Web Vulnerability Scanner v9
User Manual
Information in this document is subject to change without notice. Companies, names, and data used
in examples herein are fictitious unless otherwise noted. No part of this document may be
reproduced or transmitted in any form or by any means, electronic or mechanical, for any purpose,
without the express written permission of Acunetix Ltd.
Acunetix Web Vulnerability Scanner is copyright of Acunetix Ltd. 2004–2013.
Acunetix Ltd. All rights reserved.
http://www.acunetix.com
info@acunetix.com
Document version 9
Last updated: 13th August 2013
1
�
Contents
1. INTRODUCTION TO ACUNETIX WEB VULNERABILITY SCANNER ................................... 4
Why You Need To Secure Your Web Applications ................................................................................... 4
Acunetix Web Vulnerability Scanner ................................................................................................................ 5
Acunetix AcuSensor Technology ....................................................................................................................... 6
2. ACUNETIX WEB VULNERABILITY SCANNER PROGRAM OVERVIEW ............................. 9
Web Scanner ................................................................................................................................................................ 9
AcuSensor Technology Agent ............................................................................................................................. 9
AcuMonitor Service ................................................................................................................................................ 10
Port Scanner .............................................................................................................................................................. 10
Target Finder ............................................................................................................................................................. 11
Subdomain Scanner .............................................................................................................................................. 12
Blind SQL Injector ................................................................................................................................................... 13
HTTP Editor ................................................................................................................................................................ 14
HTTP Sniffer .............................................................................................................................................................. 15
HTTP Fuzzer ............................................................................................................................................................. 16
Authentication Tester............................................................................................................................................. 16
Web Services Scanner and Web Services Editor ................................................................................... 17
Acunetix Web Vulnerability Scanner SDK .................................................................................................. 17
Reporter ....................................................................................................................................................................... 18
New in Acunetix Web Vulnerability Scanner Version 9 ........................................................................ 18
Acunetix Blog and Support Page .................................................................................................................... 19
Licensing Acunetix Web Vulnerability Scanner ........................................................................................ 19
3. INSTALLING ACUNETIX WEB VULNERABILITY SCANNER ................................................ 21
Minimum System Requirements ...................................................................................................................... 21
Installing Acunetix Web Vulnerability Scanner ......................................................................................... 21
Registering with AcuMonitor Service ............................................................................................................. 21
Installing the AcuSensor Agent ........................................................................................................................ 22
Disabling and uninstalling AcuSensor .......................................................................................................... 25
Configuring an HTTP Proxy or SOCKS proxy Server ........................................................................... 26
Upgrading from a previous version of Acunetix Web Vulnerability Scanner ............................. 27
4. SCANNING A WEBSITE ....................................................................................................................... 29
Step 1: Select Target(s) to Scan ..................................................................................................................... 29
Step 2: Specify Scanning Profile, Scan Settings Template and Crawling Options ................ 30
Step 3: Confirm Targets and Technologies Detected ........................................................................... 31
Step 4: Configure Login for Password Protected Areas ...................................................................... 31
Step 5: Scanning a Form Based Password Protected Area .............................................................. 34
Step 6: Finalize Scan Options........................................................................................................................... 38
Step 7: Completing the scan ............................................................................................................................. 39
5. ANALYZING THE SCAN RESULTS.................................................................................................. 40
Introduction ................................................................................................................................................................. 40
Web Alerts................................................................................................................................................................... 40
Network Alerts ........................................................................................................................................................... 41
Port Scanner .............................................................................................................................................................. 41
Knowledge Base ...................................................................................................................................................... 41
Site Structure ............................................................................................................................................................. 42
Grouping of Vulnerabilities.................................................................................................................................. 44
Saving a Scan Result ............................................................................................................................................ 44
2
�
6. GENERATING A REPORT FROM THE RESULTS ...................................................................... 45
Introduction to the Reporter ............................................................................................................................... 45
Generating a Report from the Scan Results .............................................................................................. 45
Types of Reports ..................................................................................................................................................... 47
Reporter Settings ..................................................................................................................................................... 50
Saving Reports ......................................................................................................................................................... 51
Changing the Reporter Database ................................................................................................................... 51
7. SITE CRAWLER ....................................................................................................................................... 53
Introduction ................................................................................................................................................................. 53
Starting a Website Crawl ..................................................................................................................................... 53
Crawling Options ..................................................................................................................................................... 54
Acunetix DeepScan ................................................................................................................................................ 56
File Extension Filters ............................................................................................................................................. 57
Directory and File Filters ...................................................................................................................................... 58
URL Rewrite rules ................................................................................................................................................... 58
Custom Cookies ....................................................................................................................................................... 60
Configuring Input Fields to Traverse Web Form Pages....................................................................... 61
8. MANUAL CRAWLING USING THE HTTP SNIFFER .................................................................. 63
Introduction ................................................................................................................................................................. 63
Configuring Your Browser ................................................................................................................................... 63
Capturing HTTP traffic .......................................................................................................................................... 64
HTTP Sniffer Trap Filters .................................................................................................................................... 65
Editing a HTTP Request without a Trap ...................................................................................................... 66
9. COMPARE RESULTS TOOL ............................................................................................................... 67
Introduction ................................................................................................................................................................. 67
Comparing Results ................................................................................................................................................. 67
Analyzing the Results Comparison ................................................................................................................ 67
10. SCANNING WEB SERVICES ............................................................................................................ 69
Introduction ................................................................................................................................................................. 69
Starting a Web Service Scan ............................................................................................................................ 69
Web Services Editor .............................................................................................................................................. 70
HTTP Editor Export ................................................................................................................................................ 71
11. THE SCHEDULER ................................................................................................................................. 72
Introduction ................................................................................................................................................................. 72
Configuring the Scheduler service .................................................................................................................. 72
Creating a Scheduled scan ................................................................................................................................ 74
Importing Scheduling Scans .............................................................................................................................. 76
12. APPLICATION SETTINGS ................................................................................................................. 77
13. SCAN SETTINGS TEMPLATES ....................................................................................................... 80
14. SCANNING PROFILES ....................................................................................................................... 86
Creating custom vulnerability checks ............................................................................................................ 87
15. MORE INFORMATION......................................................................................................................... 88
User Manual ............................................................................................................................................................... 88
Frequently Asked Questions ............................................................................................................................. 88
Acunetix Blog ............................................................................................................................................................. 88
Request Support ...................................................................................................................................................... 88
Knowledge base / Support page ..................................................................................................................... 88
Acunetix Facebook page ..................................................................................................................................... 88
3
�
1. Introduction to Acunetix Web Vulnerability Scanner
Why You Need To Secure Your Web Applications
Website security is today's most overlooked aspect of securing the enterprise and should be a
priority in any organization.
Increasingly, hackers are concentrating their efforts on web-based applications – shopping carts,
forms, login pages, dynamic content, etc. Accessible 24/7 from anywhere in the world, insecure web
applications provide easy access to backend corporate databases and also allow hackers to perform
illegal activities using the attacked sites. A victim’s website can be used to launch criminal activities
such as hosting phishing sites or to transfer illicit content, while abusing the website’s bandwidth
and making its owner liable for these unlawful acts.
Hackers already have a wide repertoire of attacks that they regularly launch against organizations
including SQL Injection, Cross Site Scripting, Directory Traversal Attacks, Parameter Manipulation
(e.g., URL, Cookie, HTTP headers, web forms), Authentication Attacks, Directory Enumeration and
other exploits. Moreover, the hacker community is very close-knit; newly discovered web application
intrusions, known as Zero Day exploits, are posted on a number of forums and websites known only
to members of that exclusive group. Postings are updated daily and are used to propagate and
facilitate further hacking.
Web applications – shopping carts, forms, login pages, dynamic content, and other bespoke
applications – are designed to allow your website visitors to retrieve and submit dynamic content
including varying levels of personal and sensitive data.
If these web applications are not secure, then your entire database of sensitive information is at
serious risk. A Gartner Group study reveals that 75% of cyber-attacks are done at the web
application level.
Why are web applications vulnerable?
Websites and web applications are easily available via the internet 24 hours a day, 7
days a week to customers, employees, suppliers and therefore also hackers.
Firewalls and SSL provide no protection against web application hacking, simply
because access to the website has to be made public.
Web applications often have direct access to backend data such as customer
databases.
Most web applications are custom-made and, therefore, involve a lesser degree of
testing than off-the-shelf software. Consequently, custom applications are more
susceptible to attack.
Various high-profile hacking attacks have proven that web application security
remains the most critical. If your web applications are compromised, hackers will
have complete access to your backend data even though your firewall is configured
correctly and your operating system and applications are patched repeatedly.
Network security defense provides no protection against web application attacks since these are
launched on port 80 which has to remain open to allow regular operation of the business. It is
therefore imperative that you regularly and consistently audit your web applications for exploitable
vulnerabilities.
4
�
The need for automated web application security scanning
Manual vulnerability auditing of all your web applications is complex and time-consuming, since it
generally involves processing a large volume of data. It also demands a high-level of expertise and
the ability to keep track of considerable volumes of code used in a web application. In addition,
hackers are constantly finding new ways to exploit your web application, which would mean that
you have to constantly monitor the security communities, and find new vulnerabilities in your web
application code before hackers discover them.
Automated vulnerability scanning allows you to focus on the already challenging task of building a
web application. An automated web application scanner is always on the lookout for new attack
paths that hackers can use to access your web application or the data behind it.
Within minutes, an automated web application scanner can scan your web application, identify all
the files accessible from the internet and simulate hacker activity in order to identify vulnerable
components.
In addition, an automated vulnerability scanner can also be used to assess the code which makes up
a web application, allowing it to identify potential vulnerabilities which might not be obvious from
the internet, but still exist in the web application, and can thus still be exploited.
Acunetix Web Vulnerability Scanner
Acunetix Web Vulnerability Scanner is an automated web application security testing tool that audits
your web applications by checking for vulnerabilities like SQL Injections, Cross site scripting and
other exploitable vulnerabilities. In general, Acunetix Web Vulnerability Scanner scans any website
or web application that is accessible via a web browser and uses the HTTP/HTTPS protocol.
Acunetix Web Vulnerability Scanner offers a strong and unique solution for analyzing off-the-shelf
and custom web applications including those utilizing JavaScript, AJAX and Web 2.0 web
applications. Acunetix has an advanced crawler that can find almost any file. This is important since
what is not found cannot be checked.
How Acunetix Web Vulnerability Scanner Works
Acunetix Web Vulnerability Scanner works in the following manner:
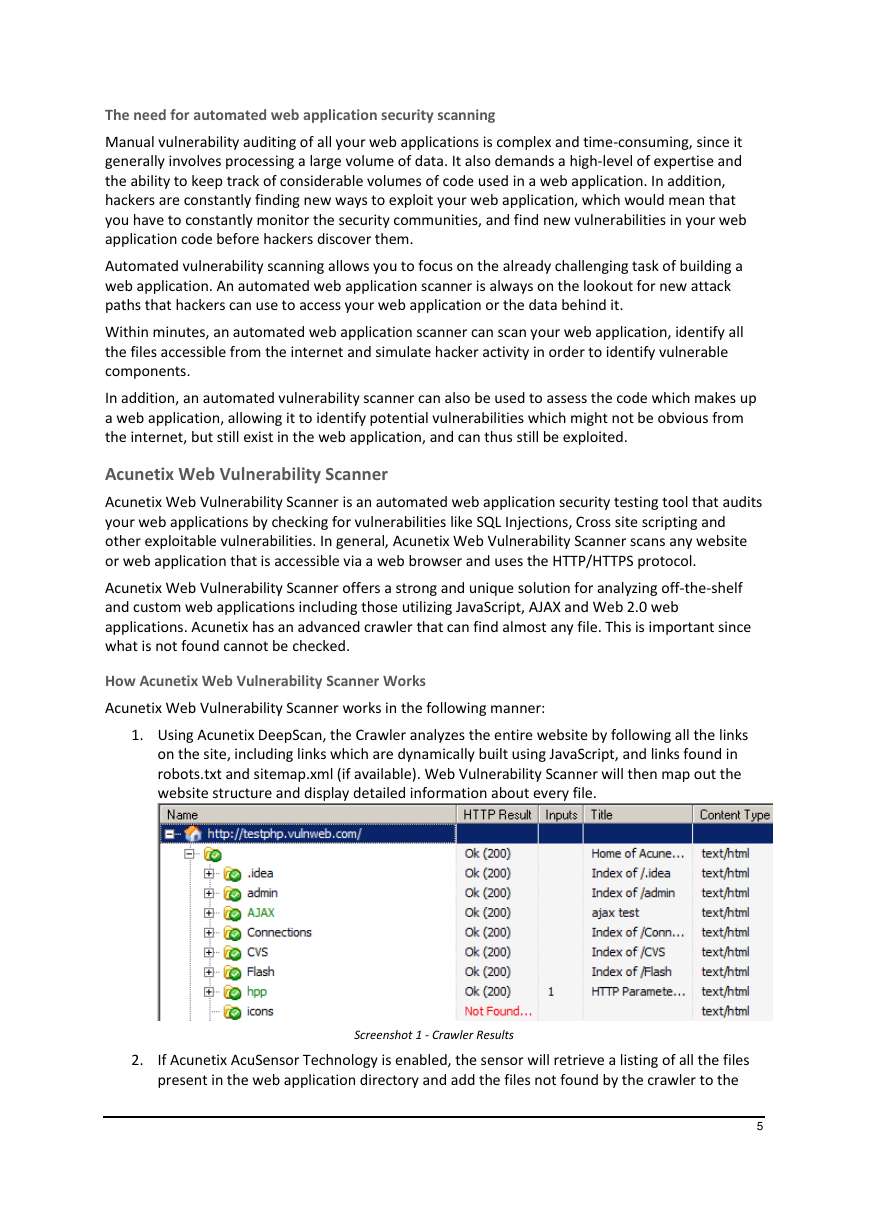
1. Using Acunetix DeepScan, the Crawler analyzes the entire website by following all the links
on the site, including links which are dynamically built using JavaScript, and links found in
robots.txt and sitemap.xml (if available). Web Vulnerability Scanner will then map out the
website structure and display detailed information about every file.
2.
If Acunetix AcuSensor Technology is enabled, the sensor will retrieve a listing of all the files
present in the web application directory and add the files not found by the crawler to the
Screenshot 1 - Crawler Results
5
�
crawler output. Such files usually are not discovered by the crawler as they are not
accessible from the web server, or not linked through the website. Acunetix AcuSensor also
analyses files which are not accessible from the internet, such as web.config.
3. After the crawling process, Web Vulnerability Scanner automatically launches a series of
vulnerability checks on each page found, in essence emulating a hacker. Also, Acunetix Web
Vulnerability Scanner analyses each page for places where it can input data, and
subsequently attempts all the different input combinations. This is the Automated Scan
Stage. If the AcuSensor Technology is enabled, a series of additional vulnerability checks are
launched against the website. More information about AcuSensor is provided in the
following section.
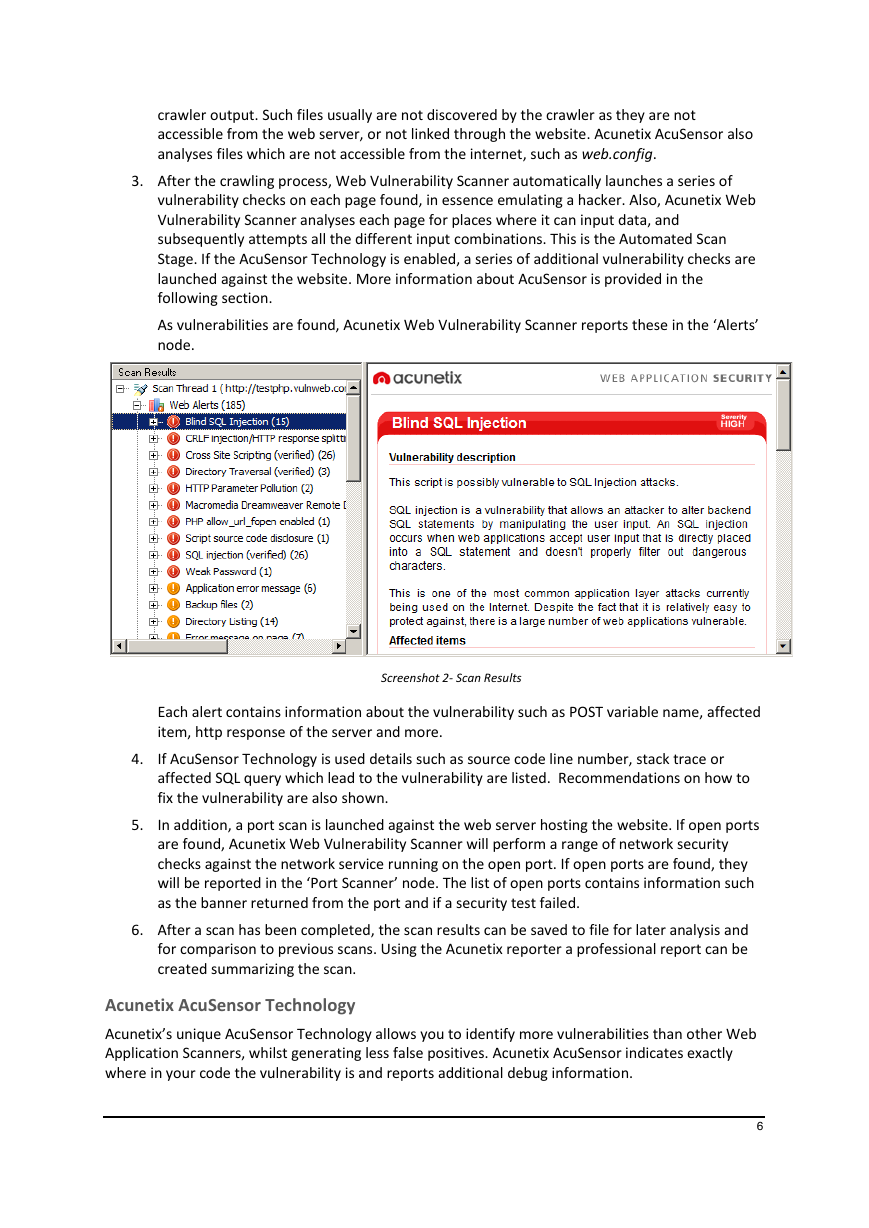
As vulnerabilities are found, Acunetix Web Vulnerability Scanner reports these in the ‘Alerts’
node.
Screenshot 2- Scan Results
Each alert contains information about the vulnerability such as POST variable name, affected
item, http response of the server and more.
4.
5.
If AcuSensor Technology is used details such as source code line number, stack trace or
affected SQL query which lead to the vulnerability are listed. Recommendations on how to
fix the vulnerability are also shown.
In addition, a port scan is launched against the web server hosting the website. If open ports
are found, Acunetix Web Vulnerability Scanner will perform a range of network security
checks against the network service running on the open port. If open ports are found, they
will be reported in the ‘Port Scanner’ node. The list of open ports contains information such
as the banner returned from the port and if a security test failed.
6. After a scan has been completed, the scan results can be saved to file for later analysis and
for comparison to previous scans. Using the Acunetix reporter a professional report can be
created summarizing the scan.
Acunetix AcuSensor Technology
Acunetix’s unique AcuSensor Technology allows you to identify more vulnerabilities than other Web
Application Scanners, whilst generating less false positives. Acunetix AcuSensor indicates exactly
where in your code the vulnerability is and reports additional debug information.
6
�
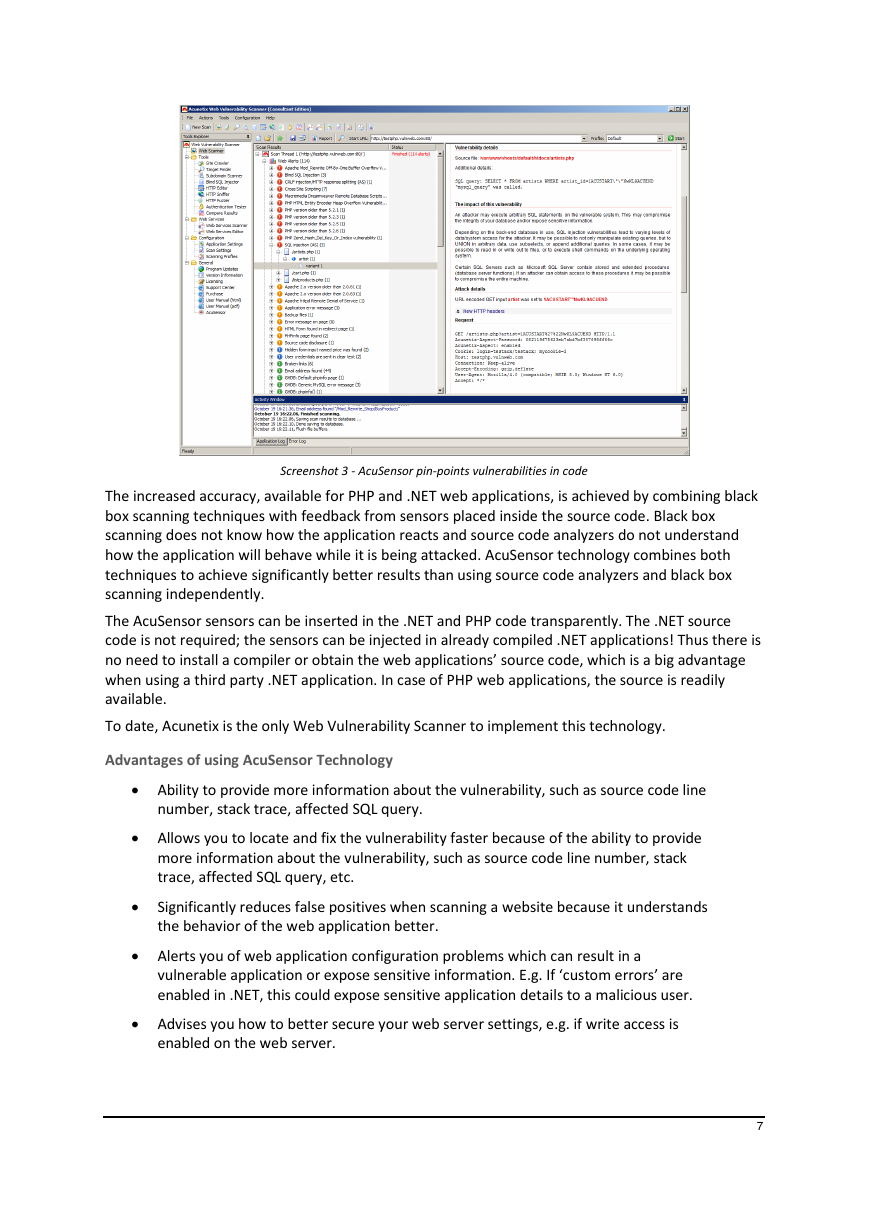
Screenshot 3 - AcuSensor pin-points vulnerabilities in code
The increased accuracy, available for PHP and .NET web applications, is achieved by combining black
box scanning techniques with feedback from sensors placed inside the source code. Black box
scanning does not know how the application reacts and source code analyzers do not understand
how the application will behave while it is being attacked. AcuSensor technology combines both
techniques to achieve significantly better results than using source code analyzers and black box
scanning independently.
The AcuSensor sensors can be inserted in the .NET and PHP code transparently. The .NET source
code is not required; the sensors can be injected in already compiled .NET applications! Thus there is
no need to install a compiler or obtain the web applications’ source code, which is a big advantage
when using a third party .NET application. In case of PHP web applications, the source is readily
available.
To date, Acunetix is the only Web Vulnerability Scanner to implement this technology.
Advantages of using AcuSensor Technology
Ability to provide more information about the vulnerability, such as source code line
number, stack trace, affected SQL query.
Allows you to locate and fix the vulnerability faster because of the ability to provide
more information about the vulnerability, such as source code line number, stack
trace, affected SQL query, etc.
Significantly reduces false positives when scanning a website because it understands
the behavior of the web application better.
Alerts you of web application configuration problems which can result in a
vulnerable application or expose sensitive information. E.g. If ‘custom errors’ are
enabled in .NET, this could expose sensitive application details to a malicious user.
Advises you how to better secure your web server settings, e.g. if write access is
enabled on the web server.
7
�
Detects more SQL injection vulnerabilities. Previously SQL injection vulnerabilities
could only be found if database errors were reported, whereas now the source code
can be analyzed for improve detection
Ability to detect SQL Injection vulnerabilities in all SQL statements, including in SQL
INSERT statements. Using a black box scanner such SQL injection vulnerabilities
cannot be found. This significantly increases the ability for Acunetix Web
Vulnerability Scanner to find vulnerabilities.
Discovers all the files present and accessible through the web server. If an attacker
gains access to the website and creates a backdoor file in the application directory,
the file is found and scanned when using the AcuSensor Technology and you will be
alerted.
AcuSensor Technology is able to intercept all web application inputs and build a
comprehensive list with all possible inputs in the website and test them.
No need to write URL rewrite rules when scanning web applications which use
search engine friendly URL’s! Using the AcuSensor Technology the scanner is able to
rewrite SEO URL’s on the fly.
Ability to test for arbitrary file creation and deletion vulnerabilities. E.g. Through a
vulnerable script a malicious user can create a file in the web application directory
and execute it to have privileged access, or delete sensitive web application files.
Ability to test for email injection. E.g. A malicious user may append additional
information such as a list or recipients or additional information to the message
body to a vulnerable web form, to spam a large number of recipients anonymously.
8
�













 2023年江西萍乡中考道德与法治真题及答案.doc
2023年江西萍乡中考道德与法治真题及答案.doc 2012年重庆南川中考生物真题及答案.doc
2012年重庆南川中考生物真题及答案.doc 2013年江西师范大学地理学综合及文艺理论基础考研真题.doc
2013年江西师范大学地理学综合及文艺理论基础考研真题.doc 2020年四川甘孜小升初语文真题及答案I卷.doc
2020年四川甘孜小升初语文真题及答案I卷.doc 2020年注册岩土工程师专业基础考试真题及答案.doc
2020年注册岩土工程师专业基础考试真题及答案.doc 2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc
2023-2024学年福建省厦门市九年级上学期数学月考试题及答案.doc 2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc
2021-2022学年辽宁省沈阳市大东区九年级上学期语文期末试题及答案.doc 2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc
2022-2023学年北京东城区初三第一学期物理期末试卷及答案.doc 2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc
2018上半年江西教师资格初中地理学科知识与教学能力真题及答案.doc 2012年河北国家公务员申论考试真题及答案-省级.doc
2012年河北国家公务员申论考试真题及答案-省级.doc 2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc
2020-2021学年江苏省扬州市江都区邵樊片九年级上学期数学第一次质量检测试题及答案.doc 2022下半年黑龙江教师资格证中学综合素质真题及答案.doc
2022下半年黑龙江教师资格证中学综合素质真题及答案.doc