AMI or admin for Debian AMI
(Correct)
Verify that the Amazon EC2 Instance was launched with the proper IAM role.
Verify that you have waited at least 1 hour after the EC2 instance was created before
connecting via SSH.
Explanation
If you use PuTTY to connect to your instance via SSH and get either of the following
errors, Error: Server refused our key or Error: No supported authentication methods
available , verify that you are connecting with the appropriate user name for your AMI.
Enter the user name in the User name box in the PuTTY Configuration window.
The appropriate user names are as follows:
•
•
•
•
•
•
-For an Amazon Linux AMI, the user name is ec2-user .
-For a RHEL AMI, the user name is ec2-user or root .
-For an Ubuntu AMI, the user name is ubuntu or root .
-For a Centos AMI, the user name is centos .
-For a Debian AMI, the user name is admin or root .
-For a Fedora AMI, the user name is ec2-user .
�
•
•
-For a SUSE AMI, the user name is ec2-user or root .
-Otherwise, if ec2-user and root don't work, check with the AMI provider.
You should also verify that your private key (.pem) file has been correctly converted to the
format recognized by PuTTY (.ppk).
Options 2 and 4 are incorrect because both an IAM user and IAM role policy have nothing
to do with this issue.
Option 5 is incorrect because you don't need to wait an hour in order to connect to a new
EC2 instance as you can immediately connect to it once it is created.
Reference:
https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/TroubleshootingInstancesConnec
ting.html#TroubleshootingInstancesConnectingPuTTY
Check out this Amazon EC2 Cheat Sheet:
https://tutorialsdojo.com/aws-cheat-sheet-amazon-elastic-compute-cloud-amazon-ec2/
Question 5:
A Solutions Architect is designing an online medical system in AWS which will store
sensitive Personally Identifiable Information (PII) of the users in an Amazon S3
bucket. Both the master keys and the unencrypted data should never be sent to AWS
to comply with the strict compliance and regulatory requirements of the company.
Which S3 encryption technique should the Architect use?
•
•
•
•
Use S3 client-side encryption with a KMS-managed customer master key.
Use S3 client-side encryption with a client-side master key.
(Correct)
Use S3 server-side encryption with a KMS managed key.
�











 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc