Computer Communications 31 (2008) 4089–4097
Contents lists available at ScienceDirect
Computer Communications
j o u r n a l h o m e p a g e : w w w . e l s e v i e r . c o m / l o c a t e / c o m c o m
Distributed power control and random access for spectrum sharing
with QoS constraint q
Bo Yang a,b,*, Yanyan Shen b, Gang Feng a, Chengnian Long b, Zhong-Ping Jiang d, Xinping Guan b,c
a Department of Manufacturing Engineering and Engineering Management, City University of Hong Kong, Hong Kong SAR, PR China
b Center for Networking Control and Bioinformatics, The Institute of Electrical Engineering, Yanshan University, Qinhuangdao 066004, PR China
c Department of Automation, School of Electronic, Information, and Electrical Engineering, Shanghai Jiaotong University, Shanghai 200240, PR China
d Department of Electrical and Computer Engineering, Polytechnic Institute of New York University, Brooklyn, NY 11201, USA
a r t i c l e
i n f o
a b s t r a c t
Article history:
Received 24 December 2007
Received in revised form 20 August 2008
Accepted 20 August 2008
Available online 29 August 2008
Keywords:
Wireless communication
Spectrum sharing
Dynamic spectrum access
Constrained optimization
1. Introduction
Distributed spectrum sharing with minimum quality of service (QoS) requirement and interference tem-
perature (IT) constraint is studied in this paper. This problem can be formulated as a non-convex optimi-
zation problem with conflicting constraints. To make solutions to this problem feasible, random access
and power control are jointly considered. The challenges in solving this problem arise from the coupling
in utility functions, the conflicting constraint sets, and coupled control variables. Moreover, there is no
centralized controller or base station in networks to coordinate unlicensed users’ transmission and pro-
tect active users’ QoS under IT constraint. By introducing variable substitution and transformation, we
derive a distributed random access and power control algorithm that can achieve global optimal solution
to the original problem. Convergence of the algorithm is proven theoretically. Simulation results demon-
strate that both QoS guarantee and interference avoidance can be achieved even with channel gain
variations.
Ó 2008 Elsevier B.V. All rights reserved.
The frequency spectrum for radio signal transmission is cur-
rently allocated in a static manner, where bands are licensed to
users by government agencies and thus licensed users have the
exclusive rights to access the allocated band. At the same time,
studies show that the spectrum has been used inefficiently in li-
censed bands [1]. In contrast, the spectrum left by licensed users
cannot meet the increasing demands for radio resources. To solve
this demand and utilization dilemma, dynamic spectrum sharing
approaches appear to be a good alternative. One of the approaches,
called the underlay sharing approach exploits the spread spectrum
techniques in cellular networks. Once a spectrum allocation map
has been acquired, unlicensed devices can coexist with licensed
users on the same frequency, provided that unlicensed users can
limit the interference to licensed users. To quantify the interfer-
q This work was supported in part by the Research Grants Council of Hong Kong
SAR, P.R. China, under Grant Cityu 112907, the China National Outstanding Youth
Foundation under Grant 60525303, NSFC under Grant 60604012, 60804030. This
material was also based upon work supported by the National Science Foundation
under Grant OISE-0430145. Part of this work was accomplished when the first
author was visiting the Polytechnic Institute of New York University under a WICAT
Fellowship.
* Corresponding author. Tel.: +852 2784 4601.
E-mail addresses: bo.yang@ieee.org (B. Yang), megfeng@cityu.edu.hk (G. Feng),
dylcn@ysu.edu.cn (C. Long), zjiang@control.poly.edu, zjiang@poly.edu (Z.-P. Jiang),
xpguan@ysu.edu.cn (X. Guan).
0140-3664/$ - see front matter Ó 2008 Elsevier B.V. All rights reserved.
doi:10.1016/j.comcom.2008.08.016
ence, the Federal Communication Commission (FCC) proposed a
new metric named the interference temperature (IT) [2]. The IT
is defined to be the radio frequency power measured at a receiving
antenna per unit bandwidth.
In this paper, we focus on the underlay spectrum sharing in ad
hoc networks where all unlicensed users spread their transmission
powers across the entire available band under the IT constraint. In
this context, power control is used to limit interference among
unlicensed users and to licensed receivers and, hence, maximize
spectrum usage. The signal-to-interference-and-noise ratio (SINR)
at the unlicensed receiver determines the successful transmission
at physical layer. However, to satisfy the minimum SINR require-
ment that characterizes the quality of service (QoS) constraint on
the bit-error rate at individual receivers, the transmitting power
of an unlicensed user may exceed its maximum value or even vio-
lates the IT constraint. To balance the minimum SINR requirement
and IT constraint, and further to efficiently and fairly utilize spec-
trum, transmission power and channel access must be determined
by coordination among unlicensed users [3]. In ad hoc networks
without infrastructure, this coordination should be implemented
distributively.
Taking these factors into consideration, we formulate a joint
random access and power control problem under IT and QoS con-
straints. To protect the primary transmission, some nodes called
measurement points are deployed to monitor the real-time IT of
the concerned band at their locations. Due to the interference rela-
tionship among wireless links and coupling between transmission
�
4090
B. Yang et al. / Computer Communications 31 (2008) 4089–4097
power and channel access, the formulated problem is non-convex
and non-separable in control variables. After variable transforma-
tion and introduction of an auxiliary variable, the optimization
problem can be turned into a convex one. Then a distributed ran-
dom access and power control algorithm is proposed within the
framework of layering as optimization decomposition [4]. The
transmission power of a link is updated not only to maintain its
own QoS but also to limit interference to peer unlicensed users
as well as licensed users. The random access of a transmission is
aimed at satisfying its own channel access requirement and sup-
porting other active links’ QoS requirement. The only involvement
of a measurement point in the implementation of this algorithm is
that when the aggregate IT violates the given upper bound the
measurement point will broadcast the current IT to all the unli-
censed transmitters. Furthermore, we prove that the proposed
algorithm can converge to the global optimum. Simulation demon-
strates that convergence of this algorithm can be ensured even
with channel gain variations.
The rest of this paper is organized as follows. In Section 2, we
review some related work on spectrum sharing and non-convex
optimization. The system model is presented in Section 3. The
spectrum sharing problem is formulated in Section 4. In Section
5, we propose our joint random access and power control algo-
rithm for spectrum sharing. Convergence results of the algorithm
are also given in Section 5. Section 6 includes performance evalu-
ation of the proposed algorithms. We conclude the paper and give
future research direction in Section 7.
2. Related work
Spectrum sharing between licensed users and unlicensed users
can be classified as overlay and underlay schemes. In the overlay
spectrum sharing unlicensed users access the network dynamically
by using a portion of spectrum that has not been used by licensed
users. For more discussions on the overlay spectrum sharing, see
[5,2]. We focus on the underlay spectrum sharing, especially the
scheme based on IT model. In [6], Huang et al. proposed the uplink
spectrum sharing algorithm based on auction theory. They charac-
terized the selfishness of unlicensed users without considering the
maximum transmission power and QoS constraints of individual
users. The base station, which is co-located with IT measurement
point, allocates the uplink transmission powers proportionally to
unlicensed users’ bids. Wang et al. [7] investigated the individual
users’ throughput maximization under IT constraint. To penalize
the individual users’ selfishness, they relied on the pricing scheme
in [8] to limit strong interference in power control. However, the
pricing scheme with the participation of a centralized base station
(BS) cannot be implemented in ad hoc networks. It is noted that all
these literatures consider how to utilize spectrum without QoS
constraint. Xing et al. [3] formulated the spectrum sharing under
IT and QoS constraint as a geometric programming problem in cel-
lular networks. To make it possible for each active user to maintain
minimum QoS requirement under IT constraint, some active unli-
censed links will be switched off temporarily by solving a central-
ized operator problem at BS. To mitigate the implementation
overhead, a learning automata algorithm is proposed in [3] and
BS needs to collect each unlicensed links’ SINR and aggregate IT
for updating uplink access probability. A non-cooperative power
control game with IT constraint was formulated by Jia and Zhang
in [9] for ad hoc networks, where the IT measurement point in-
forms the unlicensed link that generates the maximum received
power to back off when current measured IT exceeds the given
upper bound. However, the back-off scheme in [9] did not take into
account QoS requirement of unlicensed users.
The key difference between those works mentioned and ours is
that this paper studies a distributed spectrum sharing scheme to
satisfy the minimum QoS and IT constraints simultaneously in ad
hoc networks. Similar log transformation approach was proposed
in [10] to derive power control in cellular networks by solving a
non-convex optimization problem satisfying QoS constraints. In
our formulation, there is also the coupling between different kinds
of control variables, i.e., transmission power and channel access
probability. This coupling together with coupled utility and con-
straint sets have to be tackled when searching for an efficient algo-
rithm which can be easily implemented.
3. System model
The wireless network considered here is formulated as a set L
of radio links with each link corresponding to an unlicensed trans-
mitter and a receiver. Each transmitter is assumed to have a fixed
channel gain to its intended receiver as well as fixed gains to all
other receivers in the network. The quality of each link is deter-
mined by the SINR at the intended receiver. In a network with
j L j interfering links we denote the SINR for the ith user as
ci ¼
P
Giipi
j–i;j2LGijpjÞ=S ;
g2 þ ð
where Gij > 0 is the channel gain from the transmitter of the jth link
to the receiver of the ith link, pi is the power of the ith transmitter,
g2 is the background noise power that is assumed to be the same for
all users, and S is the normalized spreading sequence.
The IT is a measurement of the power and bandwidth occupied
by interference. Interference temperature TI is specified in Kelvin
and is defined as [11]
;
kB
TIðfc; BÞ ¼ PIðfc; BÞ
where PIðfc; BÞ is the average interference power in Watts centered at
fc; covering bandwidth B measured in Hertz. Boltzmann’s constant k is
1:38 � 10�23 J/K [11]. For a given bandwidth, FCC imposes an IT limit
to restrict the interference to licensed receiver at a given frequency in
a particular location. In this paper, we assume that there are measur-
ing points monitoring the real-time IT at particular band in their loca-
tions. Thus, if the aggregate IT at measurement points is lower than a
given threshold, the protection to the licensed receiver can be
achieved. Then the constraint that the total received power does
not exceed that threshold at a measurement point is given by
ð1Þ
i¼1
where G0i is the channel gain from user i0s transmitter to the measure-
ment point, and T > 0 is a pre-defined threshold. The model (1) con-
siders that only a single measurement point is deployed. Under the
scenario that multiple measurement points are deployed, all IT con-
straints should be satisfied simultaneously. Our method proposed la-
ter can be extended to the multiple measurement points case.
XjLj
piG0i 6 T;
4. Problem formulation
The demand for QoS from unlicensed transmission is denoted
by a utility of SINR, ulðclÞ; 8l; where ulð�Þ is a twice differentiable,
increasing function of cl: The minimum QoS requirement of link l
is cl0: The social utility maximization problem with QoS and IT con-
straints can be formulated as follows:
P
PjLj
i¼1
l2L
ulðclÞ
maxp2P
subject to cl P cl0 8l;
piG0i 6 T;
ðP1Þ
�
B. Yang et al. / Computer Communications 31 (2008) 4089–4097
4091
l
where P ¼ fpl; l 2 L j 0 6 pl 6 pmax
g: To introduce the criterion of
finding a feasible solution �p 2 P that solves (P1), a normalized link
(
gain matrix �G is defined as
�Gjl ¼ cl0
0
for l–j;
for l ¼ j:
Gjl=S
Gll
"
The normalized noise vector is
#
n ¼ c10g2
G11
c20g2
G22
;
; . . . ;
cjLj0g2
GjLjjLj
T
;
and
g ¼ ½G01; . . . ; G0jLjT; pmax ¼ ½pmax
With the similar analysis as in [3], the criterion of finding a feasible
solution �p 2 P that solves (P1) is given as qð�GÞ < 1, ðI � �GÞ�1
n � pmax; and ððI � �GÞ�1nÞTg 6 T:
; . . . ; pmax
jLj T:
1
However, the feasible solution to (P1) may not exist given a set
of active links. One alternative method is to let some transmission
pairs be switched off temporarily to support other active links’ QoS
requirement (minimum SINR) under IT constraint (1) as in [3]. If
the lth link is active, its SINR cl is given by
cl ¼
P
Gllpl
j–lGljpjrjÞ=S ;
ð2Þ
g2 þ ð
�
where rj is an indicator variable defined as
rj ¼ 1;
jth link is active;
0; otherwise:
ð3Þ
Given the expression of SINR in (2), problem (P1) turns into
Due to the fact that rl; 8l are binary values, it is difficult to design
distributed algorithm solving (P1)0 efficiently.
Thus, we relax the binary valued constraint on the variable rj in
(3) and replace the discrete variable rj 2 f0; 1g by a continuous
variable qj 2 ½0; 1: The variable qj can be thought of as the proba-
bility of the transmitter of the jth link being active in a transmis-
sion slot. Thus, by the relaxation on the binary valued variable
rj; the problem of joint power control and scheduling is trans-
formed into one of power controlled random access, where the
objective is to determine for each link the probability of transmis-
sion and the transmission power in order to share the spectrum
efficiently and fairly with the minimum SINR and IT constraints.
We now express the problem of power controlled random access
as a constrained optimization problem
ðulð�clÞ þ xvlðqlÞÞ
max
p2P;q2Q
subject to �cl P cl0 8l 2 L;
P
P
ðP2Þ
l2L
plqlG0l 6 T;
l2L
where P ¼ fpl; l 2 L j 0 6 pl 6 pmax
x > 0 is a constant. We use the average SINR
l
g; Q ¼ fql; l 2 L j 0 6 ql 6 1g;
�
P
�
�cl ¼
g2 þ
Gllpl
j–lGljpjqj
=S
to quantify the QoS. The second item vlðqlÞ in the objective function
is an increasing, differentiable, and concave function of ql; which
max
p 2 P
r 2 f0; 1g
subject to
ðP1Þ0
P
l2L
ulðclÞ
PjLj
cl P cl0 8l;
plG0lrl 6 T:
l¼1
captures the delay requirement for the lth link. xvlðqlÞ also serves
as a regulation term that enables (P2) to be transformed into a con-
vex optimization problem shown later. The minimum acceptable
SINR criterion for error free packet reception is now replaced by a
minimum expected SINR criterion, i.e., �cl P cl0 8l 2 L:
In general, problem (P2) is non-convex and non-separable, thus
extremely difficult to solve distributively for the global optimum.
We show next that under a readily verifiable sufficient condition
on curvatures of the utility functions, the problem (P2) can be
turned into a convex and separable optimization problem.
5. Distributed algorithm design via layered decomposition
method
5.1. Equivalent convex formulation
First, we give the following notations. Let yl ¼ �cl and logarithmic
change of variables: ^ql ¼ log ql; ^pl ¼ log pl 8l. Correspondingly, the
domains of these variables by excluding the boundary region can
g; ^Q ¼ f:^ql; l 2 L j
be denoted as ^P ¼ f^pl; l 2 L j �M 6 ^pl 6 log pmax
P
�M 6 ^ql 6 0g; ^Y ¼ f^yl; l 2 L j �M 6 ^yl 6 log ymax
g; where M is a
6 pmax
l Gll=g2: Let
sufficiently large positive constant. Note that ymax
^ulð^ylÞ ¼ ulðe^ylÞ; ^vlð^qlÞ ¼ vlðe^qlÞ; ^Ilð^p�l; ^q�lÞ ¼ g2 þ
j–leðlog Glj=Sþ^pjþ^qjÞ
and rewrite the constraint sets in (P2) with respect to the logarithmic
change of variables as follows:
l
l
l
ð
ð
ð
^Cl ^yl; ^p; ^q�l
^Dl ^p; ^q�l
^El ^p; ^qð
Þ ¼ ^yl þ log ^Il ^p�l; ^q�l
Þ ¼ log cl0 þ log ^Il ^p�l; ^q�l
Þ ¼ log
G0le^plþ^ql
X
!
ð
� log T 6 0:
Þ � ^pl � log Gll 6 0;
Þ � ^pl � log Gll 6 0;
l
ð4Þ
ð5Þ
ð6Þ
Using geometric programming [12] and variable substitute tech-
nique, we can convert the optimization problem (P2) into a convex
programming problem (P3)
ð
^ul ^ylð Þ þ xvl ^qlð
P
Þ
Þ
ðP3Þ
max
subject to ð4Þ—ð6Þ
l2L
:
The main result is given in the following Theorem.
Theorem 1. Given that �v00
lðylÞ=yl for
all l 2 L; the non-convex programming problem (P2) can be equiv-
alently converted to the convex programming problem (P3).
lðqlÞ=ql; �u00
l ðylÞ P u0
l ðqlÞ P v0
Proof. Without loss of generality, we can replace the equality
yl ¼ �cl for all l; by an inequality in the constraint (4) and rewrite
lulðylÞ: We also rewrite
one of the objective functions
the constraints in (P2) with standard geometric programming form
P
lulð�clÞ as
P
P
ðP3Þ0
l2L
max
subject to yl � Il p�l; q�l
ðulðylÞ þ xvlðqlÞÞ
ð
Þ Gllpl
ð
P
6 1;
cl0�c�1
T�1
G0lqlpl 6 1:
l
l2L
Þ�1 6 1;
ð7Þ
Note that the first inequality in (7) will always be achieved with an
equality at the optimum. The next step of this problem reformula-
tion is to take log of both sides of the constraint in (7) and a log
change of variables: ^yl ¼ log yl; ^ulð^ylÞ ¼ ulðe^ylÞ; ^vlð^qlÞ ¼ vlðe^qlÞ;
^ql ¼ log ql; ^pl ¼ log pl 8l 2 L: This reformulation turns the problem
(P3)0 into (P3). Based on the constraints for the curvatures of ulð�Þ;
vlð�Þ in Theorem 1, it is easy to verify that the utility functions
^ulð^ylÞ, ^vlð^qlÞ are concave with respect to ^yl and ^ql [13]. To show prob-
P
P
lem (P3) is a convex programming problem, one only needs to prove
the convexity of constraints set in (4)–(6). We can see that
l2LG0le^qlþ^plÞ are, respectively, convex
j–lGlje^qjþ^pj =S þ g2Þ; logð
logð
�
4092
B. Yang et al. / Computer Communications 31 (2008) 4089–4097
with respect to q; p due to the convexity of log of a sum of exponen-
tial of linear functions [14]. h
5.2. Primal-dual decomposition
In this section, we present a primal-dual decomposition method
to solve the convex programming problem (P3). Consider the dual
to the primal problem (P3)
min
k�0;l�0
Dðk; lÞ
ð8Þ
with partial dual function
Dðk; lÞ ¼ max
~P;
^y2 ^Y;^q2^Q;^p2 ^P
ð9Þ
Since the function Gð^y; kÞ ¼
P
lð^ulð^ylÞ � kl^ylÞ is concave with re-
spect to ^y; we can solve the subproblem in (10) by considering the
first-order necessary optimality condition oGð^y; kÞ=o^yl ¼ ^u0
lð^ylÞ � kl
¼ 0: The auxiliary variable is adjusted by
ylðt þ 1Þ ¼ e^u0�1
ðklðtÞÞ
h
i
:
l
ymax
l
e�M
We assume that there exists an optimal solution to the subproblem
(11). The detailed solution method is deferred to the next subsec-
tion. Now we come to solve the dual problem (8). Note that the dual
function Dðk; lÞ is not differentiable. Therefore, we cannot use the
usual gradient methods and we will instead solve the dual problem
using subgradient methods [15]. Let ð^y; ^p; ^qÞ be the associated opti-
mal solutions to the subproblems (10), (11), respectively. Note that
ð
D k
�
�
; l
D k; lð
�
l
P
�
l2L
X
�
�
�
^pl � k�
�
�
^ul ^ylð Þ � k�
X
l ^yl
�
l þ l�
k�
�
�
^pl � k�
�
Þ ¼ max
^y2 ^Y
l2L
X
�
þ max
^q2^Q;^p2 ^P
^ul ^ylð Þ � k�
X
�
l ^yl
l2L
X
þ
l þ l�
l þ l�
k�
l2L
Þ
^ul ^ylð Þ � kl^yl
ð
X
�
�
�
l2L
X
X
�
�
þ
^pl � kl þ ll
Þ kl � k�
þ
P
lkl ^Clð^yl; ^p; ^q�lÞ �
^Cl ^yl; ^p; ^q�l
kl þ ll
Þ ¼
l2L
l2L
l
l
l
log
log
l
l þ l�
X
log
j–l
X
j–l
^Dl ^p; ^q�l
ð
P
ð
D k
�; l�
ð
l2L
Þ P
Þ � D k; lð
P
lð^ulð^ylÞ þ x^vlð^qlÞÞ �
lll
where ~P ¼
^Dlð^p; ^q�lÞ:
Noting that we relax only the first and second constraints
in (P3) by introducing Lagrangian multipliers k; l; which are
also known as consistency price and link price, respectively.
(P3) and (8),
If
respectively, we have D� P ~P� with the weak duality theorem.
Since (P3) is a convex programming, there is no duality gap,
i.e., D� ¼ ~P�:
~P� and D� denote the optimal value of
The maximization in (9) can be decomposed into the following
two subproblems:
X
D1ðkÞ ¼ max
^y2 ^Y
l
D2 k; lð
Þ ¼ max
^q2^Q;^p2 ^P
s:t: ð6Þ
Þ
0
^ulð^ylÞ � kl^yl
ð
X
B@
�
kl þ ll
l
�
�
^pl � kl þ ll
�
log
þx^vl ^qlð
Þ
!
1
ð10Þ
CA
Gljpjqj=S þ g2
P
j–l
ð11Þ
Remark 1. With the dual decomposition method, the system
optimization problem (P3) can be decomposed by the auxiliary
variable into the maximization problem in (10), which maximizes
the corresponding SINR, and the resource allocation problem in
(11), which is used to determine the link’s access probability and
power level. These two subproblems interact through consistency
prices k and link prices l:
X
j–l
!
Gljpjqj=S þ g2
!
þ x^vl ^qlð
!
�
log Gll
!
l þ l�
l
�
Þ þ k�
�
l
l þ l�
�
log Gll
;
!
þ x^vl ^qlð
�
Þ þ k�
�
þ x^vl ^qlð
Þ þ kl þ ll
log Gll
;
Gljpjqj=S þ g2
!
�
�
Gljpjqj=S þ g2
Þ ll � l�
:
l
�
�
Thus, it is verified that ^C ¼ ð� ^Clð^yl; ^p; ^q�lÞ 8l 2 LÞ; ^D ¼ ð� ^Dlð^p;
^q�lÞ 8l 2 LÞ are the subgradient of dual function Dðk; lÞ at point k
and l; respectively [15]. By the subgradient method, we obtain the
following algorithm for price adjustment:
�
ð12Þ
klðt þ 1Þ ¼ klðtÞ þ aðtÞ ^Cl ^yl; ^p; ^q�l
Þ
þ
llðt þ 1Þ ¼ llðtÞ þ aðtÞ ^Dl ^p; ^q�l
ð13Þ
Þ
where t is the iteration number, aðtÞ is the positive scalar stepsize,
and ‘‘½�þ” denotes the projection onto the set Rþ of non-negative
real numbers.
�
ð
ð
þ
;
:
5.3. Joint random access and power control under interference
temperature constraint
In the following, we introduce the penalty function method to
solve the joint random access and power control problem (11).
We use a non-smooth penalty function method as follows:
max
^q2^Q;^p2 ^P
where
Þ;
W ^p; ^qð
(
X
�
W ^p; ^qð
Þ ¼
�
�
�
kl þ ll
^pl � kl þ ll
Þg � j max ^El ^p; ^qð
l2L
þx^vl ^qlð
�
ð14Þ
!
X
j–l
Þ; 0
log
Gljpjqj=S þ g2
and j is a positive penalty constant. Since the objective function of
problem (9) is concave, problem (14) is a convex optimization prob-
�
B. Yang et al. / Computer Communications 31 (2008) 4089–4097
4093
¼ kl þ ll �
lem with convex constraints which can be solved using a subgradi-
ent projection algorithm. It can be shown that
oW
o^pl
oW
o^ql
X
GklplðtÞqlðtÞmkðtÞ=S � j �plqlG0l
X
j2LpjqjG0j
GklplðtÞqlðtÞmkðtÞ=S � j �plqlG0l
j2LpjqjG0j
�
¼ xv0
�
P
P
ð15Þ
ð16Þ
l ^qlð
Þ �
k–l
k–l
;
;
8<
:
where
mkðtÞ ¼ kkðtÞ þ lkðtÞ
P
�ckðtÞ
GkkpkðtÞ ;
pjqjG0j 6 T;
0 if
j2L
� ¼
1 otherwise:
ð17Þ
ð18Þ
Then the subgradient projection algorithm that solves (14) is ob-
tained as follows. On each logical link l; transmission is decided to
take place with probability
"
"
(
�
log qlðtÞ þ bðtÞ
(
�
log plðtÞ þ bðtÞ
�����
�����
oW
o^ql
oW
o^pl
qlðt þ 1Þ ¼ exp
plðt þ 1Þ ¼ exp
)
#
)
#
1
:
ð19Þ
^p¼^pðtÞ;^q¼^qðtÞ
e�M
pmax
l
e�M
;
ð20Þ
^p¼^pðtÞ;^q¼^qðtÞ
The transmission power is updated by the transmitter of link l as
where bðtÞ is the step size.During each time slot, the following algo-
rithm is updated until convergence.
Algorithm 1.
1. At the transmitter of link l, 8l
the consistency price k is updated according to (12) and
the link price l is updated according to (13).
a message mlðtÞ (17) is broadcasted to all other transmit-
ters by a flooding protocol.
its transmission power plðtÞ and access probability qlðtÞ
are updated according to (20) and (19), respectively.
2. At the measurement point, it broadcasts the aggregate value
l2LpjqjG0j to all transmitters, if the aggregate IT violate the
the
on monitoring
keeps
it
upper-bound. Otherwise,
interference.
(a)
(b)
(c)
P
Remark 2. From the practical implementation point of view, the
P
complexity of Algorithm 1 comes from the message passing in
(15) and (16). The computations of (15) and (16) require the kth
link, 8k–l; to transmit
k–lGklplðtÞqlðtÞmkðtÞ=S to l. As the number
of transmitters increase, the convergence rate of Algorithm 1 will
become slower as shown in simulation part. One method to
decrease the complexity is to limit the message passing within a
small neighborhood of l [16], since the term (17) is multiplied by
Gkl; which is inverse proportional to the distance between the lth
transmitter and the kth receiver, 8k–l: Another method to decrease
the complexity of Algorithm 1 is to design non-cooperative ran-
dom access algorithm without message passing. Interested readers
are referred to [17].
Remark 3. Another limitation of Algorithm 1 is due to the mea-
surement of IT violation in (18). Using IT constraint as a protection
of primary transmission does not require the interaction between
primary and secondary transmissions. However, the IT measured
at the measurement point is different from that at primary receiv-
ers. We refer interested readers to [18] for more details on IT
measurement.
Theorem 2. Given small enough positive constants a; b and large
enough positive constant j; the distributed joint power control and
random access algorithm (12), (13), (19), (20) converges statistically
to the global optimum of problem (P2).
Proof. First we show that qðtÞ; pðtÞ are bounded with the subgra-
(20). Let wðtÞ ¼ ðqðtÞ; pðtÞÞ; W�ðk; lÞ ¼
dient algorithm (19),
ðq�ðk; lÞ; p�ðk; lÞÞ be the set of optimal solutions to (14) with a
given ðk; lÞ: We further define dðw; WÞ ¼ minw02Wkw � w0k and
NrðWÞ ¼ fw j dðw; Wðk; lÞÞ 6 rg: We have the following results
readily derived based on the convergence properties of subgradient
algorithm [19]. Let fwbðtÞg denote the sequence of vectors defined
by the iterative procedures stated in (19), (20) with bðtÞ ¼ b; 8t:
Then there exist a K < 1 and a function rðbÞ such that
limb!0þ rðbÞ ¼ 0; and for all j > K;
t!1 dðwðtÞ; NrðbÞðWÞÞ ¼ 0:
lim
Thus, qðtÞ; pðtÞ are bounded.
Next we show that the subgradient algorithms (12), (13) with
constant step size a converges statistically to the optimal value
ðk�; l�Þ of the dual function Dðk; lÞ: Recall that in (12), (13) the
following iterative procedures are updated:
!
#
^Il ^p�l; ^q�l
Þ
þ ^yl
^Il ^p�l; ^q�l
Þ
þ
;
!
#
ð21Þ
ð22Þ
þ
:
l
l
Þ
ð
�
Gllpl
X
"
"
Gllpl
ð
ð
ll t þ 1
klðt þ 1Þ ¼ klðtÞ þ a log
Þ ¼ llðtÞ þ a log
�
klðtÞ � k�
klðtÞ þ a log
llðtÞ þ a log
X
Introduce the Lyapunov candidate
Þ ¼ 1
ð
V kðtÞ; lðtÞ
2a
X
ð
ð
V k t þ 1
Þ; lðt þ 1Þ
6 1
X
2a
þ 1
X
�
2a
klðtÞ � k�
X
(
þ a
X
�
2
llðtÞ � l�
X
þ ^yl
ð
!
^Il ^p�l; ^q�l
¼ 1
2a
Gllpl
ð
(
�
2 þ
Gllpl
log
log
�
�
þ
ð
Þ
ð
l
l
l
l
l
l
l
l
þ a
2
ð
^Il ^p�l; ^q�l
Gllpl
Þcl0
;
log
l
þ log c0l
X
�
!
l
2 þ 1
2a
llðtÞ � l�
l
�
2
;
!
!
2
^Il ^p�l; ^q�l
Þ
þ ^yl
� k�
l
^Il ^p�l; ^q�l
Þ
Gllpl
klðtÞ � k�
!
l
2
X
�
)
!
l
þ 1
2a
Þcl0
^Il ^p�l; ^q�l
Gllpl
2
þ log c0l
�
� l�
l
ð
^Il ^p�l; ^q�l
Þ
þ ^yl
log
Gllpl
llðtÞ � l�
l
!
2
!
)
�
2
ð23Þ
ð24Þ
ð25Þ
where the first inequality is due to ðmax½z; 0Þ2 6 z2: By the sub-gra-
!
)
dient property [15], we have
)
!
(
X
�
(
l � klðtÞ
k�
X
�
D kðtÞ; lðtÞ
ð
^Il ^p�l; ^q�l
Þ � D k
ð
þ ^yl
�; l�
Þ 6
log
�
�
ð
Þ
l � llðtÞ
l�
Gllpl
ð
log
^Il ^p�l; ^q�l
Gllpl
Þcl0
l2L
þ
l2L
Substitute the above into (23)–(25)
Vðt þ 1Þ 6 VðtÞ þ D k
ð
�; l�
Þ � D kðtÞ; lðtÞ
ð
Þ þ aY
2 ;
�
4094
2
whereX
4
!
2
þ log
!
3
5
2
^Ilð^p�l; ^q�lÞcl0
log
Gllpl
^Ilð^p�l; ^q�lÞ
Gllpl
þ ^yl
6 Y;
l2L
since ^y; ^p; ^q belong to compact set and ^p–0: Applying the inequal-
ity recursively, we have
V k t þ 1
ð
DðkðsÞ; lðsÞÞ � Dðk
X
�; l�Þ
ð
t
Þ þ atY
2
s¼1
Þ � D k
ð
�; l�
Þ
Þ
6 V kð1Þ; lð1Þ
Þ
ð
t
By Jensen’s inequality, we have
Þ; lðt þ 1Þ
ð
ð
Þ
6 V kð1Þ; lð1Þ
Þ �
andP
s¼1 D k sð Þ; lðsÞ
t
P
s¼1DðkðsÞ; lðsÞÞ
ð
ð
t
t
t
X
t
s¼1
where
�kðtÞ ¼ 1
t
kðsÞ;
P Dð�kðsÞ; �lðsÞÞ;
X
�lðtÞ ¼ 1
t
t
s¼1
lðsÞ;
þ aY
2 :
b
y
t
i
l
i
b
a
b
o
r
p
s
s
e
c
c
A
since DðkðsÞ; lðsÞÞ is a convex function with respect to k; l: Further.
�
we have
�
D �k; �l
Taking limits as t ! 1; yields
� D� 6 Vð1Þ
�
�
þ aY
2 :
�
�
t
lim sup
t!1
D �k; �l
� D� 6 aY
2 :
Thus according to the definition of statistical stability in [20], the
subgradient algorithm (12), (13) converges statistically to within
aY=2 of the optimal value ðk
�; l�Þ: Then, given small enough positive
constants a; b and large enough positive constant j; the distributed
algorithms (12), (13), (19), (20) converge statistically to the global
optimal solution to problem (P2). h
6. Simulation results
6.1. Simple network scenario
We first present a simple network topology to illustrate the ef-
fects of network parameters and control parameters on algorithm
performance. Consider an ad hoc network consisting of four trans-
mission pairs. The parameters are set as follows except otherwise
specified. The target SINR is c0 ¼ 12 and the background noise is
g2 ¼ 5 � 10�13. The low rate data users are considered with a
spreading gain of S ¼ 128: The IT bound is 4 � 10�8. The maximum
power for each transmission pair is 0.5 W. The channel gain matrix
is given as follows:
0:010
0:080
0:018 0:0901
0:050
0:020
0:005
0:036
0:003
0:122
0:100
0:297
0:0996 0:016
0:138
0:010
G ¼ 10�4 �
3
7775:
2
6664
ð26Þ
½
The path gain from four transmitters to the IT point is
G0 ¼ 10�7 � 2:3682 1:4784 1:8582 1:1909
ð27Þ
Using the criterion in Section 4, it can be checked that the social
optimization solution to (P1) is infeasible. Hence, we turn to the
proposed joint random access and power control algorithm. We
T:
B. Yang et al. / Computer Communications 31 (2008) 4089–4097
a
)
W
(
r
e
w
o
p
i
i
n
o
s
s
m
s
n
a
r
T
0.1
0.08
0.06
0.04
0.02
0
0
1
0.8
0.6
0.4
0.2
0
0
R
N
S
I
25
20
15
10
5
0
0
link pair 1
link pair 2
link pair 3
link pair 4
100
200
300
Iteration
400
500
link pair 1
link pair 2
link pair 3
link pair 4
500
100
200
300
Iteration
400
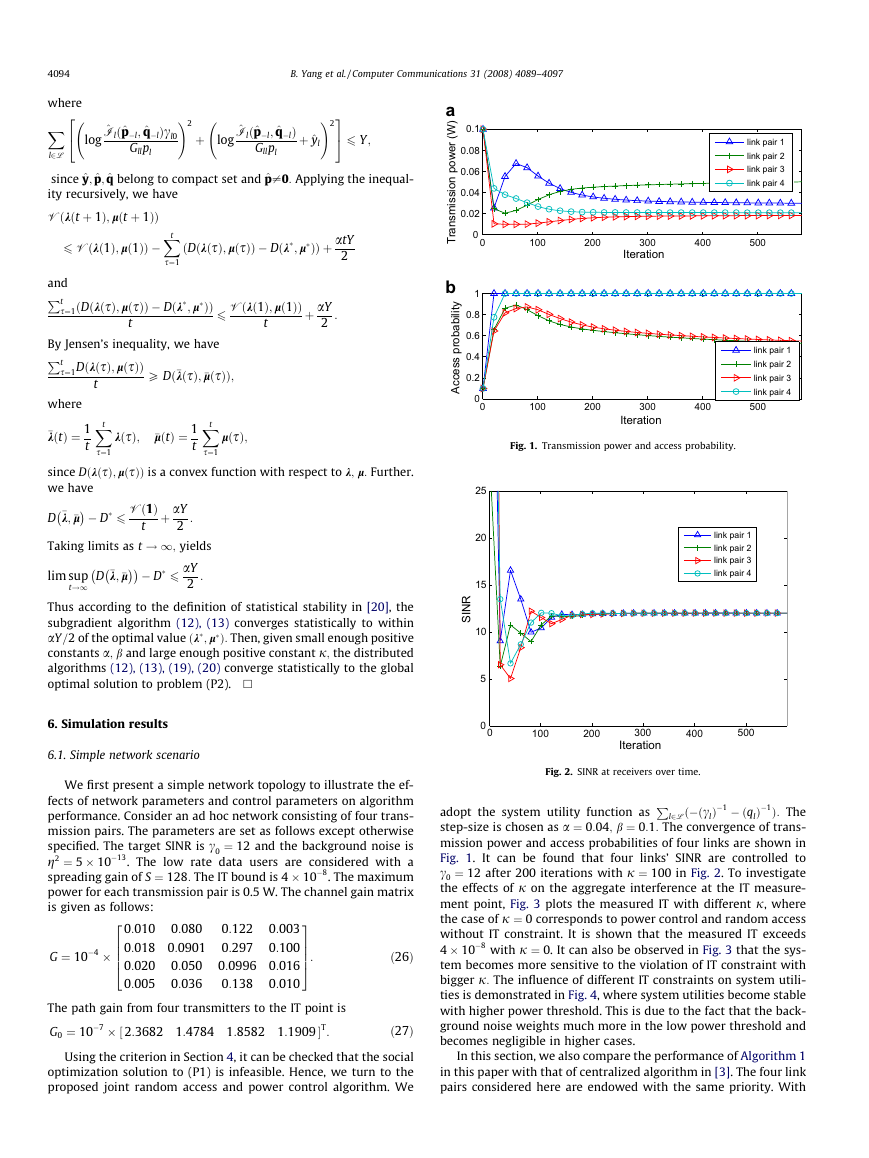
Fig. 1. Transmission power and access probability.
link pair 1
link pair 2
link pair 3
link pair 4
100
200
300
Iteration
400
500
Fig. 2. SINR at receivers over time.
P
l2Lð�ðclÞ�1 � ðqlÞ�1Þ: The
adopt the system utility function as
step-size is chosen as a ¼ 0:04; b ¼ 0:1: The convergence of trans-
mission power and access probabilities of four links are shown in
Fig. 1. It can be found that four links’ SINR are controlled to
c0 ¼ 12 after 200 iterations with j ¼ 100 in Fig. 2. To investigate
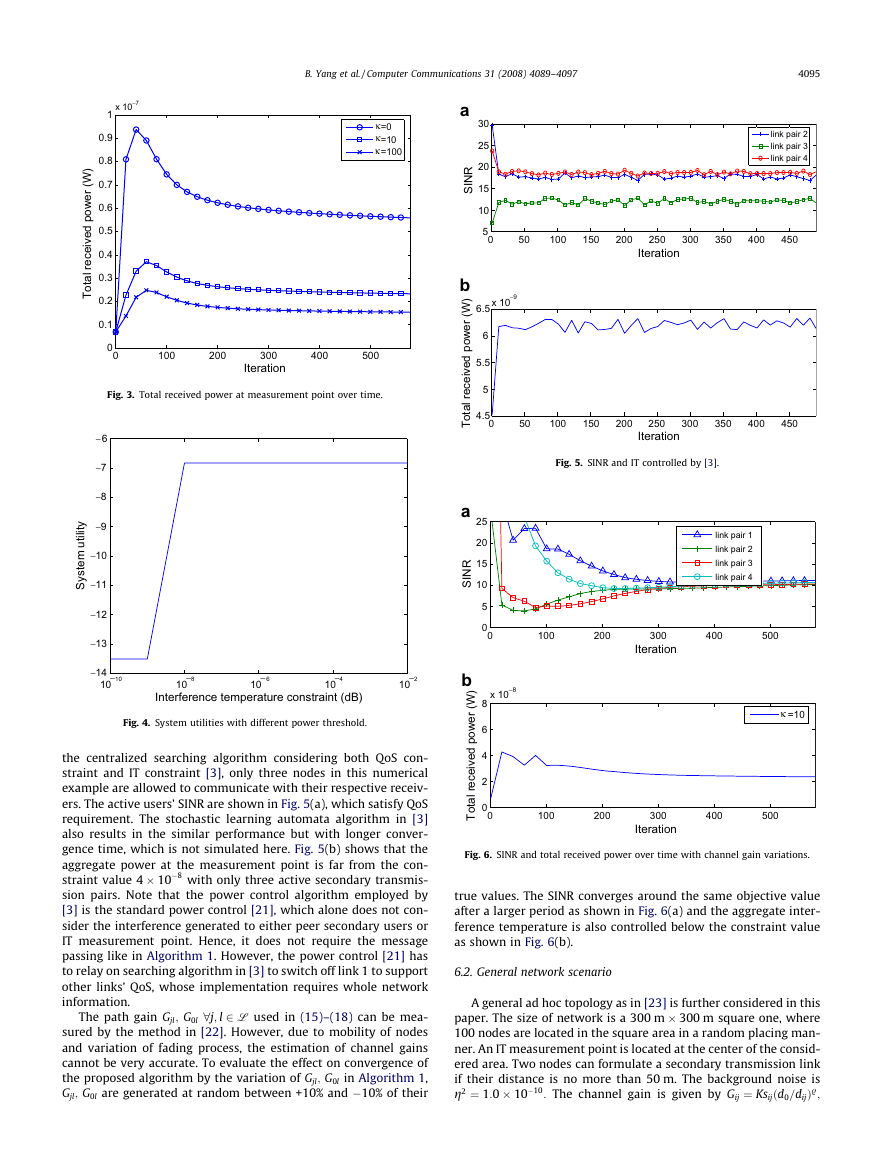
the effects of j on the aggregate interference at the IT measure-
ment point, Fig. 3 plots the measured IT with different j, where
the case of j ¼ 0 corresponds to power control and random access
without IT constraint. It is shown that the measured IT exceeds
4 � 10�8 with j ¼ 0. It can also be observed in Fig. 3 that the sys-
tem becomes more sensitive to the violation of IT constraint with
bigger j: The influence of different IT constraints on system utili-
ties is demonstrated in Fig. 4, where system utilities become stable
with higher power threshold. This is due to the fact that the back-
ground noise weights much more in the low power threshold and
becomes negligible in higher cases.
In this section, we also compare the performance of Algorithm 1
in this paper with that of centralized algorithm in [3]. The four link
pairs considered here are endowed with the same priority. With
�
B. Yang et al. / Computer Communications 31 (2008) 4089–4097
4095
1 x 10−7
0.9
)
W
(
r
e
w
o
p
d
e
v
e
c
e
r
l
a
t
o
T
i
0.8
0.7
0.6
0.5
0.4
0.3
0.2
0.1
0
0
κ=0
κ
=10
κ
=100
a
R
N
S
I
b
)
W
link pair 2
link pair 3
link pair 4
50
100
150
200
250
Iteration
300
350
400
450
30
25
20
15
10
5
0
x 10−9
6.5
6
5.5
5
4.5
0
50
100
150
200
250
Iteration
300
350
400
450
Fig. 5. SINR and IT controlled by [3].
(
r
e
w
o
p
d
e
v
e
c
e
r
l
a
o
T
t
i
a
R
N
S
I
25
20
15
10
5
0
0
link pair 1
link pair 2
link pair 3
link pair 4
100
200
300
Iteration
400
500
b
)
W
(
r
e
w
o
p
i
d
e
v
e
c
e
r
l
a
t
o
T
8
6
4
2
0
x 10−8
κ
=10
0
100
200
300
Iteration
400
500
Fig. 6. SINR and total received power over time with channel gain variations.
true values. The SINR converges around the same objective value
after a larger period as shown in Fig. 6(a) and the aggregate inter-
ference temperature is also controlled below the constraint value
as shown in Fig. 6(b).
6.2. General network scenario
A general ad hoc topology as in [23] is further considered in this
paper. The size of network is a 300 m � 300 m square one, where
100 nodes are located in the square area in a random placing man-
ner. An IT measurement point is located at the center of the consid-
ered area. Two nodes can formulate a secondary transmission link
if their distance is no more than 50 m. The background noise is
g2 ¼ 1:0 � 10�10: The channel gain is given by Gij ¼ Ksijðd0=dijÞ.;
100
200
300
Iteration
400
500
Fig. 3. Total received power at measurement point over time.
− 6
−7
−8
−9
−10
−11
−12
−13
y
t
i
l
i
t
u
m
e
t
s
y
S
−14
10
−10
−8
10
− 6
10
Interference temperature constraint (dB)
−4
10
−2
10
Fig. 4. System utilities with different power threshold.
the centralized searching algorithm considering both QoS con-
straint and IT constraint [3], only three nodes in this numerical
example are allowed to communicate with their respective receiv-
ers. The active users’ SINR are shown in Fig. 5(a), which satisfy QoS
requirement. The stochastic learning automata algorithm in [3]
also results in the similar performance but with longer conver-
gence time, which is not simulated here. Fig. 5(b) shows that the
aggregate power at the measurement point is far from the con-
straint value 4 � 10�8 with only three active secondary transmis-
sion pairs. Note that the power control algorithm employed by
[3] is the standard power control [21], which alone does not con-
sider the interference generated to either peer secondary users or
IT measurement point. Hence, it does not require the message
passing like in Algorithm 1. However, the power control [21] has
to relay on searching algorithm in [3] to switch off link 1 to support
other links’ QoS, whose implementation requires whole network
information.
The path gain Gjl; G0l 8j; l 2 L used in (15)–(18) can be mea-
sured by the method in [22]. However, due to mobility of nodes
and variation of fading process, the estimation of channel gains
cannot be very accurate. To evaluate the effect on convergence of
the proposed algorithm by the variation of Gjl; G0l in Algorithm 1,
Gjl; G0l are generated at random between +10% and �10% of their
�
4096
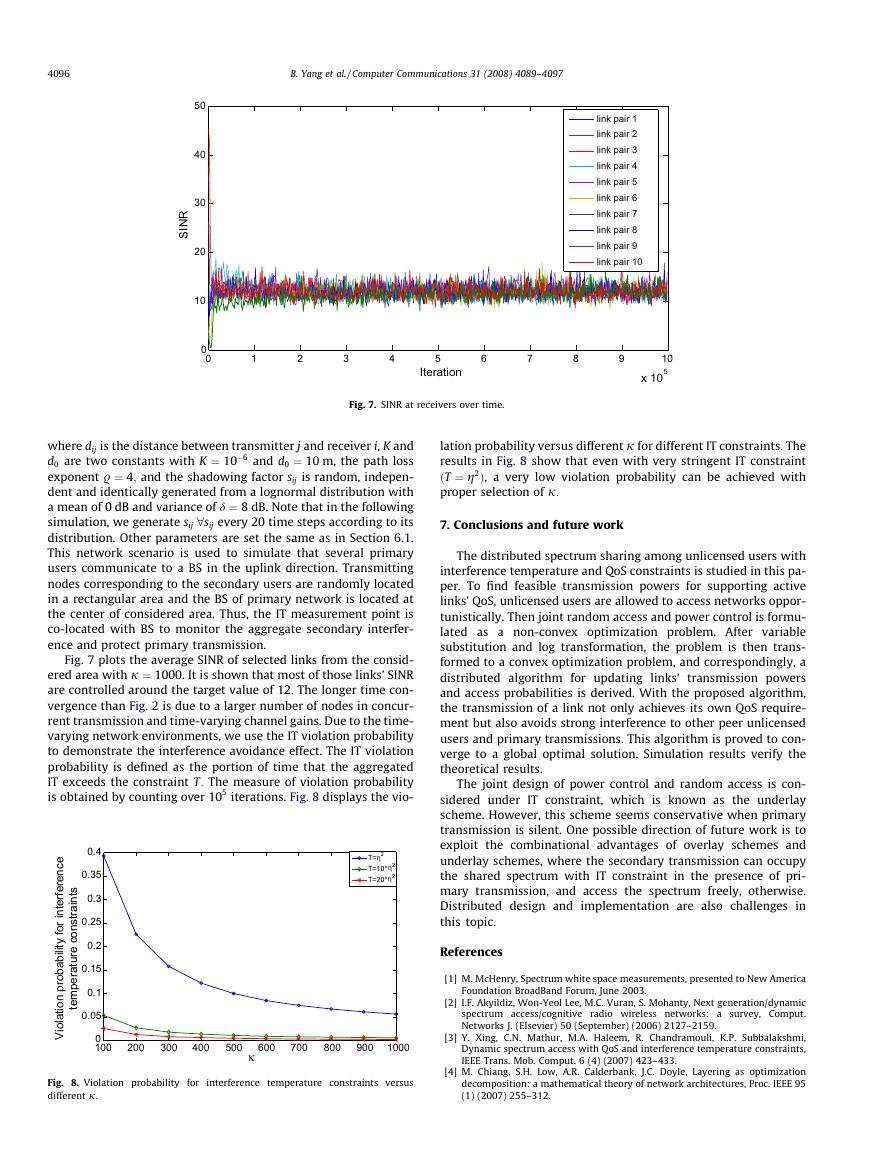
B. Yang et al. / Computer Communications 31 (2008) 4089–4097
R
N
S
I
50
40
30
20
10
0
0
link pair 1
link pair 2
link pair 3
link pair 4
link pair 5
link pair 6
link pair 7
link pair 8
link pair 9
link pair 10
1
2
3
4
5
Iteration
6
7
8
9
10
x 105
Fig. 7. SINR at receivers over time.
where dij is the distance between transmitter j and receiver i, K and
d0 are two constants with K ¼ 10�6 and d0 ¼ 10 m, the path loss
exponent . ¼ 4; and the shadowing factor sij is random, indepen-
dent and identically generated from a lognormal distribution with
a mean of 0 dB and variance of d ¼ 8 dB. Note that in the following
simulation, we generate sij 8sij every 20 time steps according to its
distribution. Other parameters are set the same as in Section 6.1.
This network scenario is used to simulate that several primary
users communicate to a BS in the uplink direction. Transmitting
nodes corresponding to the secondary users are randomly located
in a rectangular area and the BS of primary network is located at
the center of considered area. Thus, the IT measurement point is
co-located with BS to monitor the aggregate secondary interfer-
ence and protect primary transmission.
Fig. 7 plots the average SINR of selected links from the consid-
ered area with j ¼ 1000. It is shown that most of those links’ SINR
are controlled around the target value of 12. The longer time con-
vergence than Fig. 2 is due to a larger number of nodes in concur-
rent transmission and time-varying channel gains. Due to the time-
varying network environments, we use the IT violation probability
to demonstrate the interference avoidance effect. The IT violation
probability is defined as the portion of time that the aggregated
IT exceeds the constraint T: The measure of violation probability
is obtained by counting over 105 iterations. Fig. 8 displays the vio-
e
c
n
e
r
e
f
r
e
n
t
i
r
o
f
y
t
i
l
i
b
a
b
o
r
p
n
o
l
i
t
a
o
V
i
i
s
t
n
a
r
t
s
n
o
c
e
r
u
t
a
r
e
p
m
e
t
0.4
0.35
0.3
0.25
0.2
0.15
0.1
0.05
0
100
T=η2
T=10* 2
η
T=20* 2
η
200
300
400
500
κ
600
700
800
900
1000
Fig. 8. Violation probability for interference temperature constraints versus
different j:
lation probability versus different j for different IT constraints. The
results in Fig. 8 show that even with very stringent IT constraint
ðT ¼ g2Þ, a very low violation probability can be achieved with
proper selection of j:
7. Conclusions and future work
The distributed spectrum sharing among unlicensed users with
interference temperature and QoS constraints is studied in this pa-
per. To find feasible transmission powers for supporting active
links’ QoS, unlicensed users are allowed to access networks oppor-
tunistically. Then joint random access and power control is formu-
lated as a non-convex optimization problem. After variable
substitution and log transformation, the problem is then trans-
formed to a convex optimization problem, and correspondingly, a
distributed algorithm for updating links’ transmission powers
and access probabilities is derived. With the proposed algorithm,
the transmission of a link not only achieves its own QoS require-
ment but also avoids strong interference to other peer unlicensed
users and primary transmissions. This algorithm is proved to con-
verge to a global optimal solution. Simulation results verify the
theoretical results.
The joint design of power control and random access is con-
sidered under IT constraint, which is known as the underlay
scheme. However, this scheme seems conservative when primary
transmission is silent. One possible direction of future work is to
exploit the combinational advantages of overlay schemes and
underlay schemes, where the secondary transmission can occupy
the shared spectrum with IT constraint in the presence of pri-
mary transmission, and access the spectrum freely, otherwise.
Distributed design and implementation are also challenges in
this topic.
References
[1] M. McHenry, Spectrum white space measurements, presented to New America
Foundation BroadBand Forum, June 2003.
[2] I.F. Akyildiz, Won-Yeol Lee, M.C. Vuran, S. Mohanty, Next generation/dynamic
spectrum access/cognitive radio wireless networks: a survey, Comput.
Networks J. (Elsevier) 50 (September) (2006) 2127–2159.
[3] Y. Xing, C.N. Mathur, M.A. Haleem, R. Chandramouli, K.P. Subbalakshmi,
Dynamic spectrum access with QoS and interference temperature constraints,
IEEE Trans. Mob. Comput. 6 (4) (2007) 423–433.
[4] M. Chiang, S.H. Low, A.R. Calderbank, J.C. Doyle, Layering as optimization
decomposition: a mathematical theory of network architectures, Proc. IEEE 95
(1) (2007) 255–312.
�













 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc