Cryptography
Part 1, Basics
�
Introduction
• Cryptography is the art of designing mathematical
methods for protecting information
• A means of transmitting confidential information
securely over open networks: encryption
• Classical cryptographical algorithms have been
known for hundreds of years
• Innovations in the last two decades have created
a whole new branch of cryptography: asymmetric
(public key) cryptography
– Digital signatures
– Secure on-line key exchange
2
�
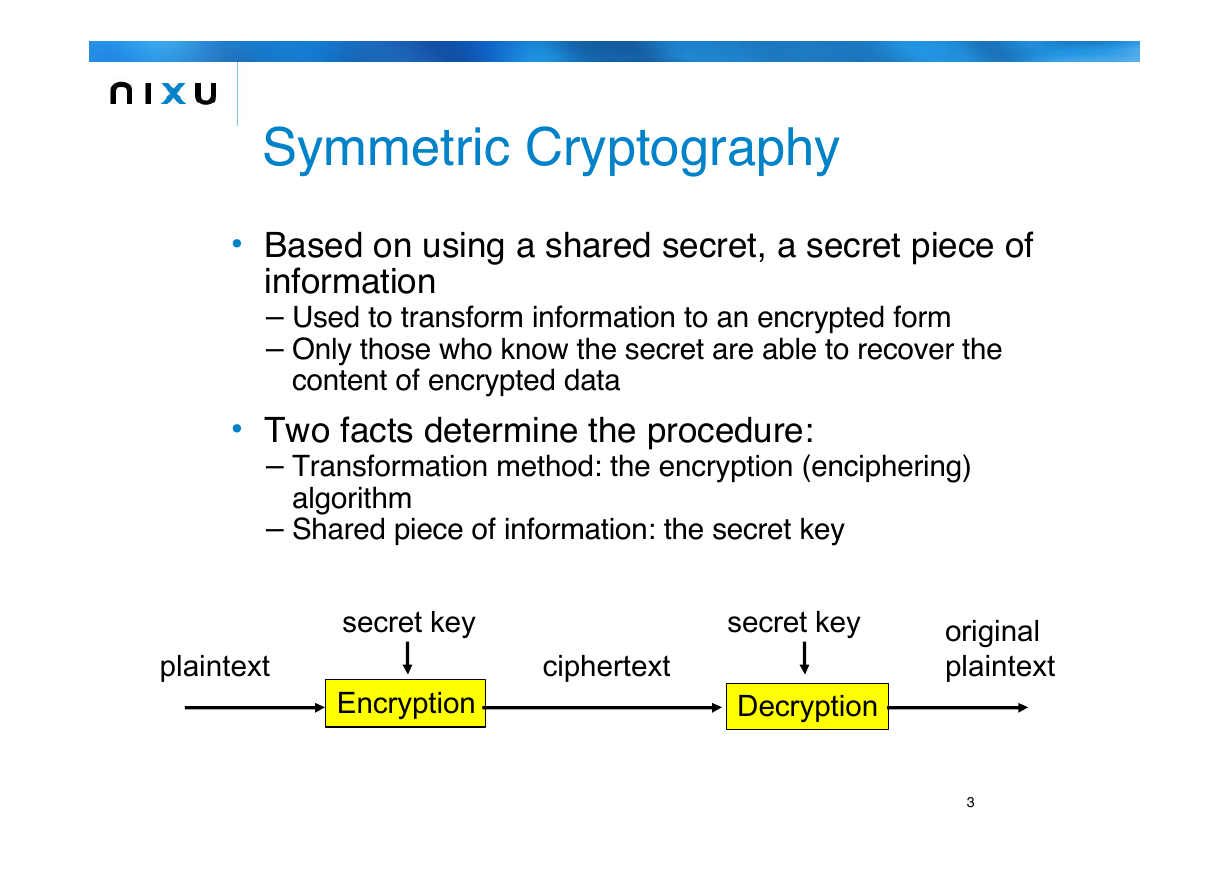
Symmetric Cryptography
• Based on using a shared secret, a secret piece of
information
– Used to transform information to an encrypted form
– Only those who know the secret are able to recover the
content of encrypted data
• Two facts determine the procedure:
– Transformation method: the encryption (enciphering)
algorithm
– Shared piece of information: the secret key
plaintext
secret key
Encryption
ciphertext
secret key
Decryption
original
plaintext
3
�
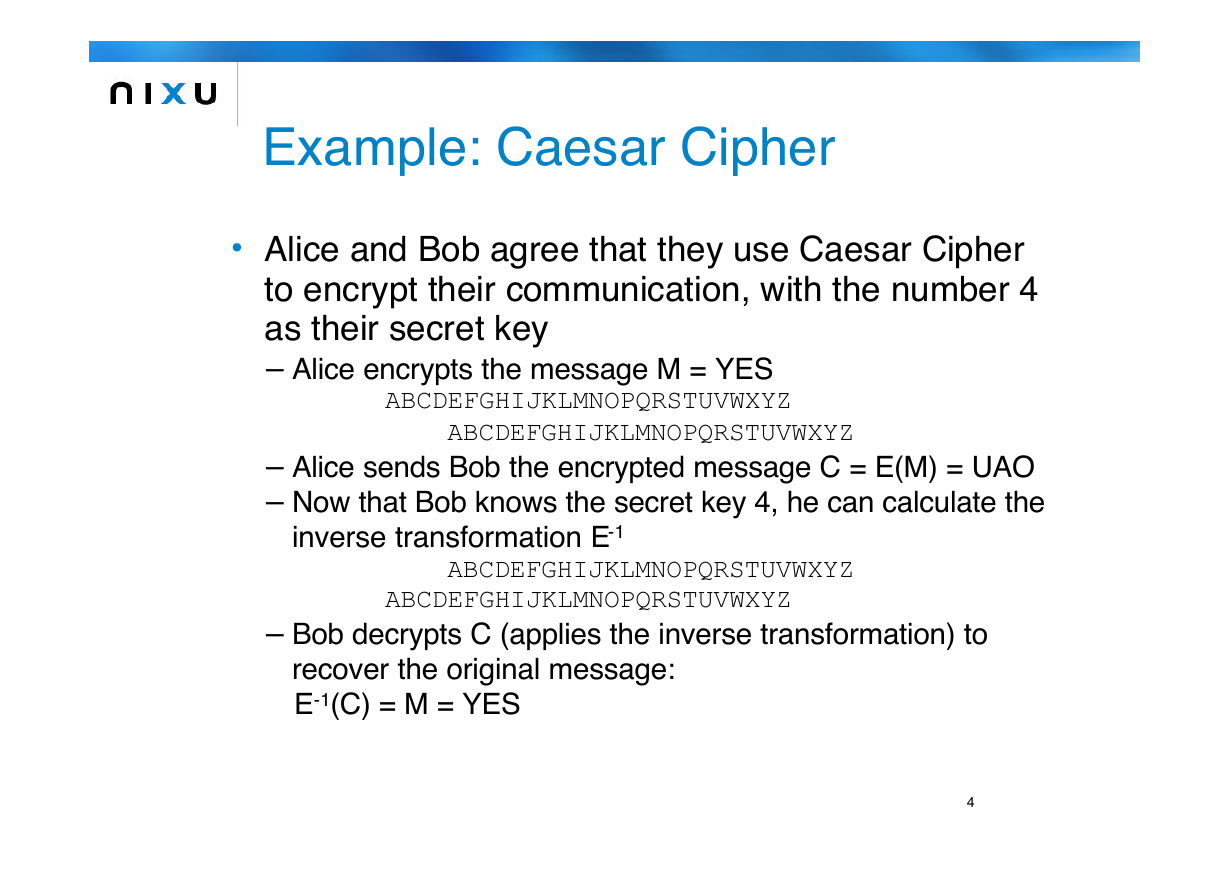
Example: Caesar Cipher
• Alice and Bob agree that they use Caesar Cipher
to encrypt their communication, with the number 4
as their secret key
– Alice encrypts the message M = YES
ABCDEFGHIJKLMNOPQRSTUVWXYZ
ABCDEFGHIJKLMNOPQRSTUVWXYZ
– Alice sends Bob the encrypted message C = E(M) = UAO
– Now that Bob knows the secret key 4, he can calculate the
inverse transformation E-1
ABCDEFGHIJKLMNOPQRSTUVWXYZ
ABCDEFGHIJKLMNOPQRSTUVWXYZ
– Bob decrypts C (applies the inverse transformation) to
recover the original message:
E-1(C) = M = YES
4
�
Example: Analysis of Caesar
Cipher
Is it possible for an attacker to find out the content of the
encrypted message?
•
• Kerkhoff’s Principle: we assume that the attacker knows the
encryption algorithm used
– The set of good encryption algorithms is small, the potential
attacker can try all of them relatively easily
• Assume that an attacker, Eve, gets to know C=UAP
– Since Eve knows that the algorithm is Caesar Cipher, she may
start ciphering C with different keys
– Using the English alphabet, there are only 26 possible keys
– In at most 26 trials, Eve breaks the cipher
• The method of trying all possible keys is called brute force
5
�
One-Time Pad
• Instead of using Caesar Cipher, with the constant
shift of 4 for every letter, Alice and Bob may
alternatively agree:
– Left-shift the first letter by 11 positions, the second letter
by 1 position and the third letter by 3 positions
– This algorithm would produce, when applied to the word M
= YES, C = E(M) = ODP
– Here the secret key constitutes of the triplet (11,1,3)
• Now the number of all possible keys is
26*26*26=17576
– This is still very small a key space to be exhaustively
searched with today’s computing resources
– However, trying every possible key would yield all English
three letter words!
6
�
One-Time Pad (cont.)
• This algorithm, called One-Time Pad, is perfectly secure
against brute force attacks (and all other imaginable
cryptographic attack methods)
In computer-based cryptography, the set of letters is 0 and 1
•
• For example, the bit-string K = 001101 could be used as a
secret key for One-Time Pad to encrypt a 6-bit string M =
011001, C = E(M) = M xor K:
M 011001
K 001101
C 010100
• One-Time Pad has two major limitations
– The same key may be used only once (otherwise there is a
statistical attack for breaking the cipher)
– The length of the key is equal to the length of the message
7
�
Cryptanalysis
• Cryptanalysis is the art of finding techniques for
breaking cryptographical algorithms
• Usually based on statistical methods
– Counting frequencies of different patterns in ciphertext
may reveal some redundancies in the original plaintext
• Cryptographical attacks may be categorized as
follows:
– Ciphertext only attack means determining the secret key
from the knowledge of a set of encrypted messages
– Known plaintext attack means determining the secret key
using the knowledge of a set of plaintext/ciphertext -pairs
– In a chosen plaintext attack the attacker has gained
knowledge of plaintext/ciphertext -pairs for chosen
plaintexts
8
�