Professor Messer’s
CompTIA Security+
SY0-401 Study Guide
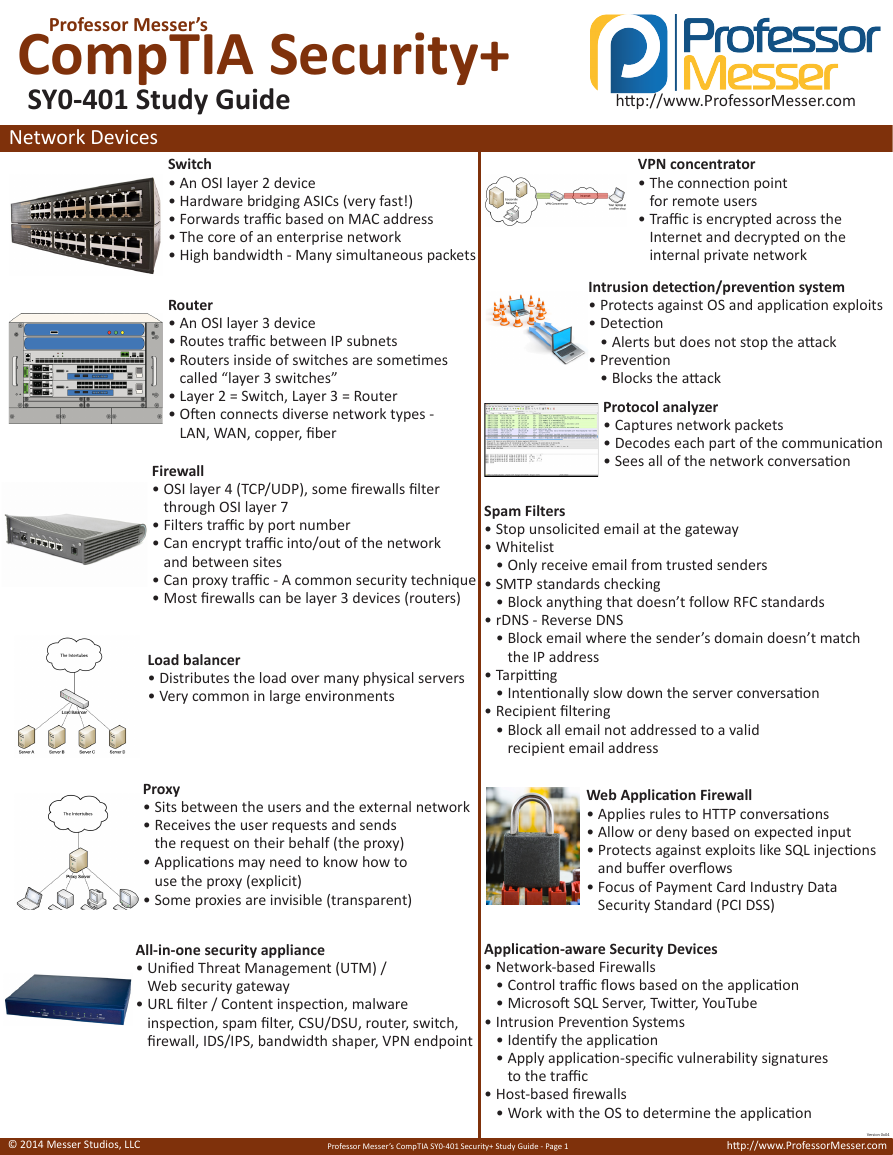
Network Devices
Switch
• An OSI layer 2 device
• Hardware bridging ASICs (very fast!)
• Forwards traffic based on MAC address
• The core of an enterprise network
• High bandwidth - Many simultaneous packets
http://www.ProfessorMesser.com
VPN concentrator
• The connection point
for remote users
• Traffic is encrypted across the
Internet and decrypted on the
internal private network
Router
• An OSI layer 3 device
• Routes traffic between IP subnets
• Routers inside of switches are sometimes
called “layer 3 switches”
• Layer 2 = Switch, Layer 3 = Router
• Often connects diverse network types -
LAN, WAN, copper, fiber
Firewall
• OSI layer 4 (TCP/UDP), some firewalls filter
through OSI layer 7
• Filters traffic by port number
• Can encrypt traffic into/out of the network
and between sites
• Can proxy traffic - A common security technique
• Most firewalls can be layer 3 devices (routers)
Load balancer
• Distributes the load over many physical servers
• Very common in large environments
Proxy
• Sits between the users and the external network
• Receives the user requests and sends
the request on their behalf (the proxy)
• Applications may need to know how to
use the proxy (explicit)
• Some proxies are invisible (transparent)
All-in-one security appliance
• Unified Threat Management (UTM) /
Web security gateway
• URL filter / Content inspection, malware
inspection, spam filter, CSU/DSU, router, switch,
firewall, IDS/IPS, bandwidth shaper, VPN endpoint
Intrusion detection/prevention system
• Protects against OS and application exploits
• Detection
• Alerts but does not stop the attack
• Prevention
• Blocks the attack
Protocol analyzer
• Captures network packets
• Decodes each part of the communication
• Sees all of the network conversation
Spam Filters
• Stop unsolicited email at the gateway
• Whitelist
• Only receive email from trusted senders
• SMTP standards checking
• Block anything that doesn’t follow RFC standards
• Block email where the sender’s domain doesn’t match
• rDNS - Reverse DNS
the IP address
• Tarpitting
• Recipient filtering
• Intentionally slow down the server conversation
• Block all email not addressed to a valid
recipient email address
Web Application Firewall
• Applies rules to HTTP conversations
• Allow or deny based on expected input
• Protects against exploits like SQL injections
and buffer overflows
• Focus of Payment Card Industry Data
Security Standard (PCI DSS)
Application-aware Security Devices
• Network-based Firewalls
• Control traffic flows based on the application
• Microsoft SQL Server, Twitter, YouTube
• Intrusion Prevention Systems
• Identify the application
• Apply application-specific vulnerability signatures
to the traffic
• Host-based firewalls
• Work with the OS to determine the application
© 2014 Messer Studios, LLC
Professor Messer’s CompTIA SY0-401 Security+ Study Guide - Page 1
http://www.ProfessorMesser.com
Version 0x04
�
Network Administration Principles
Configuring firewall rules
• Allow or disallow traffic based on security tuples
• Source IP, Destination IP, port number,
time of day, application, etc.
• Evaluated top-to-bottom
• There’s an implicit deny at the bottom
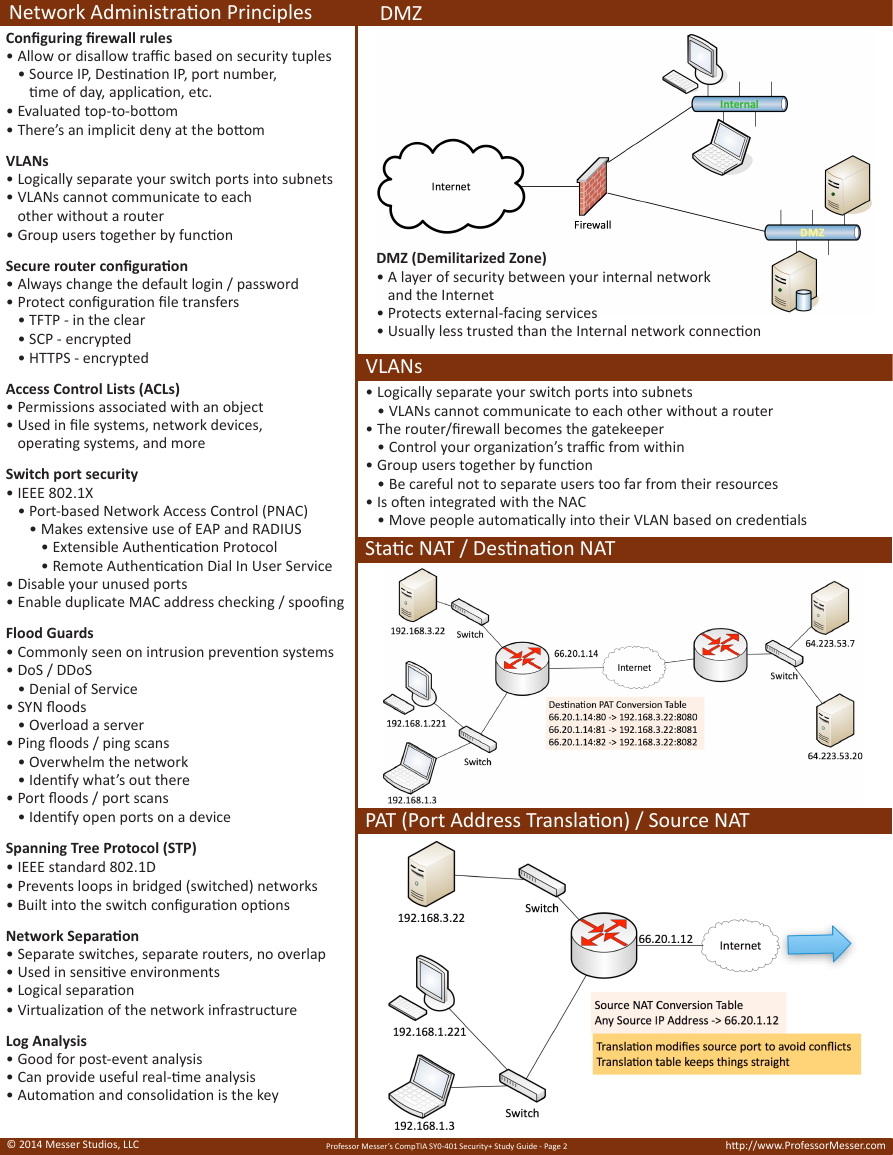
DMZ
VLANs
• Logically separate your switch ports into subnets
• VLANs cannot communicate to each
other without a router
• Group users together by function
Secure router configuration
• Always change the default login / password
• Protect configuration file transfers
• TFTP - in the clear
• SCP - encrypted
• HTTPS - encrypted
Access Control Lists (ACLs)
• Permissions associated with an object
• Used in file systems, network devices,
operating systems, and more
Switch port security
• IEEE 802.1X
• Port-based Network Access Control (PNAC)
• Makes extensive use of EAP and RADIUS
• Extensible Authentication Protocol
• Remote Authentication Dial In User Service
• Disable your unused ports
• Enable duplicate MAC address checking / spoofing
Flood Guards
• Commonly seen on intrusion prevention systems
• DoS / DDoS
• Denial of Service
• SYN floods
• Overload a server
• Ping floods / ping scans
• Overwhelm the network
• Identify what’s out there
• Port floods / port scans
• Identify open ports on a device
DMZ (Demilitarized Zone)
• A layer of security between your internal network
and the Internet
• Protects external-facing services
• Usually less trusted than the Internal network connection
VLANs
• Logically separate your switch ports into subnets
• VLANs cannot communicate to each other without a router
• The router/firewall becomes the gatekeeper
• Control your organization’s traffic from within
• Group users together by function
• Be careful not to separate users too far from their resources
• Is often integrated with the NAC
• Move people automatically into their VLAN based on credentials
Static NAT / Destination NAT
PAT (Port Address Translation) / Source NAT
Spanning Tree Protocol (STP)
• IEEE standard 802.1D
• Prevents loops in bridged (switched) networks
• Built into the switch configuration options
Network Separation
• Separate switches, separate routers, no overlap
• Used in sensitive environments
• Logical separation
• Virtualization of the network infrastructure
Log Analysis
• Good for post-event analysis
• Can provide useful real-time analysis
• Automation and consolidation is the key
© 2014 Messer Studios, LLC
Professor Messer’s CompTIA SY0-401 Security+ Study Guide - Page 2
http://www.ProfessorMesser.com
�
Network Design
Remote Access
• An important requirement
• We are increasingly mobile
• Take advantage of encryption technologies
• Keep everything private
• Consider adding additional authentication
technologies (One-time passwords)
• Constantly audit your access logs
Telephony
• One of the newest digital technologies
• And one of the most difficult to secure
• Firewalls generally don’t like VoIP technologies
• You’ll need protocol-specific application gateways
• Don’t forget your legacy telephony!
• Long distance still costs money
Network Access Control
• A complex technology
• But powerful when well engineered
• Very useful in large open environments
• Universities and large enterprises
• Requires a large security infrastructure
• Authentication is critical
• Redundancy is required
Virtualization
• Huge cost savings
• Security has to catch up to the speed of change
• The control of physical objects is gone
• Also difficult to apply external security components
• Requires additional insight
• Harder to view intra-server communication
• Take advantage of your logs
• They’ll tell you much more than you can see
Cloud Computing
Platform as a Service (PaaS)
• No servers, no software, no maintenance team
• No hardware of any kind
• Someone else handles the platform, you handle the product
• You don’t have direct control of the data, people, or infrastructure
• SalesForce.com is an example of PaaS
Software as a service (SaaS)
• On-demand software, no local installation
• Used for common business functions such as payroll services
• Data and applications are centrally managed
• Gmail and Google Docs is an example of SaaS
Infrastructure as a service (IaaS)
• Sometimes called Hardware as a Service (HaaS)
• Equipment is outsourced
• You are still responsible for the overall device and application management
• You’re also responsible for the security
• Your data is out there, but more within your control
• Web hosting and email services would be an example of IaaS
Cloud Deployment Models
• Private - A virtualized data center
• Public - Available to everyone over the Internet
• Hybrid - A mix of public and private
• Community - Several organizations share the same resources
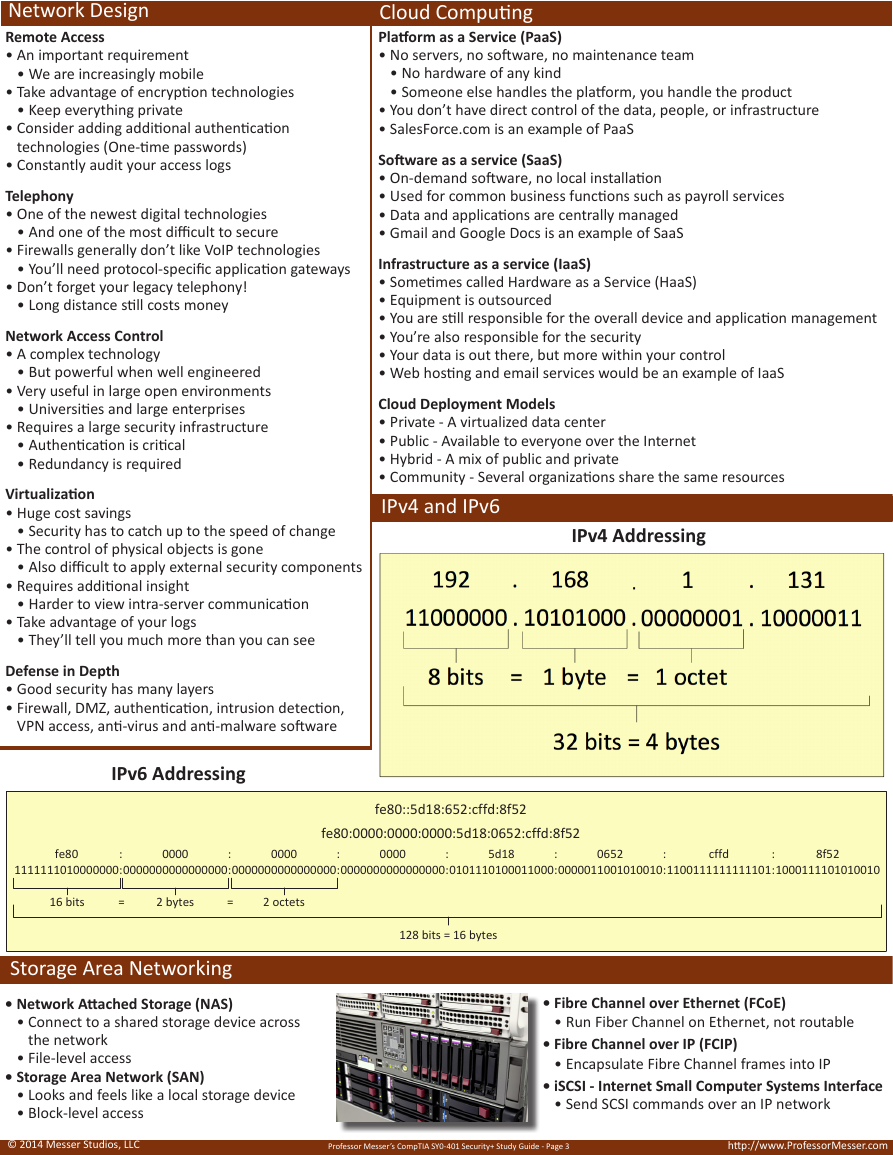
IPv4 and IPv6
IPv4 Addressing
Defense in Depth
• Good security has many layers
• Firewall, DMZ, authentication, intrusion detection,
VPN access, anti-virus and anti-malware software
IPv6 Addressing
fe80
1111111010000000
:
:
0000
0000000000000000
:
:
0000
0000000000000000
:
:
0000
0000000000000000
:
:
5d18
0101110100011000
:
:
0652
0000011001010010
:
:
cffd
1100111111111101
:
:
8f52
1000111101010010
fe80::5d18:652:cffd:8f52
fe80:0000:0000:0000:5d18:0652:cffd:8f52
16 bits
=
2 bytes
=
2 octets
128 bits = 16 bytes
Storage Area Networking
• Network Attached Storage (NAS)
• Connect to a shared storage device across
the network
• File-level access
• Storage Area Network (SAN)
• Looks and feels like a local storage device
• Block-level access
• Fibre Channel over Ethernet (FCoE)
• Run Fiber Channel on Ethernet, not routable
• Fibre Channel over IP (FCIP)
• Encapsulate Fibre Channel frames into IP
• iSCSI - Internet Small Computer Systems Interface
• Send SCSI commands over an IP network
© 2014 Messer Studios, LLC
Professor Messer’s CompTIA SY0-401 Security+ Study Guide - Page 3
http://www.ProfessorMesser.com
�
Ports and Protocols
Protocol
Port
Name
Descrip,on
FTP
SSH
SCP
SFTP
Telnet
DNS
TFTP
HTTP
tcp/20,+tcp/21
File+Transfer+Protocol
Sends+and+receives+files+between+systems
tcp/22
tcp/22
tcp/22
tcp/23
Secure+Shell
Secure+Copy
Secure+File+Transfer+Protocol
Telecommunica?on+Network
Encrypted+console+login
Rela?vely+simple+file+copy+over+SSH
SSH+file+transfer+with+file+management
Remote+console+login+to+network+devices
udp/53,+tcp/53
Domain+Name+Services
Convert+domain+names+to+IP+addresses
udp/69
tcp/80
Trivial+File+Transfer+Protocol
Hypertext+Transfer+Protocol
A+very+simple+file+transfer+applica?on
Web+server+communica?on
NetBIOS
udp/137,+udp/138
Network+Basic+Input/Output+System
NetBIOS+over+UDP+X+Name+service,+Datagram+service
tcp/139
tcp/143
udp/161
tcp/443
tcp/443
Network+Basic+Input/Output+System
NetBIOS+over+TCP+X+Session+service
Internet+Message+Access+Protocol
Retrieve+and+store+email
Simple+Network+Management+Protocol
Gather+sta?s?cs+and+manage+network+devices
Transport+Layer+Security+and+Secure+Sockets+Layer
Secure+protocols+for+web+browsing
Hypertext+Transfer+Protocol+Secure
Web+server+communica?on+with+encryp?on
tcp/990,+tcp/989
FTP+over+SSL
Adds+security+to+FTP+with+TLS/SSL
N/A
Various
Internet+Control+Message+Protocol
Management+protocol
Internet+Protocol+Security
Authen?ca?on,+integrity,+confiden?ality,+and+encryp?on
NetBIOS
IMAP
SNMP
TLS/SSL
HTTPS
FTPS
ICMP
IPsec
OSI Model
OSI Mnemonics
• Please Do Not Trust Sales Person’s Answers
• All People Seem To Need Data Processing
• Please Do Not Throw Sausage Pizza Away!
Layer&7&(&Applica.on
The$layer$we$see$+$Google$Mail,$Twi2er,$Facebook
Layer&6&(&Presenta.on
Encoding$and$encryp;on$(SSL$/$TLS)
Layer&5&(&Session
Communica;on$between$devices$(control$protocols,$tunneling$protocols)
Layer&4&(&Transport
The$"post$office"$layer$(TCP$segments,$UDP$datagrams)
Layer&3&(&Network
The$rou;ng$layer$(IP$addresses,$routers,$packets)
UDP
Layer&2&(&Data&Link
The$switching$layer$(frames,$MAC$addresses,$EUI+48,$EUI+64,$switches)
Layer&1&(&Physical
Signaling,$cabling,$connectors$(cables,$NICs,$hubs)
© 2014 Messer Studios, LLC
Professor Messer’s CompTIA SY0-401 Security+ Study Guide - Page 4
http://www.ProfessorMesser.com
�
Wireless Encryption and Authentication
EAP (Extensible Authentication Protocol)
• An authentication framework
• WPA and WPA2 use five EAP types as
authentication mechanisms
LEAP (Lightweight Extensible Authentication Protocol)
• Cisco proprietary
• Uses passwords only
• No detailed certificate management
• Based on MS-CHAP
(including MS-CHAP security shortcomings)
PEAP (Protected Extensible Authentication Protocol)
• Created by Cisco, Microsoft, and RSA Security
• Encapsulates EAP in a TLS tunnel
• Only one certificate needed, on the server
Wireless Security
Captive Portal
• Authentication to a network
• Common on wireless networks
• Access table recognizes a lack of authentication
• Redirects your web access to a captive portal page
• Username / password
• And additional authentication factors
• Once proper authentication is provided,
the web session continues
• Until the captive portal removes your access
Omnidirectional Antennas
• One of the most common
• Included on most access points
• Signal is evenly distributed on all sides
• Omni=all
• Good choice for most environments
• You need coverage in all directions
• No ability to focus the signal
• A different antenna will be required
Directional Antennas
• Focus the signal - Increased distances
• Send and receive in a single direction
• Focused transmission and listening
• Antenna performance is measured in dB
• Double power every 3dB of gain
WEP
• 64-bit or 128-bit key size
• Cryptographic vulnerabilties found in 2001
• WEP is no longer used
WPA
• Short-term workaround after WEP
• Used RC4 cipher as a TKIP (Temporal Key Integrity Protocol)
• TKIP has its own vulnerabilities
WPA2
• Replaced TKIP with CCMP (Counter Mode with Cipher Block Chaining
Message Authentication Code Protocol)
• Replaced RC4 with AES (Advanced Encryption Standard)
• WPA2 is the latest and most secure wireless encryption method
WPA2-Enterprise
• WPA2-Enterprise adds 802.1x
• RADIUS server authentication
MAC (Media Access Control) filtering
• Access is controlled through the physical hardware address
• It’s easy to find a working MAC addresses through wireless LAN analysis
• MAC addresses can be spoofed
• Security through obscurity
SSID (Service Set Identifier) Management
• The SSID is the name of the wireless network
• i.e., LINKSYS, DEFAULT, NETGEAR
• Change the SSID to something appropriate for its use
• The SSID broadcasts can be disabled
• You can still determine the SSID through wireless network analysis
• Security through obscurity
Temporal Key Integrity Protocol
• Created when WEP was broken
• We needed a stopgap to make 802.11 stronger
• Mixed the keys - Combines the secret root key with the IV
• Adds sequence counter - Prevents replay attacks
• 64-bit Message Integrity Check - Protects against tampering
• Used in WPA (Wi-Fi Protected Access) prior to the creation of WPA2
CCMP
• Counter Mode with Cipher Block Chaining
Message Authentication Code Protocol
• Replaced TKIP when WPA2 was published
• A more advanced security protocol
• Based on AES and uses a 128-bit key and a 128-bit block size
• Requires additional computing resources
• Data confidentiality - Only authorized parties can access the information
• Authentication - Provides proof of genuineness of the user
• Access control - Allow or disallow access to the network
Site Surveys
• Sample the existing wireless spectrum
• Identify existing access points
• Work around existing frequencies - layout and plan for interference
• Plan for ongoing site surveys - things will certainly change
VPN over Wireless Networks
• Wireless from your local coffee shop - no encryption
• Everyone around the coffee shop can see your traffic
• Exceptionally easy to capture your data
• Some of your data might be encrypted with HTTPS. Maybe.
• Protect all of your traffic with a VPN tunnel
• Yagi antenna - Very directional and high gain
• Parabolic antenna - Focus the signal to a single point
© 2014 Messer Studios, LLC
Professor Messer’s CompTIA SY0-401 Security+ Study Guide - Page 5
http://www.ProfessorMesser.com
�
Dealing with Risk
Control types
• Technical security controls
• Access control, audit and accountability,
identification and authentication,
system and communications protection
• Management security controls
• Security assessment and authorization, planning,
risk assessment, system and services acquisition,
program management
• Operational security controls
• Awareness and training, configuration management,
contingency planning, incident response, maintenance,
media protection, physical and environmental
protection, personnel security, system and
information integrity
False Postitives
• A report that isn’t true - a false alarm or mistaken identity
• IDS/IPS information - only as good as the signatures
• Workstation anti-virus - False positives can remove legit files
• Consider a second opinion - http://www.VirusTotal.com
False Negatives
• A report missed identifying something - no notification
• Malicious traffic got through your defenses
• It’s difficult to know when this happens - It’s completely silent
• Get catch/miss rates with industry tests - IPS, anti-virus
Security policies
• A set of policies that covers many areas of security
• Human resource policies
• Business policies
• Certificate policies
• Incident-response policies
Risk Calculation
• Annualized Rate of Occurrence (ARO)
• How likely is it that a hurricane will hit?
In Montana? In Florida?
• SLE (Single Loss Expectancy)
• What is the monetary loss if a single event occurs?
• Laptop stolen = $1,000
• ALE (Annual Loss Expectancy)
• ARO x SLE
• 7 laptops stolen a year (ARO) x $1,000 (SLE) = $7,000
• The business impact can be more than monetary
• Quantitative vs. qualitative
Quantitative Risk Assessment
• Assign a dollar value to risk
• Single Loss Expectancy (SLE) - How much loss for one event?
• Annual Loss Expectancy
• SLE x Annual Rate of Occurrence (ARO)
• Often difficult to calculate without historical reference
• How risky is a buffalo stampede?
Qualitative Risk Assessment
• Identify significant risk factors
• Ask opinions about the significance
• Display visually with traffic light grid or similar method
Threat Assessment
• Where are we vulnerable to threats?
• OS, applications, 3rd-party connections, Internet
• Constant vigilance
• New threats discovered all the time
• Old threats become popular again
Vulnerability Assessment
• Actively scan a network in search of vulnerabilities
• Known vulnerabilities
• Automated process
• For unknown vulnerabilities, consider input validation/fuzzing
• Can identify obvious and no-so-obvious vulnerabilities
• Lack of application/OS patches
• No anti-virus/anti-spyware
• Weak passwords
Vulnerabilities
• A flaw or weakness
• A door with a broken lock
• An operating system library that grants administrative access
• This doesn’t mean your system has been breached
• Someone first has to know about the vulnerability
• Some vulnerabilities were there, but previously unknown
• This is why we patch
• New vulnerabilities are identified all the time
Threat Vectors
• The path that the threat takes to the target
• Target: Your computer, mobile device, gaming system
• Email: Embedded links, attached files
• Web browser: Fake site, session hijack
• Wireless hotspot: Rogue access point
• Telephone: Social engineering
• USB flash drive: Auto-executing malware
• And many more…
Threat Probability
• Identify actual and potential threats
• Regardless of the probability
• Identify as many vulnerabilities as possible
• Check your OS, your services, and your applications
• Nobody said this would be easy
• Now you can calculate the likelihood of a successful exploit
• There’s no official formula here
• Different organizations will have different priorities
• Stop participating in high-risk activity
Deflecting Risk
• Risk-avoidance
• Risk transference
• Buy some insurance
• Risk acceptance
• Risk mitigation
• Decrease the risk level
• Risk deterrence
• A business decision; we’ll take the risk!
• Big dogs, security fences, warning signs
© 2014 Messer Studios, LLC
Professor Messer’s CompTIA SY0-401 Security+ Study Guide - Page 6
http://www.ProfessorMesser.com
�
Dealing with Risk (continued)
Risks with Cloud Computing
• Control of data
• Data in the cloud can potentially be accessed by anyone
• Security is managed elsewhere
• Your control mechanisms are in the hands of others
• Server unavailability / Account lockout
• Cloud computing doesn’t guarantee availability
Risks associated with virtualization
• Compromising the virtualization layer puts all systems at risk
• There is little control over VM to VM communication
• Support for “virtual firewalls” is an emerging technology
• Single physical host contains VMs that have different security profiles
• Physical separation is no longer possible
• There is potential for loss of separation of duties
• System admin controls many servers on a single piece of hardware
Integrating Systems and Data with Third Parties
On-boarding
• Bring a new partner into the organization
• This is more particular than hiring new staff
• Many agreements will be in place
• Legalities associated with business and security matters
• Implement technical functions
• Secure connections between partners
• Usually as an IPsec tunnel or physical segmentation
• Establish an authentication method
• Provide access to shared resources
• Audit all security controls
• Properly share (and separate) data
Off-boarding
• This process should be pre-planned
• You don’t want to decide how to do things at this point
• How will the systems be dissolved?
• What happens to the data?
• When will the final connections be terminated?
Social Media and Third-Party Concerns
• Management of data
• Social media data includes privacy concerns
• Some of the data is extremely valuable
• Your social media reputation
• Someone else is tweeting for you
• The tone is as important as the message
• Account control is important
• Social media accounts are shared by a large group
• A mistake on one phone can be seen by many
Interoperability Agreements
• Memorandum of Understanding
• Informal letter of intent;not a signed contract
• Usually includes statements of confidentiality
• Service Level Agreement (SLA)
• Minimum terms for services provided
• Uptime, response time agreement, etc.
• Business Partners Agreement (BPA)
• Commonly seen between manufacturers and resellers
• Interconnection Security Agreement (ISA)
• Used by US Federal Government to define security controls
Recovery Time Objectives
• Mean time to restore (MTTR)
• Mean time to repair
• Mean time to failure (MTTF)
• The expected lifetime of a product or system
• Mean time between failures (MTBF)
• Predict the time between failures
• Recovery time objectives (RTO)
• Get up and running quickly
• Get back to a particular service level
• Recovery point objectives (RPO)
• How much data loss is acceptable?
• Bring the system back online; how far back does data go?
Privacy Considerations
• Privacy of the individual
• Both personal and professional
• Legally mandated privacy laws in many European countries
• An employer can’t track your personal computer use
• Customer data often contains a aspect of privacy
• Even benign data can be combined to violate privacy
• Third-party agreements must consider privacy
• The rules should be in place from the beginning
Data Ownership
• Data is everything
• The most important asset in an organization
• Without the data, there’s no company
• The owner of the data has a responsibility
• Protection, privacy
• Technical / Logical controls
• Physical controls
• Who owns the data if the third-party agreement ends?
• This should be determined prior to that circumstance
Risk Awareness with Third-Parties
• Combine two systems
• Hopefully get a seamless technical integration
• Security must be designed into the project
• Usually designed by teams from both organizations
• Everyone must be aware of the risks
• Security policies must be examined for additional risks
• Resources, business requirements, and risk must be balanced
• Agreements must be in place
• For example: Who does backups?
Who gets access to the backups? How are the backups stored?
Data Ownership
• Who owns the data?
• There’s more than one participant
• Is there more than one owner?
• What part of the data is owned by which partner?
• Data ownership agreements can avoid some of the messy details
• Where is the data stored?
• Who owns the data when
• the relationship is over?
• How is data destroyed?
© 2014 Messer Studios, LLC
Professor Messer’s CompTIA SY0-401 Security+ Study Guide - Page 7
http://www.ProfessorMesser.com
�
Integrating Systems and Data with Third-Parties (continued)
Third-party Data Sharing
• Data shared between partners
• Network connections may exist
• Proper controls may not be in place
• Data shared with others
• Agreements are usually in place with the data owners
• Data is sometimes shared with others without permission
Data Backups with Third-Parties
• Backups are often overlooked
• They contain everything
• Data backups are often kept off-site
• Yet-another third-party
• Losing data from a backup is a very bad thing
• Seems to happen more often than you might think
• Not all backups are the same
• Financial data, health care data, top secret data, etc.
Mitigating Risk
Change Management
• Upgrade software, change firewall configuration, modify switch ports
• Occurs very frequently
• The change management process is often overlooked or ignored
• Clear policies are needed
• Frequency, duration, installation process, fallback procedures
Incident Management
• Series of events that negatively affects the organization
• Database hack, stolen laptop, water pipe burst
• Who will be contacted when an incident occurs?
• Who’s responsible for managing the incident response?
• Technical steps for handling systems and preserving evidence
• What goes on the report?
User Rights and Permissions
• Management sets the limits
• Security team administers the limits
• You must translate management requirements into technical access
• Periodic audits are useful
Basic Forensic Procedures
Security Policy Considerations with Third-parties
• The security policy is the weakest link
• A badly implemented security policy puts data at risk
• Protect information between vendors, partners, and customers
• Avoid data modification, disclosure, damage, or destruction
• Most of this language is contractual
• Everybody understands their responsibilities
• Security policies are constantly updated
• The threat landscape is constantly changing
Third-Party Security Compliance
• Third-party relationships add to the need for security compliance
• Shared resources require additional oversight
• Compliance can be technically challenging
• Cloud-based services add additional complexity
• Some compliance requirements are legally mandated
• HIPAA - Health Insurance Portability and Accountability Act
• PCI DSS - Payment Card Industry Data Security Standard
• FISMA - Federal Information Security Management Act
• Perform a gap analysis
• Determine all gaps in security
• Resolve the issues
• Some issues can’t be easily resolved
• A decision must be made regarding cost vs. benefit
• Perform periodic audits
• These audits may be involved and far-reaching
• More coordination required with the third-party
Auditing
• Does everyone have the correct permissions?
• How are your resources used?
• Are your systems and applications secure?
• Are your disaster recovery plans going to work?
• Can you contact the right people at the right time?
• Document everything
Preventing data loss or theft
• Involves process and procedure
• Some of the most difficult data policies to implement
• It’s very easy to carry large amounts of data around
• There are both internal and external threats
• You have to protect everywhere
• This is a bigger threat every day
Data Loss Prevention Systems
• On your computer - Data in use
• On your network - Data in motion
• On your server - Data at rest
Most%Vola)le
CPU$registers,$CPU$cache
Router$table,$ARP$cache,$process$table,$kernel$sta8s8cs,$memory
Temporary$file$systems
Disk
Remote$logging$and$monitoring$data
Physical$configura8on,$network$topology
Least%Vola)le
Archival$media
Capturing system images
• Copy the contents of a disk
• Bit-for-bit, byte-for-byte
• Software imaging tools
• Use a bootable device
• Remove the physical drive
• Use a hardware write-blocker
• Get the backup tapes
• These may already be available
© 2014 Messer Studios, LLC
Professor Messer’s CompTIA SY0-401 Security+ Study Guide - Page 8
http://www.ProfessorMesser.com
�











 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc