智能硬件漏洞挖掘与利用
主讲人: 杨坤 kun.yang@chaitin.com
�
How do hackers find your bug?
Buy one from
Official Site
Find the firmware
Get shell for debugging
and achieving more info
Identify attack surfaces
Reverse engineering or
script review
Write an exploit
Capture download links from
App or Web control portal
Serial Port?
Repacking firmware
nmap,if you have shell, use netstat
wireless protocol like bluetooth?
�
Outline
● Gathering Information
Find firmware
○
○ Get shell
○ Attack surface analysis
● Vulnerability Discovery
○ Reverse Engineering
○
Fuzzing
● Exploitation
○ Mitigations
○ Shellcode
○ ROP
�
Pwning devices step by step
● 华为荣耀路由 WS831
● 华硕 RT-AC68U 无线路由器
● 思科 CVR100W 无线路由器
�
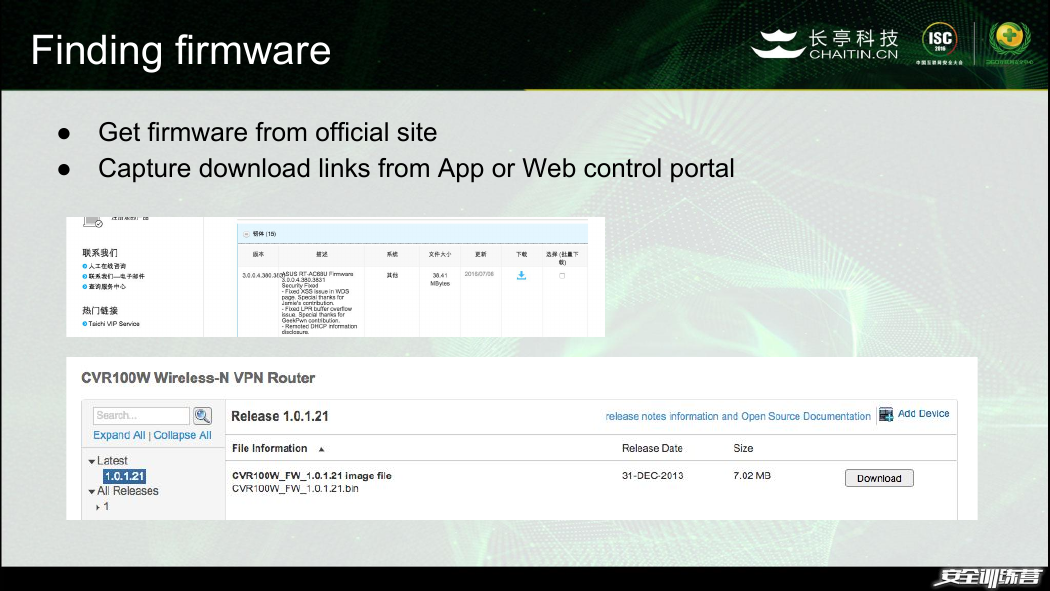
Finding firmware
● Get firmware from official site
● Capture download links from App or Web control portal
�
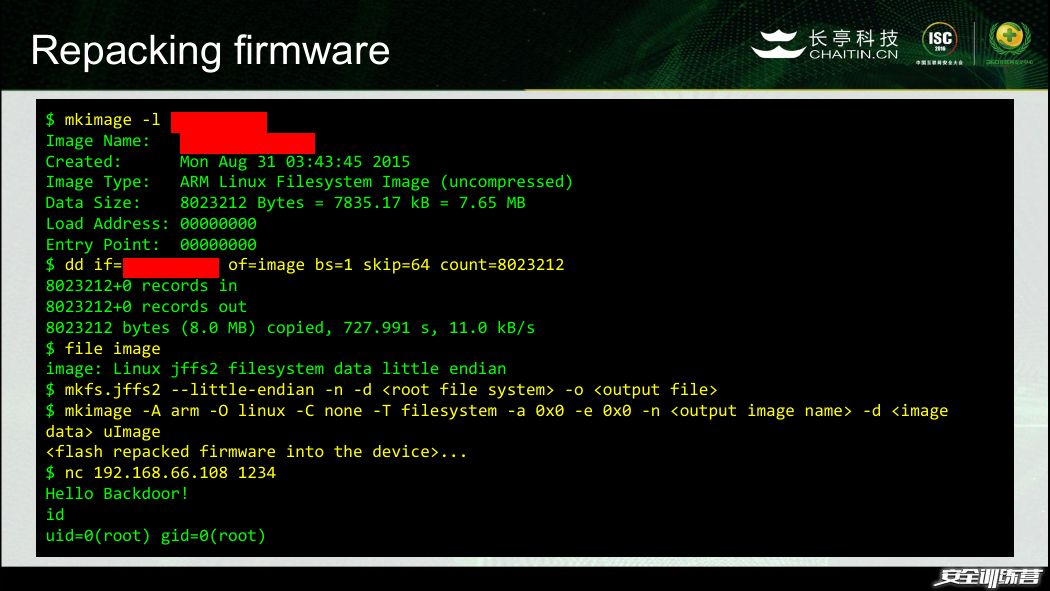
Repacking firmware
$ mkimage -l xxxxxxxxxx
Image Name: xxxxxxxxxxxxxx
Created: Mon Aug 31 03:43:45 2015
Image Type: ARM Linux Filesystem Image (uncompressed)
Data Size: 8023212 Bytes = 7835.17 kB = 7.65 MB
Load Address: 00000000
Entry Point: 00000000
$ dd if=xxxxxxxxxx of=image bs=1 skip=64 count=8023212
8023212+0 records in
8023212+0 records out
8023212 bytes (8.0 MB) copied, 727.991 s, 11.0 kB/s
$ file image
image: Linux jffs2 filesystem data little endian
$ mkfs.jffs2 --little-endian -n -d -o
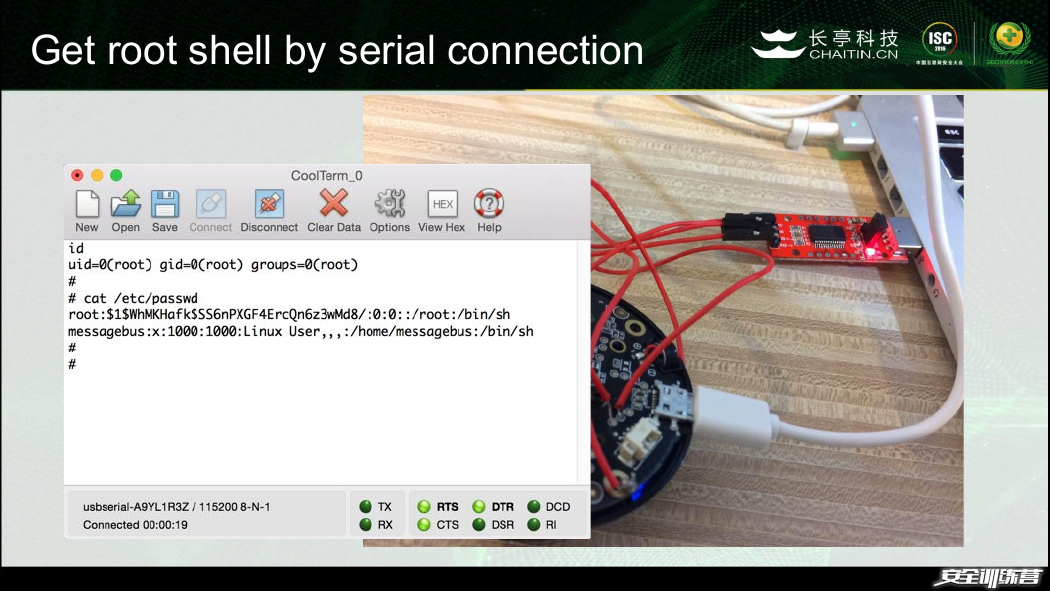
Get root shell by serial connection
�
Finding serial port
�













 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc