Netmanias Technical Document: LTE Security II - NAS and AS Security
www.nmcgroups.com
LTE Security II
- NAS and AS Security -
October 14, 2014
(Initial Release: August 21, 2012)
NMC Consulting Group (tech@netmanias.com)
www.netmanias.com
www.nmcgroups.com
About NMC Consulting Group
NMC Consulting Group is an advanced and professional network consulting company, specializing in IP network areas (e.g., FTTH, Metro Ethernet and IP/MPLS), service areas (e.g., IPTV, IMS and CDN), and wireless network areas
(e.g., Mobile WiMAX, LTE and Wi-Fi) since 2002.
Copyright © 2002-2014 NMC Consulting Group. All rights reserved.
�
Netmanias Technical Document: LTE Security II - NAS and AS Security
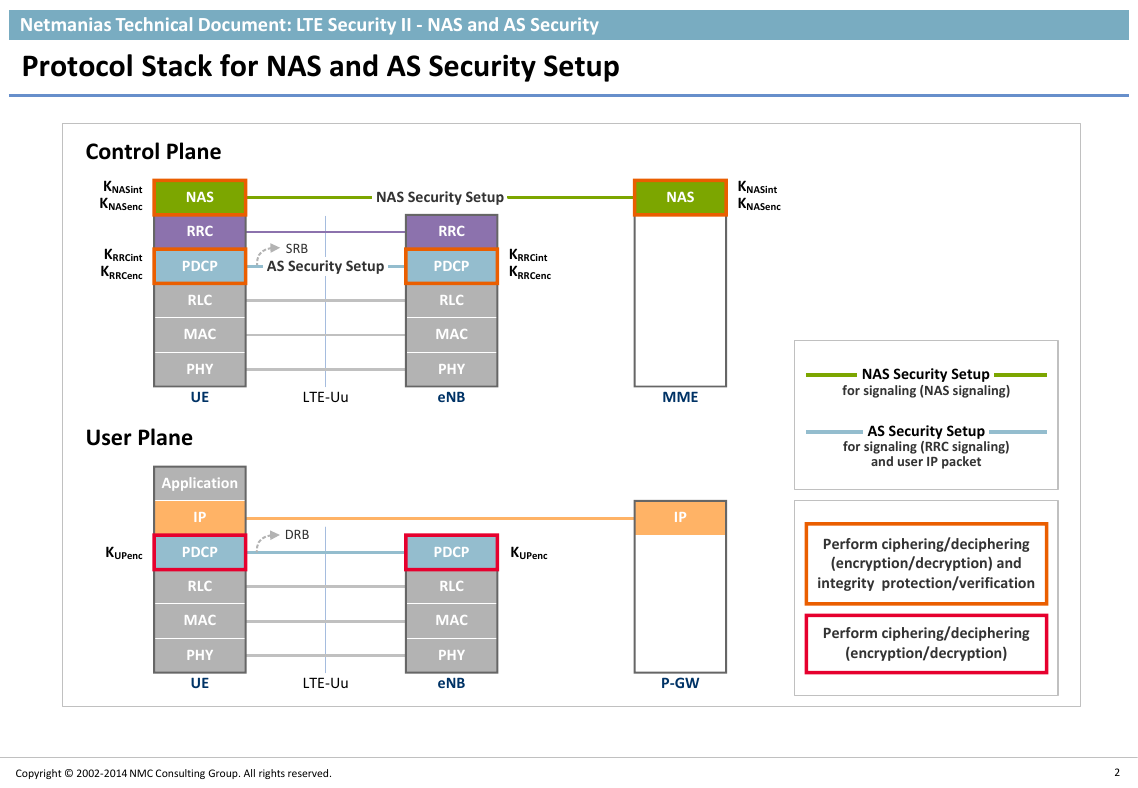
Protocol Stack for NAS and AS Security Setup
Copyright © 2002-2014 NMC Consulting Group. All rights reserved.
2
xNAS Security SetupxxAS Security SetupxRRCNASRLCPDCPPHYRRCRLCPDCPPHYNASUEeNBMMELTE-UuMACMACApplicationIPRLCPDCPPHYRLCPDCPPHYUEeNBLTE-UuMACMACPerform ciphering/deciphering (encryption/decryption) and integrity protection/verificationKUPencKUPencKNASint User PlaneControl PlanePerform ciphering/deciphering (encryption/decryption) SRBIPDRBP-GWKNASencKNASint KNASencKRRCint KRRCencKRRCint KRRCencNAS Security Setup for signaling (NAS signaling)AS Security Setup for signaling (RRC signaling)and user IP packet�
Netmanias Technical Document: LTE Security II - NAS and AS Security
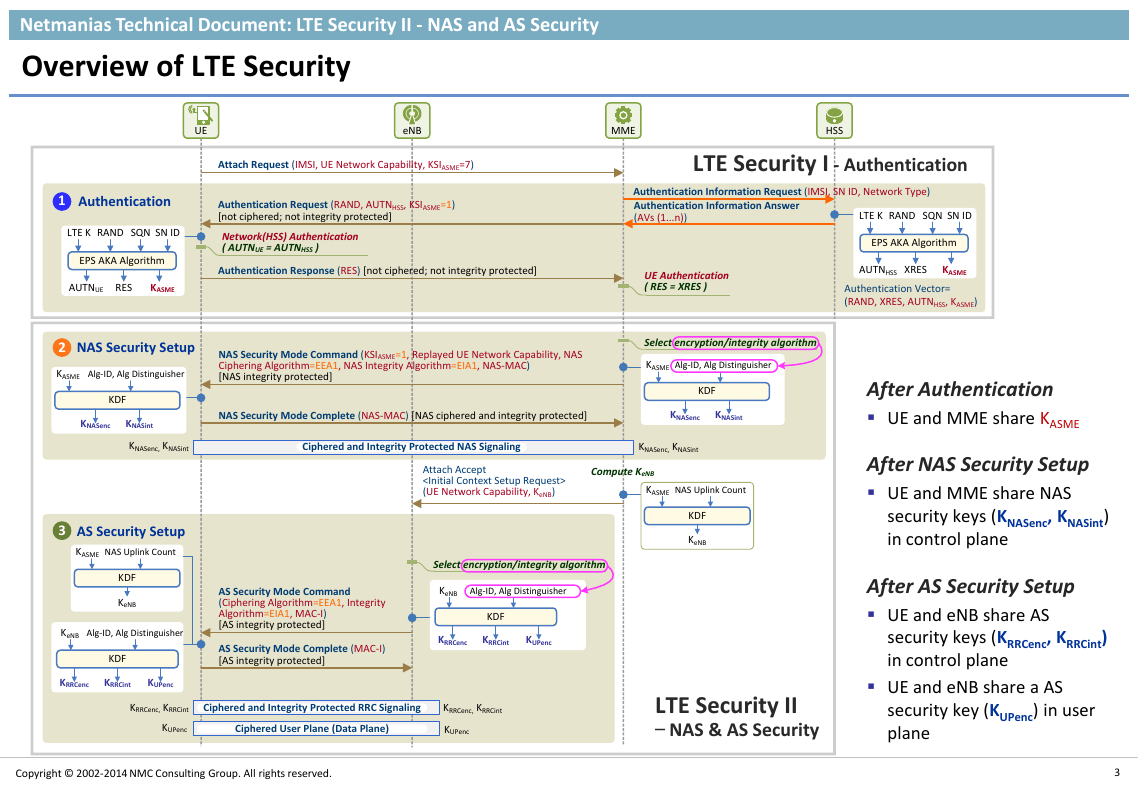
Overview of LTE Security
After Authentication
UE and MME share KASME
After NAS Security Setup
UE and MME share NAS
security keys (KNASenc, KNASint)
in control plane
After AS Security Setup
UE and eNB share AS
security keys (KRRCenc, KRRCint)
in control plane
UE and eNB share a AS
security key (KUPenc) in user
plane
Copyright © 2002-2014 NMC Consulting Group. All rights reserved.
3
Attach Request (IMSI, UE Network Capability, KSIASME=7)Authentication Information Request (IMSI, SN ID, Network Type)Authentication Information Answer (AVs (1...n))Authentication Request (RAND, AUTNHSS, KSIASME=1) [not ciphered; not integrity protected]Authentication Response (RES) [not ciphered; not integrity protected]AS Security Mode Complete (MAC-I)[AS integrity protected]AS Security Mode Command(Ciphering Algorithm=EEA1, Integrity Algorithm=EIA1, MAC-I)[AS integrity protected]Attach Accept(UE Network Capability, KeNB)NAS Security Mode Command (KSIASME=1, Replayed UE Network Capability, NAS Ciphering Algorithm=EEA1, NAS Integrity Algorithm=EIA1, NAS-MAC)[NAS integrity protected]NAS Security Mode Complete (NAS-MAC) [NAS ciphered and integrity protected]Network(HSS) Authentication( AUTNUE = AUTNHSS )UE Authentication( RES = XRES )AuthenticationNAS Security SetupAS Security SetupCiphered and Integrity Protected NAS SignalingCompute KeNBCiphered and Integrity Protected RRC SignalingCiphered User Plane (Data Plane)KNASenc, KNASint KRRCenc, KRRCintKUPencKRRCenc, KRRCintKUPenceNBUEMMEHSS123LTE KRANDEPS AKA AlgorithmAUTNUERESKASMESQNSN IDLTE KRANDEPS AKA AlgorithmAUTNHSSXRESKASMESQNSN IDAuthentication Vector=(RAND, XRES, AUTNHSS, KASME)Select encryption/integrity algorithmKNASencKASMEKDFKNASintAlg-ID, Alg DistinguisherKNASenc, KNASint NAS Uplink CountKeNBKASMEKDFAlg-ID, Alg DistinguisherKRRCencKeNBKDFKRRCintKUPencSelect encryption/integrity algorithmNAS Uplink CountKeNBKASMEKDFKNASencKASMEKDFKNASintAlg-ID, Alg DistinguisherAlg-ID, Alg DistinguisherKRRCencKeNBKDFKRRCintKUPencLTE Security I - AuthenticationLTE Security II – NAS & AS Security�
Netmanias Technical Document: LTE Security II - NAS and AS Security
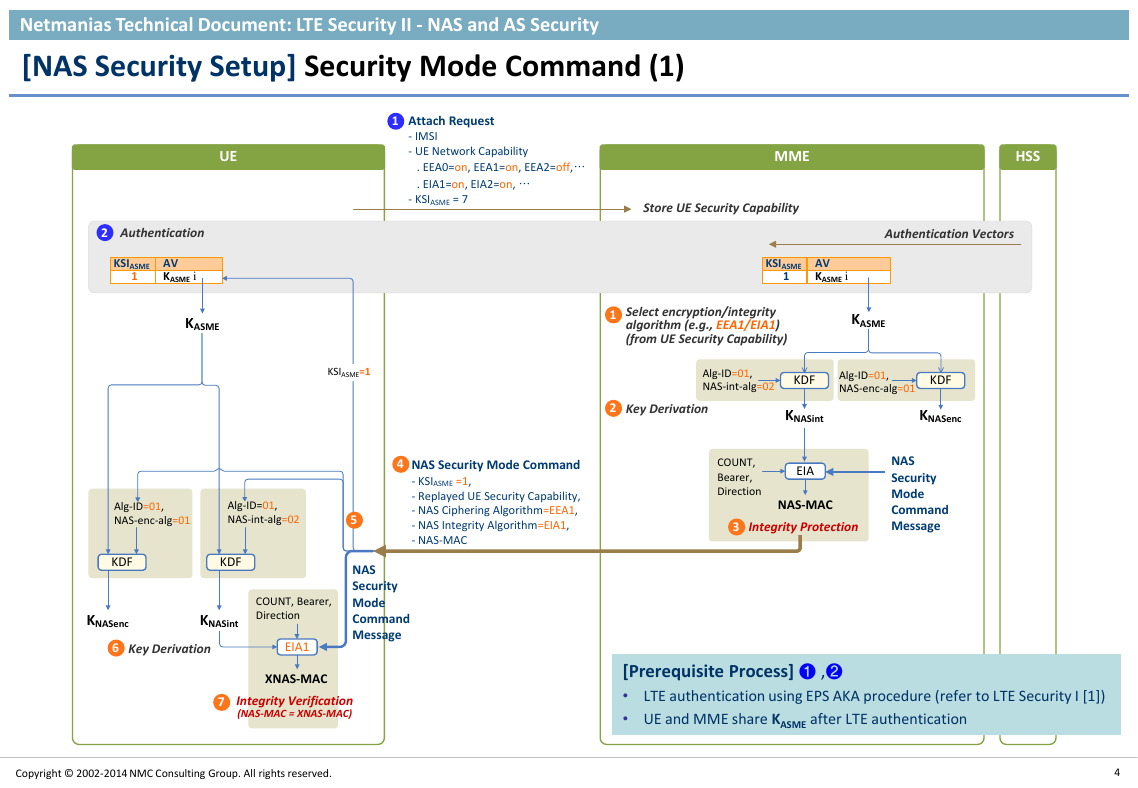
[NAS Security Setup] Security Mode Command (1)
Copyright © 2002-2014 NMC Consulting Group. All rights reserved.
4
[Prerequisite Process] ❶ ,❷
•
• UE and MME share KASME after LTE authentication
LTE authentication using EPS AKA procedure (refer to LTE Security I [1])
KASMEKNASencKNASintMMEAttach Request - IMSI- UE Network Capability . EEA0=on, EEA1=on, EEA2=off,… . EIA1=on, EIA2=on, … - KSIASME = 7Store UE Security CapabilityNAS Security Mode Command- KSIASME =1,- Replayed UE Security Capability,- NAS Ciphering Algorithm=EEA1,- NAS Integrity Algorithm=EIA1, - NAS-MACKDFKDFAlg-ID=01,NAS-int-alg=02EIANAS Security Mode Command MessageNAS-MACCOUNT,Bearer,DirectionIntegrity ProtectionSelect encryption/integrity algorithm (e.g., EEA1/EIA1)(from UE Security Capability)EIA1XNAS-MACIntegrity Verification (NAS-MAC = XNAS-MAC)KNASintKNASencCOUNT, Bearer,DirectionAlg-ID=01,NAS-enc-alg=01Alg-ID=01,NAS-int-alg=02KDFKDFKey Derivation1234Key DerivationAlg-ID=01,NAS-enc-alg=01KASME671UEMMEHSSKSIASMEAV1KASME iAuthenticationAuthentication Vectors KSIASMEAV1KASME i25KSIASME=1NAS Security Mode Command Message�
• KASME derived in ❷ (authentication process)
• Security algorithm ID selected in ❶
• Security algorithm distinguisher
KNASint = KDF (KASME, NAS-int-alg, Alg-ID)
KNASenc = KDF (KASME, NAS-enc-alg, Alg-ID)
Security Algorithm ID
Algorithm Distinguisher
Algorithm ID Description
128-EEA0
128-EEA1
128-EEA2
128-EEA3
128-EIA1
128-EIA2
128-EIA3
Null ciphering algorithm
SNOW 3G
AES
ZUC (optional)
SNOW 3G
AES
ZUC (optional)
Value
0000
0001
0010
0011
0001
0010
0011
Algorithm Distinguisher
NAS-enc-alg
NAS-int-alg
RRC-enc-alg
RRC-int-alg
UP-enc-alg
UP-int-alg*
Value
0x01
0x02
0x03
0x04
0x05
0x06
* for relay nodes only, not discussed herein
Netmanias Technical Document: LTE Security II - NAS and AS Security
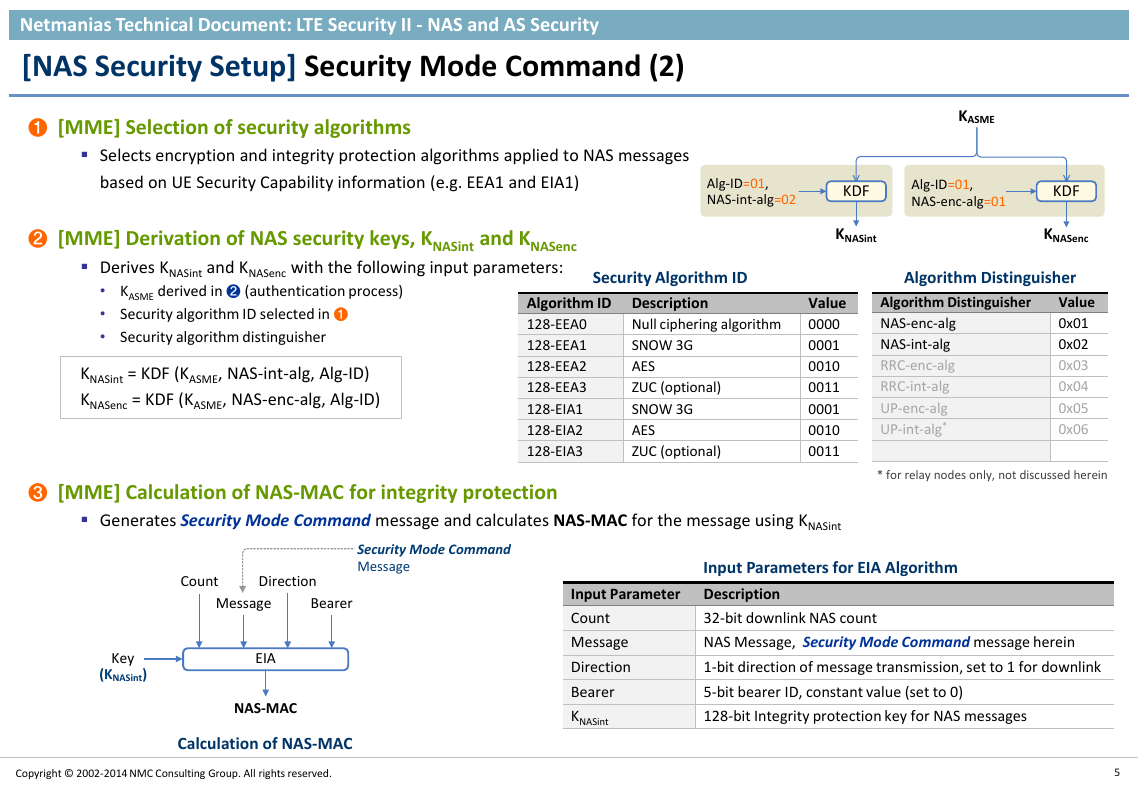
[NAS Security Setup] Security Mode Command (2)
❶ [MME] Selection of security algorithms
Selects encryption and integrity protection algorithms applied to NAS messages
based on UE Security Capability information (e.g. EEA1 and EIA1)
❷ [MME] Derivation of NAS security keys, KNASint and KNASenc
Derives KNASint and KNASenc with the following input parameters:
❸ [MME] Calculation of NAS-MAC for integrity protection
Generates Security Mode Command message and calculates NAS-MAC for the message using KNASint
Calculation of NAS-MAC
Copyright © 2002-2014 NMC Consulting Group. All rights reserved.
Input Parameters for EIA Algorithm
Input Parameter Description
Count
32-bit downlink NAS count
Message
Direction
Bearer
KNASint
NAS Message, Security Mode Command message herein
1-bit direction of message transmission, set to 1 for downlink
5-bit bearer ID, constant value (set to 0)
128-bit Integrity protection key for NAS messages
5
KASMEKNASencKNASintKDFKDFAlg-ID=01,NAS-int-alg=02Alg-ID=01,NAS-enc-alg=01EIANAS-MAC(KNASint)CountDirectionBearerKeyMessageSecurity Mode CommandMessage�
Netmanias Technical Document: LTE Security II - NAS and AS Security
[NAS Security Setup] Security Mode Command (3)
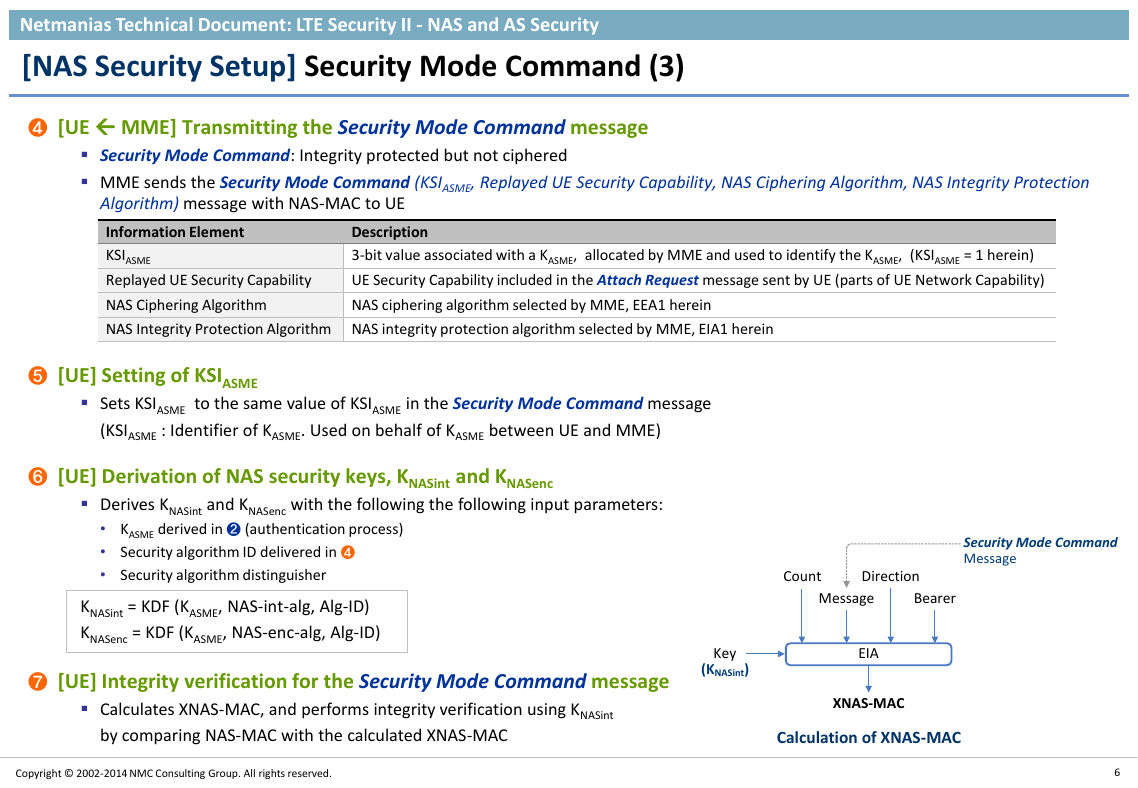
❹ [UE MME] Transmitting the Security Mode Command message
Security Mode Command: Integrity protected but not ciphered
MME sends the Security Mode Command (KSIASME, Replayed UE Security Capability, NAS Ciphering Algorithm, NAS Integrity Protection
Algorithm) message with NAS-MAC to UE
Information Element
KSIASME
Replayed UE Security Capability
Description
3-bit value associated with a KASME, allocated by MME and used to identify the KASME, (KSIASME = 1 herein)
UE Security Capability included in the Attach Request message sent by UE (parts of UE Network Capability)
NAS Ciphering Algorithm
NAS ciphering algorithm selected by MME, EEA1 herein
NAS Integrity Protection Algorithm NAS integrity protection algorithm selected by MME, EIA1 herein
❺ [UE] Setting of KSIASME
Sets KSIASME to the same value of KSIASME in the Security Mode Command message
(KSIASME : Identifier of KASME. Used on behalf of KASME between UE and MME)
❻ [UE] Derivation of NAS security keys, KNASint and KNASenc
Derives KNASint and KNASenc with the following the following input parameters:
• KASME derived in ❷ (authentication process)
• Security algorithm ID delivered in ❹
• Security algorithm distinguisher
KNASint = KDF (KASME, NAS-int-alg, Alg-ID)
KNASenc = KDF (KASME, NAS-enc-alg, Alg-ID)
❼ [UE] Integrity verification for the Security Mode Command message
Calculates XNAS-MAC, and performs integrity verification using KNASint
by comparing NAS-MAC with the calculated XNAS-MAC
Calculation of XNAS-MAC
Copyright © 2002-2014 NMC Consulting Group. All rights reserved.
6
EIAXNAS-MACCountDirectionBearerMessageSecurity Mode CommandMessage(KNASint)Key�
Netmanias Technical Document: LTE Security II - NAS and AS Security
[NAS Security Setup] Security Mode Complete (1)
Copyright © 2002-2014 NMC Consulting Group. All rights reserved.
7
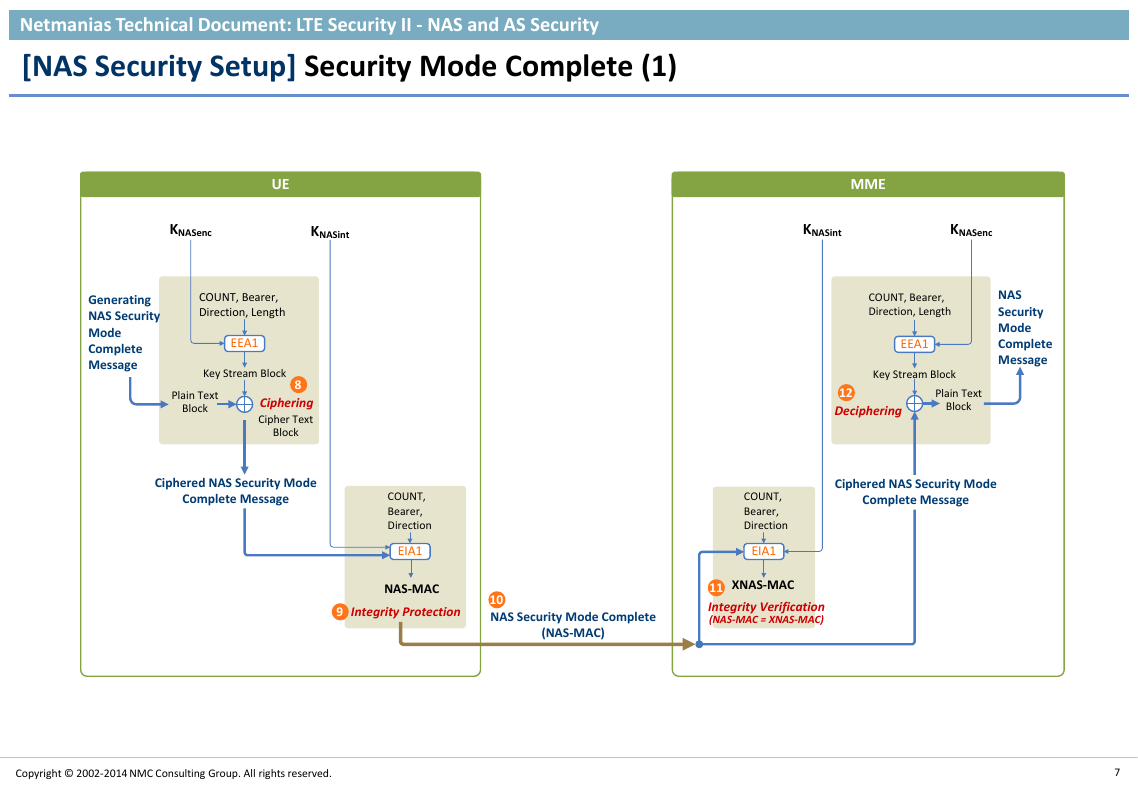
UEMMEGenerating NAS Security Mode Complete MessageEIA1NAS Security Mode Complete (NAS-MAC)EEA1Key Stream BlockPlain Text BlockCipher Text BlockCOUNT,Bearer,DirectionCOUNT, Bearer,Direction, LengthCipheringIntegrity ProtectionNAS-MACCiphered NAS Security Mode Complete MessageKNASintKNASencCOUNT,Bearer,DirectionXNAS-MACEEA1Key Stream BlockPlain Text BlockEIA1DecipheringKNASintKNASencNAS Security Mode Complete MessageCOUNT, Bearer,Direction, LengthCiphered NAS Security Mode Complete MessageIntegrity Verification (NAS-MAC = XNAS-MAC)89101211�
Netmanias Technical Document: LTE Security II - NAS and AS Security
[NAS Security Setup] Security Mode Complete (2)
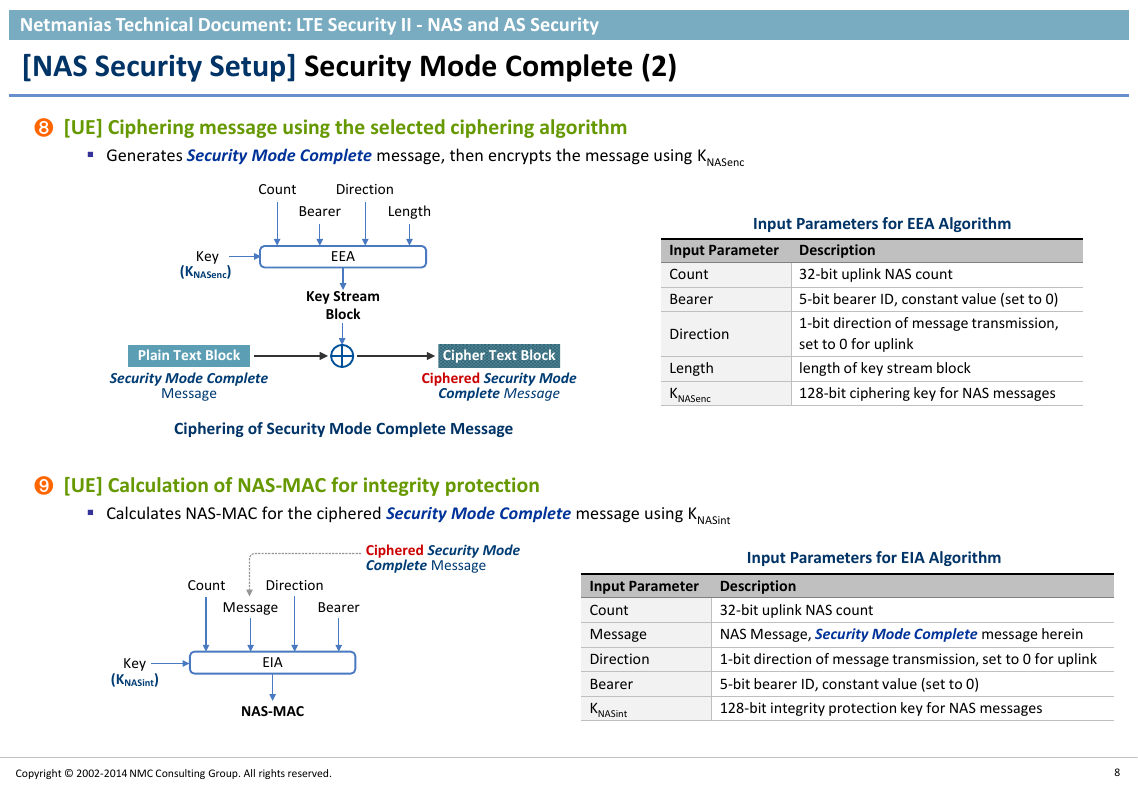
❽ [UE] Ciphering message using the selected ciphering algorithm
Generates Security Mode Complete message, then encrypts the message using KNASenc
Ciphering of Security Mode Complete Message
Input Parameters for EEA Algorithm
Input Parameter Description
Count
32-bit uplink NAS count
Bearer
5-bit bearer ID, constant value (set to 0)
Direction
Length
KNASenc
1-bit direction of message transmission,
set to 0 for uplink
length of key stream block
128-bit ciphering key for NAS messages
❾ [UE] Calculation of NAS-MAC for integrity protection
Calculates NAS-MAC for the ciphered Security Mode Complete message using KNASint
Input Parameters for EIA Algorithm
Input Parameter Description
Count
32-bit uplink NAS count
Message
Direction
Bearer
KNASint
NAS Message, Security Mode Complete message herein
1-bit direction of message transmission, set to 0 for uplink
5-bit bearer ID, constant value (set to 0)
128-bit integrity protection key for NAS messages
Copyright © 2002-2014 NMC Consulting Group. All rights reserved.
8
EEAKey Stream BlockSecurity Mode Complete Message(KNASenc)CountBearerDirectionLengthKeyCiphered Security Mode Complete MessagePlain Text BlockCipher Text BlockEIANAS-MACCountDirectionBearerMessage(KNASint)KeyCiphered Security Mode Complete Message�









 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc