www.linux520.com
DDOS
DDOS
DDOS
DDOS 常见攻击类型、攻击工具
birdarmy
ByByByBy birdarmy
www.linux520.com
birdarmy
www.linux520.com
birdarmy 整理 www.linux520.com
www.linux520.com
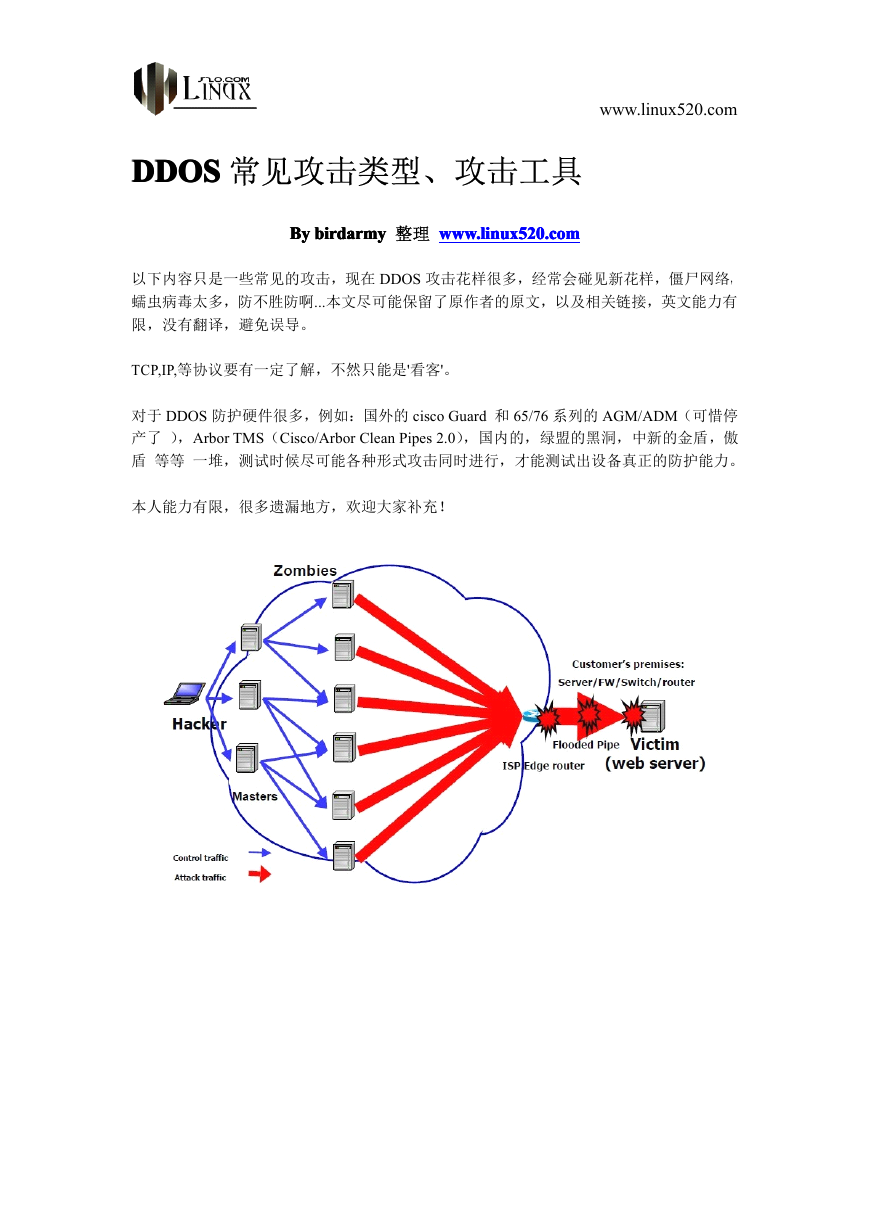
以下内容只是一些常见的攻击,现在 DDOS 攻击花样很多,经常会碰见新花样,僵尸网络,
蠕虫病毒太多,防不胜防啊...本文尽可能保留了原作者的原文,以及相关链接,英文能力有
限,没有翻译,避免误导。
TCP,IP,等协议要有一定了解,不然只能是'看客'。
对于 DDOS 防护硬件很多,例如:国外的 cisco Guard 和 65/76 系列的 AGM/ADM(可惜停
产了 ),Arbor TMS(Cisco/Arbor Clean Pipes 2.0),国内的,绿盟的黑洞,中新的金盾,傲
盾 等等 一堆,测试时候尽可能各种形式攻击同时进行,才能测试出设备真正的防护能力。
本人能力有限,很多遗漏地方,欢迎大家补充!
�
www.linux520.com
rotocol
PPPProtocol
rotocol
rotocol 漏洞漏洞漏洞漏洞
Fragment
Reassembly
Fragment
Reassembly
Fragment Reassembly
Fragment
Reassembly
(ping>65,536
PingPingPingPing ofofofof DeathDeathDeathDeath (ping>65,536
bytes)
(ping>65,536
bytes)
(ping>65,536 bytes)
bytes)
PingPingPingPing ofofofof DeathDeathDeathDeath 简称 POD 或 Ping 炸弹,是一种阻断服务攻击(DDoS)手法,借由对目标电
脑送出大量 ping 指令的封包达到攻击效果。通常一次 ping 大小为 56 bytes(若考虑 IP 标头
应为 84bytes)。有多个电脑无法处理大于 IPv4 最大封包大小(65,535 bytes)的 ping 封包。
在早期,这攻击方式可以应用在 TCP/IP 通讯协定上,可以应付多种系统,例如 Unix、Linux、
Mac、Windows、打印机、路由器等,约在 1997-1998 年后多数系统在已经修正这问题。
一般而言,送出 65,536 bytes ping 封包对 IP 通讯协定而言不是合法的用法,若送出 ping 封
包时分成多个片段,目标电脑必须不断重组封包,期间可能因发缓冲区溢位,而导致系统崩
溃
http://zh.wikipedia.org/wiki/Ping_of_death
fragments cancancancan’’’’tttt bebebebe reassembled)
fragments
(ICMP
JoltJoltJoltJolt (ICMP
reassembled)
(ICMP
fragments
reassembled)
(ICMP fragments
reassembled)
offset
confusing
(fragments withwithwithwith confusing
(fragments
Teardrop
values)
Teardrop
(fragments
confusing
offset
values)
offset values)
confusing offset
Teardrop (fragments
Teardrop
values)
Teardrop
Teardrop
Teardrop
Teardrop 是基于 UDP 的病态分片数据包的攻击方法,其工作原理是向被攻击者发送多个分
片的 IP 包(IP 分片数据包中包括该分片数据包属于哪个数据包以及在数据包中的位置等信
�
www.linux520.com
息),某些操作系统收到含有重叠偏移的伪造分片数据包时将会出现系统崩溃、重启等现象。
(利用 UDP 包重组时重叠偏移(假设数据包中第二片 IP 包的偏移量小于第一片结束的位移,
而且算上第二片 IP 包的 Data,也未超过第一片的尾部,这就是重叠现象。)的漏洞对系统主
机发动拒绝服务攻击,最终导致主机菪掉;对于 Windows 系统会导致蓝屏死机,并显示 STOP
0x0000000A 错误。)
SYNdrop
SYNdrop
SYNdrop
SYNdrop
SYNdrop
SYNdrop
SYNdrop
SYNdrop is used by an attacker to send IP fragments that cannot be reassembled properly by
manipulating the offset value of a packet. This may cause reboot or halt of victim system.
Bonk,
Nestea
Boink,
TearDrop,
targa,
SYNdrop
TearDrop2
SYNdrop
targa,
TearDrop,
Boink,
Nestea
Bonk,
TearDrop2
Many other variants of SYNdrop
Bonk, TearDrop2
Nestea Bonk,
Boink, Nestea
TearDrop, Boink,
targa, TearDrop,
SYNdrop such as targa,
TearDrop2
NewTear
andandandand NewTear
NewTear
NewTear are available. A simple reboot is the preferred remedy after this happening
http://www.rs-labs.com/papers/tacticas/ircutils/syndrop.html
Others
Others
Others
Others
nestea, bonk, boink, newtear
Closing
Connections
Closing
Connections
Closing Connections
Closing
Connections
ICMP unreachable teardown
Brkill–teardown a IRC connection
between
connections
Rst_flip––––killkillkillkill connections
Rst_flip
unixhosts
Rst_flip
connections
between
unixhosts
between unixhosts
connections between
Rst_flip
unixhosts
This is a DOS attack against an existing connection where one of the hosts is a Linux, SunOS,
FreeBSD and possibly others. it is possible to cause a connection to be dropped by sending a
customized packets to one of the hosts.
couple of
ftp://ftp.ntua.gr/mirror/technotronic/denial/rst_flip.c
Protocol
anomalies
Protocol
anomalies
Protocol anomalies
Protocol
anomalies
address/port ==== dest)
address/port
source
(Synpacket:
LandLandLandLand (Synpacket:
dest)
(Synpacket:
source
address/port
dest)
source address/port
(Synpacket: source
dest)
LANDLANDLAND (Local Area Network Denial) attack is a DoS (Denial of Service) attack that consists of
A LAND
sending a special poison spoofed packet to a computer, causing it to lock up. The security flaw
was actually first discovered in 1997 by someone using the alias "m3lt", and has resurfaced many
years later in operating systems such as Windows Server 2003 and Windows XP SP2.
�
www.linux520.com
The attack involves sending a spoofed TCP SYN packet (connection initiation) with the target
host's IP address to an open port as both source and destination.
The reason a LAND attack works is because it causes the machine to reply to itself continuously.
Definition: "A LAND attack involves IP packets where the source and destination address are set
to address the same device."
Other
land attacks have since been found in services like SNMP and Windows 88/tcp
(kerberos/global services) which were caused by design flaws where the devices accepted requests
on the wire appearing to be from themselves and causing replies repeatedly
http://en.wikipedia.org/wiki/LAND
广播域攻击
广播域攻击
广播域攻击
广播域攻击
Smurf
(ICMP)
Smurf
(ICMP)
Smurf (ICMP)
Smurf
(ICMP)
If
attack
Smurf
Smurf
attack
The Smurf
Smurf attack
attack is a way of generating significant computer network traffic on a victim
network. This is a type of denial-of-service attack that floods a target system via spoofed
broadcast ping messages.
This attack relies on a perpetrator sending a large amount of ICMP echo request (ping)
traffic to IP broadcast addresses, all of which have a spoofed source IP address of the
intended victim.
the routing device delivering traffic to those broadcast addresses
delivers the IP broadcast to all hosts (for example via a layer 2 broadcast), most hosts on
that IP network will take the ICMP echo request and reply to it with an echo reply,
multiplying the traffic by the number of hosts responding. On a multi-access broadcast
network, hundreds of machines might reply to each packet.[1]
In the late 1990s, many IP networks would participate in Smurf attacks (that is, they would
respond to pings to broadcast addresses). Today, thanks largely to the ease with which
administrators can make a network immune to this abuse, very few networks remain
vulnerable to Smurf attack
http://en.wikipedia.org/wiki/Smurf_attack
Fraggle(UDP)
Fraggle(UDP)
Fraggle(UDP)
Fraggle(UDP)
attack
fraggle
fraggle
attack
In computer security a fraggle
fraggle attack
attack is a type of denial-of-service attack where an attacker sends
a large amount of UDP echo traffic to IP broadcast addresses, all of it having a fake source address.
This is a simple rewrite of the smurf attack code.
http://en.wikipedia.org/wiki/Fraggle_attack
�
Packet
Flooding
Packet
Flooding
Packet Flooding
Packet
Flooding
SYNSYNSYNSYN flooding
flooding
flooding
flooding
www.linux520.com
A SYN flood is a form of denial-of-service attack in which an attacker sends a succession of SYN
requests to a target's system. Some systems can misdetect a SYN Flood when being scanned for
open proxies, as commonly done by IRC servers and services. These are not SYN Floods, merely
an automated system designed to check the connecting IP.[1]
�
www.linux520.com
When a client attempts to start a TCP connection to a server, the client and server exchange a
series of messages which normally runs like this:
1.The client requests a connection by sending a SYN (synchronize) message to the server.
2.The server acknowledges this request by sending SYN-ACK back to the client.
3.The client responds with an ACK, and the connection is established.
This is called the TCP three-way handshake, and is the foundation for every connection
established using the TCP protocol.
The SYN flood is a well known type of attack and is generally not effective against modern
networks[citation needed] given sufficient host CPU and bandwidth. It works if a server allocates
resources after receiving a SYN, but before it has received the ACK.
There are two methods, but both involve the server not receiving the ACK. A malicious client can
skip sending this last ACK message. Or by spoofing the source IP address in the SYN, it makes
the server send the SYN-ACK to the falsified IP address, and thus never receive the ACK. In both
cases the server will wait for the acknowledgement for some time, as simple network congestion
could also be the cause of the missing ACK.
If these half-open connections bind resources on the server, it may be possible to take up all these
resources by flooding the server with SYN messages. Once all resources set aside for half-open
connections are reserved, no new connections (legitimate or not) can be made, resulting in denial
of service. Some systems may malfunction badly or even crash if other operating system functions
are starved of resources this way.
The technology often used in 1996 for allocating resources for half open TCP connections
involved a queue which was often very short (e.g., 8 entries long) with each entry of the queue
being removed upon a completed connection, or upon expiry (e.g., after 3 minutes[2]). When the
queue was full, further connections failed. With the examples above, all further connections would
be prevented for 3 minutes by sending a total of 8 packets. A well-timed 8 packets every 3 minutes
would prevent all further TCP connections from completing. This allowed for a Denial of Service
attack with very minimal traffic.
SYN cookies provide protection against the SYN flood by eliminating the resources allocated on
the target host.
Limiting new connections per source per timeframe is not a general solution since the attacker can
spoof the packets to have multiple sources.
Reflector routers can also be used as attackers, instead of client machines.
http://en.wikipedia.org/wiki/SYN_flood
�
ACKACKACKACK flooding
flooding
flooding
flooding
www.linux520.com
ACK Flood 攻击。在 TCP 连接建立之后,所有的数据传输 TCP 报文都是带有 ACK 标志位
的,主机在接收到一个带有 ACK 标志位的数据包的时候,需要检查该 数据包所表示的连
接四元组是否存在,如果存在则检查该数据包所表示的状态是否合法,然后再向应用层传递
该数据包。如果在检查中发现该数据包不合法,例如该 数据包所指向的目的端口在本机并
未开放,则主机操作系统协议栈会回应 RST 包告诉对方此端口不存在。通常状态检测防火
墙所做的事情与此类似,只不过防火墙 只拦截非法的数据包,而不主动回应。
对比主机以及防火墙在接收到 ACK 报文和 SYN 报文时所做动作的复杂程度,显然 ACK 报
文带来 的负载要小得多。所以在实际环境中,只有当攻击程序每秒钟发送 ACK 报文的速
率达到一定的程度,才能使主机和防火墙的负载有大的变化。当发包速率很大的时 候,主
机操作系统将耗费大量的精力接收报文、判断状态,同时要主动回应 RST 报文,正常的数
据包就可能无法得到及时的处理。这时候客户端(以 IE 为例)的 表现就是访问页面反应很
慢,丢包率较高。但是状态检测的防火墙通过判断 ACK 报文的状态是否合法,借助其强大
的硬件能力可以较为有效的过滤攻击报文。当然 如果攻击流量非常大(特别是千兆线路上,
我们曾经观察到 200~300Mbps 左右的 ACK Flood),由于需要维护很大的连接状态表同时要
检查数量巨大的 ACK 报文的状态,防火墙也会不堪重负导致全网瘫痪
UDPUDPUDPUDP flooding
flooding
flooding
flooding
A UDP flood attack is a denial-of-service (DoS) attack using the User Datagram Protocol (UDP),
a stateless computer networking protocol.
Using UDP for denial-of-service attacks is not as straightforward as with the Transmission Control
Protocol (TCP). However, a UDP flood attack can be initiated by sending a large number of UDP
packets to random ports on a remote host. As a result, the distant host will:
Check for the application listening at that port;
See that no application listens at that port;
Reply with an ICMP Destination Unreachable packet.
Thus, for a large number of UDP packets, the victimized system will be forced into sending many
ICMP packets, eventually leading it to be unreachable by other clients. The IP address of outgoing
packets may also be spoofed, ensuring that the excessive ICMP return packets do not reach the
attacker, simultaneously making it harder to determine the source of the attack.
http://en.wikipedia.org/wiki/UDP_flood_attack
Reflection
Reflection
Reflection
Reflection
ICMP, UDP Broadcast Amplification
�
SYN-ACK
Flooding
SYN-ACK
Flooding
SYN-ACK Flooding
SYN-ACK
Flooding
www.linux520.com
�















 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc