Modeling and Simulation of MAC for QoS in IEEE 802.11e Using
OPNET Modeler
Weihua Helen Xi, Toby Whitley, Alistair Munro, Michael Barton
Networks & Protocols Group, CCR, Department of Electrical & Electronic Engineering, University of Bristol
Bristol, UK BS8 1UB
email: helen.xi@bristol.ac.uk
Abstract
This paper presents an IEEE 802.11e model developed using the
OPNET Modeler, which is employed for Medium Access
Control (MAC) enhancements for Quality of Service (QoS).
IEEE 802.11e QoS is implemented using the concept of varying
levels of service for different traffic types. Four Access
Categories (ACs) are defined with each supporting a different
priority for accessing the radio channel. The QoS station
(QSTA) based on the existing 802.11 model but using an AC
priority queuing and access mechanism is presented. The
enhanced queue provides virtual contention for a transmission
opportunity with higher ACs having a greater probability of
success. This work offers a flexible and more accurate model to
simulate the performance of QoS mechanisms within the
802.11e draft. The simulation results prove this model performs
as expected and demonstrate the performance of different traffic
types under different network configurations for the selected
workload.
1. Introduction
Simple deployment and high transmission speed make the
Wireless Local Area Networks (WLAN) more accepted in
public areas like offices and airports. IEEE 802.11 [1] defines the
WLAN MAC and Physical Layer (PHY) Specifications. 802.11b
extends the higher-speed PHY to 11Mbps in the 2.4 GHz band.
The standard OPNET WLAN model is based on these two
specifications. 802.11a [2] provides eight PHY modes with
transmission rates up to 54Mbps by operating in the less used
5GHz unlicensed frequency band. Recently, with the increasing
demands in transmitting multimedia over radio medium, the
IEEE 802.11e draft [3] defines MAC enhancements to support
LAN applications with QoS requirements.
This paper describes an approach for modeling the MAC
enhancements for QoS in 802.11e, based on the OPNET 802.11a
contributed model [4]. The OPNET 802.11 WLAN standard
model served as the foundation for the 802.11a contributed
model, in which the MAC and especially the PHY are heavily
modified. In the presented 802.11e model, a priority queue to
provide virtual contention among different traffic types for a
transmission opportunity within one station is defined, together
with changes in MAC to adapt the 802.11e standard. The eight
PHY modes with the Orthogonal Frequency Division
Multiplexing (OFDM) modulation schemes developed in the
802.11a model are applied.
This paper is organized as follows: Section 2 provides a brief
introduction to the legacy MAC defined in 802.11 and 802.11b;
the MAC enhancements in the 802.11e draft follow in Section 3;
Section 4 presents the implementation of the MAC
1
enhancements in OPNET; the simulation results are
demonstrated in Section 5 and finally, the paper is concluded in
Section 6.
2. 802.11 MAC Overview
The IEEE 802.11 MAC specifies two access methods, the
fundamental Distributed Coordination function (DCF) and the
optional Point Coordination Function (PCF). Most of the
commercial 802.11 products only employ contention based
DCF. Considering the doubts on the efficiency of PCF [5], it was
chosen to implement the 802.11e model supporting DCF mode
only.
DCF: The fundamental access method of the IEEE 802.11 MAC
is known as Carrier Sense Multiple Access with Collision
Avoidance (CSMA/CA). All the stations share one radio
channel, and before a station transmits data, the channel must be
idle for a contention period. To determine whether the channel is
idle or not, the station (STA) needs to continuously sense it
throughout this period. If the STA detects a signal with power
higher than a specific fixed power threshold, the radio channel is
assumed to be busy and thus unavailable for transmission. The
contention period includes a DCF Interframe Space (DIFS) and a
backoff period. The DIFS is 34µs in 802.11a and the additional
backoff period is determined as a multiple of a 9µs slot time.
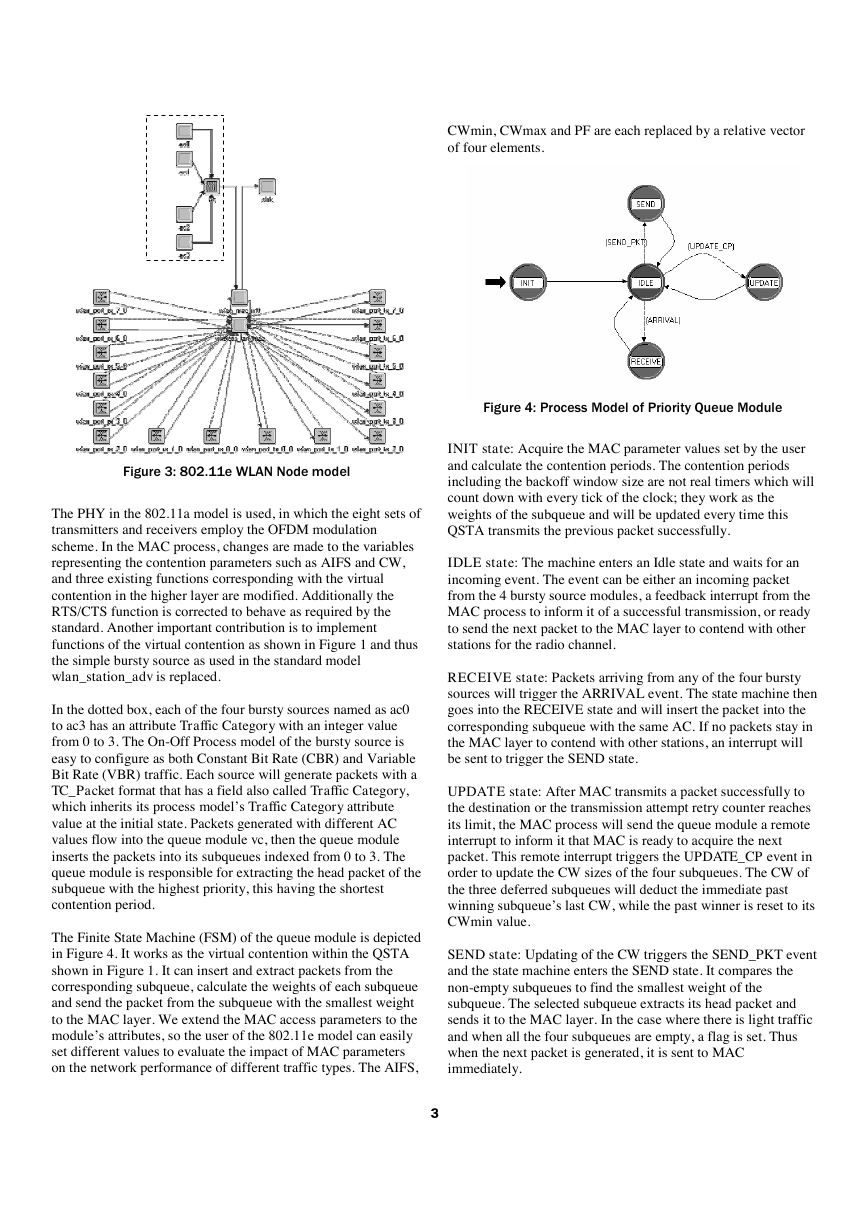
IFS: The interval between frames is called the Interframe Space
(IFS). IFS has four types in 802.11 (three shown in Figure 2).
Short IFS (SIFS) is used for an ACK frame and a CTS frame
responding to a data frame and a RTS frame, respectively. PCF
IFS (PIFS) is used by STAs operating under PCF mode to gain
priority access to the medium. In the DCF mode, DIFS is used
instead of PIFS in PCF mode. The shorter the contention period,
the higher the priority is to access the wireless medium.
CW: After sensing the channel idle for DIFS, to minimize the
collision possibility, the STA generates a random backoff period
for an additional deferral time before transmitting. The
Contention Window (CW) is used to determine the number of
slot times in the backoff period. The initial value of CW, or the
reset of CW after a successful transmission attempt, is CWmin.
The CW size will double for every unsuccessful attempt, until
the CW reaches the value of CWmax. The STAs deferred from
channel access during busy period holds the backoff value and
continue to count down the CW.
RTS/CTS: Because of the limited radio range, the transmitting
station may be unaware of stations that can interfere with the
receiving station. The Request to Send (RTS) and Clear to Send
(CTS) mechanism is used to mitigate this hidden station
�
problem. The RTS/CTS frames transmitted prior to the actual
data frame contain the Network Allocation Vector (NAV) field,
which defines the period of time that the medium is to be
reserved until the end of the Acknowledgement (ACK) to the
following data frame. All STAs within the reception range of
either the originating STA (which transmits the RTS) or the
destination STA (which transmits the CTS) will keep quiet. The
header of the data frame also contains the NAV.
PCF: The PCF provides the contention free frame transfer. This
mode only works in infrastructure networks with the Access
Point (AP) working as a Point Coordinator (PC), which performs
the role of the polling master. The PCF distributes information
within Beacon management frames to gain control of the
medium by setting the NAV in STAs.
3. MAC Enhancements for QoS in 802.11e
The QoS of 802.11e is achieved by providing different classes of
frames with different priorities when accessing the radio
channel. The access method in 802.11e is called Hybrid
Coordination Function (HCF) and combines functions from both
the DCF and the PCF. The EDCF working in the Contention
Period (CP) is the Enhanced version of DCF, which is
implemented in this model. The PCF in the Contention Free
Period (CFP) is beyond the scope of this paper.
Each QoS data packet in QSTA carries its priority value (0 to 7)
in the MAC frame header. The QSTA provides four physical
queues, or ACs, to map the eight Traffic Categories (TCs). The
priority mappings are described in Table 1, taken from the IEEE
802.1d bridge specification [6].
Table 1: Access Category Mapping
User
Priority
Access
Category
Traffic Type
1
2
0
3
4
5
6
7
0
0
1
1
2
2
3
3
Background
Spare
Best Effort
Excellent Effort
Controlled Load
“Video” < 100ms latency and jitter
“Voice” < 10ms latency and jitter
Network Control
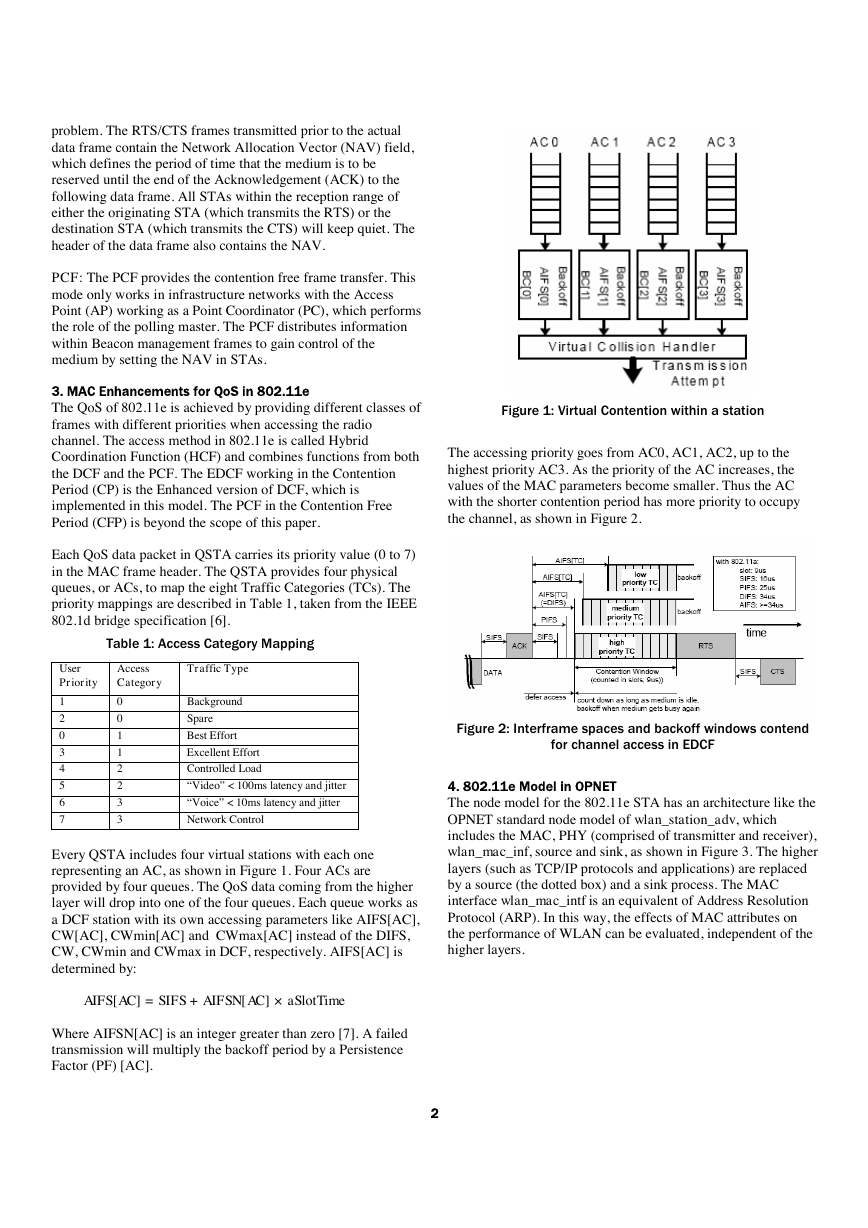
Every QSTA includes four virtual stations with each one
representing an AC, as shown in Figure 1. Four ACs are
provided by four queues. The QoS data coming from the higher
layer will drop into one of the four queues. Each queue works as
a DCF station with its own accessing parameters like AIFS[AC],
CW[AC], CWmin[AC] and CWmax[AC] instead of the DIFS,
CW, CWmin and CWmax in DCF, respectively. AIFS[AC] is
determined by:
AIFS[AC] = SIFS + AIFSN[AC] × aSlotTime
Where AIFSN[AC] is an integer greater than zero [7]. A failed
transmission will multiply the backoff period by a Persistence
Factor (PF) [AC].
2
Figure 1: Virtual Contention within a station
The accessing priority goes from AC0, AC1, AC2, up to the
highest priority AC3. As the priority of the AC increases, the
values of the MAC parameters become smaller. Thus the AC
with the shorter contention period has more priority to occupy
the channel, as shown in Figure 2.
Figure 2: Interframe spaces and backoff windows contend
for channel access in EDCF
4. 802.11e Model in OPNET
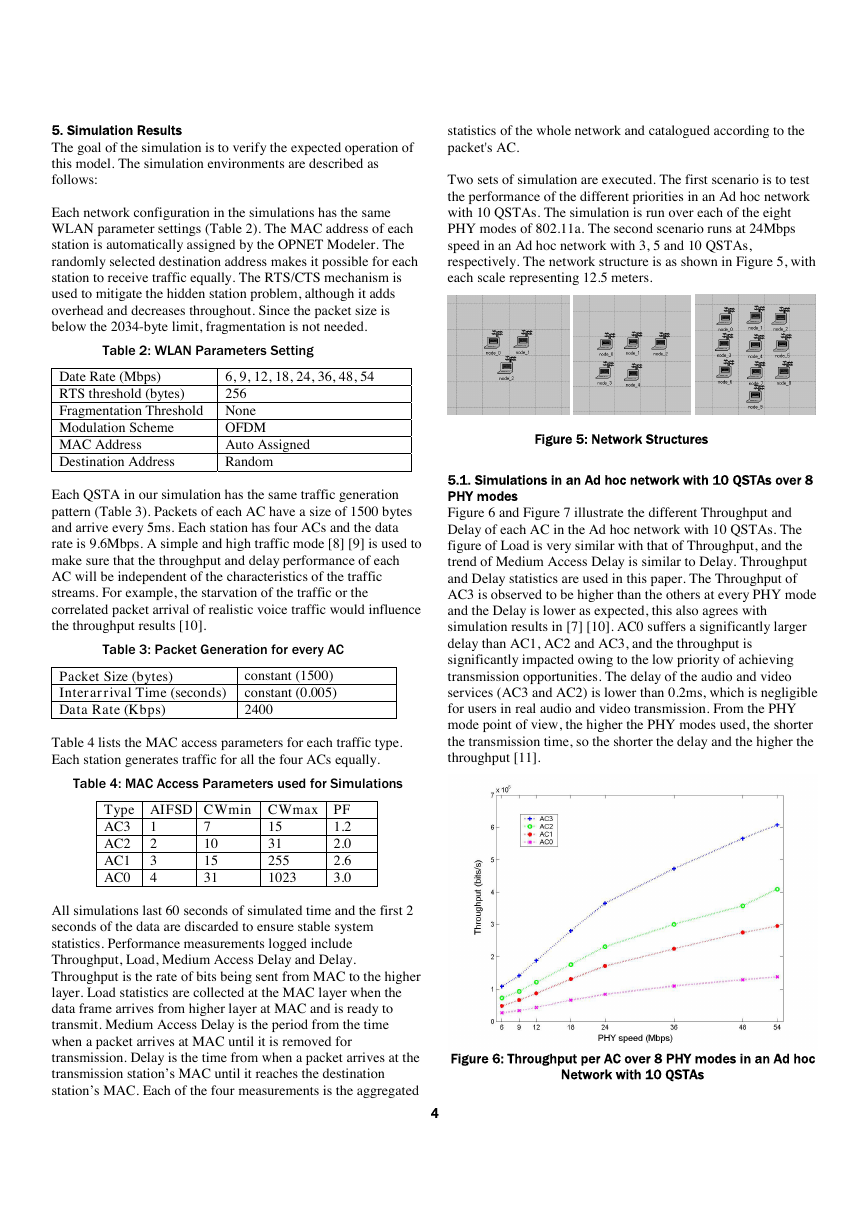
The node model for the 802.11e STA has an architecture like the
OPNET standard node model of wlan_station_adv, which
includes the MAC, PHY (comprised of transmitter and receiver),
wlan_mac_inf, source and sink, as shown in Figure 3. The higher
layers (such as TCP/IP protocols and applications) are replaced
by a source (the dotted box) and a sink process. The MAC
interface wlan_mac_intf is an equivalent of Address Resolution
Protocol (ARP). In this way, the effects of MAC attributes on
the performance of WLAN can be evaluated, independent of the
higher layers.
�
CWmin, CWmax and PF are each replaced by a relative vector
of four elements.
Figure 3: 802.11e WLAN Node model
The PHY in the 802.11a model is used, in which the eight sets of
transmitters and receivers employ the OFDM modulation
scheme. In the MAC process, changes are made to the variables
representing the contention parameters such as AIFS and CW,
and three existing functions corresponding with the virtual
contention in the higher layer are modified. Additionally the
RTS/CTS function is corrected to behave as required by the
standard. Another important contribution is to implement
functions of the virtual contention as shown in Figure 1 and thus
the simple bursty source as used in the standard model
wlan_station_adv is replaced.
In the dotted box, each of the four bursty sources named as ac0
to ac3 has an attribute Traffic Category with an integer value
from 0 to 3. The On-Off Process model of the bursty source is
easy to configure as both Constant Bit Rate (CBR) and Variable
Bit Rate (VBR) traffic. Each source will generate packets with a
TC_Packet format that has a field also called Traffic Category,
which inherits its process model’s Traffic Category attribute
value at the initial state. Packets generated with different AC
values flow into the queue module vc, then the queue module
inserts the packets into its subqueues indexed from 0 to 3. The
queue module is responsible for extracting the head packet of the
subqueue with the highest priority, this having the shortest
contention period.
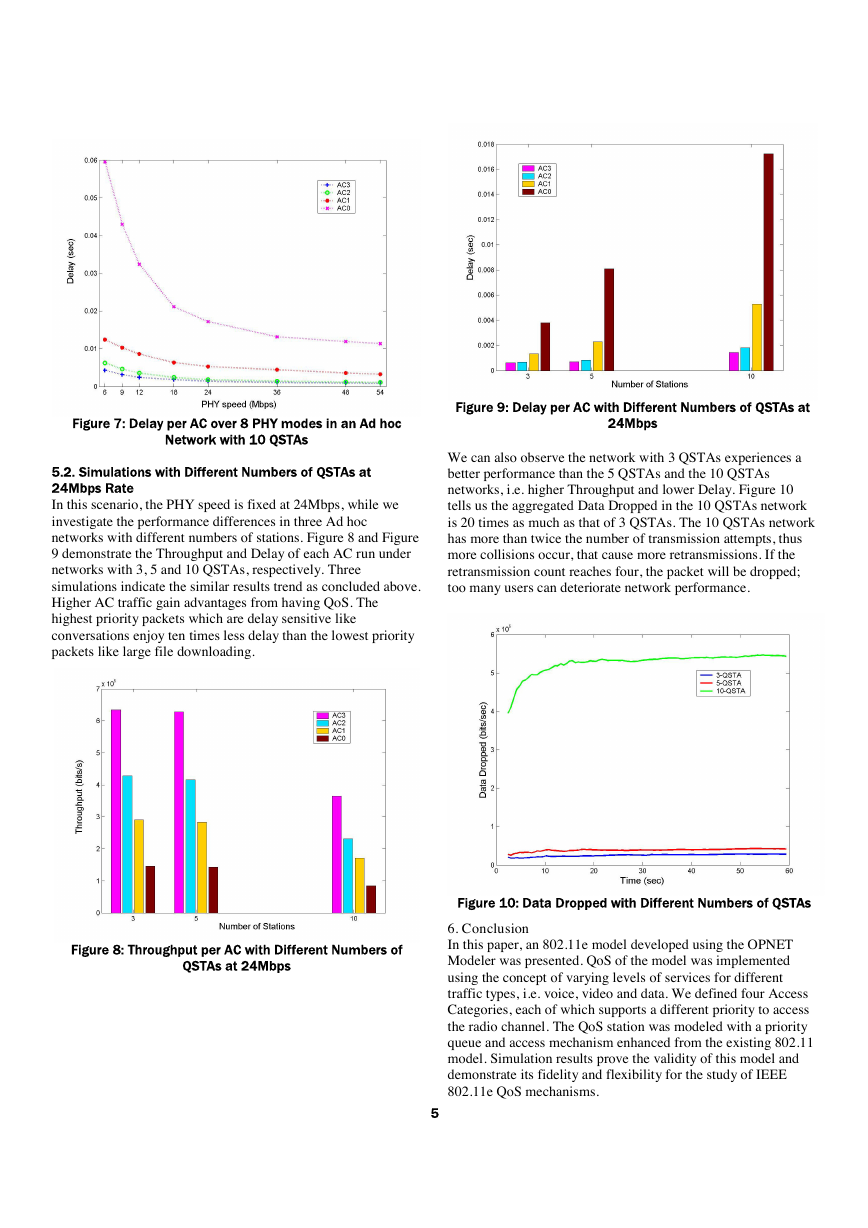
The Finite State Machine (FSM) of the queue module is depicted
in Figure 4. It works as the virtual contention within the QSTA
shown in Figure 1. It can insert and extract packets from the
corresponding subqueue, calculate the weights of each subqueue
and send the packet from the subqueue with the smallest weight
to the MAC layer. We extend the MAC access parameters to the
module’s attributes, so the user of the 802.11e model can easily
set different values to evaluate the impact of MAC parameters
on the network performance of different traffic types. The AIFS,
3
Figure 4: Process Model of Priority Queue Module
INIT state: Acquire the MAC parameter values set by the user
and calculate the contention periods. The contention periods
including the backoff window size are not real timers which will
count down with every tick of the clock; they work as the
weights of the subqueue and will be updated every time this
QSTA transmits the previous packet successfully.
IDLE state: The machine enters an Idle state and waits for an
incoming event. The event can be either an incoming packet
from the 4 bursty source modules, a feedback interrupt from the
MAC process to inform it of a successful transmission, or ready
to send the next packet to the MAC layer to contend with other
stations for the radio channel.
RECEIVE state: Packets arriving from any of the four bursty
sources will trigger the ARRIVAL event. The state machine then
goes into the RECEIVE state and will insert the packet into the
corresponding subqueue with the same AC. If no packets stay in
the MAC layer to contend with other stations, an interrupt will
be sent to trigger the SEND state.
UPDATE state: After MAC transmits a packet successfully to
the destination or the transmission attempt retry counter reaches
its limit, the MAC process will send the queue module a remote
interrupt to inform it that MAC is ready to acquire the next
packet. This remote interrupt triggers the UPDATE_CP event in
order to update the CW sizes of the four subqueues. The CW of
the three deferred subqueues will deduct the immediate past
winning subqueue’s last CW, while the past winner is reset to its
CWmin value.
SEND state: Updating of the CW triggers the SEND_PKT event
and the state machine enters the SEND state. It compares the
non-empty subqueues to find the smallest weight of the
subqueue. The selected subqueue extracts its head packet and
sends it to the MAC layer. In the case where there is light traffic
and when all the four subqueues are empty, a flag is set. Thus
when the next packet is generated, it is sent to MAC
immediately.
�
5. Simulation Results
The goal of the simulation is to verify the expected operation of
this model. The simulation environments are described as
follows:
Each network configuration in the simulations has the same
WLAN parameter settings (Table 2). The MAC address of each
station is automatically assigned by the OPNET Modeler. The
randomly selected destination address makes it possible for each
station to receive traffic equally. The RTS/CTS mechanism is
used to mitigate the hidden station problem, although it adds
overhead and decreases throughout. Since the packet size is
below the 2034-byte limit, fragmentation is not needed.
Table 2: WLAN Parameters Setting
statistics of the whole network and catalogued according to the
packet's AC.
Two sets of simulation are executed. The first scenario is to test
the performance of the different priorities in an Ad hoc network
with 10 QSTAs. The simulation is run over each of the eight
PHY modes of 802.11a. The second scenario runs at 24Mbps
speed in an Ad hoc network with 3, 5 and 10 QSTAs,
respectively. The network structure is as shown in Figure 5, with
each scale representing 12.5 meters.
6, 9, 12, 18, 24, 36, 48, 54
256
Date Rate (Mbps)
RTS threshold (bytes)
Fragmentation Threshold None
Modulation Scheme
MAC Address
Destination Address
OFDM
Auto Assigned
Random
Each QSTA in our simulation has the same traffic generation
pattern (Table 3). Packets of each AC have a size of 1500 bytes
and arrive every 5ms. Each station has four ACs and the data
rate is 9.6Mbps. A simple and high traffic mode [8] [9] is used to
make sure that the throughput and delay performance of each
AC will be independent of the characteristics of the traffic
streams. For example, the starvation of the traffic or the
correlated packet arrival of realistic voice traffic would influence
the throughput results [10].
Table 3: Packet Generation for every AC
Packet Size (bytes)
Interarrival Time (seconds)
Data Rate (Kbps)
constant (1500)
constant (0.005)
2400
Table 4 lists the MAC access parameters for each traffic type.
Each station generates traffic for all the four ACs equally.
Table 4: MAC Access Parameters used for Simulations
Figure 5: Network Structures
5.1. Simulations in an Ad hoc network with 10 QSTAs over 8
PHY modes
Figure 6 and Figure 7 illustrate the different Throughput and
Delay of each AC in the Ad hoc network with 10 QSTAs. The
figure of Load is very similar with that of Throughput, and the
trend of Medium Access Delay is similar to Delay. Throughput
and Delay statistics are used in this paper. The Throughput of
AC3 is observed to be higher than the others at every PHY mode
and the Delay is lower as expected, this also agrees with
simulation results in [7] [10]. AC0 suffers a significantly larger
delay than AC1, AC2 and AC3, and the throughput is
significantly impacted owing to the low priority of achieving
transmission opportunities. The delay of the audio and video
services (AC3 and AC2) is lower than 0.2ms, which is negligible
for users in real audio and video transmission. From the PHY
mode point of view, the higher the PHY modes used, the shorter
the transmission time, so the shorter the delay and the higher the
throughput [11].
Type AIFSD CWmin CWmax PF
1.2
AC3
AC2
2.0
2.6
AC1
AC0
3.0
15
31
255
1023
7
10
15
31
1
2
3
4
All simulations last 60 seconds of simulated time and the first 2
seconds of the data are discarded to ensure stable system
statistics. Performance measurements logged include
Throughput, Load, Medium Access Delay and Delay.
Throughput is the rate of bits being sent from MAC to the higher
layer. Load statistics are collected at the MAC layer when the
data frame arrives from higher layer at MAC and is ready to
transmit. Medium Access Delay is the period from the time
when a packet arrives at MAC until it is removed for
transmission. Delay is the time from when a packet arrives at the
transmission station’s MAC until it reaches the destination
station’s MAC. Each of the four measurements is the aggregated
4
Figure 6: Throughput per AC over 8 PHY modes in an Ad hoc
Network with 10 QSTAs
�
Figure 7: Delay per AC over 8 PHY modes in an Ad hoc
Network with 10 QSTAs
5.2. Simulations with Different Numbers of QSTAs at
24Mbps Rate
In this scenario, the PHY speed is fixed at 24Mbps, while we
investigate the performance differences in three Ad hoc
networks with different numbers of stations. Figure 8 and Figure
9 demonstrate the Throughput and Delay of each AC run under
networks with 3, 5 and 10 QSTAs, respectively. Three
simulations indicate the similar results trend as concluded above.
Higher AC traffic gain advantages from having QoS. The
highest priority packets which are delay sensitive like
conversations enjoy ten times less delay than the lowest priority
packets like large file downloading.
Figure 9: Delay per AC with Different Numbers of QSTAs at
24Mbps
We can also observe the network with 3 QSTAs experiences a
better performance than the 5 QSTAs and the 10 QSTAs
networks, i.e. higher Throughput and lower Delay. Figure 10
tells us the aggregated Data Dropped in the 10 QSTAs network
is 20 times as much as that of 3 QSTAs. The 10 QSTAs network
has more than twice the number of transmission attempts, thus
more collisions occur, that cause more retransmissions. If the
retransmission count reaches four, the packet will be dropped;
too many users can deteriorate network performance.
Figure 8: Throughput per AC with Different Numbers of
QSTAs at 24Mbps
Figure 10: Data Dropped with Different Numbers of QSTAs
6. Conclusion
In this paper, an 802.11e model developed using the OPNET
Modeler was presented. QoS of the model was implemented
using the concept of varying levels of services for different
traffic types, i.e. voice, video and data. We defined four Access
Categories, each of which supports a different priority to access
the radio channel. The QoS station was modeled with a priority
queue and access mechanism enhanced from the existing 802.11
model. Simulation results prove the validity of this model and
demonstrate its fidelity and flexibility for the study of IEEE
802.11e QoS mechanisms.
5
�
References
[1] IEEE Std. 802.11-1999, Part 11: Wireless LAN Medium Access
Control (MAC) and Physical Layer (PHY) Specifications, Reference
number ISO/IEC 8802-11:1999(E), IEEE Std. 802.11, 1999
edition, 1999.
[2] IEEE Std. 802-11a, IEEE Standard for Wireless LAN Medium
Access Control (MAC) and Physical Layer (PHY) Specifications: High-
Speed Physical Layer in the 5 GHz Band, September 1999.
[3] IEEE 802.11e/D4.0, Draft Supplement to Part 11: Wireless Medium
Access Control (MAC) and physical layer (PHY) specifications:
Medium Access Control (MAC) Enhancements for Quality of Service
(QoS), November 2002.
[4] B. E. Braswell, J. C. McEachen, "A Baseline Model for the IEEEE
802.11A WLAN Protocol," OPNETWORK 2001 Proceedings, August
2001.
[5] S. Mangold, S. Choi, “IEEE 802.11e Wireless LAN for Quality of
Service,” in Proc. European Wireless ’02, Florence, Italy, February
2002.
[6] IEEE 802.1d-1998, Part 3: Media Access Control (MAC) bridges,
ANSI/IEEE Std. 802.1D, 1998 edition, 1998.
[7] S. Choi, J.Prado, S. Shankar N, and S. Mangold, “IEEE 802.11e
Contention-Based Channel Access (EDCF) Performance Evaluation,”
in Proc. IEEE ICC’03, Anchorage, Alaska, USA, May 2003.
[8] ITU-T Recommendation H.261: Video codec for audiovisual
services at 64 kb/s. (1993).
[9] ISO/IEC JTC1/SC29/WG11: MPEG4 coding of audio visual
objects: visual. (1998).
[10] S. Mangold, S. Choi, "Analysis of IEEE 802.11e for QoS Support
in Wireless LANs," IEEE Wireless Communications, Dec 2003.
[11] D. Qiao, S. Choi, and K. G. Shin, "Goodput Analysis and Link
Adaptation for IEEE 802.11a Wireless LANs,” IEEE Trans. on Mobile
Computing (TMC), vol. 1, no. 4, pp. 278-292, October-December 2002.
6
�








 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc