Chapter 17
�
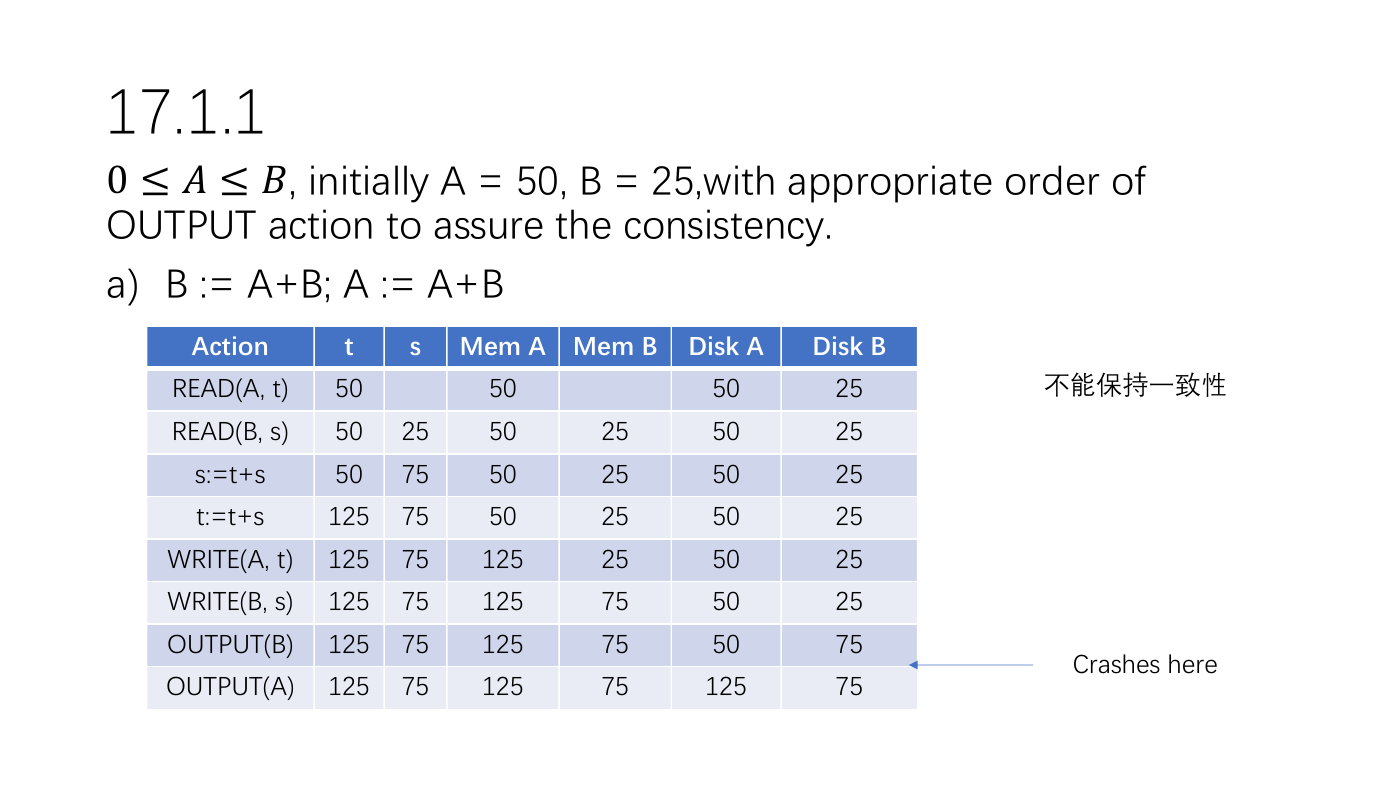
17.1.1
0≤≤, initially A = 50, B = 25,with appropriate order of
OUTPUT action to assure the consistency.
a) B := A+B; A := A+B
Action
READ(A, t)
READ(B, s)
s:=t+s
t:=t+s
WRITE(A, t)
WRITE(B, s)
OUTPUT(B)
OUTPUT(A)
t
50
50
50
125
125
125
125
125
s Mem A Mem B Disk A
Disk B
50
50
50
50
125
125
125
125
25
75
75
75
75
75
75
50
50
50
50
50
50
50
125
25
25
25
25
75
75
75
25
25
25
25
25
25
75
75
不能保持一致性
Crashes here
�
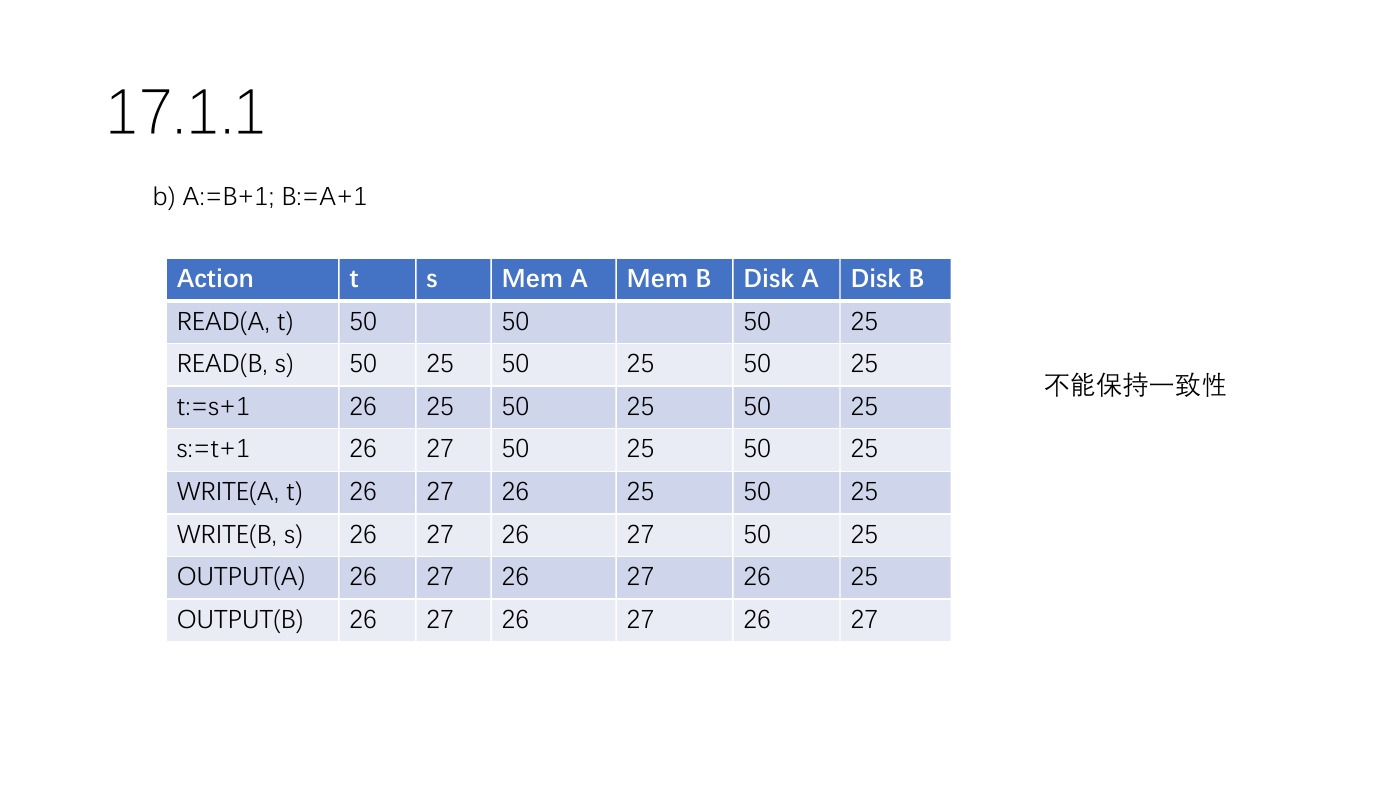
17.1.1
b) A:=B+1; B:=A+1
Action
READ(A, t)
READ(B, s)
t:=s+1
s:=t+1
WRITE(A, t)
WRITE(B, s)
OUTPUT(A)
OUTPUT(B)
t
50
50
26
26
26
26
26
26
s
25
25
27
27
27
27
27
Mem A Mem B Disk A Disk B
50
50
50
50
26
26
26
26
50
50
50
50
50
50
26
26
25
25
25
25
27
27
27
25
25
25
25
25
25
25
27
不能保持一致性
�
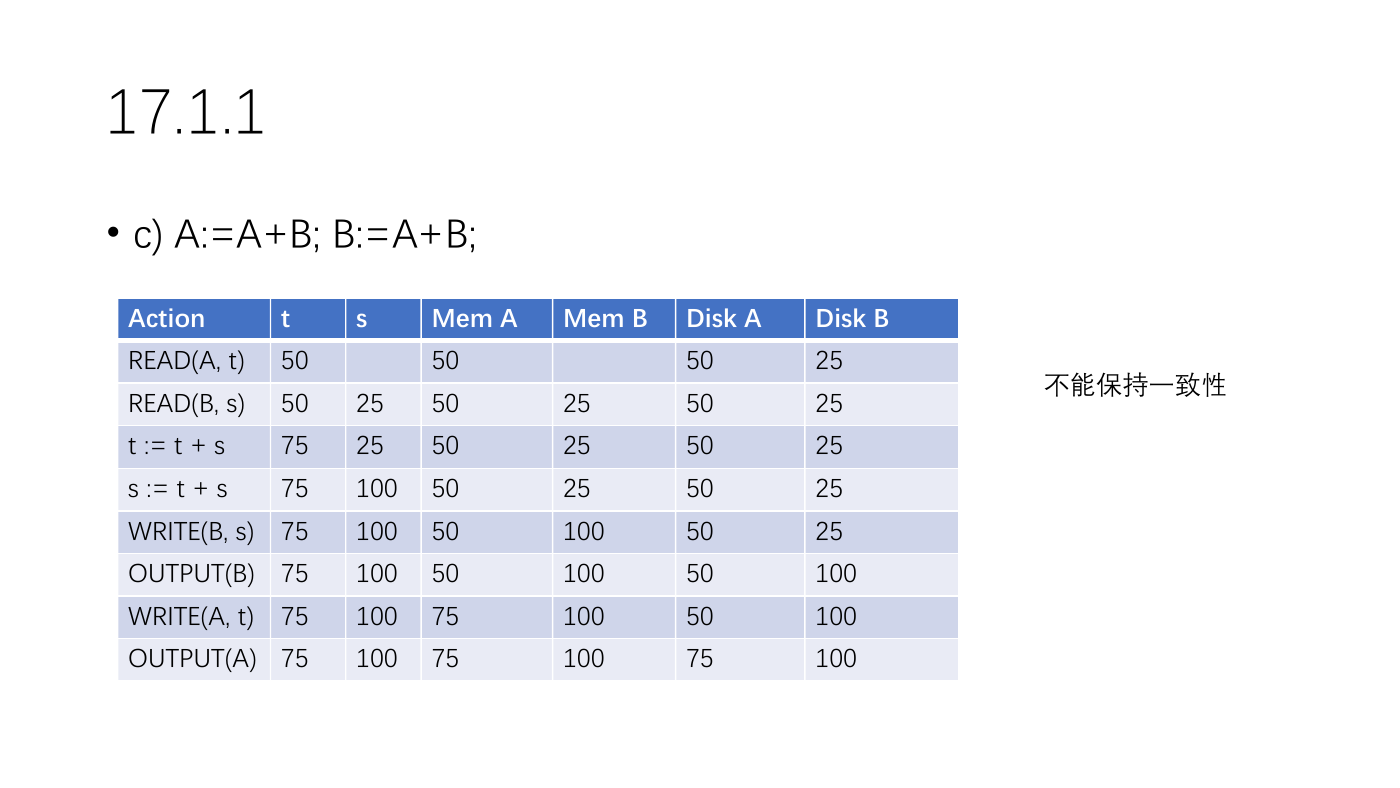
17.1.1
• c) A:=A+B; B:=A+B;
t
Action
50
READ(A, t)
50
READ(B, s)
75
t := t + s
s := t + s
75
WRITE(B, s) 75
OUTPUT(B) 75
WRITE(A, t) 75
OUTPUT(A) 75
s
25
25
100
100
100
100
100
Mem A Mem B
50
50
50
50
50
50
75
75
25
25
25
100
100
100
100
Disk A
50
50
50
50
50
50
50
75
Disk B
25
25
25
25
25
100
100
100
不能保持一致性
�
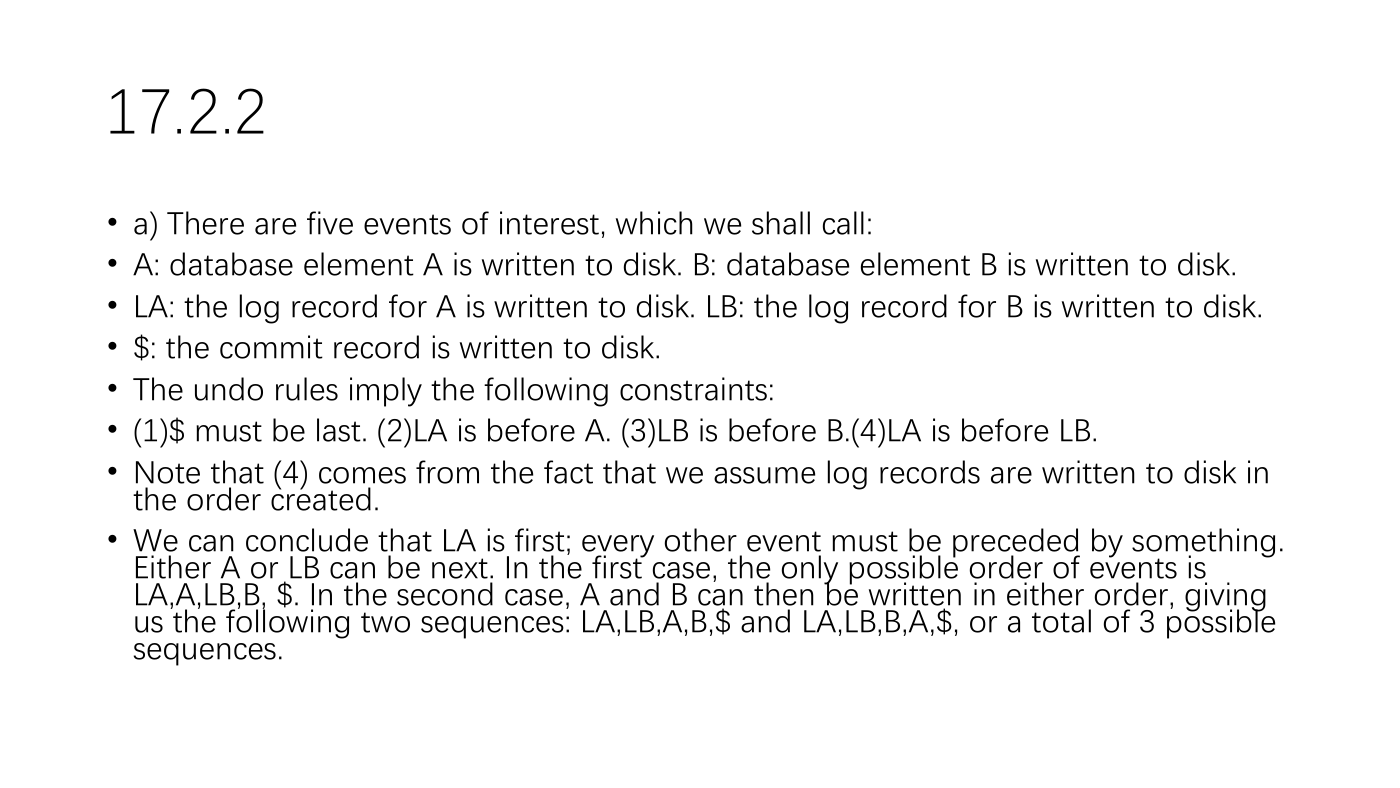
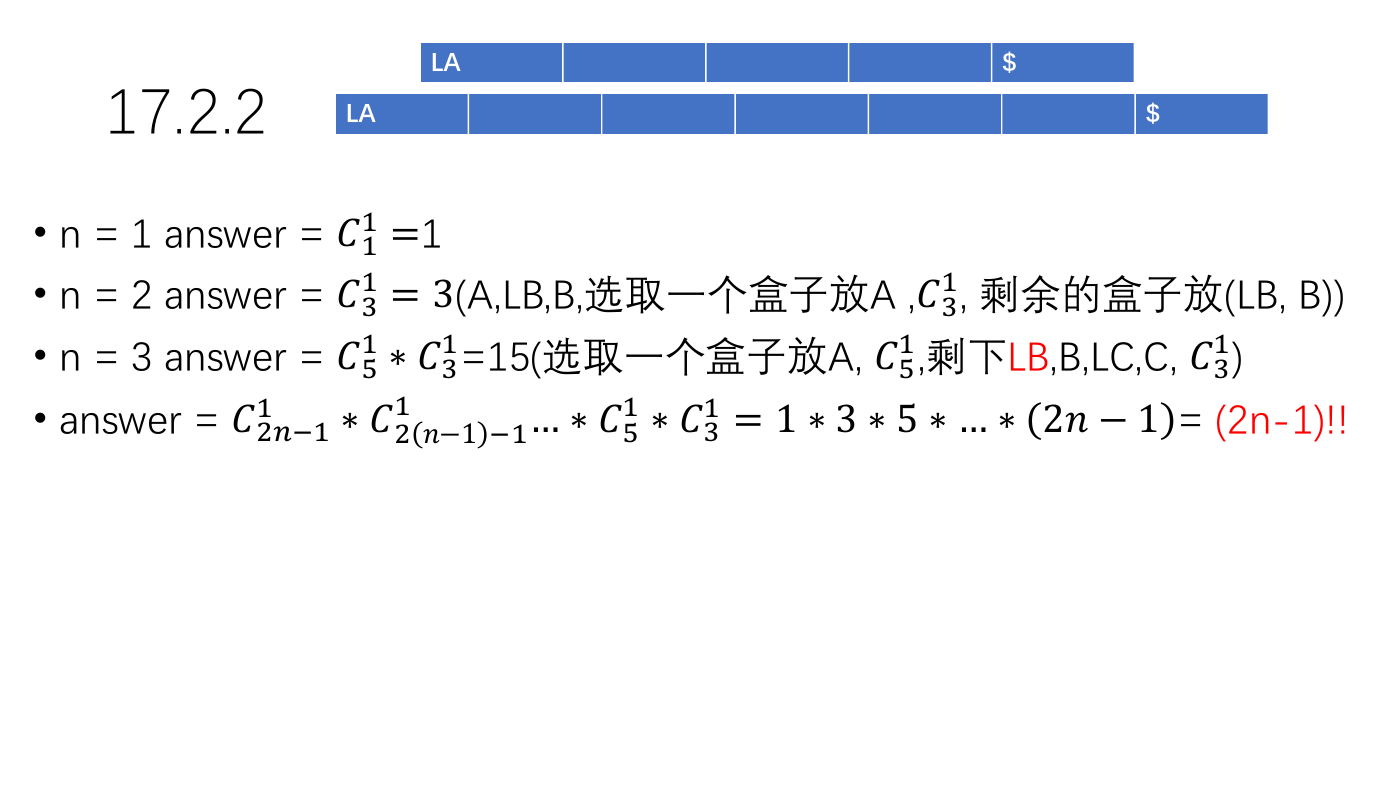
17.2.2
• a) There are five events of interest, which we shall call:
• A: database element A is written to disk. B: database element B is written to disk.
• LA: the log record for A is written to disk. LB: the log record for B is written to disk.
• $: the commit record is written to disk.
• The undo rules imply the following constraints:
• (1)$ must be last. (2)LA is before A. (3)LB is before B.(4)LA is before LB.
• Note that (4) comes from the fact that we assume log records are written to disk in
the order created.
• We can conclude that LA is first; every other event must be preceded by something.
Either A or LB can be next. In the first case, the only possible order of events is
LA,A,LB,B, $. In the second case, A and B can then be written in either order, giving
us the following two sequences: LA,LB,A,B,$ and LA,LB,B,A,$, or a total of 3 possible
sequences.
�
17.2.2
LA
LA
$
$
• n = 1 answer = 11=1
• n = 2 answer = 31=3(A,LB,B,选取一个盒子放A ,31, 剩余的盒子放(LB, B))
• n = 3 answer = 51∗31=15(选取一个盒子放A, 51,剩下LB,B,LC,C, 31)
…∗51∗31=1∗3∗5∗…∗ 2−1 = (2n-1)!!
∗2 −1 −1
• answer = 2−1
1
1
�
i.
ii.
At what points could the record written?
For each possible crash point, how far back in the log we must
look to find all possible incomplete transactions. Consider both
the case that the record was or was not written
prior to the crash.
(a).
i.
ii.
The can occur anywhere after /
The only active transaction when the checkpoint began was
S. If the crash occurs after the END CKPT, then we need
only go back as far as the . However, if the
crash occurs before the checkpoint ended, go back to
(undo s)
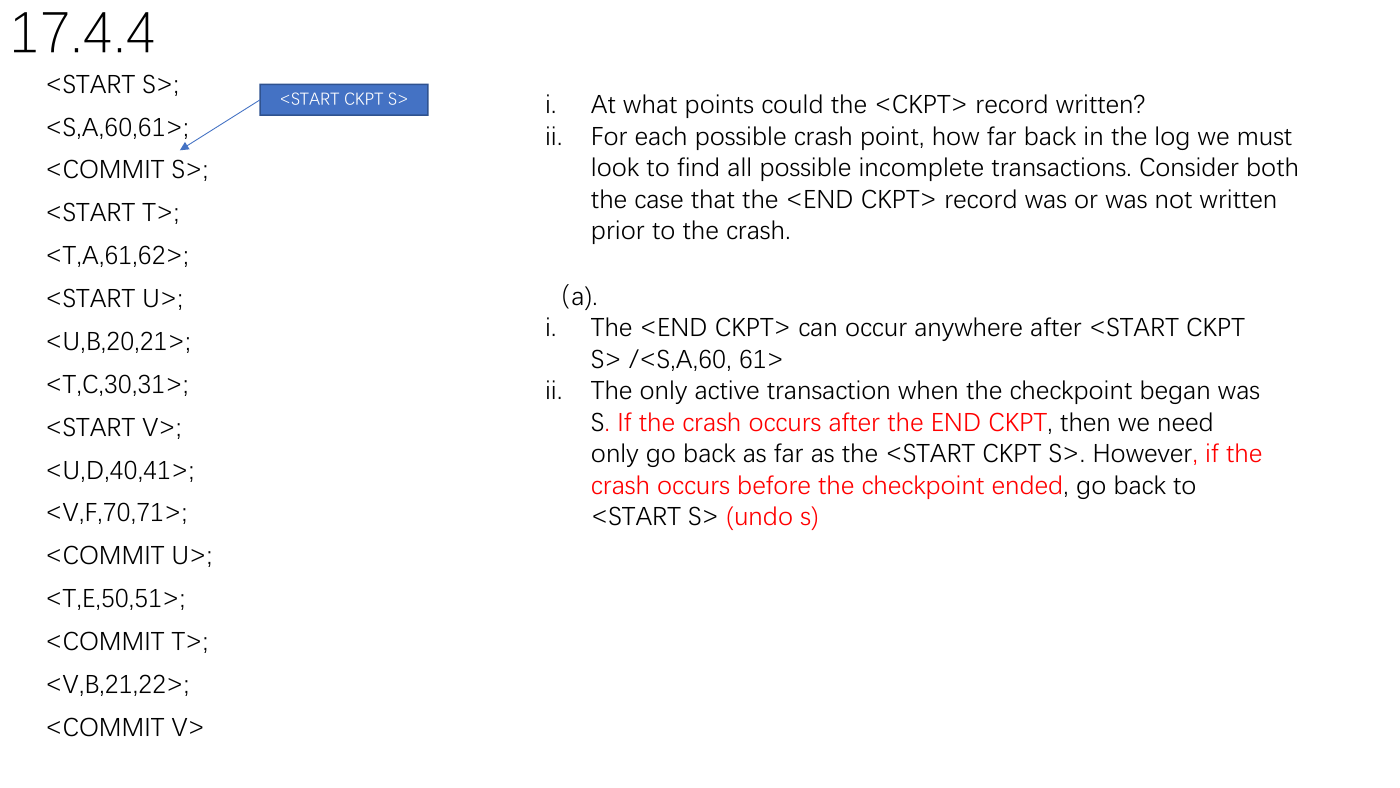
17.4.4
;
;
;
;
;
;
;
;
;
;
;
;
;
;
;
�
17.4.4
;
;
;
;
;
;
;
;
;
;
;
;
;
;
;
b)
i.
ii.
The END CKPT record could appear anywhere
after the record .
The only active transaction when the
checkpoint began was T.
If the crash occurs after the END CKPT,
go back as far as the .
if the crash occurs before the checkpoint ended,
then any transaction that was active when the
previous checkpoint ended may have written
some but not all of its data to disk. In this case, the
only other transaction that could qualify is S, so we
must look back to the beginning of S, i.e., to the
beginning of the log in this simple example
(undo S)
�










 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc