Available online at www.sciencedirect.com
Journal of the Franklin Institute 354 (2017) 8490–8512
www.elsevier.com/locate/jfranklin
H ∞
filtering for networked systems with
hybrid-triggered communication mechanism and
stochastic cyber attacks
Jinliang Liu
∗
a ,
, Lili Wei
a , Engang Tian
b , Shumin Fei
a
c , Jie Cao
a College of Information Engineering, Nanjing University of Finance and Economics, Nanjing, Jiangsu 210023, PR
China
b Institute of Information and Control Engineering Technology, Nanjing Normal University, Nanjing, Jiangsu
c School of Automation, Southeast University, Nanjing, Jiangsu 210096, PR China
210042, PR China
Received 4 April 2017; received in revised form 10 September 2017; accepted 14 October 2017
Available online 24 October 2017
Abstract
This paper concentrates on investigating H ∞
filtering for networked systems with hybrid-triggered
communication mechanism and stochastic cyber attacks. Random variables satisfying Bernoulli distri-
bution are introduced to describe the hybrid-triggered scheme and stochastic cyber attacks, respectively.
Firstly, a mathematical H ∞
filtering error model with hybrid-triggered communication mechanism is
constructed under the stochastic cyber attacks. Secondly, by using Lyapunov stability theory and linear
matrix inequality (LMI) techniques, the sufficient conditions which can guarantee the stability of aug-
mented filtering error system are obtained and the parameters of the designed filter can be presented in
an explicit form. Finally, numerical examples are given to demonstrate the feasibility of the designed
filter.
© 2017 The Franklin Institute. Published by Elsevier Ltd. All rights reserved.
1. Introduction
Networked control systems (NCSs) are a kind of control systems wherein feedback signals
and control signals are exchanged through a network in a form of information package. It’s
∗
Corresponding author.
E-mail address: liujinliang@vip.163.com (J. Liu).
https://doi.org/10.1016/j.jfranklin.2017.10.007
0016-0032/© 2017 The Franklin Institute. Published by Elsevier Ltd. All rights reserved.
�
J. Liu et al. / Journal of the Franklin Institute 354 (2017) 8490–8512
8491
characterized by enabling the execution of several tasks far away when it connects cyber
space to physical space [1] . Due to the advantages such as high flexibility, low cost and
simple installation [2,3] , NCSs are applied in different kinds of fields referring to aircrafts,
automobiles, vehicles and so on [4–6] . Therefore, NCSs are attracting more and more interest
owing to the development and the advantages of the Internet [7] . In [8] , the robust H ∞
con-
troller is designed for networked control systems with uncertainties such like network-induced
delay and data dropouts. The synchronization problem of feedback control is investigated in
[9] with time-varying delay for complex dynamic networks. The authors in [10] study the
robust fault tolerant control problem for distributed network control systems.
In the past few years, time-triggered method (periodic sampling) is widely adopted for
system modeling and analysis in the NCSs [11] , however, periodic sampling will generate lots
of redundant signals if all the sampled data is transmitted through the network. To make full
use of the limited network resource, lots of researchers propose the event-triggered schemes
to overcome the problem caused by periodic sampling, for example, a novel event-triggered
scheme is proposed in [12] , in which a H ∞
controller is designed for NCSs. The core idea of
the novel event-triggered scheme in [12] is that whether the newest sampled data is released or
not is dependent on a threshold, and the adoption of event-triggered scheme can largely help
alleviate the burden of the network [13] . Consequently, there are large numbers of researchers
interested in the investigations about the novel event-triggered scheme proposed in [12] . An
event-triggered non-parallel distribution compensation control problem in [14] is addressed
for networked Takagi–Sugeno (T–S) fuzzy systems. The authors of [15] consider the event-
triggered filtering problem for discrete-time linear system with package dropouts satisfying
Bernoulli distribution. In [16] , a discrete event-triggered scheme is proposed for fuzzy filter
design in a class of nonlinear NCSs. Inspired by the aforementioned event-triggered scheme in
[12] , the hybrid-triggered scheme which consists of time-triggered scheme and event-triggered
scheme is firstly proposed in [17] , which investigates the problem of control stabilization for
networked control systems under the hybrid-triggered scheme. Based on the hybrid-triggered
scheme above, the authors in [18] are concerned with the hybrid-driven-based reliable control
design for a class of T–S fuzzy systems with probabilistic actuator faults and nonlinear
perturbations. Motivated by the proposed hybrid-triggered scheme in [17] , this paper is devoted
to the hybrid-triggered H ∞
filtering subject to stochastic cyber attacks on the measurement
outputs.
Due to the insertion of the network in the control systems, challenges including packet
dropouts, network-induced delay and randomly occurring nonlinearities [19–22] are inevitable.
It is nonnegligible that another phenomena named cyber attacks can be more destroyable. Cy-
ber attacks are offensive maneuvers which target networked information systems, infrastruc-
tures and networked devices by various means of malicious acts. By hacking into a susceptible
system, cyber attacks can be the biggest threat to the security of network. As the description
in [23] , there are three kinds of common attacks containing denial of service attacks [24,25] ,
relay attacks [26,27] and deception attacks [28,29] . With the rapid development of the net-
work, the influence of cyber attacks can not be neglected any more. Based on the cyber attacks
mentioned above, lots of researches are investigated and impressive results are yielded. The
authors are concerned with extended Kalman filter design for stochastic nonlinear systems
under cyber attacks in [30] . The distributed recursive filtering problem is studied in [31] with
quantization and deception attacks for a class of discrete time-delayed systems. In [32] , a
novel state filtering approach and sensor scheduling co-design with random deception attacks
are presented.
�
8492
J. Liu et al. / Journal of the Franklin Institute 354 (2017) 8490–8512
This paper addresses the issue about H ∞
filtering for networked systems under stochastic
cyber attacks with hybrid-triggered communication mechanism. The main contributions of this
paper are as follows. (1) In order to make full use of networked bandwidth and guarantee
the desired system performance, the hybrid-triggered scheme which consists of time-triggered
scheme and event-triggered scheme is introduced. (2) Due to the insertion of network, the
stochastic cyber attacks are considered, and the launching probability of cyber attacks is
governed by Bernoulli random variable. (3) By taking the hybrid-triggered communication
mechanism and stochastic cyber attacks into consideration, an H ∞
filter is designed for net-
worked systems. Although there are several researches concerned with filter design, to the
best of our knowledge, there is no research investigating the H ∞
filter design for networked
systems by considering both hybrid-triggered scheme and cyber attacks.
The rest of this paper is organized as follows. In the Section 2 , a filtering error system
is constructed by introducing the hybrid-triggered communication mechanism and taking the
stochastic cyber attacks into account. Section 3 gives the sufficient conditions which can guar-
antee the augmented filtering system stable by using Lyapunov functional approach and LMI
techniques. Moreover, the design algorithm of H ∞
filter is presented and the filtering param-
eters are obtained in an explicit form. Section 4 gives illustrative examples to demonstrate
the usefulness of desired H ∞
× m
real matrices; the su-perscript T stands for matrix transposition; I is the identity matrix of
× n means that the
appropriate dimension; the notation X
matrix X is real symmetric positive definite (respectively, positive semi-definite). For a matrix
∗
×m denote the n-dimensional Euclidean space, and the set of n
≥ 0), for X
∈
n
R
B and two symmetric matrices A, C and
denotes a symmetric matrix, where
0 (respectively, X
Notation: R
n
n and R
filter.
>
∗
A
B C
denotes the entries implied by symmetry.
2. Problem description and preliminaries
In this paper, the problem of H ∞
filtering for networked system with hybrid-triggered
communication mechanism and stochastic cyber attacks is investigated. The framework of
hybrid-triggered H ∞
filtering for networked systems under stochastic cyber attacks is shown
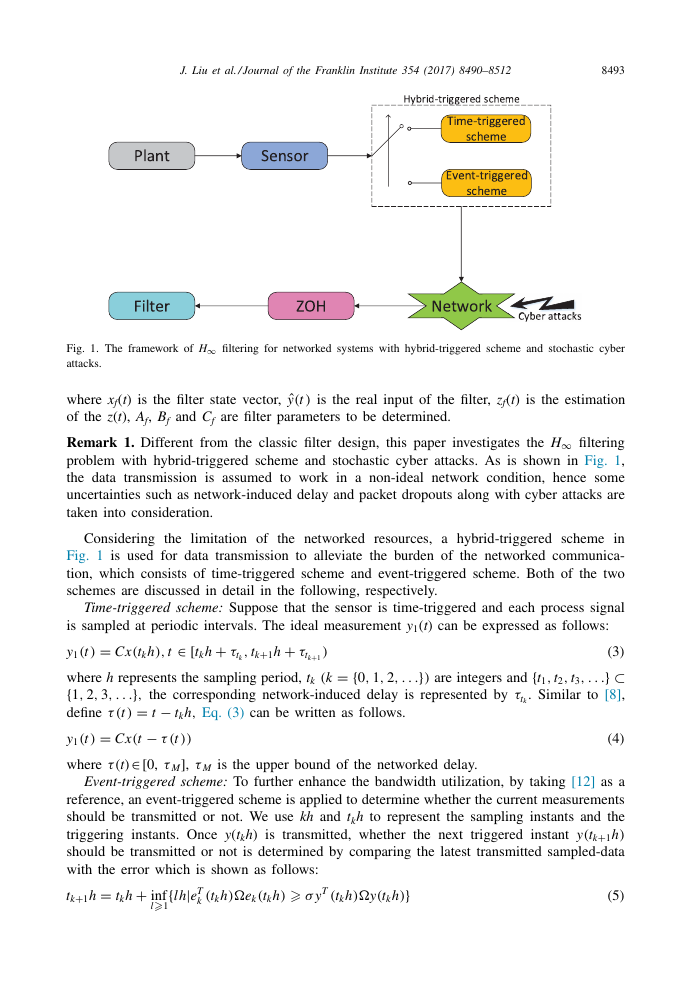
as Fig. 1 . From Fig. 1 , one can see that the framework consists of the sensor, the hybrid-
triggered scheme, the filter, a zero-order-hold (ZOH), a network channel.
The purpose of this paper is to design a hybrid-triggered H ∞
filter under stochastic cyber
attacks for networked systems. Consider the following filter system.
=
A f x f
=
C f x f
(t )
(t )
+
ˆ
y
B f
(t )
(2)
(t )
(t )
˙ x f
z f
+
Bw(t )
⎧
⎨
Consider the following continuous-time linear system.
˙
⎩
x
(t )
y(t )
z(t )
=
Ax(t )
=
Cx(t )
=
L x
(t )
∈
where x ( t )
R
be estimated, w(t )
known real matrices with appropriate dimensions.
∈
n is the state vector, y ( t )
R
2 [0,
∞
+
L
∈
)
∈
m is the ideal measurement, z ( t )
R
p is the signal to
represents the disturbance input vector, A , B , C and L are
(1)
�
J. Liu et al. / Journal of the Franklin Institute 354 (2017) 8490–8512
8493
Fig. 1. The framework of H ∞
attacks.
filtering for networked systems with hybrid-triggered scheme and stochastic cyber
ˆ
y
(t )
is the real input of the filter, z f ( t ) is the estimation
where x f ( t ) is the filter state vector,
of the z ( t ), A f , B f and C f are filter parameters to be determined.
Remark 1. Different from the classic filter design, this paper investigates the H ∞
filtering
problem with hybrid-triggered scheme and stochastic cyber attacks. As is shown in Fig. 1 ,
the data transmission is assumed to work in a non-ideal network condition, hence some
uncertainties such as network-induced delay and packet dropouts along with cyber attacks are
taken into consideration.
Considering the limitation of the networked resources, a hybrid-triggered scheme in
Fig. 1 is used for data transmission to alleviate the burden of the networked communica-
tion, which consists of time-triggered scheme and event-triggered scheme. Both of the two
schemes are discussed in detail in the following, respectively.
Time-triggered scheme: Suppose that the sensor is time-triggered and each process signal
t
,
(t )
∈
+
[ t k h
=
Cx(t k h)
+
t k+1 h
,
τt k
is sampled at periodic intervals. The ideal measurement y 1 ( t ) can be expressed as follows:
y 1
τt k+1
)
where h represents the sampling period, t k
{
}
the corresponding network-induced delay is represented by
1
3
2,
,
,
,
.
.
=
− t k h,
define
t
τ (t )
− τ (t ))
=
Cx(t
∈
τ M ],
[0,
τ ( t )
(3)
}
⊂
{
are integers and
t 3
t 2
t 1
.
,
,
,
. Similar to [8] ,
τt k
τ M is the upper bound of the networked delay.
Eq. (3) can be written as follows.
y 1
where
=
(k
1
2,
,
(4)
(t )
}
.
)
.
{
0,
.
.
.
.
Event-triggered scheme: To further enhance the bandwidth utilization, by taking [12] as a
reference, an event-triggered scheme is applied to determine whether the current measurements
should be transmitted or not. We use kh and t k h to represent the sampling instants and the
triggering instants. Once y ( t k h ) is transmitted, whether the next triggered instant y(t k+1 h)
should be transmitted or not is determined by comparing the latest transmitted sampled-data
with the error which is shown as follows:
=
+
{
t k+1 h
inf
t k h
l
1
T (t k h)�y(t k h)
T
e
(t k h)�e k
k
(t k h)
lh|
(5)
σ y
}
�
8494
J. Liu et al. / Journal of the Franklin Institute 354 (2017) 8490–8512
.
.
0,
� >
σ ∈
where
=
1
2,
,
[0, 1) and l
. The threshold error e k
(t k h)
.
τt k+1
)
+
+
t k+1 h
For analyzing more easily, the interval [ t k h
τt k
,
+
+
+
ηt+
ηt+
h
lh
t k h
,
l
≤ τt k
≤ η(t )
≤ h
+
0
can be written as
=
y(t k h)
+
subintervals. Suppose that there exists a constant g which satisfies [ t k h
g
l=1
1
2,
where
,
,
�l
− 1 . Define
t k
+
x(t k h
lh)
=
Cx(t
=
+
+
[ t k h
lh
�l
=
− t k h
− lh,
η(t )
t
the measurement y 2
(t )
,
− η(t ))
− y(t k h
+
.
lh)
can be divided into several
=
+
t k+1 h
τt k+1
τt k
,
)
=
=
{
g}
−
l+1 ]
t k+1
l
g
,
,
.
.
.
,
=
−
ηM . Let e k
(t )
x(t k h)
ηt k+
l+1
+
Ce k
(6)
(t )
(t )
y 2
Remark 2. From the event-triggered judgement algorithm above, for a given period h , the
sampler samples the data can be found at time kh , and the next sensor measurement is at
+
··· are the release time, then it is easily obtained
1)
time
(k
=
− t i h denote the release period of event generator in (5) , where s i h mean that
t i+1 h
that s i h
the sampling instants between the two conjoint releasing instants.
h. Suppose that t 0 h,
t 2 h,
t 1 h,
.
.
0,
}
.
1
2,
,
⊆ {
···}
Remark 3. According to the event-triggered algorithm (5) , a set of the releasing instants
{
. Learning from the research [8] , it is not required that t k+1
t k .
t 1
t 3
t 2
>
,
,
,
{
=
+
=
. If t k+1
The packet dropouts will not occur only when
1
t 1
t 3
t 2
t k
.
.
,
,
,
,
¯τ and
=
+
h imply the packet dropouts and
then h
τt k
τt k
¯τ is a constant. Thus, the frequency of releasing instants
the network-induced delay, where
depends on the value of
σ and the variations of the sensor measurements.
two special cases about
,
τt k
τt k+1
}
.
<
1
2,
,
}
.
3
,
>
{
.
.
Combine Eq. (4) in time-triggered scheme and Eq. (6) in event-triggered scheme, similar
via hybrid-triggered scheme can be expressed as follows:
to [17] , the measurement
¯y
(t )
=
=
α(t )
α(t )
¯y
(t )
− α(t
+
(1
))
+
(1
− τ (t ))
y 1
(t )
Cx(t
∈
[0, 1],
α( t )
where
mathematical variance of
α( t ).
y 2
(t
)
− α(t ))
− η(t ))
[ Cx(t
+
Ce k
(t )
]
¯α is utilized to represent the expectation of
(7)
α( t ), and
ρ2
1
represents the
Remark 4. To describe the stochastic switching rule between the time-triggered scheme and
α( t ) which satisfies the Bernoulli distribution
the event-triggered scheme, the random variable
− τ (t ))
=
it is observed that the data is
is introduced. In (7) , when
Cx(t
,
=
¯y
=
then,
0,
transmitted via time-triggered scheme; When
Cx(t
α(t )
(t )
,
the event-triggered scheme is activated in data transmission.
− η(t ))
+
Ce k
=
1
,
¯y
(t )
α(t )
(t )
The cyber attacks in this paper belong to deception attacks which aim to destroy the
stability and performance of networked system. A nonlinear function f ( x ( t )) is utilized to
describe the deception attacks which is assumed to satisfy the following assumption:
Assumption 1. Suppose that deception attacks f ( x ( t )) satisfy the following condition:
||
≤ ||
||
||
f
(x(t ))
2
Gx(t )
2
(8)
where G is a constant matrix representing the upper bound of the nonlinearity.
Remark 5. In order to describe the restrictive condition of nonlinear perturbation, the infor-
mation of upper bound is introduced in [36,37] . Similarly, we use matrix G to represent the
�
J. Liu et al. / Journal of the Franklin Institute 354 (2017) 8490–8512
8495
upper bound of stochastic cyber attacks in Assumption 1 , and its value depends on the actual
situation of networked attacks.
In the transmitting process, normal signals are subject to cyber attacks randomly in the
networked channel, then we use variable d ( t ) to represent the time-varying delay of the
aggressive signals which are delivered to the filter.
By using the similar methods in [23,33] , the Bernoulli variable
θ( t ) is introduced to govern
ˆ
y
(t )
of filter can be written as
the stochastic cyber attacks, then the real input
ˆ
y
(t )
+
− d (t )))
− θ (t
(1
{
+
−d (t )))
−θ (t ))
(1
¯y
(t
)
Cx(t
α(t )
(x(t
(x(t
θ (t )
θ (t )
C f
C f
=
=
))
−τ (t ))
+
−α(t ))
(1
−η(t ))
[ Cx(t
+
Ce k
(t )
}
]
∈
[0, d M ],
∈
[0, 1].
¯θ is utilized to represent the expectation of
where d ( t )
utilized to represent the mathematical variance of
θ( t )
θ( t ).
(9)
θ( t ),
ρ2
2
is
Remark 6. Bernoulli variables are used to describe the stochastic characteristic in the control
systems. In [34] , the stochastic delay is described by random Bernoulli variable for NCSs.
In [35] , the occurring probability of the two different sampling periods are described by
Bernoulli variable. In this paper, the random variables
θ( t ) which satisfy Bernoulli
distribution are used to describe the stochastic switching changes between the two different
schemes and the stochastic cyber attacks, respectively. It is noted that the Bernoulli variables
α( t ) and
θ( t ) are mutually independent.
α( t ) and
According to (9) , we can obtain the real input
of the filter. Substitute
ˆ
y
(t )
− θ (t
))
{
α(t
Cx(t
)
− τ (t
))
ˆ
y
(t )
into Eq.
(10)
⎧
⎨
˙
⎩
x f
z f
(2) , then the filter can be written as follows:
+
− d (t )))
(1
+
}}
]
(t )
Ce k
C f
(x(t
− η(t ))
(t )
+
{
(t )
θ (t )
B f
− α(t ))
[ Cx(t
(t )
(t )
=
A f x f
+
(1
=
C f x f
x(t )
(t )
x f
Define
=
e
(t )
˜
z
(t )
,
=
z(t )
− z f
(t )
(12)
⎧
⎨
Based on Eqs. (1) and (10), the filtering error system can be described as
˙
⎩
e
(t )
˜
z
(t )
−τ (t
(t
))
+
θ (t )
(t
)
−α(t
))
))
(1
¯A f e
=
+
¯C f e
=
+
−θ (t
(1
(t )
α(t
)
− α(t
− θ (t ))(1
))
(t )
¯B f H e
¯B f e k
¯B w(t
+
+
−θ (t ))(1
(1
)
¯B f f
− d (t )))
(x(t
0
A
0 A f
¯B f
=
,
¯B
=
,
0
B f C
=
H
,
B
0
I 0
,
¯C f
=
L
−C f
where
=
¯A f
Some important lemmas are introduced in the following:
¯B f H e
−η(t
(t
))
(11)
∈
n , and positive definite matrix Q
n
R
× n , the following
∈
Lemma 1 ( [38] ) . For any vectors x , y
R
inequality holds:
+
T Qx
y
≤ x
−1 y
T Q
T y
2x
�
8496
J. Liu et al. / Journal of the Franklin Institute 354 (2017) 8490–8512
∈
[0,
τ ( t )
∈
[0, d M ],
τ M ], d ( t )
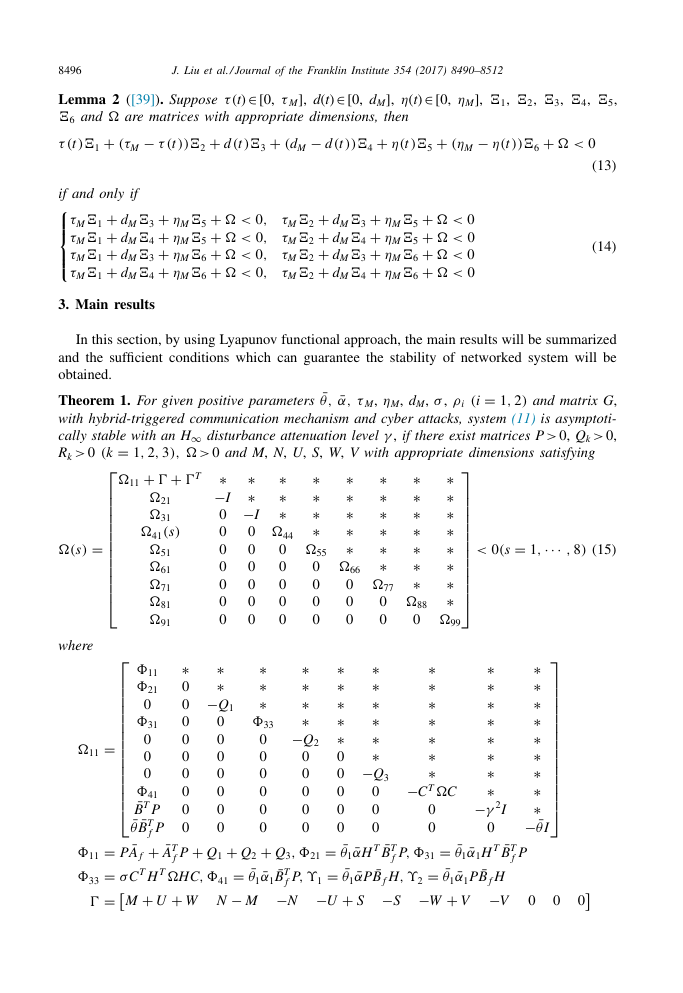
Lemma 2 ( [39] ) . Suppose
�6 and
� are matrices with appropriate dimensions, then
+
τ (t )�1
− τ (t ))�2
+
+
d (t )�3
− d (t ))�4
+
(d M
(τM
∈
[0,
η( t )
+
η(t )�5
− η(t ))�6
+
(ηM
� < 0
ηM ],
�1 ,
�2 ,
�3 ,
�4 ,
�5 ,
⎧
⎪
⎪
⎨
⎪
⎪
⎩
if and only if
+
d M
�1
+
d M
�1
+
d M
�1
+
d M
�1
+
�3
+
�4
+
�3
+
�4
τM
τM
τM
τM
+
�5
+
�5
+
�6
+
�6
ηM
ηM
ηM
ηM
� <
� <
� <
� <
0,
0,
0,
0,
+
d M
�2
+
d M
�2
+
d M
�2
+
d M
�2
+
�3
+
�4
+
�3
+
�4
τM
τM
τM
τM
+
�5
+
�5
+
�6
+
�6
ηM
ηM
ηM
ηM
� <
� <
� <
� <
0
0
0
0
(13)
(14)
3. Main results
In this section, by using Lyapunov functional approach, the main results will be summarized
and the sufficient conditions which can guarantee the stability of networked system will be
obtained.
¯θ ,
¯α,
=
1
2)
(i
,
>
ρi
σ ,
τ M ,
ηM , d M ,
γ , if there exist matrices P
disturbance attenuation level
0, Q k
>
0 and M , N , U , S , W , V with appropriate dimensions satisfying
Theorem 1. For given positive parameters
and matrix G ,
with hybrid-triggered communication mechanism and cyber attacks, system (11) is asymptoti-
cally stable with an H ∞
0,
R k
� >
�T ∗
−I
0
0
0
0
0
0
0
∗
∗
∗
∗
∗
∗
∗
�88
0
∗
∗
∗
∗
∗
∗
�77
0
0
∗
∗
∗
∗
∗
�66
0
0
0
∗
∗
∗
∗
∗
∗
∗
∗
�99
⎤
⎥
⎥
⎥
⎥
⎥
⎥
⎥
⎥
⎥
⎥
⎥
⎥
⎦
=
1
0(s
,
··· ,
(15)
�(s)
8)
>
<
where
0
=
�41
∗
∗
−I
0
0
0
0
0
0
∗
∗
∗
�44
0
0
0
0
0
∗
∗
∗
∗
�55
0
0
0
0
⎡
=
1
2,
3)
(k
,
,
⎢
+
� +
⎢
⎢
�11
⎢
⎢
�21
⎢
⎢
�31
⎢
⎢
(s)
⎢
⎢
�51
⎢
⎣
�61
�71
�81
�91
⎡
⎢
∗
∗
∗
⎢
⎢
�11
∗
∗
⎢
⎢
0
�21
−Q 1
∗
⎢
⎢
0
0
⎢
⎢
0
0
�33
�31
⎢
⎢
0
0
0
0
⎢
⎢
0
0
0
0
⎢
⎣
0
0
0
0
0
0
0
�41
¯B
T P
0
0
0
¯θ ¯B
T
P 0
0
0
f
¯A
¯A f
=
+
+
=
+
+
Q 3
Q 2
Q 1
P
�11
�21
,
¯θ1
¯B
=
=
¯α1
=
T �H C,
T H
T
σC
P,
ϒ1
�41
�33
f
+
− M
−N
−U
+
� =
U
W N
M
∗
∗
∗
∗
−Q 2
0
0
0
0
0
�11
T
P
f
=
∗
∗
∗
∗
∗
0
0
0
0
0
∗
∗
∗
∗
∗
∗
−Q 3
0
0
0
¯θ1
T ¯B
¯αH
¯θ1
¯B f H,
¯αP
+
−S
S
∗
∗
∗
∗
∗
∗
∗
∗
∗
∗
∗
∗
∗
∗
−C
∗
T �C
−γ 2 I
0
0
0
¯θ1
T ¯B
¯α1 H
=
T
P,
�31
f
¯θ1
¯B f H
=
¯α1 P
ϒ2
−W
+
−V
V
⎤
⎥
∗
⎥
⎥
∗
⎥
⎥
∗
⎥
⎥
∗
⎥
⎥
∗
⎥
⎥
∗
⎥
⎥
∗
⎥
⎦
∗
∗
− ¯θI
T
P
f
0 0 0
�
8497
,
=
=
=
=
=
=
,
,
,
,
,
,
=
=
=
(6)
�61
�21
�51
�41
(2)
�41
(7)
�41
(4)
�41
(3)
�41
(5)
�41
(1)
=
�31
⎤
⎦
⎤
⎦
J. Liu et al. / Journal of the Franklin Institute 354 (2017) 8490–8512
⎡
√
⎣
√
T
τM M
√
⎡
T
ηM U
T
d M V
√
⎣
√
T
τM N
√
T
ηM U
T
d M V
√
√
ϒ2 0 0 0
τM
√
ϒ2 0 0 0
ηM
ϒ2 0 0 0
d M
√
− ¯θ1
√
τM P
ρ1
− ¯θ1
√
ηM P
ρ1
− ¯θ1
d M P
ρ1
√
¯α1
√
τM P
ρ2
¯α1
√
ηM P
ρ2
¯α1
d M P
ρ2
√
−ρ1
√
τM P
ρ2
−ρ1
√
ηM P
ρ2
−ρ1
d M P
ρ2
¯C f 0 0 0 0 0 0 0 0 0
⎡
⎤
⎡
⎡
⎤
⎤
¯θ2 GH 0 0 0 0
0 0 0 0 0
√
√
√
⎣
⎦
⎣
⎣
⎦
⎦
√
√
√
T
T
T
τM M
τM M
τM M
√
√
√
⎡
⎤
⎡
⎤
⎡
⎤
T
T
T
ηM U
ηM S
ηM S
T
T
T
d M W
d M W
d M V
√
√
√
⎣
⎦
⎦
⎣
⎦
⎣
√
√
√
T
T
T
τM N
τM N
τM N
=
=
√
√
√
⎡
⎤
T
T
T
ηM U
ηM S
ηM S
(8)
�41
T
T
T
d M W
d M W
d M V
√
√
√
√ τM P
⎣
⎦
¯θ
¯θ1
¯A f
¯B f
¯B f
¯B
¯α1
√
√
√
√ ηM P
τM P
τM P
τM P
¯θ
¯θ1
¯A f
¯B
¯B f
¯B f
¯α1
√
√
√
√
⎡
⎤
ηM P
ηM P
ηM P
¯θ1
¯θ
¯A f
¯B f
¯B f
¯B
¯α1
d M P
d M P
d M P
d M P
√
√
⎣
⎦
¯θ1
− ¯θ1
¯B f H 0 0 0
¯B f 0 0
√
√
0
τM P
τM P
ρ1
ρ1
¯θ1
− ¯θ1
¯B f 0 0
¯B f H 0 0 0
√
√
⎡
0
ηM P
ηM P
ρ1
ρ1
¯θ1
− ¯θ1
¯B f H 0 0 0
¯B f 0 0
0
d M P
d M P
ρ1
ρ1
√
√
⎣
¯B f H
¯B f
¯αρ2
¯α1
√
√
0
τM P
τM P
ρ2
¯B f H 0 0 0
¯B f
¯αρ2
¯α1
√
√
⎡
⎤
0
ηM P
ηM P
ρ2
¯B f H 0 0 0
¯B f
¯αρ2
¯α1
0
d M P
d M P
ρ2
√
√
⎣
⎦
¯B f 0 0
¯B f H 0 0 0
−ρ1
√
√
0
τM P
τM P
ρ2
ρ1
ρ2
¯B f 0 0
¯B f H 0 0 0
−ρ1
√
√
⎡
⎤
0
ηM P
ηM P
ρ2
ρ1
ρ2
¯B f H 0 0 0
¯B f 0 0
−ρ1
0
d M P
d M P
ρ1
ρ2
ρ2
√
⎣
⎦
¯B f
√
0 0 0 0 0 0 0 0 0
τM P
ρ2
¯B f
√
0 0 0 0 0 0 0 0 0
�91
ηM P
ρ2
¯B f
0 0 0 0 0 0 0 0 0
d M P
ρ2
¯θ ,
¯θ2
¯θ ¯θ1
¯θ1
− ¯θ ,
=
=
=
=
diag{−R 1
ρ2
1
�44
2
−P R
{−P R
=
−P R
=
}
−1
−1
−1
P,
P
P,
�66
�55
3
2
1
T =
T =
0 0 0 0 0 0 0 0
N
M
,
T =
T =
0 0 0 0 0 0
U
S
,
T =
T =
0 0 0 0
W
V
,
�41
√
√
ϒ1 0
τM
√
ϒ1 0
ηM
ϒ1 0
d M
¯B f H 0
¯B f H 0
¯B f H 0
¯B f H
¯B f H 0
¯B f H 0
¯B f H 0
¯B f H 0
¯B f H 0
T
M
2
T
0 0 U
4
T
0 0 0 0 W
6
T
T
0 N
N
3
2
T
0 0 0 S
0 0 0 0 0
4
T
0 0 0 0 0 V
6
0 0 0 0 0 0 0
T
S
5
0 0 0
− ¯α,
=
¯α ¯α1
ρ2
1
=
=
�99
�88
−R 3
}
−R 2
¯α1
=
1
=
�77
0 0
0 0
0 0
T
M
1
T
U
1
T
W
1
0 0 0
�71
�81
T
V
7
=
=
=
,
,
0
,
,
⎤
⎦
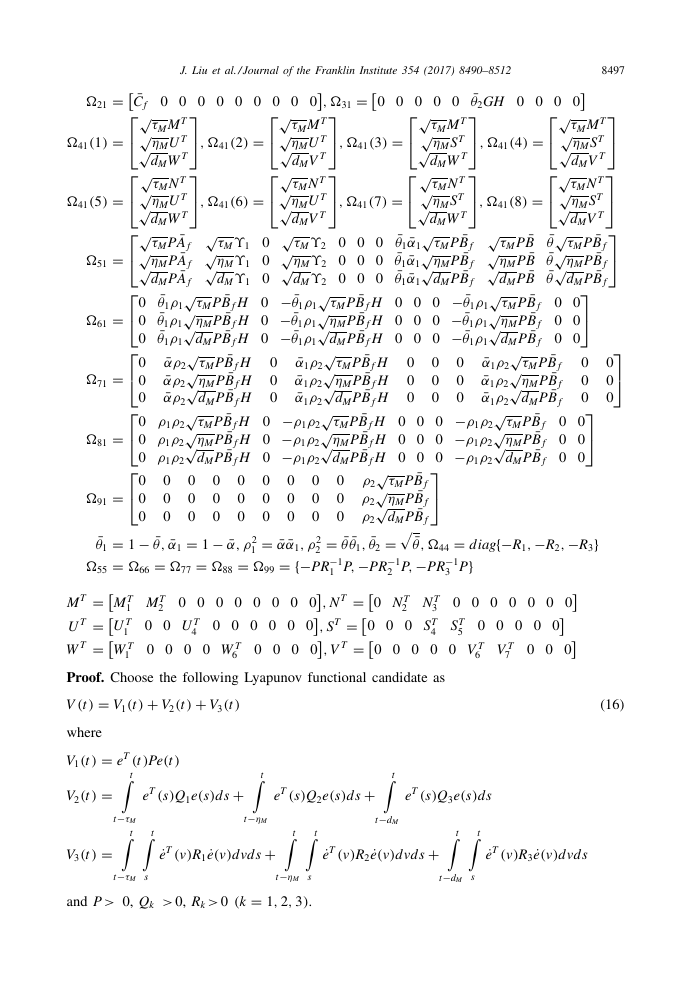
Proof. Choose the following Lyapunov functional candidate as
=
V 1
(t )
+
V 2
(t )
+
V 3
(t )
V
(t )
(16)
t
t
T (t )
Pe
(t )
V 1
(t )
where
=
e
=
(t )
V 2
t
t
t−τM
=
V 3
(t )
T (s)
e
Q 1 e
(s)
t
˙
T (v)
e
˙
e
R 1
(v)
T (s)
e
t
+
ds
t−ηM
+
d vd s
t−ηM
=
3)
1
2,
(k
,
0
s
.
s
t−τM
0, Q k
>
and P
>
0, R k
>
Q 2 e
(s)
t
˙
T (v)
e
+
ds
t−d M
˙
e
R 2
(v)
T (s)
e
Q 3 e
(s)
ds
t
t
+
d vd s
t−d M
s
˙
T (v)
e
˙
e
R 3
(v)
d vd s
�













 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc