Cover
FrontPage
Preface
Acknowledgements
Table of Contents
Table of Illustrations
CHAPTER 1 Unix Systems Programming The big Picture
1.1 INTRODUCTION
1.2 WHAT IS SYSTEMS PROGRAMMING
1.2.1 The Simple Program Model
1.2.2 Face Reality
1.2.3 The Role of the Operating System
1.2.4 Providing Services to Programs
1.3 UNDERSTANDING SYSTEMS PROGRAMMING
1.3.1 System Resources
1.3.2 Our Goal: Understanding Systems Programming
1.3.3 Our Method: Three Simple Steps
1.4 UNIX FROM USER PERSPECTIVE
1.4.1 What Does Unix Do?
1.4.2 Log In--Run Programis--Log Out
1.4.3 Working with Directory
1.4.4 Working with Files
1.5 UNIX FROM THE LARGER PERSPECTIVE
1.5.1 Connections between Users and Programs
1.5.2 Internet Bridge Tournaments
1.5.3 bc: The Secret Life of a Unix Desk Calculator
1.5.4 From bc/dc to the Web
1.6 CAN I TRY TO DO ONE?
1.7 A LOT OF QUESTIONS AND A MAP
1.7.1 What Now?
1.7.2 And Now for the Map
1.7.3 What Is Unix? History and Dialects
SUMMARY
CHAPTER 2 Users, Files, and the Manual: who Is First
2.1 INTRODUCTION
2.2 ASKING ABOUT who
2.2.1 Commands Are Programs
2.3 QUESTION 1: WHAT DOES who DO?
2.3.1 Reading the Manual
2.4 QUESTION 2: HOW DOES who DO IT?
2.4.1 We Now Know How who Works
2.5 QUESTION 3: CAN I WRITE who?
2.5.1 Question: How Do I Read Structs from a File?
2.5.2 Answer: Use open, read, and close
2.5.3 Writing who1.c
2.5.4 Displaying Log-In Records
2.5.5 Writing who2.c
2.5.6 A Look Back and a Look Forward
2.6 PROJECT TWO: WRITING cp (READ AND WRITE)
2.6.1 Question 1: What Does cp Do?
2.6.2 Question 2: How Does cp Create and Write
2.6.3 Question 3: Can I Write cp?
2.6.4 Unix Programming Seems Pretty Easy
2.7 MORE EFFICIENT FILE I/O: BUFFERING
2.7.1 Does the Size of the Buffer Matter?
2.7.2 Why System Calls Are Time Consuming
2.7.3 Does This Mean That who2.c Is Inefficient
2.7.4 Adding Buffering to who2.c
2.8 BUFFERING AND THE KERNEL
2.8.1 If Buffering Is So Smart, Why Doesn't the kernel Do it?
2.9 READING AND WRITING A FILE
2.9.1 Logging Out: What It Does
2.9.2 Logging Out: How it Works
2.9.3 Moving the Current Position: lseek
2.9.4 Code to Log Out from a Terminal
2.10 WHAT TO DO WITH SYSTEM-CALL ERRORS
EXPLORATIONS
PROGRAMMING EXERCISES
PROJECTS
CHAPTER 3 Directories and File Properties: Looking through ls
3.1 INTRODUCTION
3.2 QUESTION 1: WHAT DOES ls DO?
3.2.1 ls Lists Names of Files and Reports File Attributes
3.2.2 Listing Other Directories, Reporting on Other Files
3.2.3 Popular Command-Line Options
3.2.4 Answer One: A Summary
3.3 BRIEF REVIEW OF THE FILE SYSTEM TREE
3.4 QUESTION 2: HOW DOES ls WORK
3.4.1 What Is a Directory, Anyway?
3.4.2 Do open, read, and close Work for Directory?
3.4.3 OK, OK, How Do I Read a Directory?
3.5 QUESTION 3: CAN I WRITE ls?
3.5.1 How Dis We Do?
3.6 PROJECT TWO: WRITING ls -l
3.6.1 Question 1: What Does ls -l Do?
3.6.2 Question 2: How Does ls -l Work?
3.6.3 Answer: The stat Call Gets File Information
3.6.4 What Other Information Does stat Provide
3.6.5 How'd We Do?
3.6.6 Converting File Mode to a String
3.6.7 Converting User/Group ID to Strings
3.6.8 Putting It All Together: ls2.c
3.7 THE THREE SPECIAL BITS
3.7.1 The Set-User-ID Bit
3.7.2 The Set-Group-ID Bit
3.7.3 The Sticky Bit
3.7.4 The Special Bits and ls -l
3.8 SUMMARY OF ls
3.9 SETTING AND MODIFYING THE PROPERTIES OF A FILE
3.9.1 Type of a File
3.9.2 Permission Bits and Special Bits
3.9.3 Number of Links to a File
3.9.4 Owner and Group of a File
3.9.5 Size of a File
3.9.6 Modification and Access Time
3.9.7 Name of a File
SUMMARY
EXPLORATIONS
PROGRAMMING EXERCISES
PROJECTS
CHAPTER 4 Focus on File Systems: Writing pwd
4.1 INTRODUCTION
4.2 A USER'S VIEW OF THE FILE SYSTEM
4.2.1 Directories and Files
4.2.2 Directory Commands
4.2.3 File Commands
4.2.4 Tree Commands
4.2.5 Almost No Limits to Tree Structure
4.2.6 Summary of the Unix File System
4.3 INTERNAL STRUCTURE OF THE UNIX FILE SYSTEM
4.3.1 Abstraction Zero: From Platter's to Partitions
4.3.2 Abstraction One: From Platters an Array of Blocks
4.3.3 Abstraction Two: From an Array of Blocks to Three Regions
4.3.4 The File System in Practice: Create a File
4.3.5 The File System in Practice: How Directories Work
4.3.6 THe File System in Practice: How cat Works
4.3.7 Inodes and Big Files
4.3.8 Variations on the Unix File System
4.4 UNDERSTANDING DIRECTORIES
4.4.1 Understanding Directory Structure
4.4.2 Commands and System Calls for Directory Trees
4.5 WRITING pwd
4.5.1 How pwd Works
4.5.2 A Version of pwd
4.6 MULTIPLE FILE SYSTEMS: A TREE OF TREES
4.6.1 Mount Points
4.6.2 Duplicate Inode Numbers and Cross-Device Links
4.6.3 Symbolic Links: Panacea or Pasta City
SUMMARY
EXPLORATIONS
PROGRAMMING EXERCISES
PROJECTS
CHAPTER 5 Connection Control: Studying stty
5.1 PROGRAMMING FOR DEVICES
5.2 DEVICES ARE JUST LIKE FILES
5.2.1 Devices Have Filenames
5.2.2 Devices and System Calls
5.2.3 Example: Terminals Are Just Like Files
5.2.4 Properites of Device Files
5.2.5 Writing write
5.2.6 Device Files and Inodes
5.3 DEVICE ARE NOT LIKE FILES
5.3.1 Connection Attributes and Control
5.4 ATTRIBUTES OF DISK CONNECTIONS
5.4.1 Attribute 1: Buffering
5.4.2 Attribute 2: Auto-Append Mode
5.4.3 Controlling File Descriptors with open
5.4.4 Summary of Disk Connections
5.5 ATTRIBUTES OF TERMINAL CONNECTIONS
5.5.1 Terminal I/O Is Not as Simple as It Appers
5.5.2 The Terminal Driver
5.5.3 The stty Command
5.5.4 Programming the Terminal Driver: The Setting
5.5.5 Programming the Terminal Driver: The Functions
5.5.6 Programming the Terminal Driver: The Bits
5.5.7 Programming the Terminal Driver: Sample Programs
5.5.8 Summary of Terminal Connections
5.6 PROGRAMMING OTHER DEVICES: ioctl
5.7 UP IN THE SKY! IT'S A FILE, IT'S A DEVICE, IT'S A STREAM
SUMMARY
EXPLORATIONS
PROGRAMMING EXERCISES
PROJECTS
CHAPTER 6 Programming for Humans: Terminal Control and Signals
6.1 SOFTWARE TOOLS VS. DEVICE-SPECIFIC PROGRAMS
6.2 MODES OF THE TERMINAL DRIVER
6.2.1 Canonical Mode: Buffering and Editing
6.2.2 Noncanonical Processing
6.2.3 Summary of Terminal Modes
6.3 WRITING A USER PROGRAM: play_again.c
6.3.1 Nonblocking Input: play_again3.c
6.4 SIGNALS
6.4.1 What Does Ctrl-C Do?
6.4.2 What Is a Signal?
6.4.3 What Can a Process Do about a Signal?
6.4.4 Examples of Signal Handling
6.5 PREPARED FOR SIGNALS: play_again4.c
6.6 PROCESS ARE MORTAL
6.7 PROGRAMMING FOR DEVICES
SUMMARY
EXPLORATIONS
PROGRAMMING EXERCISES
CHAPTER 7 Event-Driven Programming: Writing a Video Game
7.1 VIDEO GAMES AND OPERATING SYSTEMS
7.2 THE PROJECT: WRITE SINGLE-PLAYER pong
7.3 SPACE PROGRAMMING: THE curses LIBRARY
7.3.1 Introduction to curses
7.3.2 Curses Internals: Virtual and Real Screens
7.4 TIME PROGRAMMING: sleep
7.5 PROGRAMMING WITH TIME I: ALARMS
7.5.1 Adding a Delay: sleep
7.5.2 How sleep() Works: Using Alarms in Unix
7.5.3 Scheduling a Future Action
7.6 PROGRAMMING WITH TIME II: INTERVAL TIMERS
7.6.1 Adding a Finer Delay: usleep
7.6.2 Three Kinds of Timers: Real, Process, Profile
7.6.3 Two Kinds of Intervals: Initial and Repeating
7.6.4 Programming with the Interval Timers
7.6.5 How Many Clocks Does the Computer Have
7.6.6 Summary of Timers
7.7 SIGNAL HANDLING I: USING signal
7.7.1 Old-Style Signal Handling
7.7.2 Handling Multiple Signals
7.7.3 Testing Multiple Signals
7.7.4 More Signal Weaknesses
7.8 SIGNAL HANDLING II: sigaction
7.8.1 Handling Signal: sigaction
7.8.2 Summary of Siganals
7.9 PROTECTING DATA FROM CORRUPTION
7.9.1 Examples of Data Corruption
7.9.2 Critical Sections
7.9.3 Blocking Signals: sigprocmask and sigsetops
7.9.4 Reentrant Code: Dangers of Recursion
7.9.5 Critical Sections in Video Games
7.10 kill: SENDING SIGNALS FROM A PROCESS
7.11 USING TIMERS AND SIGNALS: VIDEO GAMES
7.11.1 bounce1d.c: Controlled Animation on a Line
7.11.2 bounce2d.c: Animation in Two Dimensions
7.11.3 Now for the Complete Game
7.12 SIGNAL ON INPUT: ASYCHRONOUS I/O
7.12.1 Bouncing with Asynchronous I/O
7.12.2 Method 1: Using O_ASYNC
7.12.3 Method 2: Using aio_read
7.12.4 Do We Need Asynchronous Reads for Bounce?
7.12.5 Asychronous Input, Video Games, and Operating Systems
SUMMARY
EXPLORATIONS
PROGRAMMING EXERCISES
PROJECTS
CHAPTER 8 Processes and Programs: Studying sh
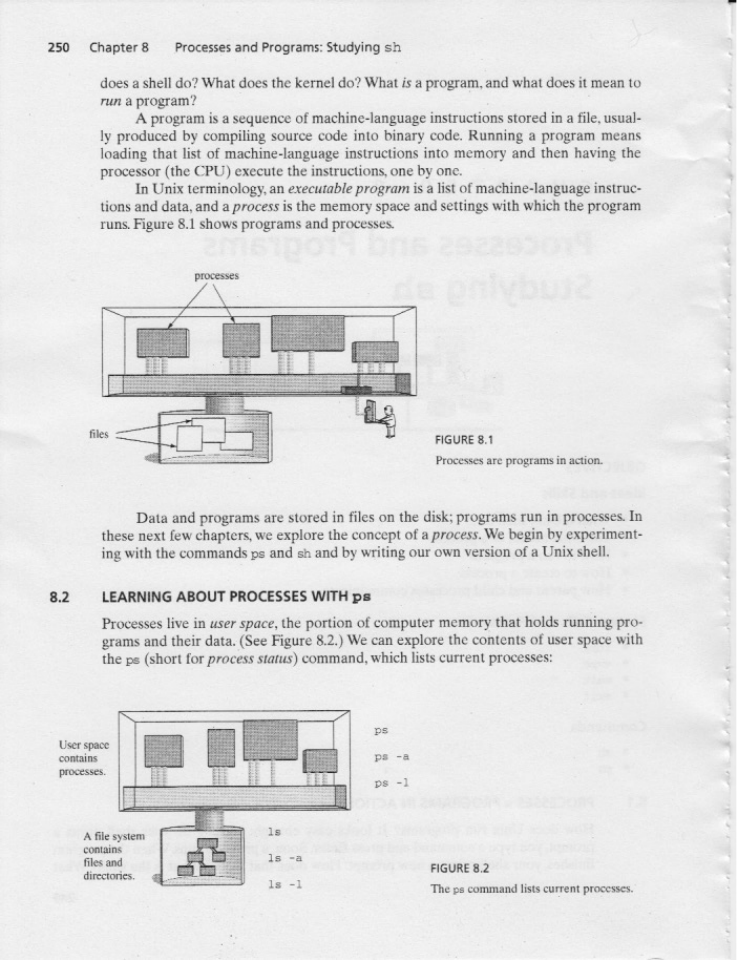
8.1 PROCESSES=PROGRAMS IN ACTION
8.2 LEARNING ABOUT PROCESSES WITH ps
8.2.1 System Processes
8.2.2 Process Management and File Management
8.2.3 Computer Memory and Computer Programs
8.3 THE SHELL: A TOOL PROCESS AND PROGRAM CONTROL
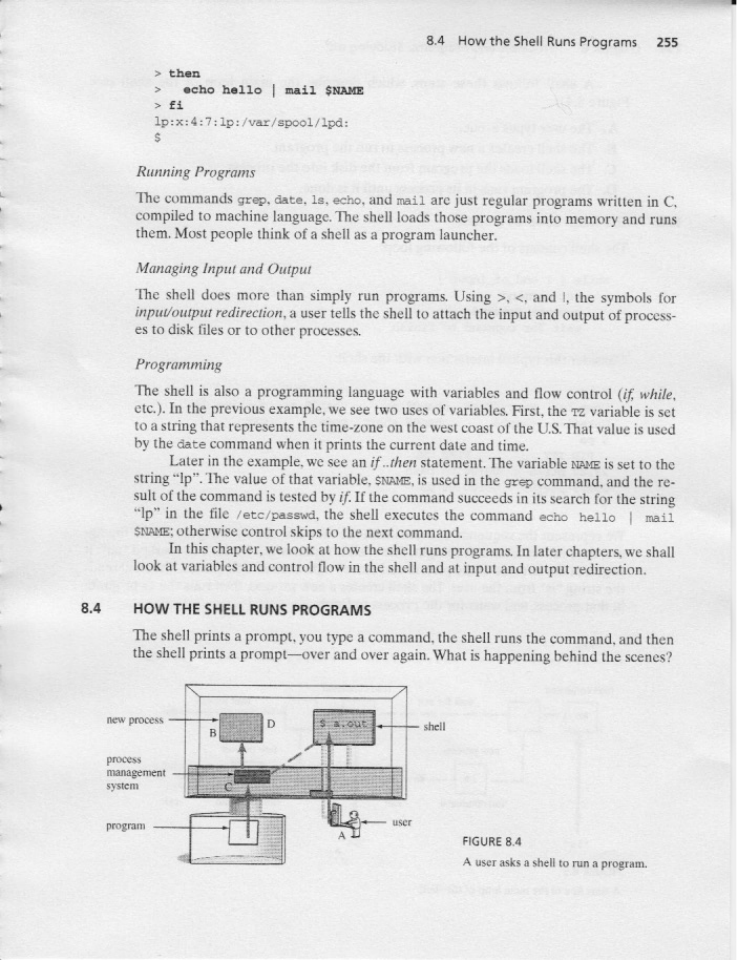
8.4 HOW THE SHELL RUNS PROGRAMS
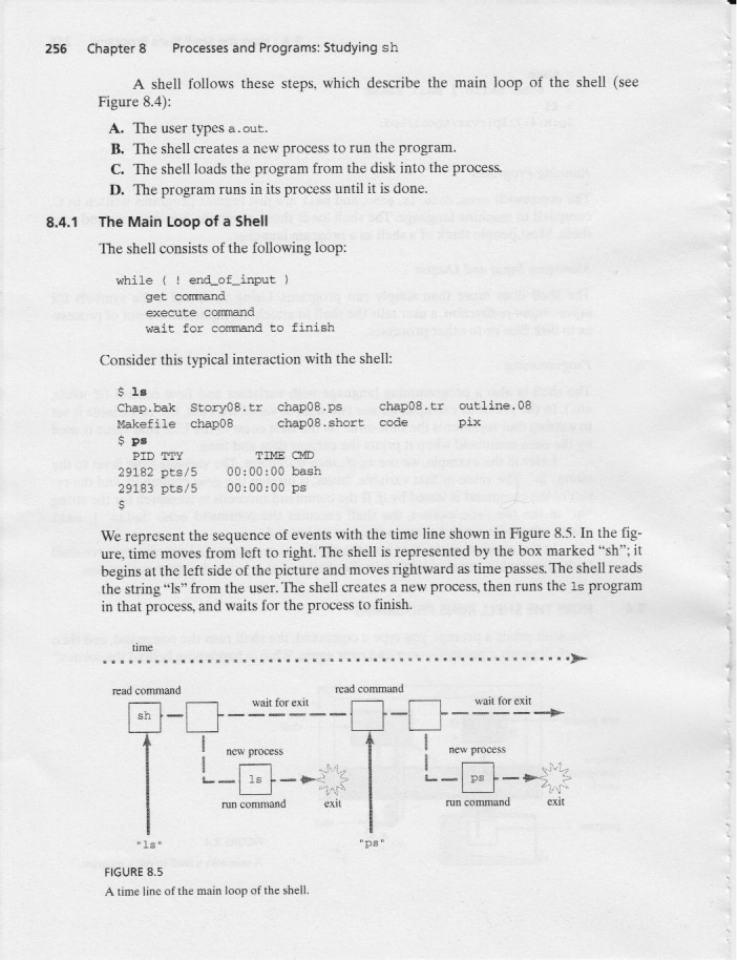
8.4.1 The Main Loop of a Shell
8.4.2 Question 1: How Does a Program Run a Program?
8.4.3 Question 2: How Do We Get a New Process?
8.4.4 Question 3: How Does the Parent Wait for the Child to exit?
8.4.5 Summary: How the Shell Runs Programs
8.5 WRITING A SHELL: psh2.c
8.5.1 Signals and psh2.c
8.6 REFLECTION: PROGRAMMING WITH PROCESSES
8.7 EXTRA ABOUT EXIT AND EXEC
8.7.1 Death of a Process: exit and _exit
8.7.2 The exec Family
SUMMARY
EXPLORATIONS
PROGRAMMING EXERCISES
CHAPTER 9 A Programmable Shell: Shell Variables and the Environment
9.1 SHELL PROGRAMMING
9.2 SHELL SCRIPTS: WHAT AND WHY?
9.2.1 A Shell Script Is a Batch of Commands
9.3 smsh1--COMMAND-LINE PARSING
9.3.1 Notes on smsh1
9.4 CONTROL FLOW IN THE SHELL: WHY AND HOW
9.4.1 What if Does
9.4.2 How if Works
9.4.3 Adding if to smsh
9.4.4 smsh2.c: The Revised Code
9.5 SHELL VARIABLES: LOCAL AND GLOBAL
9.5.1 Using Shell Variables
9.5.2 A Storage System for Variables
9.5.3 Adding Variable Commands: Built-ins
9.5.4 How'd We Do?
9.6 THE ENVIARONMENT: PERSONALIZED SETTINGS
9.6.1 Using the Environment
9.6.2 What is the Environment? How it Works
9.6.3 Adding Environment Handling to smsh
9.6.4 Code for varlib.c
9.7 STATE-OF-THE-SHELL REPORT
SUMMARY
EXPLORATIONS
PROGRAMMING EXERCISES
CHAPTER 10 I/O Redirection and Pipes
10.1 SHELL PROGRAMMING
10.2 A SHELL APPLICATION: WATCH FOR USERS
10.3 FACTS ABOUT STANDARD I/O AND REDIRECTION
10.3.1 Fact One: Three standard File Descriptors
10.3.2 Default Connections: the tty
10.3.3 Output Goes Only to stdout
10.3.4 The Shell, Not the Program, Redirects I/O
10.3.5 Understanding I/O Redirection
10.3.6 Fact Two: The "Lowest-Available-fd" Principle
10.3.7 The Synthesis
10.4 HOW TO ATTACH stdin TO A FILE
10.4.1 Method 1: Close Then Opne
10.4.2 Method 2: open..close..dup..close
10.4.3 System Call Summary: dup
10.4.4 Method 3: open..dup2..close
10.4.5 But the Shell Redirects stdin for Other Programs
10.5 REDIRECTING I/O FOR ANOTHER PROGRAM: who > userlist
10.5.1 Summary of Redirection to Files
10.6 PROGRAMMING PIPES
10.6.1 Creating a Pipe
10.6.2 Using fork to Share a Pipe
10.6.3 The Finale: Using pipe, fork and exec
10.6.4 Technical Details: Pipes Are Not Files
SUMMARY
EXPLORATIONS
PROGRAMMING EXERCISES
CHAPTER 11 Connecting to Processes Near and Far: Servers and Sockets
11.1 PRODUCTS AND SERVICES
11.2 INTRODUCTORY METHAPHOR: A BEVERAGE INTERFACE
11.3 bc: A UNIX CALCULATOR
11.3.1 Coding bc: pipe, fork, dup, exec
11.3.2 Remarks on Coroutines
11.3.3 fdopen: Making File Descriptors Look like Files
11.4 popen: MAKING PROCESS LOOK LIKE FILES
11.4.1 What popen Does
11.4.2 Writing popen: Using fdopen
11.4.3 Access to Data: Files, APIs, and Servers
11.5 SOCKETS: CONNECTING TO REMOTE PROCESSES
11.5.1 An Analogy: "At the Tone, the Time Will Be..."
11.5.2 Internet Time, DAP, and Weather Servers
11.5.3 Lists of Services: Well-Known Ports
11.5.4 Writing timeserv.c: A Time Server
11.5.5 Testing timeserv.c
11.5.6 Writing timeclnt.c: A Time Client
11.5.7 Testing timeclnt.c
11.5.8 Another Server: remote ls
11.6 SOFTWARE DAEMONS
SUMMARY
EXPLORATIONS
PROGRAMMING EXERCISES
CHAPTER 12 Connections and Protocols: Writing a Web Server
12.1 SPOTLIGHT ON SERVERS
12.2 THREE MAIN OPERATIONS
12.3 OPERTAIONS 1 AND 2: MAKING A CONNECTION
12.3.1 Operation 1: Setting Up a Server Socket
12.3.2 Operation 2: Connecting to Server
12.3.3 socklib.c
12.4 OPERATION3 : CLIENT/SERVER CONVERSATION
12.4.1 timeserv/timeclnt using socklib.c
12.4.2 A Second Version of the Server: Using fork
12.4.3 Server Design Question: DIY or Delegate
12.5 WRITING A WEB SERVER
12.5.1 What a Web Server Does
12.5.2 Planning Our Web Server
12.5.3 The Protocol of a Web Server
12.5.4 Writing a Web Server
12.5.5 Running the Web Server
12.5.6 Webserv Source Code
12.5.7 Comparing Web Servers
SUMMARY
EXPLORATIONS
PROGRAMMING EXERCISES
PROJECTS
CHAPTER 13 Programming with Datagrams: A License Server
13.1 SOFTWARE CONTROL
13.2 A BRIEF HISTORY OF LICENSE CONTROL
13.3 A NONCOMPUTER EXAMPLE: MANAGING COMPANY CARS
13.3.1 Description of Car Key Management
13.3.2 Managing Cars in Client/Server Terms
13.4 LICENSE MANAGEMENT
13.4.1 The License Server System: What Does It Do?
13.4.2 The License Server System: How Does it Work
13.4.3 A Communication System
13.5 DATAGRAM SOCKETS
13.5.1 Streams vs. Datagrams
13.5.2 Programming with Datagrams
13.5.3 Summary of sendto and recvfrom
13.5.4 Replying to Datagrams
13.5.5 Summary of Datagrams
13.6 LICENSE SERVER VERSION 1.0
13.6.1 Client Version 1
13.6.2 Server Version 1
13.6.3 Testing Version 1
13.6.4 How'd We Do?
13.7 REAL-WORLD PROGRAMMING
13.7.1 Handling Client Crashed
13.7.2 Handling Server Crashes
13.7.3 Testing Version 2
13.8 DISTRIBUTED LICENSE SERVERS
13.9 UNIX DOMAIN SOCKETS
13.9.1 Filenames as Socket Addresses
13.9.2 Programming with Unix Domain Sockets
13.10 SUMMARY: SOCKETS AND SERVERS
SUMMARY
EXPLORATIONS
PROGRAMMING EXERCISES
PROJECTS
CHAPTER 14 Threads Concurrent Functions
14.1 DOING SEVERAL THINGS AT ONCE
14.2 THREADS OF EXECUTION
14.2.1 A Single-Threaded Program
14.2.2 A Multithreaded Program
14.2.3 Function Summaries
14.3 INTERTHREAD COOPERATION
14.3.1 Example 1: incrprint.c
14.3.2 Example 2: twordcount.c
14.3.3 Interthread Cooperation: Summary
14.4 COMPARING THREADS WITH PROCESSES
14.5 INTERTHREAD NOTIFICATION
14.5.1 Notifying Election Central
14.5.2 Programming with Condition Variables
14.5.3 Functions for Condition Variables
14.5.4 Back to the Web
14.6 A THREADED WEB SERVER
14.6.1 Changes to Our Web Server
14.6.2 Threads Allow a New Feature
14.6.3 Preventing Zombie Threads: Detached Threads
14.6.4 The Code
14.7 THREADS AND ANIMATION
14.7.1 Advantages of Threads
14.7.2 Threaded bounce1d.c
14.7.3 Multiple Animations: tanimate.c
14.7.4 Mutexes and tanimate.c
14.7.5 A Thread for Curses
SUMMARY
EXPLORATIONS
PROGRAMMING EXERCISES
CHATPER 15 IPC Roundup: Can We Talk?
15.1 PROGRAMMING CHOICES
15.2 THE talk COMMAND: READING FROM MULTIPLE INPUTS
15.2.1 Reading from Two File Descriptors at Once
15.2.2 The select System Call
15.2.3 select and talk
15.2.4 select vs. poll
15.3 COMMUNICATION CHOICES
15.3.1 One Problem, Three Solutions
15.3.2 IPC with Files
15.3.3 Named Pipes
15.3.4 Shared Memory
15.3.5 Comparing Communication Methods
15.4 INTERPROCESS COOPERATION AND COORDINATION
15.4.1 File Locks
15.4.2 Semaphores
15.4.3 Sockets and FIFOs vs. Shared Storage
15.5 A PRINT SPOOLER
15.5.1 Many Writers, One Reader
15.5.2 A Client/Server Model
15.6 IPC OVERVIEW
15.7 CONNECTIONS AND GAMES
SUMMARY
EXPLORATIONS
PROGRAMMING EXERCISES
Index













 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc