MMCA CONFIDENTIAL
The
Content Protection
SecureMMC
System Specification
Version 1.00
November 2001
�
Revision History
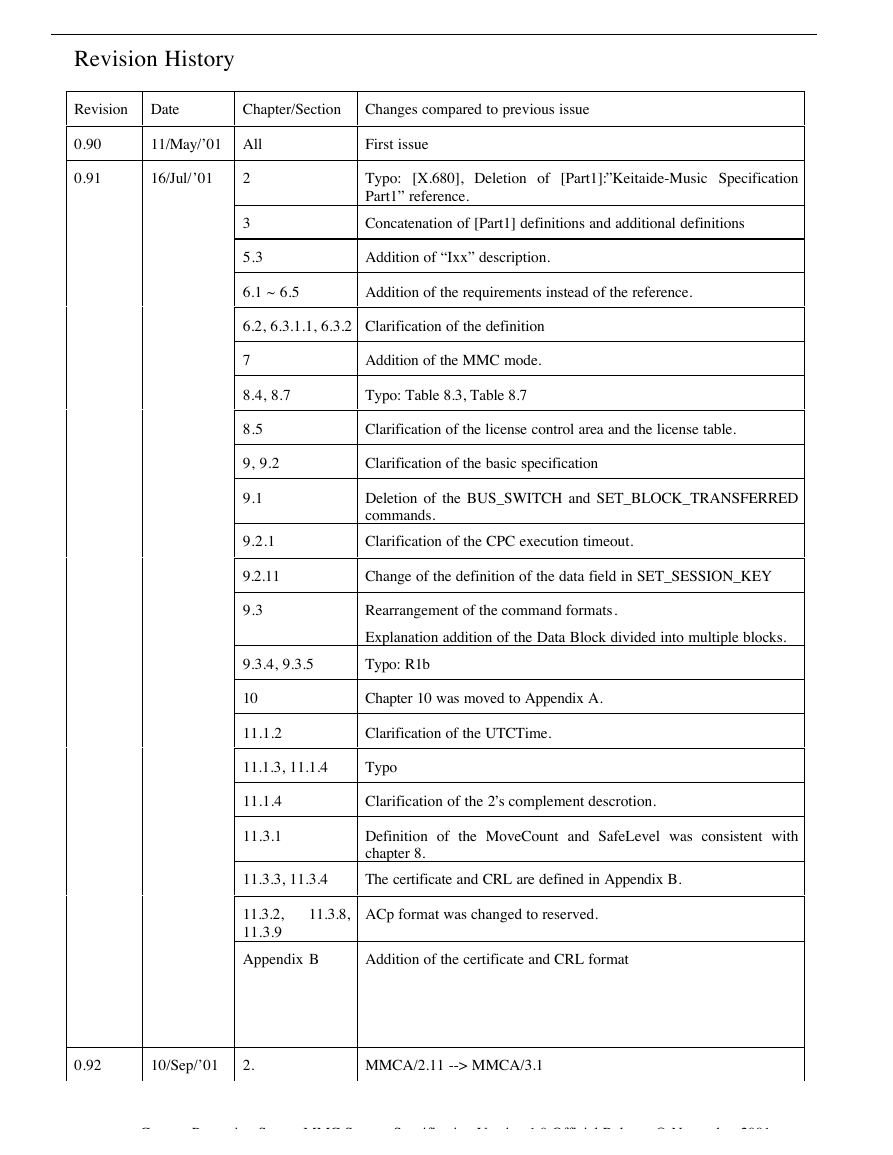
Revision
Date
Chapter/Section
Changes compared to previous issue
0.90
0.91
11/May/’01 All
First issue
16/Jul/’01
2
3
5.3
Typo: [X.680], Deletion of [Part1]:”Keitaide-Music Specification
Part1” reference.
Concatenation of [Part1] definitions and additional definitions
Addition of “Ixx” description.
6.1 ~ 6.5
Addition of the requirements instead of the reference.
6.2, 6.3.1.1, 6.3.2 Clarification of the definition
7
Addition of the MMC mode.
8.4, 8.7
Typo: Table 8.3, Table 8.7
8.5
9, 9.2
9.1
9.2.1
9.2.11
9.3
Clarification of the license control area and the license table.
Clarification of the basic specification
Deletion of the BUS_SWITCH and SET_BLOCK_TRANSFERRED
commands.
Clarification of the CPC execution timeout.
Change of the definition of the data field in SET_SESSION_KEY
Rearrangement of the command formats.
Explanation addition of the Data Block divided into multiple blocks.
9.3.4, 9.3.5
Typo: R1b
10
11.1.2
Chapter 10 was moved to Appendix A.
Clarification of the UTCTime.
11.1.3, 11.1.4
Typo
11.1.4
11.3.1
Clarification of the 2’s complement descrotion.
Definition of the MoveCount and SafeLevel was consistent with
chapter 8.
11.3.3, 11.3.4
The certificate and CRL are defined in Appendix B.
11.3.2,
11.3.9
11.3.8,
ACp format was changed to reserved.
Appendix B
Addition of the certificate and CRL format
0.92
10/Sep/’01
2.
MMCA/2.11 --> MMCA/3.1
Content Protection Secure MMC System Specification Version 1.0 Official Release ª
November 2001
�
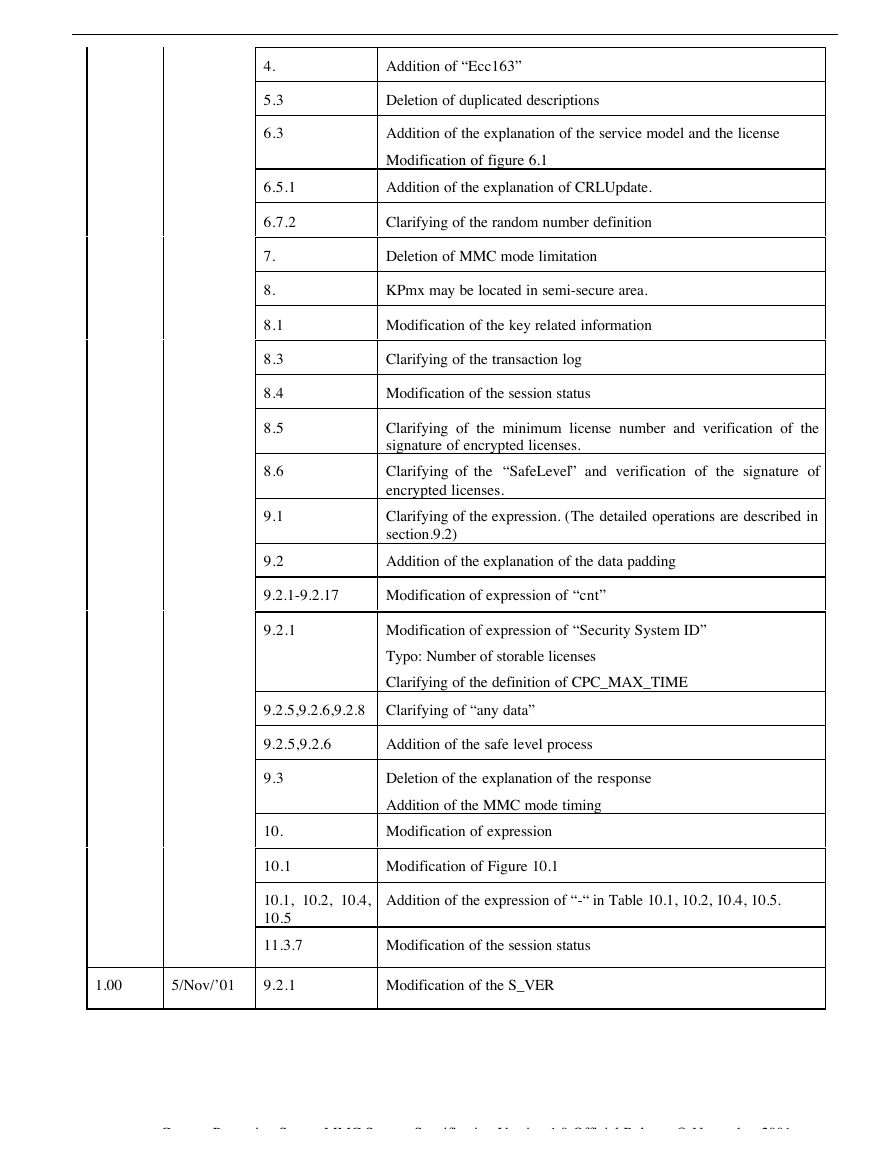
4.
5.3
6.3
6.5.1
6.7.2
7.
8.
8.1
8.3
8.4
8.5
8.6
9.1
9.2
Addition of “Ecc163”
Deletion of duplicated descriptions
Addition of the explanation of the service model and the license
Modification of figure 6.1
Addition of the explanation of CRLUpdate.
Clarifying of the random number definition
Deletion of MMC mode limitation
KPmx may be located in semi-secure area.
Modification of the key related information
Clarifying of the transaction log
Modification of the session status
Clarifying of the minimum license number and verification of the
signature of encrypted licenses.
Clarifying of the “SafeLevel” and verification of the signature of
encrypted licenses.
Clarifying of the expression. (The detailed operations are described in
section.9.2)
Addition of the explanation of the data padding
9.2.1-9.2.17
Modification of expression of “cnt”
9.2.1
Modification of expression of “Security System ID”
Typo: Number of storable licenses
Clarifying of the definition of CPC_MAX_TIME
9.2.5,9.2.6,9.2.8
Clarifying of “any data”
9.2.5,9.2.6
Addition of the safe level process
9.3
10.
10.1
Deletion of the explanation of the response
Addition of the MMC mode timing
Modification of expression
Modification of Figure 10.1
10.1, 10.2, 10.4,
10.5
Addition of the expression of “-“ in Table 10.1, 10.2, 10.4, 10.5.
11.3.7
Modification of the session status
1.00
5/Nov/’01
9.2.1
Modification of the S_VER
Content Protection Secure MMC System Specification Version 1.0 Official Release ª
November 2001
�
is provided
the attached standard (the “Standard)
You acknowledge
to you on an “AS IS” basis.
MULTIMEDIACARD ASSOCIATION (“MMCA”) MAKES NO EXPRESS, IMPLIED OR STATUORY
WARRENTIES AND EXPRESSLY DISCLAIMS THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR
A PARTICULAR PURPOSE AND NON-INFRINGEMENT OF THIRD PARTY RIGHTS. MMCA SHALL NOT
BE LIABLE FOR (I) TECHNICAL OR EDITORIAL ERRORS OR OMISSIONS CONTAINED WITHIN THE
STANDARD, OR (II) ANY INCIDENTAL, SPECIAL, EXEMPLARY OR CONSEQUENTAIL DAMAGES
(INCLUDING WITHOUT LIMITATION LOST PROFITS OR LOSS OF USE) RESULTING FROM THE
FURNISING, PERFORMANCE OR USE OF THE STANDARD, EVEN IF THE ADVISED OF THE
POSSIBILITY OF SUCH DAMAGES.
Copyright ª
reserved.
November 2001 MultiMediaCard Association, P.O. Box 2012, Cupertino, CA 95015-2012. World rights
No part of this publication may be transmitted, reproduced or distributed in any way, including but not limited to
photocopying, electronic copying, magnetic or other recording without the prior written consent of MMCA.
Content Protection Secure MMC System Specification Version 1.0 Official Release ª
November 2001
�
Introduction
Due to the recent trends in the rapid popularization of mobile phones and the Internet as well as the realization of
high-speed data transmission, a new type of information distribution service has gradually been emerged into the
market as a large volume data distribution service through these cyber networks. In addition, the music data
content distribution service is expected to grow in the future among the various large volume data distribution
services. However, in distributing a valuable content such as the music data on the Internet, it is crucial to
establish the technologies to protect the content from illegal piracies and unauthorized distributions, which have
emerged as one of the important social issues.
The Content Protection Secure MultiMediaCard System Specification describes the technical specifications
required to distribute the digital data content from the server to the storage media inserted in the portable device
for recording and playback of the digital data content. This specification realizes those functions both in a secure
manner and without losses of conveniences for the users.
This specification is based on the protocols for the interoperability among systems to realize the content
protection technology called UDAC-MB (Universal Distribution with Access Control - Media Base). UDAC-MB
is applicable to the encrypted content distribution through not only the cyber networks but also packaged media
or the local data exchange between consumers.
Implementations conforming to this specification avail to strongly protect the content distributed through the
mobile phone networks and/or the Internet and, hence, easily realize the new type of content distribution services
through the networks. Though this specification mainly describes on the distribution of contents through the
mobile phone terminals, its application may also be expanded and applied to other various types of network
terminals, portable devices and contents.
‘UDAC-MB’ is the trademark of FUJITSU LIMITED, Hitachi Ltd., NIPPON COLUMBIA CO., LTD., PFU Limited
and SANYO Electric Co, Ltd.
Content Protection Secure MMC System Specification Version 1.0 Official Release ª
November 2001
�
Contents
1
SCOPE........................................................................................................................................1
2 REFERENCES .............................................................................................................................2
3 DEFINITIONS .............................................................................................................................3
3.1 Definitions in [X. 509]..................................................................................................................................................3
3.2 Definitions in [MMCA/3.1].........................................................................................................................................3
3.3 Additional Definitions in this Specification..............................................................................................................3
4 ABBREVIATIONS........................................................................................................................6
5 CONVENTIONS ..........................................................................................................................7
5.1 Expression of Numerical Values .................................................................................................................................7
5.2 Expression of Keys .......................................................................................................................................................7
5.3 Notations.........................................................................................................................................................................7
6 REQUIREMENTS........................................................................................................................9
6.1 Compatibility..................................................................................................................................................................9
6.2 User Requirements ........................................................................................................................................................9
6.3 Supposed Service Model..............................................................................................................................................9
6.4 Security Requirements................................................................................................................................................11
Supposed Requirements for Content Protection..................................................................................11
Content Usage Control (Access Control)............................................................................................ 12
Access Control by Security Level.......................................................................................................... 13
Relationship with Electronic Commerce Security.............................................................................. 13
6.5 Supposed Protocol.......................................................................................................................................................14
Authorization Protocol Basic Procedure............................................................................................. 14
Procedures of each Protocol.................................................................................................................. 16
6.6 Structural Requirements .............................................................................................................................................16
6.7 Implementation criteria...............................................................................................................................................17
Implementation of Tamper Resistant Module ..................................................................................... 17
Generation of Random Numbers........................................................................................................... 17
FEATURES................................................................................................................................18
6.4.1
6.4.2
6.4.3
6.4.4
7
6.5.1
6.5.2
6.7.1
6.7.2
8
INFORMATION IN SEMI-SECURE AND SECURE AREA.............................................................20
8.1 Key Related Information............................................................................................................................................20
8.2 Certificates....................................................................................................................................................................21
8.3 CRL................................................................................................................................................................................21
8.4 Transaction Log ...........................................................................................................................................................21
8.5 License Table................................................................................................................................................................22
8.6 License Control Area ..................................................................................................................................................22
8.7 Work Registers.............................................................................................................................................................23
9 ADDITIONAL COMMANDS.......................................................................................................25
9.1 Outline ...........................................................................................................................................................................25
9.2 Additional Command Specifications .......................................................................................................................27
SEND_SCSR............................................................................................................................................. 28
SEND_LOG............................................................................................................................................... 29
ESTABLISH_WRITE_SESSION ............................................................................................................ 30
SEND_SESSION_KEY............................................................................................................................ 30
SEND_PLAY_LICENSE.......................................................................................................................... 31
SEND_MOVE_LICENSE ....................................................................................................................... 31
SEND_SIGNED_LOG............................................................................................................................. 32
SEND_CERT............................................................................................................................................. 32
WRITE_LICENSE.................................................................................................................................... 33
READ_LICENSE...................................................................................................................................... 33
SET_SESSION_KEY................................................................................................................................ 34
9.2.1
9.2.2
9.2.3
9.2.4
9.2.5
9.2.6
9.2.7
9.2.8
9.2.9
9.2.10
9.2.11
Content Protection Secure MMC System Specification Version 1.0 Official Release ª
November 2001
�
9.3.1
9.3.2
9.3.3
9.3.4
9.3.5
9.2.12
9.2.13
9.2.14
9.2.15
9.2.16
9.2.17
SET_LICENSE ..........................................................................................................................................35
ESTABLISH_PLAY_SESSION ................................................................................................................35
ESTABLISH_MOVE_SESSION ..............................................................................................................36
RECOVER_SESSION...............................................................................................................................36
SEARCH_LICENSE .................................................................................................................................37
VERIFY_CERT..........................................................................................................................................38
9.3 Command Format........................................................................................................................................................ 39
Block Read type (without SEND_CERT)..............................................................................................39
SEND_CERT .............................................................................................................................................40
Block Write type........................................................................................................................................41
WRITE_LICENSE.....................................................................................................................................41
READ_LICENSE ......................................................................................................................................42
10 STATE TRANSITIONS .............................................................................................................. 44
10.1 Whole State Transition for CPCs ............................................................................................................................. 45
10.2 Reading Session .......................................................................................................................................................... 47
10.3 Licensing for Playback............................................................................................................................................... 49
10.4 Moving License........................................................................................................................................................... 51
10.5 Writing Session ........................................................................................................................................................... 53
10.6 Retrying Session.......................................................................................................................................................... 55
11 MESSAGE FORMAT................................................................................................................. 57
11.2.1
11.2.2
11.2.3
11.2.4
11.2.5
11.3.1
11.3.2
11.3.3
11.3.4
11.3.5
11.3.6
11.3.7
11.3.8
11.3.9
11.1.1
11.1.2
11.1.3
11.1.4
11.1.5
11.1.6
11.1.7
11.1.8
11.1.9
11.1 Basic Rules ................................................................................................................................................................... 57
Encoding Rule...........................................................................................................................................57
Tag...............................................................................................................................................................57
Size Field Rule..........................................................................................................................................57
INTEGER Type Rule ................................................................................................................................57
BIT STRING Type Rule............................................................................................................................58
OCTET STRING Type Rule.....................................................................................................................58
SEQUENCE Type Rule............................................................................................................................58
OPTIONAL Rule.......................................................................................................................................59
UTCTime Type Rule .................................................................................................................................59
11.2 Appending Rules ......................................................................................................................................................... 60
Application Tags.......................................................................................................................................60
TripleDesKey Format...............................................................................................................................60
TripleDesCode Format............................................................................................................................61
Ecc163PublicKey Format.......................................................................................................................62
Ecc163Code Format................................................................................................................................62
11.3 Structure Definition .................................................................................................................................................... 62
ACm Structure...........................................................................................................................................62
ACp Structure............................................................................................................................................64
Certificate Structure ................................................................................................................................64
CRL Structure ...........................................................................................................................................67
SessionInformation Structure .................................................................................................................70
EncryptedLicense Structure....................................................................................................................70
TransactionLog Structure .......................................................................................................................72
PlayInformation Structure......................................................................................................................74
License Structure ......................................................................................................................................74
11.4 Terminal – Media Command..................................................................................................................................... 77
SEND_LOG command.............................................................................................................................77
SEND_CERT command...........................................................................................................................77
SET_SESSION_KEY command..............................................................................................................78
RECOVER_SESSION command............................................................................................................78
ESTABLISH_WRITE_SESSION command ..........................................................................................80
SET_LICENSE command........................................................................................................................81
WRITE_LICENSE command..................................................................................................................82
SEARCH_LICENSE command...............................................................................................................82
SEND_SIGNED_LOG command...........................................................................................................82
VERIFY_CERT command.......................................................................................................................82
SEND_SESSION_KEY command ..........................................................................................................83
ESTABLISH_MOVE_SESSION command ...........................................................................................84
ESTBLISH_PLAY_SESSION command................................................................................................85
11.4.1
11.4.2
11.4.3
11.4.4
11.4.5
11.4.6
11.4.7
11.4.8
11.4.9
11.4.10
11.4.11
11.4.12
11.4.13
Content Protection Secure MMC System Specification Version 1.0 Official Release ª
November 2001
�
11.4.14
11.4.15
11.4.16
READ_LICENSE command................................................................................................................... 85
SEND_MOVE_LICENSE command..................................................................................................... 86
SEND_PLAY_LICENSE command....................................................................................................... 86
APPENDIX A SEQUENCE AND INTERNAL DATA FLOW EXAMPLES ..............................................88
APPENDIX B CERTIFICATE/CRL FORMAT (INFORMATIVE) .......................................................96
Content Protection Secure MMC System Specification Version 1.0 Official Release ª
November 2001
�