SOLUTIONS MANUAL
CRYPTOGRAPHY AND NETWORK
SECURITY
PRINCIPLES AND PRACTICE
FOURTH EDITION
WILLIAM STALLINGS
�
Copyright 2006: William Stallings
-2-
�
© 2006 by William Stallings
All rights reserved. No part of this document may
be reproduced, in any form or by any means, or
posted on the Internet, without permission in
writing from the author.
-3-
�
NOTICE
This manual contains solutions to all of the review questions and
homework problems in Cryptography and Network Security, Fourth
Edition. If you spot an error in a solution or in the wording of a
problem, I would greatly appreciate it if you would forward the
information via email to ws@shore.net. An errata sheet for this manual,
if needed, is available at ftp://shell.shore.net/members/w/s/ws/S.
W.S.
-4-
�
TABLE OF CONTENTS
Chapter 1:
Introduction ..................................................................................................5
Chapter 2:
Classical Encryption Techniques ...............................................................7
Chapter 3:
Block Ciphers and the Date Encryption Standard ................................13
Chapter 4:
Finite Fields.................................................................................................21
Chapter 5:
Advanced Encryption Standard ..............................................................28
Chapter 6:
More on Symmetric Ciphers ....................................................................33
Chapter 7:
Confidentiality Using Symmetric Encryption .......................................38
Chapter 8:
Introduction to Number Theory..............................................................42
Chapter 9:
Public-Key Cryptography and RSA ........................................................46
Chapter 10: Key Management; Other Public-Key Cryptosystems...........................55
Chapter 11: Message Authentication and Hash Functions .......................................59
Chapter 12: Hash and MAC Algorithms .....................................................................62
Chapter 13: Digital Signatures and Authentication Protocols..................................66
Chapter 14: Authentication Applications ....................................................................71
Chapter 15:
Electronic Mail Security ............................................................................73
Chapter 16:
IP Security ...................................................................................................76
Chapter 17: Web Security...............................................................................................80
Chapter 18:
Intruders......................................................................................................83
Chapter 19: Malicious Software ....................................................................................87
Firewalls ......................................................................................................89
Chapter 20:
-5-
�
CHAPTER 1
INTRODUCTION
ANSWERS TO QUESTIONS
1.1 The OSI Security Architecture is a framework that provides a systematic way of defining
the requirements for security and characterizing the approaches to satisfying those
requirements. The document defines security attacks, mechanisms, and services, and the
relationships among these categories.
1.2 Passive attacks have to do with eavesdropping on, or monitoring, transmissions.
Electronic mail, file transfers, and client/server exchanges are examples of
transmissions that can be monitored. Active attacks include the modification of
transmitted data and attempts to gain unauthorized access to computer systems.
1.3 Passive attacks: release of message contents and traffic analysis. Active attacks:
masquerade, replay, modification of messages, and denial of service.
1.4 Authentication: The assurance that the communicating entity is the one that it claims to be.
Access control: The prevention of unauthorized use of a resource (i.e., this service controls
who can have access to a resource, under what conditions access can occur, and what those
accessing the resource are allowed to do).
Data confidentiality: The protection of data from unauthorized disclosure.
Data integrity: The assurance that data received are exactly as sent by an authorized entity
(i.e., contain no modification, insertion, deletion, or replay).
Nonrepudiation: Provides protection against denial by one of the entities involved in a
communication of having participated in all or part of the communication.
Availability service: The property of a system or a system resource being accessible and
usable upon demand by an authorized system entity, according to performance
specifications for the system (i.e., a system is available if it provides services according to
the system design whenever users request them).
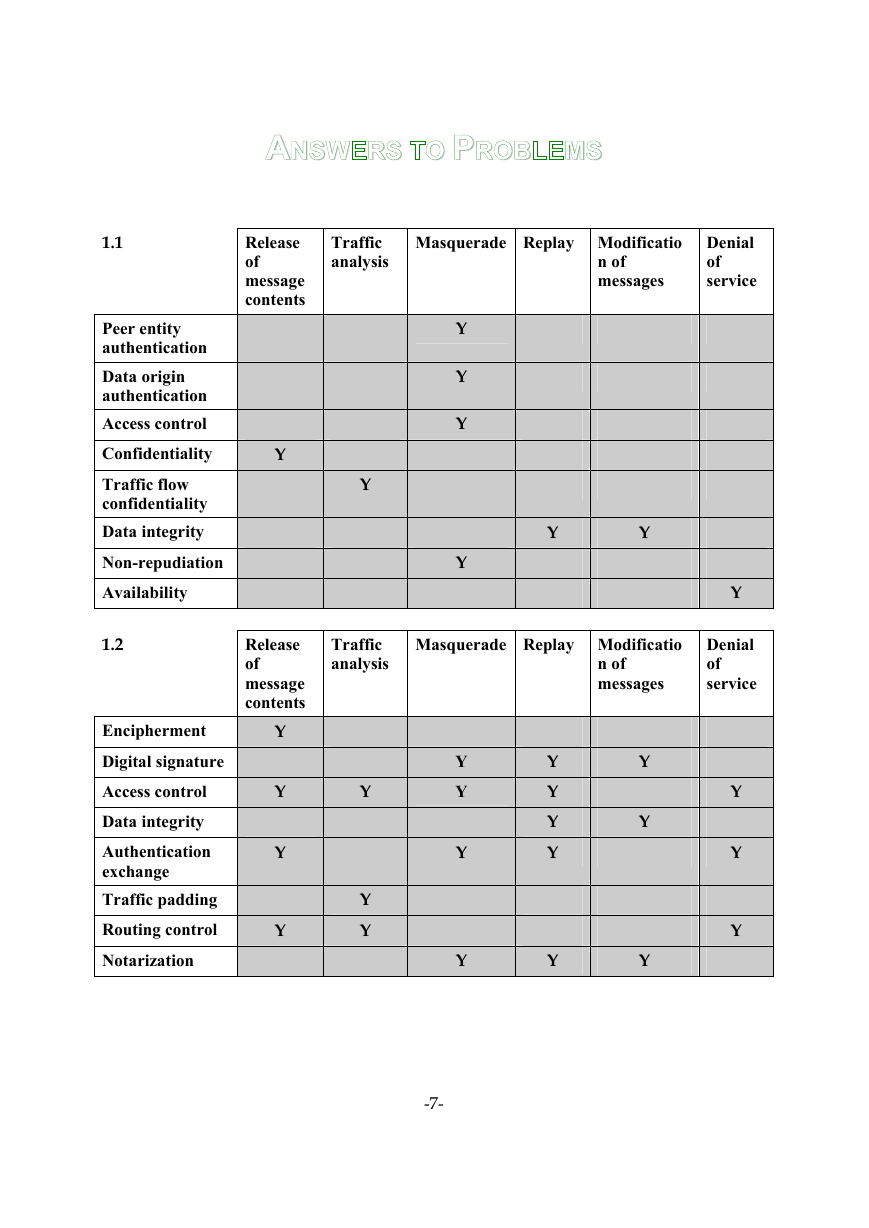
1.5 See Table 1.3.
-6-
�
1.1
Peer entity
authentication
Data origin
authentication
Access control
Confidentiality
Traffic flow
confidentiality
Data integrity
Non-repudiation
Availability
1.2
Encipherment
Digital signature
Access control
Data integrity
Authentication
exchange
Traffic padding
Routing control
Notarization
ANSWERS TO PROBLEMS
Traffic
analysis
Release
of
message
contents
Masquerade Replay Modificatio
n of
messages
Y
Y
Y
Y
Y
Y
Y
Y
Denial
of
service
Y
Traffic
analysis
Release
of
message
contents
Masquerade Replay Modificatio
n of
messages
Denial
of
service
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
Y
-7-
�
CHAPTER 2
CLASSICAL ENCRYPTION TECHNIQUESR
ANSWERS TO QUESTIONS
2.1 Plaintext, encryption algorithm, secret key, ciphertext, decryption algorithm.
2.2 Permutation and substitution.
2.3 One key for symmetric ciphers, two keys for asymmetric ciphers.
2.4 A stream cipher is one that encrypts a digital data stream one bit or one byte at a
time. A block cipher is one in which a block of plaintext is treated as a whole and
used to produce a ciphertext block of equal length.
2.5 Cryptanalysis and brute force.
2.6 Ciphertext only. One possible attack under these circumstances is the brute-force
approach of trying all possible keys. If the key space is very large, this becomes
impractical. Thus, the opponent must rely on an analysis of the ciphertext itself,
generally applying various statistical tests to it. Known plaintext. The analyst may
be able to capture one or more plaintext messages as well as their encryptions.
With this knowledge, the analyst may be able to deduce the key on the basis of the
way in which the known plaintext is transformed. Chosen plaintext. If the analyst
is able to choose the messages to encrypt, the analyst may deliberately pick
patterns that can be expected to reveal the structure of the key.
2.7 An encryption scheme is unconditionally secure if the ciphertext generated by the
scheme does not contain enough information to determine uniquely the
corresponding plaintext, no matter how much ciphertext is available. An
encryption scheme is said to be computationally secure if: (1) the cost of breaking
the cipher exceeds the value of the encrypted information, and (2) the time
required to break the cipher exceeds the useful lifetime of the information.
2.8 The Caesar cipher involves replacing each letter of the alphabet with the letter
standing k places further down the alphabet, for k in the range 1 through 25.
2.9 A monoalphabetic substitution cipher maps a plaintext alphabet to a ciphertext
alphabet, so that each letter of the plaintext alphabet maps to a single unique letter
of the ciphertext alphabet.
-8-
�















 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc