9/1/2017
1 - 120 / 120
CSTA K-12 Computer Science Standards - Revised 2017
Identifier
Grades
Standard
Concept
Subconcept
Practice(s)
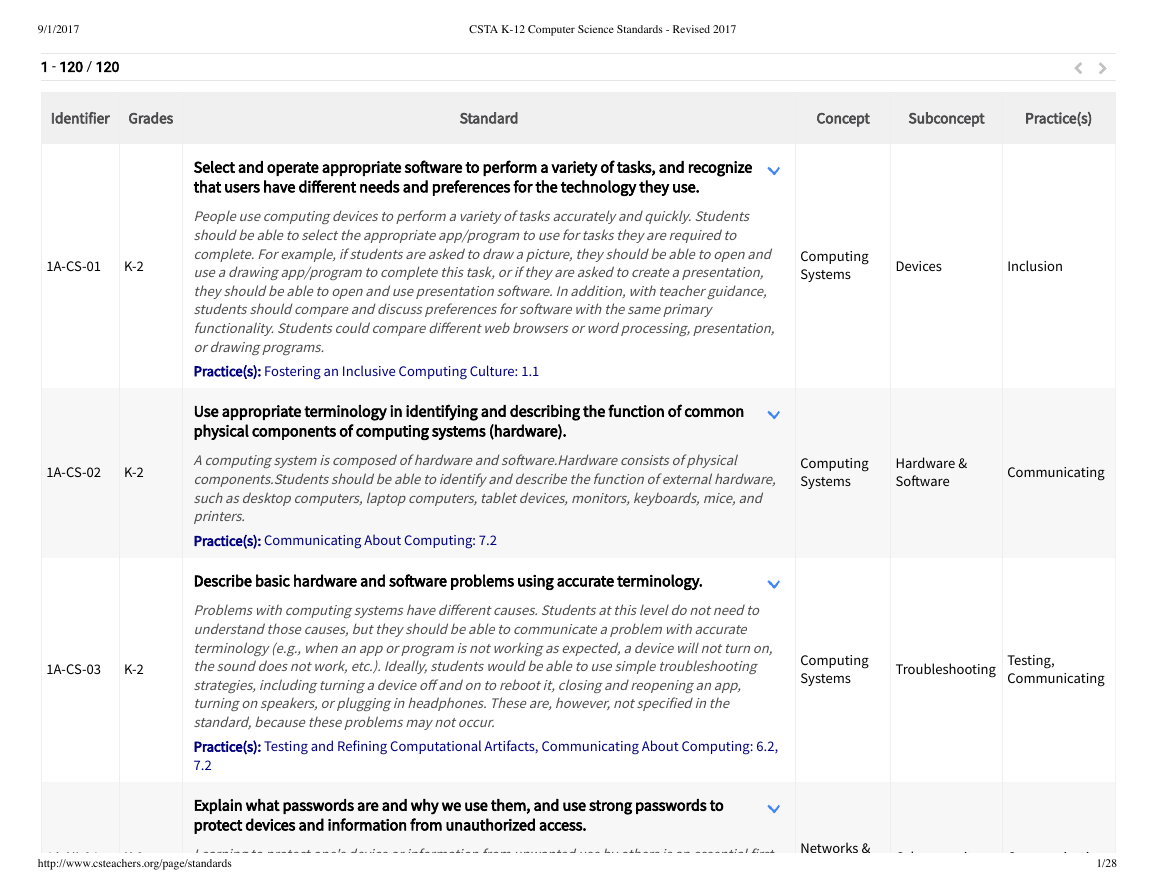
1A-CS-01
K-2
1A-CS-02
K-2
1A-CS-03
K-2
Select and operate appropriate so�ware to perform a variety of tasks, and recognize
that users have di�erent needs and preferences for the technology they use.
People use computing devices to perform a variety of tasks accurately and quickly. Students
should be able to select the appropriate app/program to use for tasks they are required to
complete. For example, if students are asked to draw a picture, they should be able to open and
use a drawing app/program to complete this task, or if they are asked to create a presentation,
they should be able to open and use presentation so�ware. In addition, with teacher guidance,
students should compare and discuss preferences for so�ware with the same primary
functionality. Students could compare di�erent web browsers or word processing, presentation,
or drawing programs.
Practice(s): Fostering an Inclusive Computing Culture: 1.1
Use appropriate terminology in identifying and describing the function of common
physical components of computing systems (hardware).
A computing system is composed of hardware and so�ware.Hardware consists of physical
components.Students should be able to identify and describe the function of external hardware,
such as desktop computers, laptop computers, tablet devices, monitors, keyboards, mice, and
printers.
Practice(s): Communicating About Computing: 7.2
Describe basic hardware and so�ware problems using accurate terminology.
Problems with computing systems have di�erent causes. Students at this level do not need to
understand those causes, but they should be able to communicate a problem with accurate
terminology (e.g., when an app or program is not working as expected, a device will not turn on,
the sound does not work, etc.). Ideally, students would be able to use simple troubleshooting
strategies, including turning a device o� and on to reboot it, closing and reopening an app,
turning on speakers, or plugging in headphones. These are, however, not specified in the
standard, because these problems may not occur.
Practice(s): Testing and Refining Computational Artifacts, Communicating About Computing: 6.2,
7.2
Explain what passwords are and why we use them, and use strong passwords to
protect devices and information from unauthorized access.
1A-NI-04
http://www.csteachers.org/page/standards
K-2
Learning to protect one's device or information from unwanted use by others is an essential first
Computing
Systems
Devices
Inclusion
Computing
Systems
Hardware &
So�ware
Communicating
Computing
Systems
Troubleshooting
Testing,
Communicating
Networks &
Cybersecurity
Communicating
1/28
�
9/1/2017
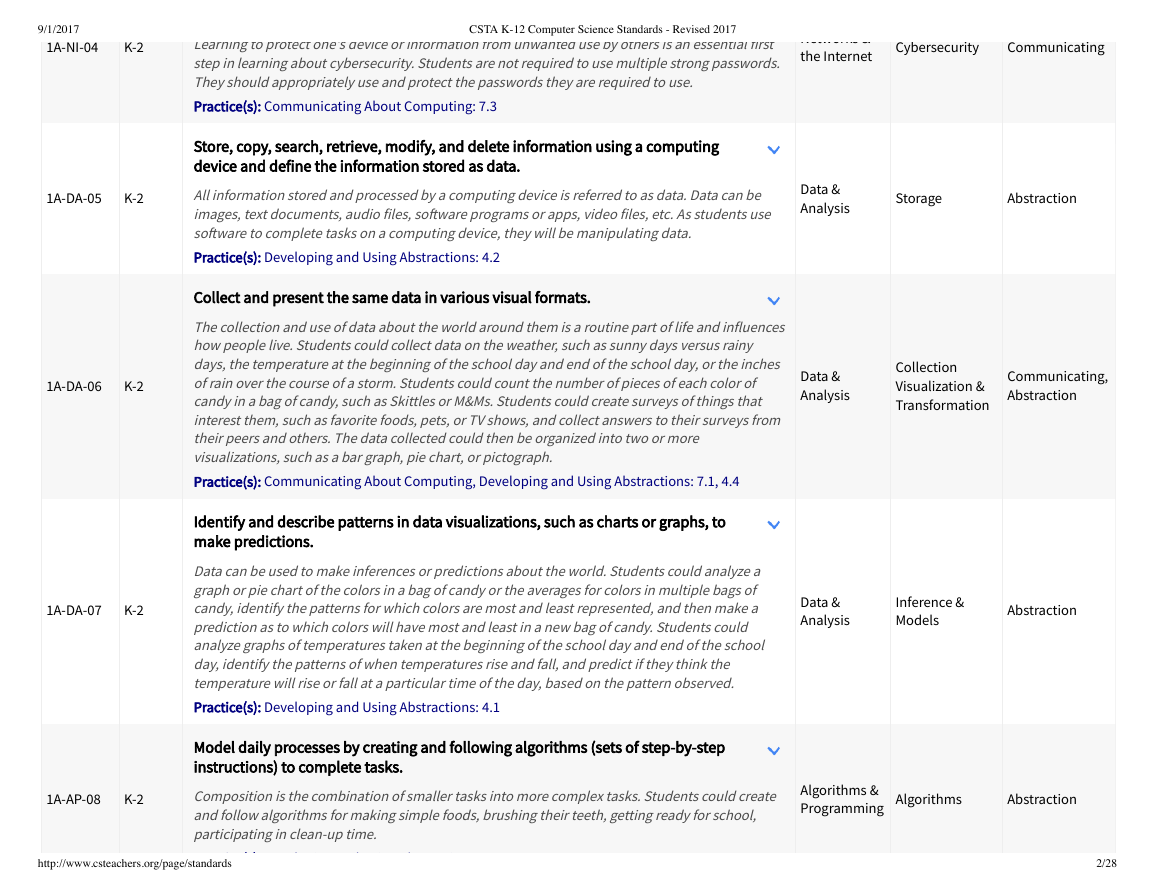
1A-NI-04
K-2
CSTA K-12 Computer Science Standards - Revised 2017
Learning to protect one's device or information from unwanted use by others is an essential first
step in learning about cybersecurity. Students are not required to use multiple strong passwords.
They should appropriately use and protect the passwords they are required to use.
Practice(s): Communicating About Computing: 7.3
Networks &
the Internet
Cybersecurity
Communicating
Store, copy, search, retrieve, modify, and delete information using a computing
device and define the information stored as data.
All information stored and processed by a computing device is referred to as data. Data can be
images, text documents, audio files, so�ware programs or apps, video files, etc. As students use
so�ware to complete tasks on a computing device, they will be manipulating data.
Practice(s): Developing and Using Abstractions: 4.2
Collect and present the same data in various visual formats.
The collection and use of data about the world around them is a routine part of life and influences
how people live. Students could collect data on the weather, such as sunny days versus rainy
days, the temperature at the beginning of the school day and end of the school day, or the inches
of rain over the course of a storm. Students could count the number of pieces of each color of
candy in a bag of candy, such as Skittles or M&Ms. Students could create surveys of things that
interest them, such as favorite foods, pets, or TV shows, and collect answers to their surveys from
their peers and others. The data collected could then be organized into two or more
visualizations, such as a bar graph, pie chart, or pictograph.
Practice(s): Communicating About Computing, Developing and Using Abstractions: 7.1, 4.4
Identify and describe patterns in data visualizations, such as charts or graphs, to
make predictions.
Data can be used to make inferences or predictions about the world. Students could analyze a
graph or pie chart of the colors in a bag of candy or the averages for colors in multiple bags of
candy, identify the patterns for which colors are most and least represented, and then make a
prediction as to which colors will have most and least in a new bag of candy. Students could
analyze graphs of temperatures taken at the beginning of the school day and end of the school
day, identify the patterns of when temperatures rise and fall, and predict if they think the
temperature will rise or fall at a particular time of the day, based on the pattern observed.
Practice(s): Developing and Using Abstractions: 4.1
Model daily processes by creating and following algorithms (sets of step-by-step
instructions) to complete tasks.
Composition is the combination of smaller tasks into more complex tasks. Students could create
and follow algorithms for making simple foods, brushing their teeth, getting ready for school,
participating in clean-up time.
Practice(s): Developing and Using Abstractions: 4.4
1A-DA-05
K-2
1A-DA-06
K-2
1A-DA-07
K-2
1A-AP-08
K-2
http://www.csteachers.org/page/standards
Data &
Analysis
Storage
Abstraction
Data &
Analysis
Collection
Visualization &
Transformation
Communicating,
Abstraction
Data &
Analysis
Inference &
Models
Abstraction
Algorithms &
Programming
Algorithms
Abstraction
2/28
�
9/1/2017
CSTA K-12 Computer Science Standards - Revised 2017
Practice(s): Developing and Using Abstractions: 4.4
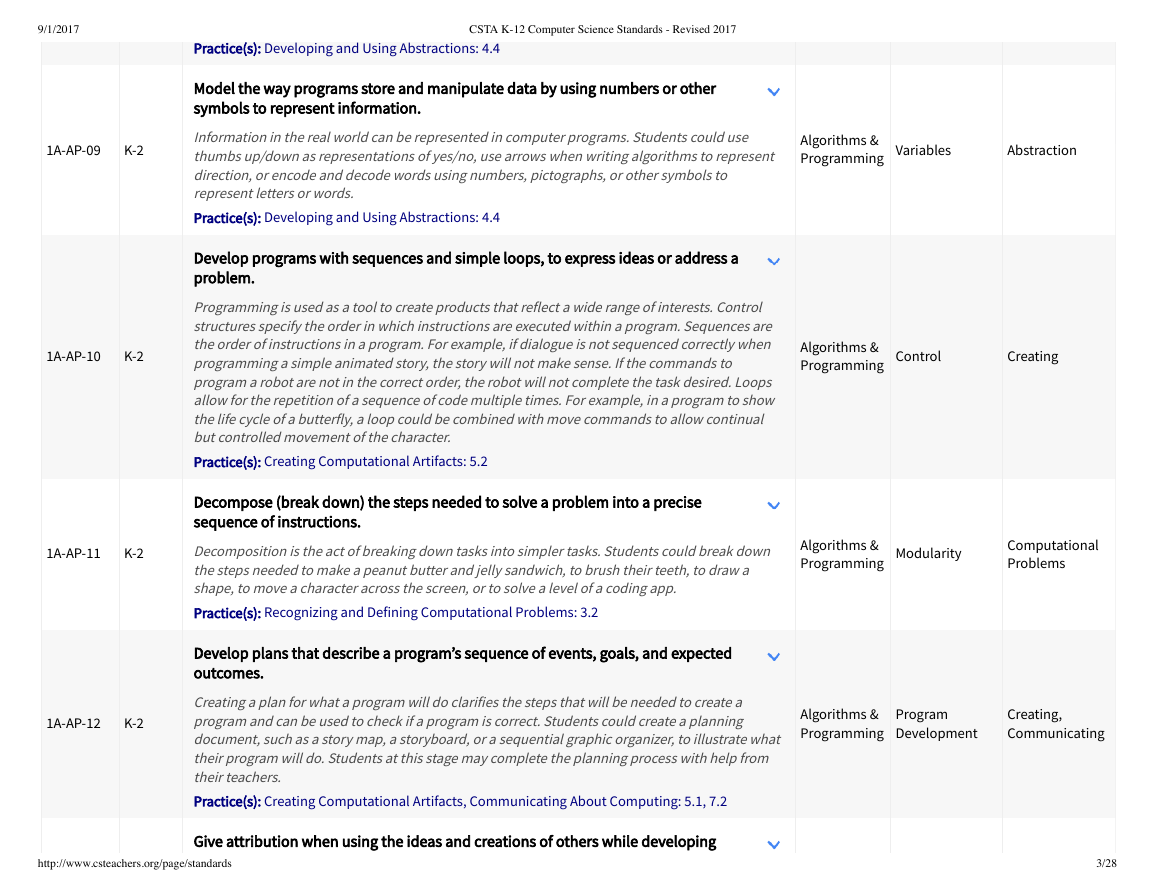
1A-AP-09
K-2
1A-AP-10
K-2
1A-AP-11
K-2
1A-AP-12
K-2
Model the way programs store and manipulate data by using numbers or other
symbols to represent information.
Information in the real world can be represented in computer programs. Students could use
thumbs up/down as representations of yes/no, use arrows when writing algorithms to represent
direction, or encode and decode words using numbers, pictographs, or other symbols to
represent letters or words.
Practice(s): Developing and Using Abstractions: 4.4
Develop programs with sequences and simple loops, to express ideas or address a
problem.
Programming is used as a tool to create products that reflect a wide range of interests. Control
structures specify the order in which instructions are executed within a program. Sequences are
the order of instructions in a program. For example, if dialogue is not sequenced correctly when
programming a simple animated story, the story will not make sense. If the commands to
program a robot are not in the correct order, the robot will not complete the task desired. Loops
allow for the repetition of a sequence of code multiple times. For example, in a program to show
the life cycle of a butterfly, a loop could be combined with move commands to allow continual
but controlled movement of the character.
Practice(s): Creating Computational Artifacts: 5.2
Decompose (break down) the steps needed to solve a problem into a precise
sequence of instructions.
Decomposition is the act of breaking down tasks into simpler tasks. Students could break down
the steps needed to make a peanut butter and jelly sandwich, to brush their teeth, to draw a
shape, to move a character across the screen, or to solve a level of a coding app.
Practice(s): Recognizing and Defining Computational Problems: 3.2
Develop plans that describe a program’s sequence of events, goals, and expected
outcomes.
Creating a plan for what a program will do clarifies the steps that will be needed to create a
program and can be used to check if a program is correct. Students could create a planning
document, such as a story map, a storyboard, or a sequential graphic organizer, to illustrate what
their program will do. Students at this stage may complete the planning process with help from
their teachers.
Practice(s): Creating Computational Artifacts, Communicating About Computing: 5.1, 7.2
Algorithms &
Programming Variables
Abstraction
Algorithms &
Programming Control
Creating
Algorithms &
Programming
Modularity
Computational
Problems
Algorithms &
Programming
Program
Development
Creating,
Communicating
http://www.csteachers.org/page/standards
Give attribution when using the ideas and creations of others while developing
programs.
3/28
�
9/1/2017
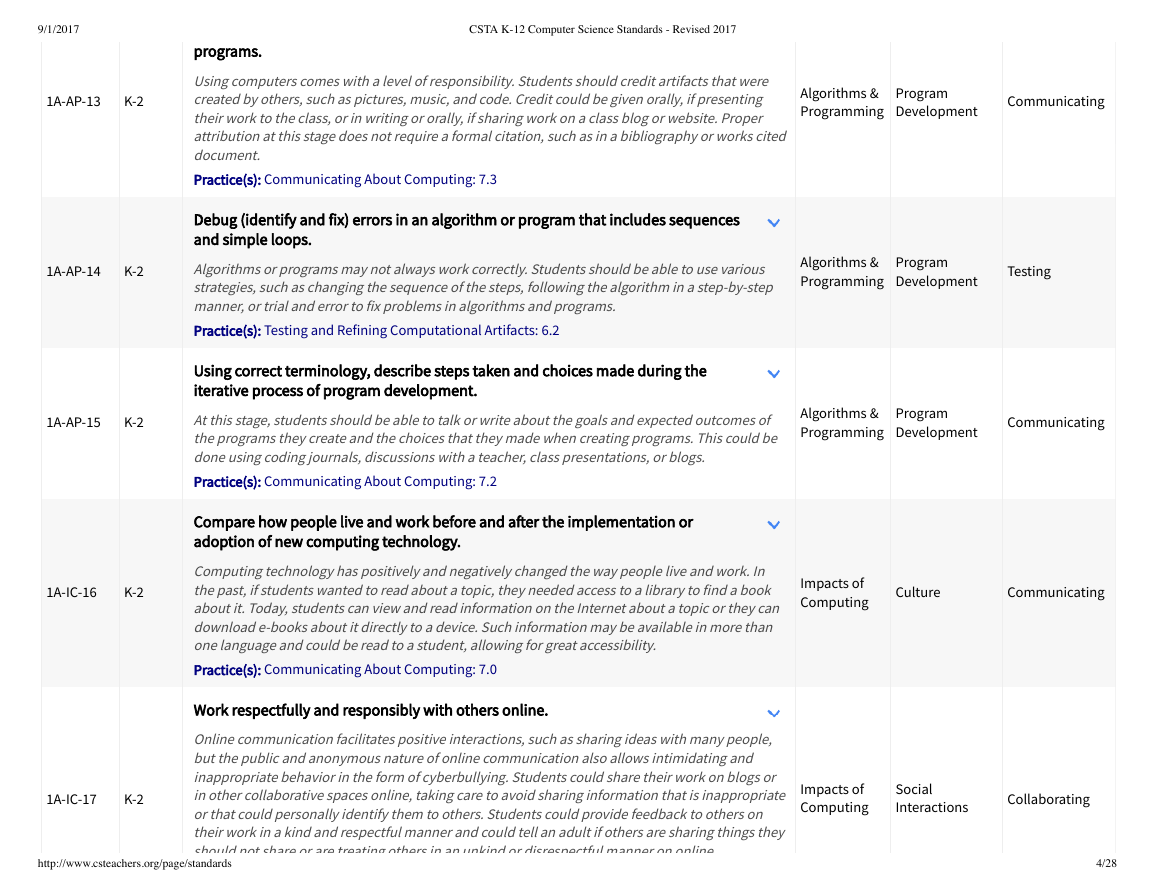
1A-AP-13
K-2
1A-AP-14
K-2
1A-AP-15
K-2
1A-IC-16
K-2
1A-IC-17
K-2
http://www.csteachers.org/page/standards
CSTA K-12 Computer Science Standards - Revised 2017
programs.
Using computers comes with a level of responsibility. Students should credit artifacts that were
created by others, such as pictures, music, and code. Credit could be given orally, if presenting
their work to the class, or in writing or orally, if sharing work on a class blog or website. Proper
attribution at this stage does not require a formal citation, such as in a bibliography or works cited
document.
Practice(s): Communicating About Computing: 7.3
Debug (identify and fix) errors in an algorithm or program that includes sequences
and simple loops.
Algorithms or programs may not always work correctly. Students should be able to use various
strategies, such as changing the sequence of the steps, following the algorithm in a step-by-step
manner, or trial and error to fix problems in algorithms and programs.
Practice(s): Testing and Refining Computational Artifacts: 6.2
Using correct terminology, describe steps taken and choices made during the
iterative process of program development.
At this stage, students should be able to talk or write about the goals and expected outcomes of
the programs they create and the choices that they made when creating programs. This could be
done using coding journals, discussions with a teacher, class presentations, or blogs.
Practice(s): Communicating About Computing: 7.2
Compare how people live and work before and a�er the implementation or
adoption of new computing technology.
Computing technology has positively and negatively changed the way people live and work. In
the past, if students wanted to read about a topic, they needed access to a library to find a book
about it. Today, students can view and read information on the Internet about a topic or they can
download e-books about it directly to a device. Such information may be available in more than
one language and could be read to a student, allowing for great accessibility.
Practice(s): Communicating About Computing: 7.0
Work respectfully and responsibly with others online.
Online communication facilitates positive interactions, such as sharing ideas with many people,
but the public and anonymous nature of online communication also allows intimidating and
inappropriate behavior in the form of cyberbullying. Students could share their work on blogs or
in other collaborative spaces online, taking care to avoid sharing information that is inappropriate
or that could personally identify them to others. Students could provide feedback to others on
their work in a kind and respectful manner and could tell an adult if others are sharing things they
should not share or are treating others in an unkind or disrespectful manner on online
Algorithms &
Programming
Program
Development
Communicating
Algorithms &
Programming
Program
Development
Testing
Algorithms &
Programming
Program
Development
Communicating
Impacts of
Computing
Culture
Communicating
Impacts of
Computing
Social
Interactions
Collaborating
4/28
�
9/1/2017
should not share or are treating others in an unkind or disrespectful manner on online
collaborative spaces.
Practice(s): Collaborating Around Computing: 2.1
CSTA K-12 Computer Science Standards - Revised 2017
1A-IC-18
K-2
Keep login information private, and log o� of devices appropriately.
People use computing technology in ways that can help or hurt themselves or others. Harmful
behaviors, such as sharing private information and leaving public devices logged in should be
recognized and avoided.
Practice(s): Communicating About Computing: 7.3
1B-CS-01
3-5
1B-CS-02
3-5
1B-CS-03
3-5
Describe how internal and external parts of computing devices function to form a
system.
Computing devices o�en depend on other devices or components. For example, a robot depends
on a physically attached light sensor to detect changes in brightness, whereas the light sensor
depends on the robot for power. Keyboard input or a mouse click could cause an action to
happen or information to be displayed on a screen; this could only happen because the computer
has a processor to evaluate what is happening externally and produce corresponding responses.
Students should describe how devices and components interact using correct terminology.
Practice(s): Communicating About Computing: 7.2
Model how computer hardware and so�ware work together as a system to
accomplish tasks.
In order for a person to accomplish tasks with a computer, both hardware and so�ware are
needed. At this stage, a model should only include the basic elements of a computer system, such
as input, output, processor, sensors, and storage. Students could draw a model on paper or in a
drawing program, program an animation to demonstrate it, or demonstrate it by acting this out in
some way.
Practice(s): Developing and Using Abstractions: 4.4
Determine potential solutions to solve simple hardware and so�ware problems
using common troubleshooting strategies.
Although computing systems may vary, common troubleshooting strategies can be used on all of
them. Students should be able to identify solutions to problems such as the device not
responding, no power, no network, app crashing, no sound, or password entry not working.
Should errors occur at school, the goal would be that students would use various strategies, such
as rebooting the device, checking for power, checking network availability, closing and reopening
an app, making sure speakers are turned on or headphones are plugged in, and making sure that
the caps lock key is not on, to solve these problems, when possible.
Practice(s): Testing and Refining Computational Artifacts: 6.2
Impacts of
Computing
Safety Law &
Ethics
Communicating
Computing
Systems
Devices
Communicating
Computing
Systems
Hardware &
So�ware
Abstraction
Computing
Systems
Troubleshooting Testing
http://www.csteachers.org/page/standards
5/28
�
9/1/2017
CSTA K-12 Computer Science Standards - Revised 2017
1B-NI-04
3-5
1B-NI-05
3-5
1B-DA-06
3-5
Model how information is broken down into smaller pieces, transmitted as packets
through multiple devices over networks and the Internet, and reassembled at the
destination.
Information is sent and received over physical or wireless paths. It is broken down into smaller
pieces called packets, which are sent independently and reassembled at the destination.
Students should demonstrate their understanding of this flow of information by, for instance,
drawing a model of the way packets are transmitted, programming an animation to show how
packets are transmitted, or demonstrating this through an unplugged activity which has them act
it out in some way.
Practice(s): Developing and Using Abstractions: 4.4
Discuss real-world cybersecurity problems and how personal information can be
protected.
Just as we protect our personal property o�line, we also need to protect our devices and the
information stored on them. Information can be protected using various security measures. These
measures can be physical and/or digital. Students could discuss or use a journaling or blogging
activity to explain, orally or in writing, about topics that relate to personal cybersecurity issues.
Discussion topics could be based on current events related to cybersecurity or topics that are
applicable to students, such as the necessity of backing up data to guard against loss, how to
create strong passwords and the importance of not sharing passwords, or why we should install
and keep anti-virus so�ware updated to protect data and systems.
Practice(s): Recognizing and Defining Computational Problems: 3.1
Organize and present collected data visually to highlight relationships and support a
claim.
Raw data has little meaning on its own. Data is o�en sorted or grouped to provide additional
clarity. Organizing data can make interpreting and communicating it to others easier. Data points
can be clustered by a number of commonalities. The same data could be manipulated in di�erent
ways to emphasize particular aspects or parts of the data set. For example, a data set of sports
teams could be sorted by wins, points scored, or points allowed, and a data set of weather
information could be sorted by high temperatures, low temperatures, or precipitation.
Practice(s): Communicating About Computing: 7.1
Use data to highlight or propose cause-and-e�ect relationships, predict outcomes,
or communicate an idea.
Networks &
the Internet
Network
Communication
& Organization
Abstraction
Networks &
the Internet
Cybersecurity
Computational
Problems
Data &
Analysis
Collection
Visualization &
Transformation
Communicating
The accuracy of data analysis is related to how realistically data is represented. Inferences or
predictions based on data are less likely to be accurate if the data is not su�icient or if the data is
incorrect in some way. Students should be able to refer to data when communicating an idea. For
example, in order to explore the relationship between speed, time, and distance, students could
http://www.csteachers.org/page/standards
6/28
�
9/1/2017
1B-DA-07
3-5
1B-AP-08
3-5
1B-AP-09
3-5
CSTA K-12 Computer Science Standards - Revised 2017
example, in order to explore the relationship between speed, time, and distance, students could
operate a robot at uniform speed, and at increasing time intervals to predict how far the robot
travels at that speed. In order to make an accurate prediction, one or two attempts of di�ering
times would not be enough. The robot may also collect temperature data from a sensor, but that
data would not be relevant for the task. Students must also make accurate measurements of the
distance the robot travels in order to develop a valid prediction. Students could record the
temperature at noon each day as a basis to show that temperatures are higher in certain months
of the year. If temperatures are not recorded on non-school days or are recorded incorrectly or at
di�erent times of the day, the data would be incomplete and the ideas being communicated
could be inaccurate. Students may also record the day of the week on which the data was
collected, but this would have no relevance to whether temperatures are higher or lower. In order
to have su�icient and accurate data on which to communicate the idea, students might want to
use data provided by a governmental weather agency.
Practice(s): Communicating About Computing: 7.1
Compare and refine multiple algorithms for the same task and determine which is
the most appropriate.
Di�erent algorithms can achieve the same result, though sometimes one algorithm might be
most appropriate for a specific situation. Students should be able to look at di�erent ways to
solve the same task and decide which would be the best solution. For example, students could
use a map and plan multiple algorithms to get from one point to another. They could look at
routes suggested by mapping so�ware and change the route to something that would be better,
based on which route is shortest or fastest or would avoid a problem. Students might compare
algorithms that describe how to get ready for school. Another example might be to write di�erent
algorithms to draw a regular polygon and determine which algorithm would be the easiest to
modify or repurpose to draw a di�erent polygon.
Practice(s): Testing and Refining Computational Artifacts, Recognizing and Defining
Computational Problems: 6.3
Create programs that use variables to store and modify data.
Variables are used to store and modify data. At this level, understanding how to use variables is
su�icient. For example, students may use mathematical operations to add to the score of a game
or subtract from the number of lives available in a game. The use of a variable as a countdown
timer is another example.
Practice(s): Creating Computational Artifacts: 5.2
Create programs that include sequences, events, loops, and conditionals.
Data &
Analysis
Inference &
Models
Communicating
Algorithms &
Programming Algorithms
Testing,
Computational
Problems
Algorithms &
Programming Variables
Creating
Control structures specify the order (sequence) in which instructions are executed within a
program and can be combined to support the creation of more complex programs. Events allow
portions of a program to run based on a specific action. For example, students could write a
program to explain the water cycle and when a specific component is clicked (event), the program
http://www.csteachers.org/page/standards
7/28
�
9/1/2017
1B-AP-10
3-5
1B-AP-11
3-5
1B-AP-12
3-5
1B-AP-13
3-5
1B-AP-14
3-5
http://www.csteachers.org/page/standards
CSTA K-12 Computer Science Standards - Revised 2017
program to explain the water cycle and when a specific component is clicked (event), the program
would show information about that part of the water cycle. Conditionals allow for the execution
of a portion of code in a program when a certain condition is true. For example, students could
write a math game that asks multiplication fact questions and then uses a conditional to check
whether or not the answer that was entered is correct. Loops allow for the repetition of a
sequence of code multiple times. For example, in a program that produces an animation about a
famous historical character, students could use a loop to have the character walk across the
screen as they introduce themselves.
Practice(s): Creating Computational Artifacts: 5.2
Decompose (break down) problems into smaller, manageable subproblems to
facilitate the program development process.
Decomposition is the act of breaking down tasks into simpler tasks. For example, students could
create an animation by separating a story into di�erent scenes. For each scene, they would select
a background, place characters, and program actions.
Practice(s): Recognizing and Defining Computational Problems: 3.2
Modify, remix, or incorporate portions of an existing program into one's own work,
to develop something new or add more advanced features.
Programs can be broken down into smaller parts, which can be incorporated into new or existing
programs. For example, students could modify prewritten code from a single-player game to
create a two-player game with slightly di�erent rules, remix and add another scene to an
animated story, use code to make a ball bounce from another program in a new basketball game,
or modify an image created by another student.
Practice(s): Creating Computational Artifacts: 5.3
Use an iterative process to plan the development of a program by including others'
perspectives and considering user preferences.
Planning is an important part of the iterative process of program development. Students outline
key features, time and resource constraints, and user expectations. Students should document
the plan as, for example, a storyboard, flowchart, pseudocode, or story map.
Practice(s): Fostering an Inclusive Computing Culture, Creating Computational Artifacts: 1.1, 5.1
Observe intellectual property rights and give appropriate attribution when creating
or remixing programs.
Intellectual property rights can vary by country but copyright laws give the creator of a work a set
of rights that prevents others from copying the work and using it in ways that they may not like.
Students should identify instances of remixing, when ideas are borrowed and iterated upon, and
credit the original creator. Students should also consider common licenses that place limitations
or restrictions on the use of computational artifacts, such as images and music downloaded from
Algorithms &
Programming
Control
Creating
Algorithms &
Programming
Modularity
Computational
Problems
Algorithms &
Programming
Modularity
Creating
Algorithms &
Programming
Program
Development
Inclusion,
Creating
Algorithms &
Programming
Program
Development
Creating,
Communicating
8/28
�








 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc