2018/5/2
文档 1453883.1
PowerView 已关闭
家鹏 (可用)
(0)
与我们联系 帮助
面板
知识
服务请求 补丁程序和更新程序
社区 认证 系统 收集器
Patches & Updates >
提供反馈...
Copyright (c) 2018, Oracle. All rights reserved.
Using Class of Secure Transport (COST) to Restrict Instance Registration (文档 ID 1453883.1)
转到底部
I n t h i s D o c u m e n t
Goal
Solution
References
APPLIES TO:
Oracle Net Services - Version 10.2.0.3 to 12.1.0.2 [Release 10.2 to 12.1]
Oracle Database - Enterprise Edition - Version 10.2.0.3 to 12.1.0.2 [Release 10.2 to 12.1]
Oracle Database - Standard Edition - Version 10.2.0.3 to 12.1.0.2 [Release 10.2 to 12.1]
Information in this document applies to any platform.
GOAL
To demonstrate how the COST parameter "SECURE_REGISTER_listener_name =" is used to restrict instance
registration with database listeners. With this COST restriction in place only local instances will be
allowed to register. These instructions can be used to address the issues published in Oracle Security
Alert CVE-2012-1675 by using COST to restrict connections to only local instances.
A b o u t C O S T
The class of secure transports (COST) parameters specify a list of transports that are considered secure
for administration and registration of a particular listener. The COST parameters identify which
transports are considered secure for that installation and whether the administration of a listener
requires secure transports. COST will not affect client connections utilizing other protocols. For more
details and for information about other available COST parameters please see the 11.2 Network
Administrators Guide and Network Reference.
A b o u t t h e I P C P r o t o c o l
IPC protocol support is similar to BEQ protocol support in that it can only be used when the client
program and the Oracle server are installed on the same system. IPC protocol support differs from BEQ
protocol support in that it can be used with Oracle Shared Server configurations. IPC protocol support
requires a listener for its operation. For more information about IPC please see Doc ID 29232.1 "IPC
Explained".
O r a c l e v e r s i o n s t h a t s u p p o r t C O S T
Although not documented in the Oracle 10g Network Administration Guides COST parameters and functionality
are supported as of 10.2.0.3.
Starting with Oracle Database Version 11.2.0.4 and Oracle Database 12c (12.1.0.1), the screening of
service registration requests from database instances is performed using the Oracle Listener inherent
"Valid Node Checking for Registration" feature. Oracle recommends using the "VNCR" feature in 11.2.0.4
and 12c as an alternative to COST if the implementation is only to regulate database service
registration requests with Listeners. If COST parameters are needed for Oracle Database 11.2.0.4 or
12c for other or for additional reasons, then they should be used as intended.
For more information information about "Valid Node Checking for Registration" in 11.2.0.4 and 12c
please reference the following links:
Oracle Net 12c: Valid Node Checking For Registration (VNCR) (Doc ID 1600630.1)
Oracle® Database Net Services Reference
12c Release 1 (12.1)
New features overview
Oracle® Clusterware Administration and Deployment Guide
12c Release 1 (12.1)
SCAN Listeners and Service Registration Restriction With Valid Node Checking
SOLUTION
There are two methods that can be used to protect the listener using COST
"SECURE_REGISTER_listener_name =" in stand alone database installations.
此文档是否有帮助?
是
否
文档详细信息
类型:
状态:
上次主更
新:
上次更新:
语言:
HOWTO
PUBLISHED
2015-2-18
2017-12-15
English
相关产品
Oracle Database -
Enterprise Edition
Oracle Database -
Standard Edition
Oracle Net Services
信息中心
Information Center:
Overview Database
Server/Client
Installation and
Upgrade/Migration
[1351022.2]
Index of Oracle Database
Information Centers
[1568043.2]
インフォメーション・セン
ター: データベースおよび
Enterprise Manager 日本語
ドキュメント [1946305.2]
Information Center:
Overview of Database
Security Products
[1548952.2]
Oracle Database 11g
Release 2 Information
Center [1436725.2]
文档引用
IPC Explained [29232.1]
Valid Node Checking For
Registration (VNCR)
[1600630.1]
Force Connections to a
Specific Database Service
When two Identical
Services are Registered
to CMAN [1455068.1]
Using Class of Secure
Transport (COST) to
Restrict Instance
Registration in Oracle
RAC [1340831.1]
最近查看
Using Class of Secure
Transport (COST) to
Restrict Instance
Registration in Oracle
RAC [1340831.1]
Release Schedule of
Current Database
Releases [742060.1]
https://support.oracle.com/epmos/faces/DocumentDisplay?_afrLoop=344058498322677&id=1453883.1&_afrWindowMode=0&_adf.ctrl-state=8uxcrggjt_1306
1/7
�
2018/5/2
文档 1453883.1
1) Restricting registration to the T C P protocol (Requires the fix for BUG:12880299)
- or -
2) Restricting registration to the I P C protocol (The patch for BUG:12880299 is N O T required for the
IPC method)
Either method accomplishes the same goal but it is your choice which to implement. Both methods will
be discussed.
T o p i c s i n t h i s s e c t i o n :
1) Setting a COST restriction using the TCP protocol to limit registration to local instances.
2) Setting a COST restriction using the IPC protocol to limit registration to local instances.
3) Verifying that COST is working.
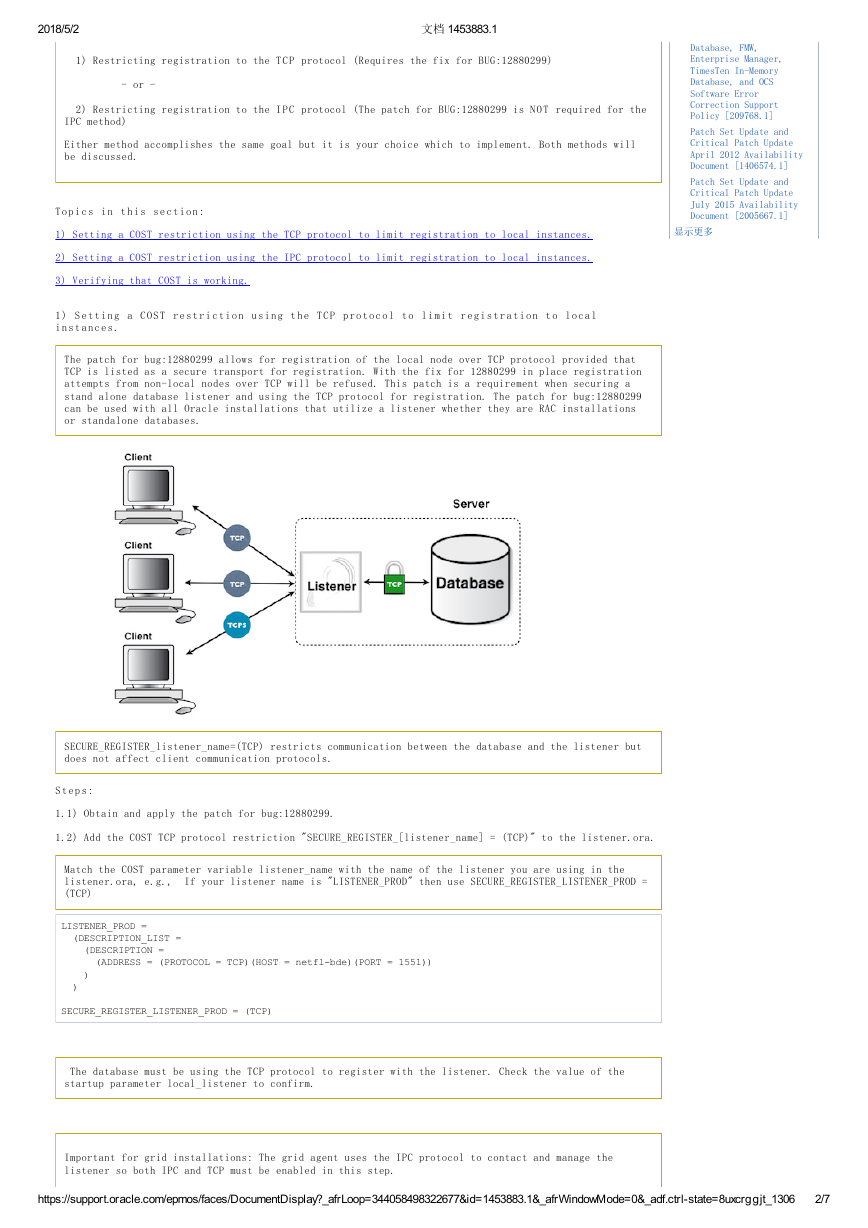
1 ) S e t t i n g a C O S T r e s t r i c t i o n u s i n g t h e T C P p r o t o c o l t o l i m i t r e g i s t r a t i o n t o l o c a l
i n s t a n c e s .
The patch for bug:12880299 allows for registration of the local node over TCP protocol provided that
TCP is listed as a secure transport for registration. With the fix for 12880299 in place registration
attempts from non-local nodes over TCP will be refused. This patch is a requirement when securing a
stand alone database listener and using the TCP protocol for registration. The patch for bug:12880299
can be used with all Oracle installations that utilize a listener whether they are RAC installations
or standalone databases.
Database, FMW,
Enterprise Manager,
TimesTen In-Memory
Database, and OCS
Software Error
Correction Support
Policy [209768.1]
Patch Set Update and
Critical Patch Update
April 2012 Availability
Document [1406574.1]
Patch Set Update and
Critical Patch Update
July 2015 Availability
Document [2005667.1]
显示更多
SECURE_REGISTER_listener_name=(TCP) restricts communication between the database and the listener but
does not affect client communication protocols.
S t e p s :
1.1) Obtain and apply the patch for bug:12880299.
1.2) Add the COST TCP protocol restriction "SECURE_REGISTER_[listener_name] = (TCP)" to the listener.ora.
Match the COST parameter variable listener_name with the name of the listener you are using in the
listener.ora, e.g., If your listener name is "LISTENER_PROD" then use SECURE_REGISTER_LISTENER_PROD =
(TCP)
LISTENER_PROD =
(DESCRIPTION_LIST =
(DESCRIPTION =
(ADDRESS = (PROTOCOL = TCP)(HOST = netfl-bde)(PORT = 1551))
)
)
SECURE_REGISTER_LISTENER_PROD = (TCP)
The database must be using the TCP protocol to register with the listener. Check the value of the
startup parameter local_listener to confirm.
Important for grid installations: The grid agent uses the IPC protocol to contact and manage the
listener so both IPC and TCP must be enabled in this step.
https://support.oracle.com/epmos/faces/DocumentDisplay?_afrLoop=344058498322677&id=1453883.1&_afrWindowMode=0&_adf.ctrl-state=8uxcrggjt_1306
2/7
�
2018/5/2
文档 1453883.1
For a grid environment use the following value,
SECURE_REGISTER_LISTENER_PROD = (IPC,TCP)
1.3) Restart the listener.
The listener will now only accept database registration information from the local database and over TCP.
With COST enabled for the TCP protocol attempts to register with the listener from anything other than the
local system using TCP is rejected and an event is logged in the listener log.
11-MAY-2011 10:27:23 * service_register_NSGR * 1194
TNS-01194: The listener command did not arrive in a secure transport
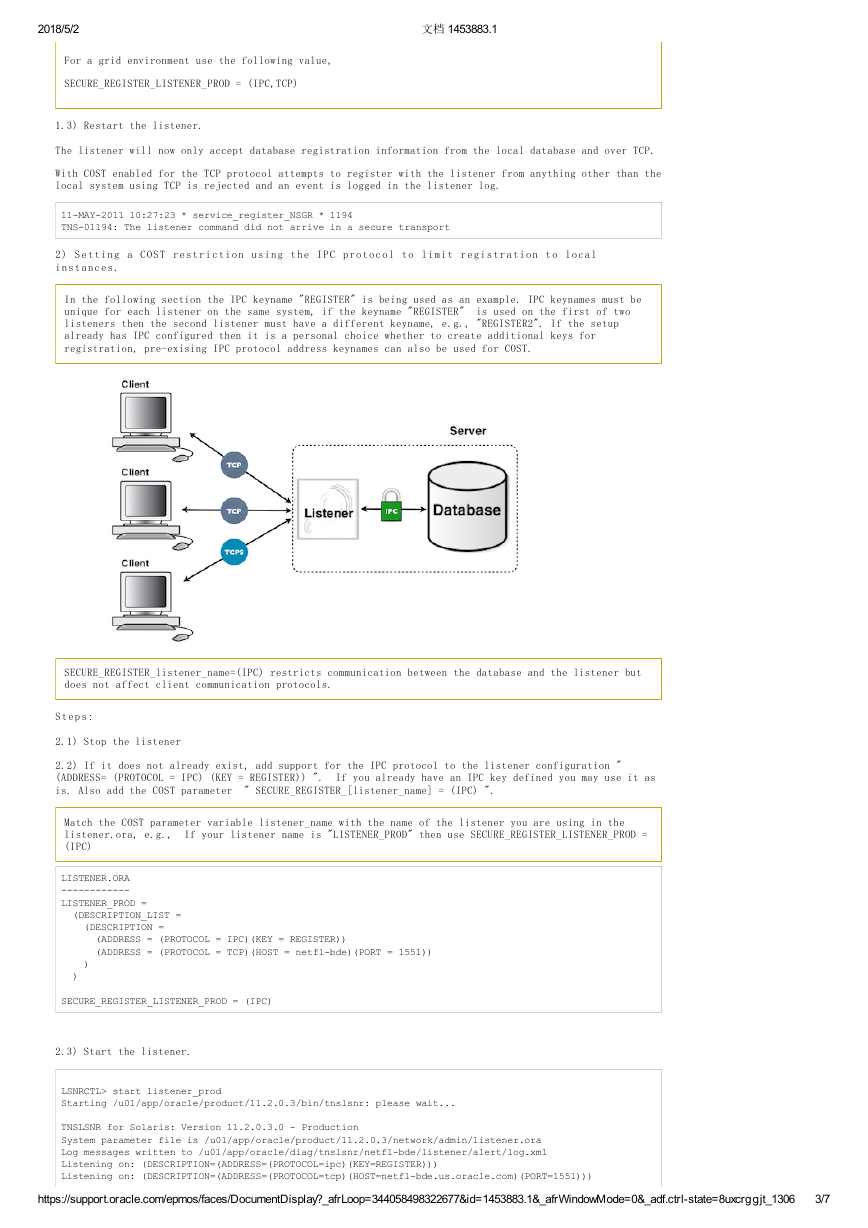
2 ) S e t t i n g a C O S T r e s t r i c t i o n u s i n g t h e I P C p r o t o c o l t o l i m i t r e g i s t r a t i o n t o l o c a l
i n s t a n c e s .
In the following section the IPC keyname "REGISTER" is being used as an example. IPC keynames must be
unique for each listener on the same system, if the keyname "REGISTER" is used on the first of two
listeners then the second listener must have a different keyname, e.g., "REGISTER2". If the setup
already has IPC configured then it is a personal choice whether to create additional keys for
registration, pre-exising IPC protocol address keynames can also be used for COST.
SECURE_REGISTER_listener_name=(IPC) restricts communication between the database and the listener but
does not affect client communication protocols.
S t e p s :
2.1) Stop the listener
2.2) If it does not already exist, add support for the IPC protocol to the listener configuration "
(ADDRESS= (PROTOCOL = IPC) (KEY = REGISTER)) ". If you already have an IPC key defined you may use it as
is. Also add the COST parameter " SECURE_REGISTER_[listener_name] = (IPC) ".
Match the COST parameter variable listener_name with the name of the listener you are using in the
listener.ora, e.g., If your listener name is "LISTENER_PROD" then use SECURE_REGISTER_LISTENER_PROD =
(IPC)
LISTENER.ORA
------------
LISTENER_PROD =
(DESCRIPTION_LIST =
(DESCRIPTION =
(ADDRESS = (PROTOCOL = IPC)(KEY = REGISTER))
(ADDRESS = (PROTOCOL = TCP)(HOST = netfl-bde)(PORT = 1551))
)
)
SECURE_REGISTER_LISTENER_PROD = (IPC)
2.3) Start the listener.
LSNRCTL> start listener_prod
Starting /u01/app/oracle/product/11.2.0.3/bin/tnslsnr: please wait...
TNSLSNR for Solaris: Version 11.2.0.3.0 - Production
System parameter file is /u01/app/oracle/product/11.2.0.3/network/admin/listener.ora
Log messages written to /u01/app/oracle/diag/tnslsnr/netfl-bde/listener/alert/log.xml
Listening on: (DESCRIPTION=(ADDRESS=(PROTOCOL=ipc)(KEY=REGISTER)))
Listening on: (DESCRIPTION=(ADDRESS=(PROTOCOL=tcp)(HOST=netfl-bde.us.oracle.com)(PORT=1551)))
https://support.oracle.com/epmos/faces/DocumentDisplay?_afrLoop=344058498322677&id=1453883.1&_afrWindowMode=0&_adf.ctrl-state=8uxcrggjt_1306
3/7
�
2018/5/2
文档 1453883.1
Connecting to (DESCRIPTION=(ADDRESS=(PROTOCOL=IPC)(KEY=REGISTER)))
STATUS of the LISTENER
------------------------
Alias LISTENER_PROD
Version TNSLSNR for Solaris: Version 11.2.0.3.0 - Production
Start Date 27-APR-2012 16:34:20
Uptime 0 days 0 hr. 0 min. 0 sec
Trace Level off
Security ON: Local OS Authentication
SNMP OFF
Listener Parameter File /u01/app/oracle/product/11.2.0.3/network/admin/listener.ora
Listener Log File /u01/app/oracle/diag/tnslsnr/netfl-bde/listener/alert/log.xml
Listening Endpoints Summary...
(DESCRIPTION=(ADDRESS=(PROTOCOL=ipc)(KEY=REGISTER)))
(DESCRIPTION=(ADDRESS=(PROTOCOL=tcp)(HOST=netfl-bde.us.oracle.com)(PORT=1551)))
The listener supports no services
The command completed successfully
2.4) Replace the TCP address in the database local_listener parameter with the IPC address used by the
listener.
Some installations may be using a pfile rather than spfile as this example shows. In that case modify
the pfile startup parameter to provide the same functionality.
SQL> show parameter local_listener
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
local_listener string (ADDRESS = (PROTOCOL = TCP)(HO
ST = netfl-bde)(PORT = 1551))
SQL> alter system set local_listener='(DESCRIPTION=(ADDRESS=(PROTOCOL=IPC)(KEY=REGISTER)))' scope =
both;
System altered.
SQL> show parameter local_listener
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
local_listener string (DESCRIPTION=(ADDRESS=(PROTOCO
L=IPC)(KEY=REGISTER)))
2.5) Verify that the instance is now registered with the listener.
LSNRCTL> services listener_prod
Connecting to (DESCRIPTION=(ADDRESS=(PROTOCOL=IPC)(KEY=REGISTER)))
Services Summary...
Service "N11203.us.oracle.com" has 1 instance(s).
Instance "N11203", status READY, has 1 handler(s) for this service...
Handler(s):
"DEDICATED" established:0 refused:0 state:ready
LOCAL SERVER
The command completed successfully
With COST enabled attempts to register with the listener using a protocol other than IPC is rejected and
an event is logged in the listener log.
11-MAY-2011 10:27:23 * service_register_NSGR * 1194
TNS-01194: The listener command did not arrive in a secure transport
3 ) V e r i f y i n g t h a t C O S T i s w o r k i n g
Overview: To confirm the functionality of a COST configuration in a standalone database environment start
the COST protected listener and attempt to register with it from a remote machine. A remotely registered
instance will display as "REMOTE SERVER" in lsnrctl services output.
This is just one example of how to check. Configurations and listener output may vary per setup but the
test logic remains the same; can an unauthorized protocol register with the listener? This same testing
methodology can be used for COST restrictions using IPC, TCP or TCPS protocol or any combinations thereof.
prerequisites:
If the installation is using COST with a TCP restriction the patch for bug:12880299 should have
already been applied.
Two systems are required, the installation and listener you are verifying and a remote instance with
which to attempt registration.
Test Logic: First ensure that remote registration will take place with COST disabled, then re-enable COST
and verify that it is restricting the same remote registration attempts.
https://support.oracle.com/epmos/faces/DocumentDisplay?_afrLoop=344058498322677&id=1453883.1&_afrWindowMode=0&_adf.ctrl-state=8uxcrggjt_1306
4/7
�
2018/5/2
文档 1453883.1
In this example patch 12880299 is installed and COST is configured to restrict registration to the
local node only over the TCP protocol.
S t e p s :
3.1) Comment the COST rule in listener.ora and restart the listener.
LISTENER_PROD =
(DESCRIPTION =
(ADDRESS_LIST=
(ADDRESS=(PROTOCOL=IPC)(KEY=EXTPROC2))
(ADDRESS=(PROTOCOL = TCP)(HOST=netfl-bde)(PORT=1551))
)
)
#SECURE_REGISTER_LISTENER_PROD = (TCP)
3.2) At the remote system that will be sending registration information to the listener being tested, load
the target listeners TCP address into the database initialization parameter "remote_listener=". Enclose
the address in single quotes and use the scope clause "scope=memory;". This action will tell the instance
to also send registration packets to the remote listener over TCP.
[mes2]/u01/app/oracle/product/10.2.0> sqlplus "/ as sysdba"
SQL*Plus: Release 10.2.0.5.0 - Production on Fri May 4 10:11:27 2012
Connected to:
Oracle Database 10g Enterprise Edition Release 10.2.0.5.0 - 64bit Production
With the Partitioning, OLAP, Data Mining and Real Application Testing options
SQL> show parameter remote_listener;
NAME TYPE VALUE
------------------------------------ ----------- ------------------------------
remote_listener string
SQL> alter system set remote_listener='(ADDRESS=(PROTOCOL=TCP)(HOST=netfl-bde)(PORT=1551))'
scope=memory;
System altered.
3.3) Back at the listener you should now see a service handler created for the remotely registered
instance. Notice how it is listed as a REMOTE SERVER.
LSNRCTL> services listener_prod
Connecting to (DESCRIPTION=(ADDRESS=(PROTOCOL=IPC)(KEY=EXTPROC2)))
Services Summary...
Service "N102.us.oracle.com" has 1 instance(s).
Instance "N102", status READY, has 1 handler(s) for this service...
Handler(s):
"DEDICATED" established:0 refused:0 state:ready
REMOTE SERVER
(ADDRESS=(PROTOCOL=TCP)(HOST=mes2)(PORT=1521))
The command completed successfully
3.4) With remote registration confirmed test COST. Remove the comment from the COST parameter in the
listener.ora and restart the listener. COST is now protecting the listener from registration attempts that
are not coming from the local node.
3.5) At the remote instance force another registration attempt by issuing the SQL command "alter system
register;" .
SQL> alter system register;
System altered.
SQL>
3.6) Check the listener for service handlers, no handlers for REMOTE SERVER(s) should be seen.
[oracle@bde]$ lsnrctl
LSNRCTL for Linux: Version 11.2.0.2.0 - Production on 04-MAY-2012 10:42:57
Copyright (c) 1991, 2010, Oracle. All rights reserved.
Welcome to LSNRCTL, type "help" for information.
LSNRCTL> services listener_prod
Connecting to (DESCRIPTION=(ADDRESS=(PROTOCOL=IPC)(KEY=EXTPROC2)))
The listener supports no services
The command completed successfully
https://support.oracle.com/epmos/faces/DocumentDisplay?_afrLoop=344058498322677&id=1453883.1&_afrWindowMode=0&_adf.ctrl-state=8uxcrggjt_1306
5/7
�
2018/5/2
文档 1453883.1
3.7) Check the listener log, TNS-01194 messages will occur with each registration attempt that was
refused.
[oracle@bde]$ tail /u01/app/oracle/product/11.2.0.2/network/log/listener.log
04-MAY-2012 10:43:03 * (CONNECT_DATA=(CID=(PROGRAM=)(HOST=netfl-bde)(USER=oracle))
(COMMAND=services)(ARGUMENTS=64)(SERVICE=LISTENER)(VERSION=186647040)) * services * 0
04-MAY-2012 10:43:05 * service_register_NSGR * 1194
TNS-01194: The listener command did not arrive in a secure transport
04-MAY-2012 10:44:05 * service_register_NSGR * 1194
TNS-01194: The listener command did not arrive in a secure transport
With COST enabled the results of steps 3.6 and 3.7 above are expected and confirm that the COST
registration restriction is working properly.
3.8) When finished testing clear the remote_listener value of the remote instance either by restarting or
replacing the parameter in memory with a null string.
SQL> alter system set remote_listener='' scope=memory;
System altered.
This same test method will also confirm COST restrictions that are set to IPC or TCPS .
Patch/fix information for BUG:12880299
The fix for BUG:12880299 will be included in Oracle 11.2.0.4.
PSU's that include the fix:
Cumulative Patch Inclusion - DBPSU 10.2.0.5.8 (Released)
Cumulative Patch Inclusion - DBPSU 11.2.0.2.7 (Released)
Cumulative Patch Inclusion - DBPSU 10.2.0.4.13 (Released)
Cumulative Patch Inclusion - DBPSU 11.2.0.3.3 (Released)
Cumulative Patch Inclusion - DBPSU 11.1.0.7.12 (Released)
Windows patch availability for bugfix:12880299
11.2.0.3: 12880299 is included in bundle 6 (Released)
--------
32-bit : Patch 13965210
64-bit : Patch 13965211
11.2.0.2: 12880299 is included in bundle 19 (Released)
--------
32-bit : Patch 14046710
64-bit : Patch 14046711
11.1.0.7: 12880299 is included in bundle 46 (Released)
10.2.0.5: 12880299 is included in bundle 17 (Released)
REFERENCES
NOTE:29232.1 - IPC Explained
NOTE:1600630.1 - Valid Node Checking For Registration (VNCR)
NOTE:1455068.1 - Force Connections to a Specific Database Service When two Identical Services are
Registered to CMAN
NOTE:1340831.1 - Using Class of Secure Transport (COST) to Restrict Instance Registration in Oracle RAC
未找到您要查找的产品?
在社区中提问...
相关内容
产品
Oracle Database Products > Oracle Database Suite > Oracle Database > Oracle Database - Enterprise Edition > Database Security > Other issues
Oracle Database Products > Oracle Database Suite > Oracle Database > Oracle Database - Standard Edition
Oracle Database Products > Oracle Database Suite > Net Services > Oracle Net Services
关键字
INSTANCE REGISTRATION; IPC; LISTENER; LOCAL_LISTENER; SECURE; SECURITY
https://support.oracle.com/epmos/faces/DocumentDisplay?_afrLoop=344058498322677&id=1453883.1&_afrWindowMode=0&_adf.ctrl-state=8uxcrggjt_1306
6/7
�
2018/5/2
错误
ORA-12514; TNS-01194
翻译
英语 源
返回页首
文档 1453883.1
日语 日本語
韩语 한국어
Copyright (c) 2018, Oracle. All rights reserved.
Legal Notices and Terms of Use
Privacy Statement
https://support.oracle.com/epmos/faces/DocumentDisplay?_afrLoop=344058498322677&id=1453883.1&_afrWindowMode=0&_adf.ctrl-state=8uxcrggjt_1306
7/7
�










 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc