Secure MultiMediaCard
(SecureMMC)
The
A internal use only
C
M
For M
System Specification
Version 1.0
Infineon Technologies AG
�
SecureMMC
Revision History
Version Date Section/ Page
Author
Changes compared to previous issue
0.1
0.2
0.3
1.0
11.00
01.01
03.01
05.01
all
all
all
5
Dr. Th. Böker,
Infineon
Dr. Th. Böker,
Infineon
Dr. Th. Böker,
Infineon
Dr. Th. Böker,
Infineon
first draft specification of SecureMMC
major changes in Chapter 3 after MMCA meeting
Nov.2000, Hawaii
overall review after MMCA meeting Feb.2001,
Orlando
setting the mandatory and optional cryptoalgo-
rithms after MMCA meeting Apr. 2001, Rome
2
SecureMMC Specification Version 1.0 Preliminary
�5/16/01 Infineon Technologies AG
�
SecureMMC
1 Scope............................................................................................................................. 5
2 General description of the SecureMMC ..................................................................... 7
2.1 Standard MMC versus SecureMMC ....................................................................... 7
2.2 Memory partitions.................................................................................................... 7
2.3 File Structure for the operation system in the SecureMMC .................................... 8
2.4 The secure command set...................................................................................... 10
2.5 Logical channels ................................................................................................... 11
3 Secure command structure and transport through standard MMC ...................... 13
3.1 Framing of the Security Commands and Responses............................................ 13
3.2 Transport of the SecCMD tokens through the standard MMC interface ............... 14
3.3 The Status Word for the SecureMMC ................................................................... 17
4 Description of the Secure Command Set................................................................. 18
A internal use only
4.1 Overview of the Secure Commands ..................................................................... 18
4.2 Detailed description of the Security Commands and Responses ......................... 19
4.2.1 OPEN_CHANNEL ......................................................................................................20
4.2.2 CLOSE_CHANNEL ....................................................................................................21
4.2.3 VERIFY.......................................................................................................................22
4.2.4 DISABLE_VERIFICATION_REQUIREMENT.............................................................23
4.2.5 ENABLE_VERIFICATION_REQUIREMENT..............................................................23
4.2.6 CHANGE_REFERENCE_DATA ................................................................................24
4.2.7 RESET_RETRY_COUNTER......................................................................................24
4.2.8 OPEN_FILE................................................................................................................25
4.2.9 CLOSE_FILE..............................................................................................................26
4.2.10 WRITE_FILE ............................................................................................................26
4.2.11 READ_FILE ..............................................................................................................27
4.2.12 MANAGE_SECURITY_ENVIRONMENT (MSE) ......................................................27
4.2.12.1 MSE_RESTORE...............................................................................................28
4.2.12.2 MSE_SET .........................................................................................................28
4.2.12.3 MSE_DERIVE_KEY .........................................................................................29
4.2.13 PERFORM_SECURITY_OPERATION (PSO) .........................................................29
4.2.13.1 PSO_ENCIPHER..............................................................................................30
4.2.13.2 PSO_DECIPHER..............................................................................................31
4.2.13.3 PSO_COMPUTE_DIGITAL_SIGNATURE .......................................................32
4.2.13.4 PSO_VERIFY_DIGITAL_SIGNATURE ............................................................32
4.2.13.5 PSO_COMPUTE_CRYPTOGRAPHIC_CHECKSUM ......................................33
4.2.13.6 ASK_RANDOM.................................................................................................34
For M
C
M
SecureMMC Specification Version 1.0 Preliminary
�5/16/01 Infineon Technologies AG
3
�
SecureMMC
5 Cryptographic features of the SecureMMC.............................................................. 35
5.1 How to use these algorithms................................................................................. 35
5.2 Asymmetric cryptoalgorithms ................................................................................ 35
5.3 Elliptic curves ........................................................................................................ 38
5.4 Symmetric cryptoalgorithms for bulk encryption ................................................... 38
5.5 Hash functions ...................................................................................................... 40
6 SecureMMC characterization .................................................................................... 41
6.1 Card Package ....................................................................................................... 41
6.2 Robustness level................................................................................................... 41
7 Glossary ...................................................................................................................... 44
8 References .................................................................................................................. 46
A internal use only
C
M
For M
SecureMMC Specification Version 1.0 Preliminary
�5/16/01 Infineon Technologies AG
4
�
SecureMMC
1 Scope
The scope of the SecureMMC is to support applications that need from low to high level
security. Figure 1.1 shows different applications that require different levels of security. For
example, it makes no sense to apply security protection to freely distributed data such as
advertising or demonstration material (e.g., low quality MP3 files). At a slightly higher secu-
rity level, since the news in newspapers is usually outdated after a couple of days or weeks,
simple content scrambling is probably sufficient. At a yet higher security level, content pro-
tection (e.g., for digital music like MP3 files), is seen as a mid-level security application with
e/m-commerce and payment applications as being more sensitive applications requiring a
higher level of security.The SecureMMC is designed to be used up to the highest level of
security by using public key infrastructures (PKI) as well as chip card technologies such as
tamper resistant modules (TRM) to prevent hardware hacker attacks.
typical applications
money: e/m-commerce, online
banking
GSM/WAP: identification,
authentication
personal data: banking
receipts, PIN, ...
protected content: music, video,
books, .…
personal data: EMail, addresses, ..
newspaper
free distributable data:
advertising, demos, ..
y
t
i
r
u
c
e
s
f
o
l
e
v
e
l
crypto-features
Public Key Infrastructure (PKI)
Digital Signatures
Certificates
RSA, Elliptic Curves
3-DES, 112bit key
DES, 56bit key
C2 cipher, 56bit key
symmetric encryption
with <56bit secret key
content scrambling
%
Figure 1.1: Different levels of security
It should be noted that of course the SecureMMC is capable of applying lower level security
applications such as content protection schemes as well. An example of a music distribu-
tion and content protection system using a PKI is the Keitaide-Music System (see
http:\\www.keitaide-music.org). It uses a standard MMC with an additional set of security
related commands. The tamper resistant design guarantees low risk for content providers
SecureMMC Specification Version 1.0 Preliminary
�5/16/01 Infineon Technologies AG
5
�
SecureMMC
to have unlimited copies of their content by unauthorized users. This system is SDMI com-
pliant and started service in November 2000.
The SecureMMC has a more sophisticated command set that is based on chip card com-
mands. The focus has been placed on the mobile e-commerce market. When used as a
security element (SE) the SecureMMC may be used in a mobile phone to create a personal
trusted device (PTD) as proposed by the MeT forum (Mobile electronic Transaction forum;
see [MeT_White]).
The WIM functionality (WAP Identity Module; see [WAP_WIM]) is a key feature in the secu-
rity element for mobile transactions and has therefore been chosen to be the target applica-
tion for the SecureMMC. By adding to the WIM standard primitive command set chip card
related commands (see [ISO7816-4] and [ISO7816-8]) the SecureMMC becomes more
flexible. This is to benefit a wider variety of applications such as banks, financial services,
online-shops, and many more. These well-known standards make it easy for any service
provider to implement their security scheme by using the SecureMMC.
6
SecureMMC Specification Version 1.0 Preliminary
�5/16/01 Infineon Technologies AG
�
SecureMMC
2 General description of the SecureMMC
The following chapter gives an overview of the additional features of the SecureMMC in
contrast to the standard MMC. It also describes the general setup of the SecureMMC such
as memory partitioning, the file structure, and the command set.
2.1 Standard MMC versus SecureMMC
The SecureMMC is meant to be fully compliant with the standard MMC system specification
[MMC_Spec3.0]. All features described in there such as command and data structures to
transport (i.e. read, write, and erase) any type of data are the same for the SecureMMC.
However, like in the standard MMC the SecureMMC may not support all command classes
but class 0 is mandatory.
The SecureMMC has an extended CSD register which provides the information that the
new opcode set for the security mode is supported. With the SWITCH command the host
must switch to the SecureMMC mode in which the transport commands for the security
functions are enabled. The host must not switch to other modes during a security session.
2.2 Memory partitions
The standard MMC possesses memory areas that can be directly accessed from the host
analogous to Flash and ROM cards. However, for security reasons, some information
needs to be kept secret such as private keys and verification data (such as a PIN). Even if
such data are stored on the Flash or ROM payload area and protected by the password
mechanism (see [MMC_Spec3.0] Chapter 4.4.4) the level of security is not sufficient for
most applications using a PKI.
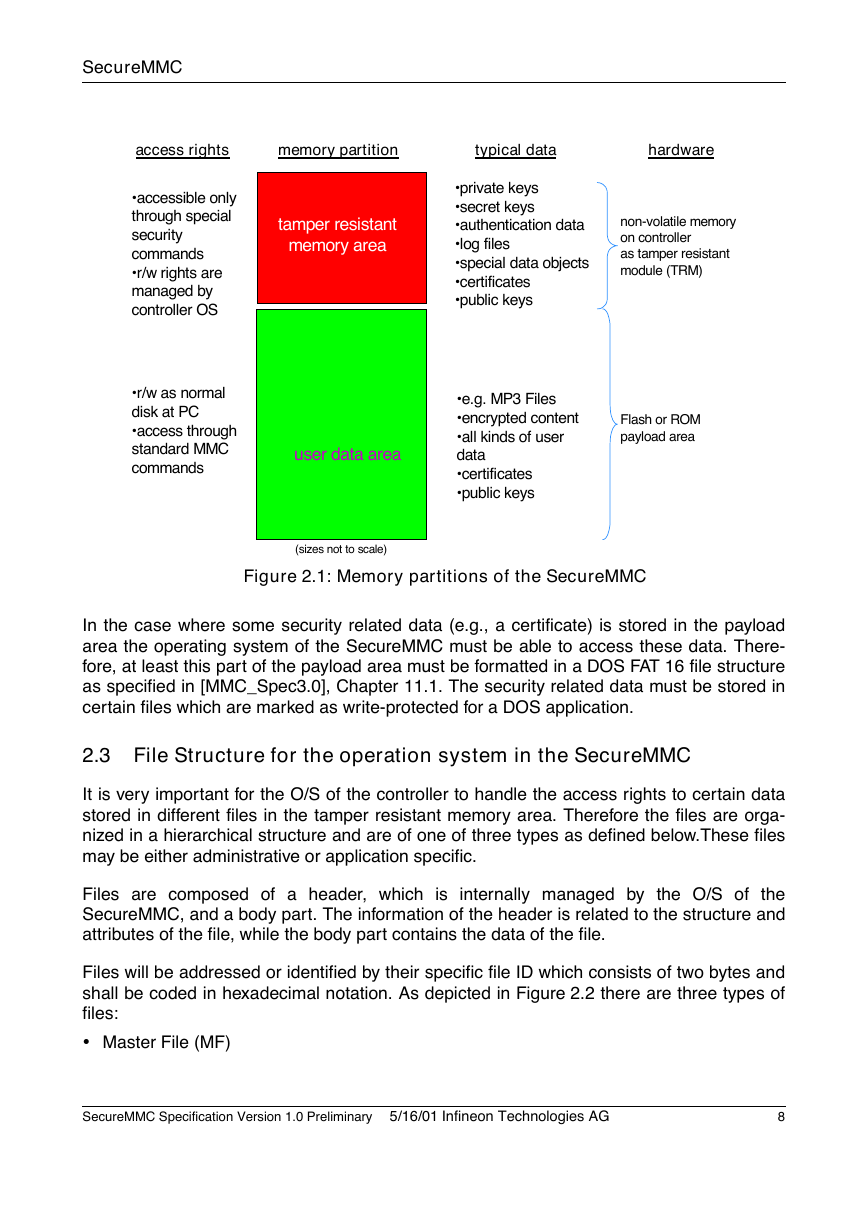
Therefore an additional memory area is present in the SecureMMC. Figure 2.1 depicts the
different memory areas consisting of the standard user data or payload area and a tamper
resistant area. As mentioned above the user has unlimited access rights to the payload
area which typically contains all kinds of user data. However, a number of security related
data may be stored as well in this area as far as they are not sensitive. Such data could be
certificates, public keys, and also receipt depending on their specific content.
The access rights to the tamper resistant memory area is managed by the operating sys-
tem of the SecureMMC. Only after a certain authentication process which is dependent on
the application currently using the SecureMMC the user (i.e. its application) gets access to
the data in this area which belong to this specific application. Each application can only get
access to its corresponding data.
The latter memory area will be typically an embedded non-volatile memory area of the
security controller. As a tamper resistant module the controller is protected against hard-
ware attacks as well. This means sensitive data such as private keys, secret keys, authen-
tication data, and so forth are well protected against unauthorized access.
SecureMMC Specification Version 1.0 Preliminary
�5/16/01 Infineon Technologies AG
7
�
SecureMMC
access rights
memory partition
typical data
hardware
accessible only
through special
security
commands
r/w rights are
managed by
controller OS
r/w as normal
disk at PC
access through
standard MMC
commands
tamper resistant
memory area
private keys
secret keys
authentication data
log files
special data objects
certificates
public keys
non-volatile memory
on controller
as tamper resistant
module (TRM)
e.g. MP3 Files
encrypted content
all kinds of user
data
certificates
public keys
Flash or ROM
payload area
user data area
(sizes not to scale)
Figure 2.1: Memory partitions of the SecureMMC
In the case where some security related data (e.g., a certificate) is stored in the payload
area the operating system of the SecureMMC must be able to access these data. There-
fore, at least this part of the payload area must be formatted in a DOS FAT 16 file structure
as specified in [MMC_Spec3.0], Chapter 11.1. The security related data must be stored in
certain files which are marked as write-protected for a DOS application.
2.3 File Structure for the operation system in the SecureMMC
It is very important for the O/S of the controller to handle the access rights to certain data
stored in different files in the tamper resistant memory area. Therefore the files are orga-
nized in a hierarchical structure and are of one of three types as defined below.These files
may be either administrative or application specific.
Files are composed of a header, which is internally managed by the O/S of the
SecureMMC, and a body part. The information of the header is related to the structure and
attributes of the file, while the body part contains the data of the file.
Files will be addressed or identified by their specific file ID which consists of two bytes and
shall be coded in hexadecimal notation. As depicted in Figure 2.2 there are three types of
files:
• Master File (MF)
SecureMMC Specification Version 1.0 Preliminary
�5/16/01 Infineon Technologies AG
8
�