本资源来自数缘社区
http://maths.utime.cn:81
欢迎来到数缘社区。本社区是一个高等数学及密码学的技术性论坛,由山东大学数学院研究
生创办。在这里您可以尽情的遨游数学的海洋。作为站长,我诚挚的邀请您加入,希望大家能一
起支持发展我们的论坛,充实每个版块。把您宝贵的资料与大家一起分享!
数学电子书库
每天都有来源于各类网站的与数学相关的新内容供大家浏览和下载,您既可以点击左键弹出
网页在线阅读,又可以点右键选择下载。现在书库中藏书 1000 余本。如果本站没有您急需的电
子书,可以发帖说明,我们有专人负责为您寻找您需要的电子书。
密码学论文库
国内首创信息安全专业的密码学论文库,主要收集欧密会(Eurocrypt)、美密会(Crypto)、
亚密会(Asiacrypt)等国内外知名论文。现在论文库中收藏论文 4000 余篇(包括论文库版块 700
余篇、论坛顶部菜单“密码学会议论文集”3000 余篇)。如果本站没有您急需的密码学论文,可
以发帖说明,我们有专人负责为您寻找您需要的论文。
提示:本站已经收集到 1981-2003 年欧密会、美密会全部论文以及 1997 年-2003 年五大
会议全部论文(欧密会、美密会、亚密会、PKC、FSE)。
数学综合讨论区
论坛管理团队及部分会员来源于山东大学数学院七大专业(基础数学、应用数学、运筹学、
控制论、计算数学、统计学、信息安全),在数学方面均为思维活跃、成绩优秀的研究生,相信
会给您的数学学习带来很大的帮助。
密码学与网络安全
山东大学数学院的信息安全专业师资雄厚,前景广阔,具有密码理论、密码技术与网络安全
技术三个研究方向。有一大批博士、硕士及本科生活跃于本论坛。本版块适合从事密码学或网络
安全方面学习研究的朋友访问。
网络公式编辑器
数缘社区公式编辑器采用 Latex 语言,适用于任何支持图片格式的论坛或网页。在本论坛编
辑好公式后,您可以将自动生成的公式图片的链接直接复制到你要发的帖子里以图片的形式发
表。
如果您觉得本站对您的学习和成长有所帮助,请把它添加到您的收藏夹。如果您对本论坛有
任何的意见或者建议,请来论坛留下您宝贵的意见。
附录 A:本站电子书库藏书目录
http://maths.utime.cn:81/bbs/dispbbs.asp?boardID=18&ID=2285
附录 B:版权问题
数缘社区所有电子资源均来自网络,版权归原作者所有,本站不承担任何版权责任。
�
SOLUTIONS MANUAL
CRYPTOGRAPHY AND NETWORK
SECURITY
Third Edition
WILLIAM STALLINGS
Copyright 2002: William Stallings
-1-
�
TABLE OF CONTENTS
Classical Encryption Techniques...............................................................4
Chapter 2:
Block Ciphers and the Date Encryption Standard...................................8
Chapter 3:
Introduction to Finite Fields.....................................................................15
Chapter 4:
Advanced Encryption Standard ..............................................................20
Chapter 5:
Contemporary Symmetric Ciphers..........................................................25
Chapter 6:
Confidentiality Using Symmetric Encryption .......................................30
Chapter 7:
Introduction to Number Theory..............................................................33
Chapter 8:
Public-Key Cryptography and RSA........................................................37
Chapter 9:
Key Management; Other Public-Key Cryptosystems...........................42
Chapter 10:
Chapter 11: Message Authentication and Hash Functions.......................................45
Chapter 12: Hash and MAC Algorithms......................................................................48
Chapter 13:
Digital Signatures and Authentication Protocols..................................50
Chapter 14:
Authentication Applications ....................................................................54
Chapter 15:
Electronic Mail Security ............................................................................57
Chapter 16:
IP Security ...................................................................................................60
Chapter 17: Web Security...............................................................................................65
Chapter 18:
Intruders......................................................................................................68
Chapter 19: Malicious Software.....................................................................................72
Chapter 20:
Firewalls ......................................................................................................74
-2-
�
NOTICE
This manual contains solutions to all of the review questions and
homework problems in Cryptography and Network Security, Third Edition. If
you spot an error in a solution or in the wording of a problem, I would
greatly appreciate it if you would forward the information via email to
me at ws@shore.net. An errata sheet for this manual, if needed, is
available at ftp://shell.shore.net/members/w/s/ws/S/
W.S.
-3-
�
CHAPTER 2
CLASSICAL ENCRYPTION TECHNIQUES
AA NSWERS TO
NSWERS TO QQ U E S T I O N S
U E S T I O N S
2.1 Plaintext, encryption algorithm, secret key, ciphertext, decryption algorithm.
2.2 Permutation and substitution.
2.3 One key for symmetric ciphers, two keys for asymmetric ciphers.
2.4 A stream cipher is one that encrypts a digital data stream one bit or one byte at a
time. A block cipher is one in which a block of plaintext is treated as a whole and
used to produce a ciphertext block of equal length.
2.5 Cryptanalysis and brute force.
2.6 Ciphertext only. One possible attack under these circumstances is the brute-force
approach of trying all possible keys. If the key space is very large, this becomes
impractical. Thus, the opponent must rely on an analysis of the ciphertext itself,
generally applying various statistical tests to it. Known plaintext. The analyst may
be able to capture one or more plaintext messages as well as their encryptions.
With this knowledge, the analyst may be able to deduce the key on the basis of the
way in which the known plaintext is transformed. Chosen plaintext. If the analyst
is able to choose the messages to encrypt, the analyst may deliberately pick
patterns that can be expected to reveal the structure of the key.
2.7 An encryption scheme is unconditionally secure if the ciphertext generated by the
scheme does not contain enough information to determine uniquely the
corresponding plaintext, no matter how much ciphertext is available. An
encryption scheme is said to be computationally secure if: (1) the cost of breaking
the cipher exceeds the value of the encrypted information, and (2) the time
required to break the cipher exceeds the useful lifetime of the information.
2.8 The Caesar cipher involves replacing each letter of the alphabet with the letter
standing k places further down the alphabet, for k in the range 1 through 25.
2.9 A monoalphabetic substitution cipher maps a plaintext alphabet to a ciphertext
alphabet, so that each letter of the plaintext alphabet maps to a single unique letter
of the ciphertext alphabet.
2.10 The Playfair algorithm is based on the use of a 5 ¥ 5 matrix of letters constructed
using a keyword. Plaintext is encrypted two letters at a time using this matrix.
2.11 A polyalphabetic substitution cipher uses a separate monoalphabetic substitution
cipher for each successive letter of plaintext, depending on a key.
-4-
�
2.12 1. There is the practical problem of making large quantities of random keys. Any
heavily-used system might require millions of random characters on a regular
basis. Supplying truly random characters in this volume is a significant task.
2. Even more daunting is the problem of key distribution and protection. For every
message to be sent, a key of equal length is needed by both sender and receiver.
Thus, a mammoth key distribution problem exists.
2.13 A transposition cipher involves a permutation of the plaintext letters.
2.14 Steganography involves concealing the existence of a message.
AA NSWERS TO
NSWERS TO PP R O B L E M S
R O B L E M S
2.1 A good glass in the Bishop's hostel in the Devil's seat—twenty-one degrees and
thirteen minutes—northeast and by north—main branch seventh limb east
side—shoot from the left eye of the death's head— a bee line from the tree through
the shot fifty feet out. (from The Gold-Bug, by Edgar Allan Poe)
a. The first letter t corresponds to A, the second letter h corresponds to B, e is C, s
is D, and so on. Second and subsequent occurrences of a letter in the key
sentence are ignored. The result
2.2
ciphertext: SIDKHKDM AF HCRKIABIE SHIMC KD LFEAILA
plaintext: basalisk to leviathan blake is contact
b. It is a monalphabetic cipher and so easily breakable.
c. The last sentence may not contain all the letters of the alphabet. If the first
sentence is used, the second and subsequent sentences may also be used until
all 26 letters are encountered.
2.3 The cipher refers to the words in the page of a book. The first entry, 534, refers to
page 534. The second entry, C2, refers to column two. The remaining numbers are
words in that column. The names DOUGLAS and BIRLSTONE are simply words
that do not appear on that page. Elementary! (from The Valley of Fear, by Sir Arthur
Conan Doyle)
2.4 SPUTNIK
2.5 25! ª 284
2.6
a. We need an even number of letters, so append a "q" to the end of the message.
Then convert the letters into the corresponding alphabetic positions:
m
13
p
16
t
20
e
5
l
12
h
8
e
5
a
1
a
1
t
20
c
3
n
14
m
13
e
5
e
5
e
5
a
1
i
9
a
1
t
20
g
7
t
20
t
20
h
8
t
20
e
5
t
20
h
8
n
14
o
15
e
5
r
18
c
3
u
21
a
1
l
12
s
19
t
20
o
15
u
21
h
8
c
3
a
1
e
5
k
11
l
12
r
18
q
17
-5-
�
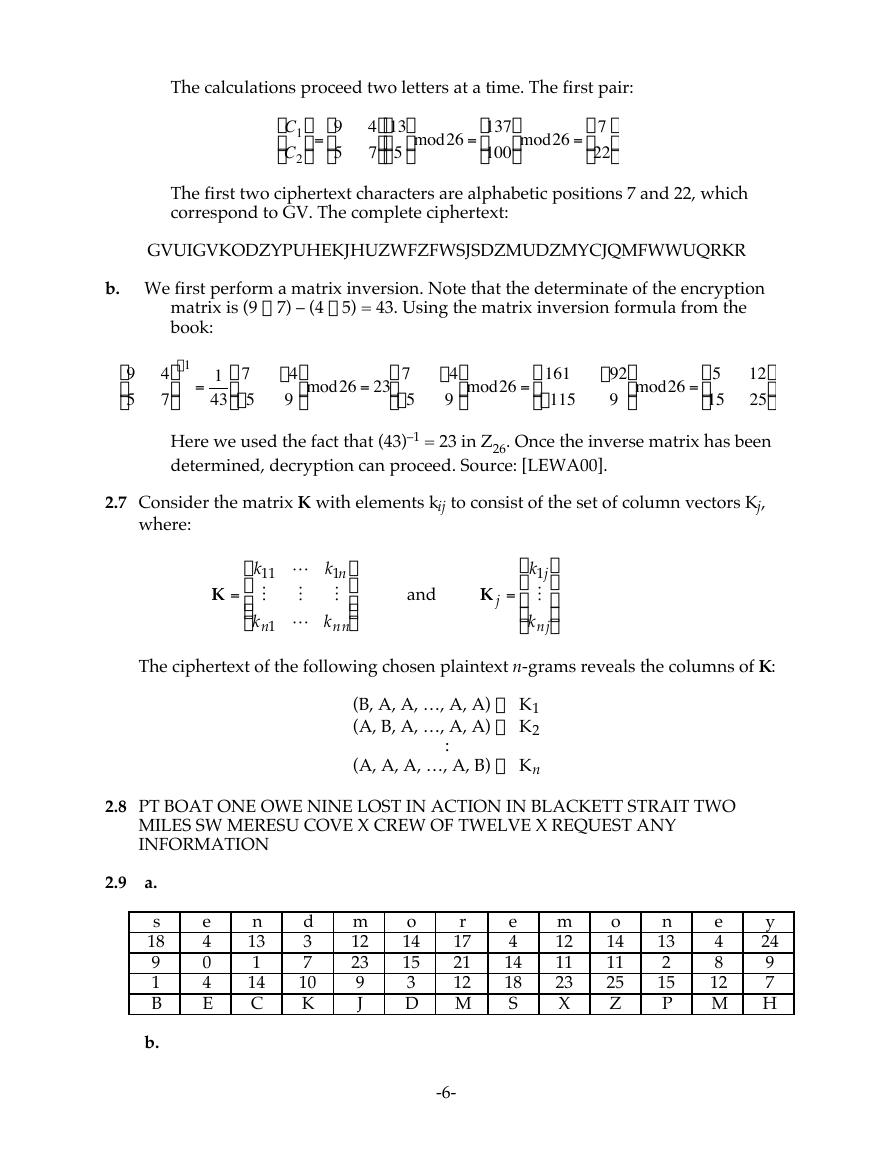
The calculations proceed two letters at a time. The first pair:
C1
Ê
Á
C2
Ë
ˆ
˜ =
¯
9
Ê
Á
5
Ë
4
7
13
ˆ
ˆ
Ê
˜ mod26 =
˜
Á
5
¯
¯
Ë
137
Ê
Á
100
Ë
ˆ
˜ mod26 =
¯
7
ˆ
Ê
Á
˜
22
¯
Ë
The first two ciphertext characters are alphabetic positions 7 and 22, which
correspond to GV. The complete ciphertext:
†
GVUIGVKODZYPUHEKJHUZWFZFWSJSDZMUDZMYCJQMFWWUQRKR
†
b. We first perform a matrix inversion. Note that the determinate of the encryption
matrix is (9 ¥ 7) – (4 ¥ 5) = 43. Using the matrix inversion formula from the
book:
9
Ê
Á
5
Ë
4
7
=
-4
9
1
43
7
Ê
Á
-5
Ë
7
Ê
ˆ
˜ mod26 = 23
Á
-5
¯
Ë
-1
ˆ
ˆ
˜
˜
¯
¯
Here we used the fact that (43)–1 = 23 in Z26. Once the inverse matrix has been
determined, decryption can proceed. Source: [LEWA00].
ˆ
˜ mod26 =
¯
161
Ê
Á
-115
Ë
-4
9
-92
9
ˆ
˜ mod26 =
¯
5
Ê
Á
15
Ë
12
25
2.7 Consider the matrix K with elements kij to consist of the set of column vectors Kj,
where:
k11 L k1n
ˆ
Ê
˜
Á
M
M
Á Á
˜ ˜
kn1 L knn
Ë
¯
M
K =
and
k1j
ˆ
Ê
˜
Á
˜
Á
M
Á
˜
knj
¯
Ë
K j =
The ciphertext of the following chosen plaintext n-grams reveals the columns of K:
(B, A, A, …, A, A) ´ K1
(A, B, A, …, A, A) ´ K2
(A, A, A, …, A, B) ´ Kn
:
2.8 PT BOAT ONE OWE NINE LOST IN ACTION IN BLACKETT STRAIT TWO
MILES SW MERESU COVE X CREW OF TWELVE X REQUEST ANY
INFORMATION
2.9
a.
s
18
9
1
B
b.
e
4
0
4
E
n
13
1
14
C
d
3
7
10
K
m
12
23
9
J
o
14
15
3
D
r
17
21
12
M
e
4
14
18
S
m
12
11
23
X
o
14
11
25
Z
n
13
2
15
P
e
4
8
12
M
y
24
9
7
H
-6-
�
c
2
25
1
B
a
0
4
4
E
s
18
22
14
C
h
7
3
10
K
n
13
22
9
J
o
14
15
3
D
t
19
19
12
M
n
13
5
18
S
e
4
19
23
X
e
4
21
25
Z
d
3
12
15
P
e
4
8
12
M
d
3
4
7
H
2.10 your package ready Friday 21st room three Please destroy this immediately.
2.11 a. Lay the message out in a matrix 8 letters across. Each integer in the key tells
you which letter to choose in the corresponding row. Result:
He sitteth between the cherubims. The isles may be glad
thereof. As the rivers in the south.
b. Quite secure. In each row there is one of eight possibilities. So if the ciphertext
is 8n letters in length, then the number of possible plaintexts is 8n.
c. Not too secure. Lord Peter figured it out. (from The Nine Tailors)
-7-
�















 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc