© ISO SAE 21434 – All rights reserved
ISO SAE 21434:2018(X)
ISO TC 22/SC 32/WG 11
SAE
Secretariat: ISO SAE
Road vehicles – Cybersecurity engineering
CD stage
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
This document is not an ISO International Standard. It is distributed for review and comment. It is subject to
change without notice and may not be referred to as an International Standard.
Recipients of this draft are invited to submit, with their comments, notification of any relevant patent rights of
which they are aware and to provide supporting documentation.
Warning for WDs and CDs
To help you, this guide on writing standards was produced by the ISO/TMB and is available at
https://www.iso.org/iso/how‐to‐write‐standards.pdf
A model manuscript of a draft International Standard (known as “The Rice Model”) is available at
https://www.iso.org/iso/model_document‐rice_model.pdf
�
20
21
22
23
24
25
26
27
28
29
30
31
32
ISO SAE 21434:2018(X)
© ISO SAE 2018
All rights reserved. Unless otherwise specified, or required in the context of its implementation, no part of this
publication may be reproduced or utilized otherwise in any form or by any means, electronic or mechanical,
including photocopying, or posting on the internet or an intranet, without prior written permission. Permission
can be requested from either ISO at the address below or ISO’s member body in the country of the requester.
ISO copyright office
CP 401 • Ch. de Blandonnet 8
CH-1214 Vernier, Geneva
Phone: +41 22 749 01 11
Fax: +41 22 749 09 47
Email: copyright@iso.org
Website: www.iso.org
Published in Switzerland
ii
© ISO SAE 21434 – All rights reserved
�
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
Contents
ISO SAE 21434:2018(X)
Foreword ....................................................................................................................................................................... vii
Introduction................................................................................................................................................................. viii
1 Scope .......................................................................................................................................................................... 1
2 Normative references .......................................................................................................................................... 1
3 Terms and abbreviations .................................................................................................................................... 1
Terms and definitions .......................................................................................................................................... 1
3.1
3.2
Abbreviated terms ................................................................................................................................................ 6
4 General considerations (informative) ........................................................................................................... 6
4.1
The vehicle ecosystem ......................................................................................................................................... 6
4.2
Organizational overview of cybersecurity management ........................................................................ 8
4.3
Lifecycle ..................................................................................................................................................................... 8
4.4
Stages of the post‐production phase ............................................................................................................... 9
5 Management of Cybersecurity ....................................................................................................................... 10
5.1
Overall Cybersecurity Management ............................................................................................................ 10
5.1.1 Objectives ........................................................................................................................................................ 10
5.1.2 General ............................................................................................................................................................. 11
5.1.3
Inputs ................................................................................................................................................................ 11
5.1.4 Requirements and recommendations .................................................................................................. 11
5.1.5 Work products ............................................................................................................................................... 16
5.2
Cybersecurity management during the concept phase and product development .................... 16
5.2.1 Objectives ........................................................................................................................................................ 16
5.2.2 General ............................................................................................................................................................. 16
5.2.3
Inputs ................................................................................................................................................................ 17
5.2.4 Requirements and recommendations .................................................................................................. 17
5.2.5 Work products ............................................................................................................................................... 24
5.3
Cybersecurity management during production, operations and maintenance ........................... 24
5.3.1 Objectives ........................................................................................................................................................ 24
5.3.2 General ............................................................................................................................................................. 24
5.3.3
Inputs ................................................................................................................................................................ 24
5.3.4 Requirements and recommendations .................................................................................................. 25
5.4
Information Collection and Retention ........................................................................................................ 26
5.4.1 Objective .......................................................................................................................................................... 26
5.4.2 General ............................................................................................................................................................. 26
5.4.3
Inputs ................................................................................................................................................................ 26
5.4.4 Requirements and recommendations .................................................................................................. 26
6 Risk assessment methods ................................................................................................................................ 27
6.1
Risk assessment methods introduction (informative) ......................................................................... 27
6.2
Asset identification ............................................................................................................................................ 29
6.2.1 Objectives ........................................................................................................................................................ 29
6.2.2 General ............................................................................................................................................................. 29
6.2.3
Inputs ................................................................................................................................................................ 30
6.2.4 Requirements and Recommendations ................................................................................................. 31
6.2.5 Work Products ............................................................................................................................................... 31
6.3
Threat Analysis .................................................................................................................................................... 32
6.3.1 Objectives ........................................................................................................................................................ 32
6.3.2 General ............................................................................................................................................................. 32
6.3.3
Inputs ................................................................................................................................................................ 32
6.3.4 Requirements and recommendations .................................................................................................. 33
6.3.5 Work products ............................................................................................................................................... 33
© ISO SAE 21434 – All rights reserved
iii
�
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
ISO SAE 21434:2018(X)
Impact Assessment ............................................................................................................................................. 33
6.4
6.4.1 Objectives ........................................................................................................................................................ 33
6.4.2 General ............................................................................................................................................................. 33
6.4.3
Inputs ................................................................................................................................................................ 34
6.4.4 Requirements and Recommendations ................................................................................................. 34
6.4.5 Work products ............................................................................................................................................... 36
6.5
Vulnerability analysis ....................................................................................................................................... 36
6.5.1 Objectives ........................................................................................................................................................ 36
6.5.2 General ............................................................................................................................................................. 36
6.5.3
Inputs ................................................................................................................................................................ 38
6.5.4 Requirements and Recommendations ................................................................................................. 39
6.5.5 Work products ............................................................................................................................................... 40
6.6
Attack analysis ..................................................................................................................................................... 40
6.6.1 Objectives ........................................................................................................................................................ 40
6.6.2 General ............................................................................................................................................................. 40
6.6.3
Inputs ................................................................................................................................................................ 40
6.6.4 Requirements and recommendations .................................................................................................. 41
6.6.5 Work products ............................................................................................................................................... 42
6.7
Attack Feasibility Assessment ........................................................................................................................ 42
6.7.1 Objectives ........................................................................................................................................................ 42
6.7.2 General ............................................................................................................................................................. 42
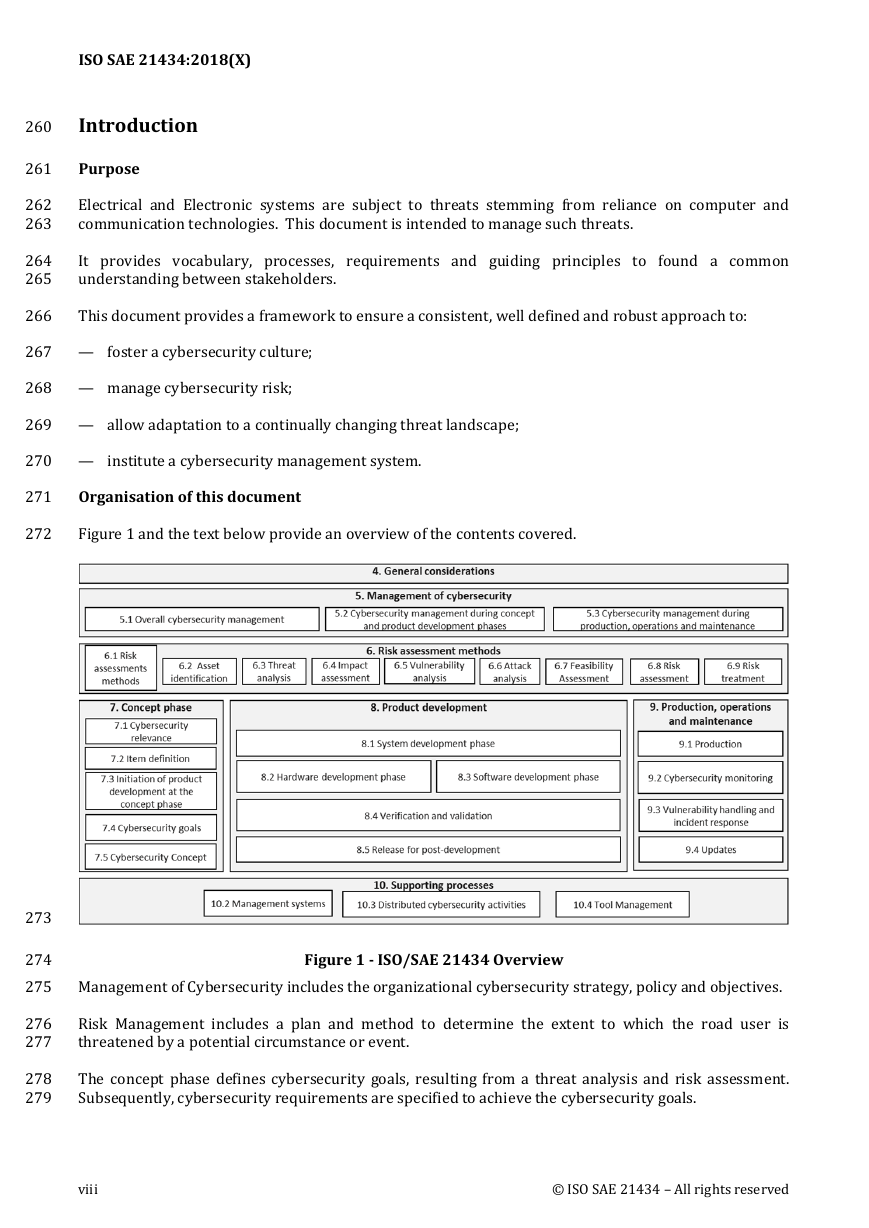
6.7.3
Inputs ................................................................................................................................................................ 42
6.7.4 Requirements and recommendations .................................................................................................. 42
6.7.5 Work products ............................................................................................................................................... 44
6.8
Risk assessment .................................................................................................................................................. 44
6.8.1 Objectives ........................................................................................................................................................ 44
6.8.2 General ............................................................................................................................................................. 44
6.8.3
Inputs ................................................................................................................................................................ 45
6.8.4 Requirements and Recommendations ................................................................................................. 45
6.8.5 Work products ............................................................................................................................................... 45
6.9
Risk Treatment .................................................................................................................................................... 45
6.9.1 Objectives ........................................................................................................................................................ 45
6.9.2 General ............................................................................................................................................................. 45
6.9.3
Inputs ................................................................................................................................................................ 46
6.9.4 Requirements and Recommendations ................................................................................................. 47
6.9.5 Work products ............................................................................................................................................... 47
7 Concept Phase ...................................................................................................................................................... 47
7.1
Cybersecurity Relevance .................................................................................................................................. 47
7.1.1 Objectives ........................................................................................................................................................ 47
7.1.2 General ............................................................................................................................................................. 48
7.1.3
Inputs ................................................................................................................................................................ 48
7.1.4 Requirements and Recommendations ................................................................................................. 48
7.1.5 Work products ............................................................................................................................................... 48
7.2
Item Definition ..................................................................................................................................................... 48
7.2.1 Objectives ........................................................................................................................................................ 48
7.2.2 General ............................................................................................................................................................. 48
7.2.3
Inputs ................................................................................................................................................................ 49
7.2.4 Requirements and Recommendations ................................................................................................. 49
7.2.5 Work products ............................................................................................................................................... 50
7.3
Initiation of product development at the concept phase ..................................................................... 50
7.3.1 Objectives ........................................................................................................................................................ 50
7.3.2 General ............................................................................................................................................................. 50
7.3.3
Inputs ................................................................................................................................................................ 50
7.3.4 Requirements and recommendations .................................................................................................. 50
© ISO SAE 21434 – All rights reserved
iv
�
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
ISO SAE 21434:2018(X)
7.3.5 Work Products ............................................................................................................................................... 51
7.4
Cybersecurity goals ............................................................................................................................................ 51
7.4.1 Objectives ........................................................................................................................................................ 51
7.4.2 General ............................................................................................................................................................. 51
7.4.3
Inputs ................................................................................................................................................................ 51
7.4.4 Requirements and recommendations .................................................................................................. 51
7.4.5 Work Products ............................................................................................................................................... 53
7.5
Cybersecurity concept ...................................................................................................................................... 53
7.5.1 Objectives ........................................................................................................................................................ 53
7.5.2 General ............................................................................................................................................................. 53
7.5.3
Inputs ................................................................................................................................................................ 53
7.5.4 Requirements and recommendations .................................................................................................. 54
7.5.5 Work Products ............................................................................................................................................... 55
8 Product development ........................................................................................................................................ 55
8.1
System development phase ............................................................................................................................. 55
8.1.1 Objectives ........................................................................................................................................................ 55
8.1.2 General ............................................................................................................................................................. 55
8.1.3
Inputs ................................................................................................................................................................ 56
8.1.4 Requirements and recommendations .................................................................................................. 57
8.1.5 Work products ............................................................................................................................................... 63
8.2
Hardware development phase ....................................................................................................................... 63
8.2.1 Objectives ........................................................................................................................................................ 63
8.2.2 General ............................................................................................................................................................. 64
8.2.3
Inputs ................................................................................................................................................................ 64
8.2.4 Requirements and recommendations .................................................................................................. 65
8.2.5 Work products ............................................................................................................................................... 68
8.3
Software development phase ......................................................................................................................... 68
8.3.1 Objectives ........................................................................................................................................................ 68
8.3.2 General ............................................................................................................................................................. 69
8.3.3
Inputs ................................................................................................................................................................ 69
8.3.4 Requirements and recommendations .................................................................................................. 70
8.3.5 Work products ............................................................................................................................................... 82
8.4
Verification and validation ............................................................................................................................. 83
8.4.1 Objective .......................................................................................................................................................... 83
8.4.2 General ............................................................................................................................................................. 83
8.4.3
Inputs ................................................................................................................................................................ 84
8.4.4 Requirements and recommendations .................................................................................................. 84
8.4.5 Work products ............................................................................................................................................... 87
8.5
Release for post‐development ....................................................................................................................... 87
8.5.1 Objective .......................................................................................................................................................... 87
8.5.2 General ............................................................................................................................................................. 87
8.5.3
Inputs ................................................................................................................................................................ 88
8.5.4 Requirements and recommendations .................................................................................................. 88
8.5.5 Work products ............................................................................................................................................... 89
9 Production, operations and maintenance ................................................................................................. 89
9.1
Production ............................................................................................................................................................. 89
9.1.1 Objectives ........................................................................................................................................................ 89
9.1.2 General ............................................................................................................................................................. 89
9.1.3
Inputs ................................................................................................................................................................ 89
9.1.4 Requirements and recommendations .................................................................................................. 89
9.1.5 Work products ............................................................................................................................................... 91
9.2
Cybersecurity Monitoring ................................................................................................................................ 91
9.2.1 Objectives ........................................................................................................................................................ 91
9.2.2 General ............................................................................................................................................................. 91
© ISO SAE 21434 – All rights reserved
v
�
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
ISO SAE 21434:2018(X)
9.2.3
Inputs ................................................................................................................................................................ 92
9.2.4 Requirements and recommendations .................................................................................................. 92
9.2.5 Work Products ............................................................................................................................................... 94
9.3
Vulnerability handling and incident response ........................................................................................ 94
9.3.1 Objectives ........................................................................................................................................................ 94
9.3.2 General ............................................................................................................................................................. 94
9.3.3
Inputs to this clause ..................................................................................................................................... 94
9.3.4 Requirements and recommendations .................................................................................................. 94
9.3.5 Work products ............................................................................................................................................... 98
9.4
Updates ................................................................................................................................................................... 98
9.4.1 Objectives ........................................................................................................................................................ 98
9.4.2 General ............................................................................................................................................................. 99
9.4.3
Inputs ................................................................................................................................................................ 99
9.4.4 Requirements and recommendations .................................................................................................. 99
9.4.5 Work products ............................................................................................................................................. 102
10 Supporting processes ...................................................................................................................................... 102
10.1
Objectives ...................................................................................................................................................... 102
10.2
Management Systems................................................................................................................................ 102
10.3
Distributed cybersecurity activities .................................................................................................... 103
10.3.1 General ........................................................................................................................................................... 103
10.3.2 Requirements and recommendations ................................................................................................ 103
10.4
Tool Management ....................................................................................................................................... 106
10.4.1 General ........................................................................................................................................................... 106
10.4.2 Input to this subclause ............................................................................................................................. 106
10.4.3 Requirements and recommendations ................................................................................................ 107
10.5
Work products ............................................................................................................................................. 109
Annex A (informative) Summary of cybersecurity activities .................................................................. 110
Annex B (informative) Examples of a cybersecurity culture ................................................................... 113
Annex C (informative) DIA Template Example ............................................................................................. 115
Annex D (informative) Cybersecurity Relevance Assessment: Methodology and Examples ....... 117
Annex E (informative) Cybersecurity Assurance Levels ........................................................................... 121
Annex F (informative) Methods for Verification and Validation ............................................................ 130
Annex G (informative) Artefacts needed for production and post‐production phase ................... 132
Annex H (informative) Example Use Cases and Work Products: Head Lamp System ..................... 134
Annex I (informative) Information to reader about terms with Oxford dictionary definition ... 139
Annex J (informative) Methods for testing cybersecurity vulnerabilities in the
cybersecurity event assessment ........................................................................................................... 140
vi
© ISO SAE 21434 – All rights reserved
�
Foreword
ISO SAE 21434:2018(X)
229
230
ISO (the International Organization for Standardization) is a worldwide federation of national
231
standards bodies (ISO member bodies). The work of preparing International Standards is normally
232
carried out through ISO technical committees. Each member body interested in a subject for which a
233
technical committee has been established has the right to be represented on that committee.
234
International organizations, governmental and non-governmental, in liaison with ISO, also take part in
235 matters of electrotechnical standardization.
the work. ISO collaborates closely with the International Electrotechnical Commission (IEC) on all
236
237
The procedures used to develop this document and those intended for its further maintenance are
238
described in the ISO/IEC Directives, Part 1. In particular, the different approval criteria needed for the
239
different types of ISO documents should be noted. This document was drafted in accordance with the
240
editorial rules of the ISO/IEC Directives, Part 2 (see www.iso.org/directives).
241
Attention is drawn to the possibility that some of the elements of this document may be the subject of
242
patent rights. ISO shall not be held responsible for identifying any or all such patent rights. Details of
any patent rights identified during the development of the document will be in the Introduction and/or
243
244
on the ISO list of patent declarations received (see www.iso.org/patents).
245
Any trade name used in this document is information given for the convenience of users and does not
constitute an endorsement.
246
For an explanation of the voluntary nature of standards, the meaning of ISO specific terms and
247
expressions related to conformity assessment, as well as information about ISO's adherence to the
248 World Trade Organization (WTO) principles in the Technical Barriers to Trade (TBT), see
249 www.iso.org/iso/foreword.html.
250
251
This document was prepared by Technical Committee [or Project Committee] ISO/TC [or ISO/PC] ###,
[name of committee], Subcommittee SC ##, [name of subcommittee].
252
This second/third/… edition cancels and replaces the first/second/… edition (ISO #####:####), which
253
254
has been technically revised.
255 — xxx xxxxxxx xxx xxxx
The main changes compared to the previous edition are as follows:
256
A list of all parts in the ISO ##### series can be found on the ISO website.
257
258
Any feedback or questions on this document should be directed to the user’s national standards body. A
259
complete listing of these bodies can be found at www.iso.org/members.html.
© ISO SAE 21434 – All rights reserved
vii
�
Introduction
Purpose
ISO SAE 21434:2018(X)
260
261
Electrical and Electronic systems are subject to threats stemming from reliance on computer and
262
communication technologies. This document is intended to manage such threats.
263
It provides vocabulary, processes, requirements and guiding principles to found a common
264
understanding between stakeholders.
265
266 — foster a cybersecurity culture;
This document provides a framework to ensure a consistent, well defined and robust approach to:
267 — manage cybersecurity risk;
268 — allow adaptation to a continually changing threat landscape;
269 — institute a cybersecurity management system.
270
271
Figure 1 and the text below provide an overview of the contents covered.
272
Organisation of this document
Figure 1 ‐ ISO/SAE 21434 Overview
273
274 Management of Cybersecurity includes the organizational cybersecurity strategy, policy and objectives.
275
276
Risk Management includes a plan and method to determine the extent to which the road user is
277
threatened by a potential circumstance or event.
278
The concept phase defines cybersecurity goals, resulting from a threat analysis and risk assessment.
279
Subsequently, cybersecurity requirements are specified to achieve the cybersecurity goals.
viii
© ISO SAE 21434 – All rights reserved
�














 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc